Microsoft releases EMET 5.0 Tech Preview
One of the programs that I install instantly after setting up a new PC with Windows is Microsoft's Enhanced Mitigation Experience Toolkit EMET.
The program adds another layer of defense to the operating system and springs to action when malware is executed on the system. It can mitigate attacks so that they are not successful at all or reduced in scope.
It should be clear that this is not a 100% protection against malware, but it does add a level of protection to the system that can be quite useful if attackers do not target EMET directly as well.
Microsoft has released a Tech Preview of EMET 5.0, the upcoming version of the Enhanced Mitigation Experience Toolkit.
EMET 5.0 introduces two new mitigations to the 12 security mitigations of version 4.1 which improve the defensive capabilities of the program further.
Attack Surface Reduction (ASR)
ASR has been designed to block certain plugins from being loaded from within applications. You can configure applications in EMET to block the loading of plugins automatically. Basic examples are to block the execution of Flash code in Microsoft Word, or Internet Explorer from loading the Java plugin on Internet Zone websites while allowing it to be loaded on Intranet Zone websites.
EMET 5.0 Technical Preview is configured by default to block certain plug-ins from being loaded in Internet Explorer, Microsoft Word and Excel.
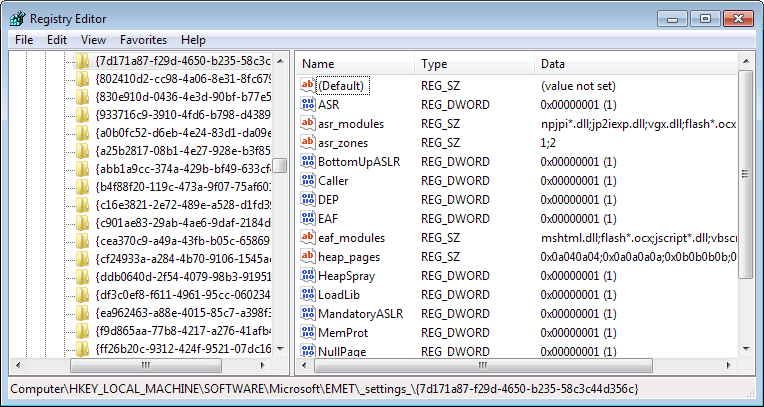
The list of blocked modules and the security zones the modules are allowed to be loaded are defined in the Windows Registry.
HKLM\SOFTWARE\Microsoft\EMET\_settings_\{CLSID}\asr_modules = “…â€
HKLM\SOFTWARE\Microsoft\EMET\_settings_\{CLSID}\asr_zones = “…â€
The module flash*.ocx is blocked from loading in winword.exe and excel.exe, while the modules npjpi*.dll;jp2iexp.dll;vgx.dll;flash*.ocx are blocked from being loaded in Internet Explorer on Local, Internet and Untrusted Zone websites.
You can add or remove module, or modify zones for these three programs or for other programs that you have added to eMET.
Export Address Table Filtering Plus (EAF+)
New capabilities have been added to the existing EAF functionality. EAF+ adds the following safeguards when enabled:
- Add protection for KERNELBASE exports in addition to the existing NTDLL.DLL and KERNEL32.DLL
- Perform additional integrity checks on stack registers and stack limits when export tables are read from certain lower-level modules
- Prevent memory read operations on protected export tables when they originate from suspicious modules that may reveal memory corruption bugs used as “read primitives†for memory probing
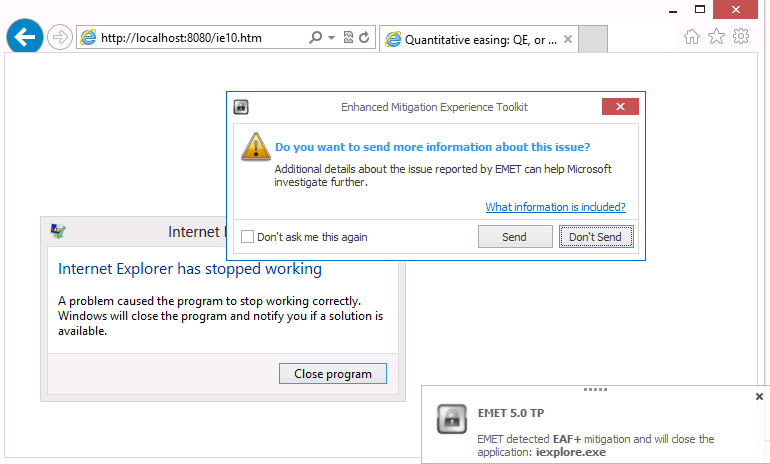
EAF+ is enabled by default. You can disable the feature with a click on Apps in the EMET interface and a click on the EAF+ box under mitigation settings in the ribbon.
Other improvements
The Deep Hooks mitigation setting is enabled in the technical preview of EMET. The feature was disabled by default previously due to third-party application incompatibilities.
These compatibility issues appear to have been resolved according to Microsoft, which is why Deep Hooks is enabled by default now.
Note that this is only the case for the Technical Preview, and that Microsoft will evaluate this during the preview phase. It is theoretically possible that EMET 5.0 final will ship with it disabled again depending on the outcome.
In addition, several compatibility issues were fixed including one involving Adobe Reader and the "MemProt" mitigation.
Download
If you are interested in running the EMET 5.0 Technical Preview, visit the official website of the program to download it. You find the download link in the right sidebar section on the homepage.
Here you can also download the updated guide that walks you through all the features and settings of the application.
Advertisement

















This is a great tool! It’s the first thing I load with a new PC also, and has saved me from malware a couple of times.
Read the ars article this morning. My understanding of the case is that any program running at the same layer as the attacking program — as EMET runs alongside trojans et al — will be easily bypassed.
EMET’s great, I have it on several of the PCs I control, but I think MS could build better kernel-level (ok, there’s no kernel, but you know what I mean) protections. Both the MacOS and linux iterations are inherently more secure because of this quasi-sandboxing. Perhaps we’ll see this with Win9.. if MS is still a desktop player at that point.
Like I said, EMET does not promise 100% protection against all exploit or attack types. But, it protects against many standard attacks that are not targeted specifically against the system EMET is running on.
While Microsoft could — and should — implement EMET natively in Windows 9, I’m not convinced that this is going to happen.
Microsoft already has low level sandboxing protections – they’re called integrity levels.
For what it’s worth, EMET doesn’t actually do anything in and of itself. All of the settings that it modifies you can change yourself without having to even download the program. What EMET does do, is provide a nice, clean, easy to use graphical front-end for making the changes.
Some of the improvements done in EMET 5 may be directly related to this article: http://arstechnica.com/security/2014/02/new-attack-completely-bypasses-microsoft-zero-day-protection-app/