KeePassXC adds support for Passkeys, improves database import from Bitwarden and 1Password

KeePassXC has been updated to 2.7.7. The latest version of the open source password manager adds support for Passkeys, and has gained the ability to import your vault data from Bitwarden.
Passkeys in KeePassXC
Several password managers have added support for Passkeys over the past year, including Bitwarden, 1Password, Dashlane, Google Password Manager, Apple iCloud Keychain, even Windows 11 supports it. KeePassXC is the latest to join the party to support the phishing-resistant protocol created by FIDO.
An important thing to note here is that this is not a standalone feature, it requires you to install the KeePassXC browser extension, which works in tandem with the desktop program. Download the KeePassXC browser extension for Firefox, Chrome or Edge.
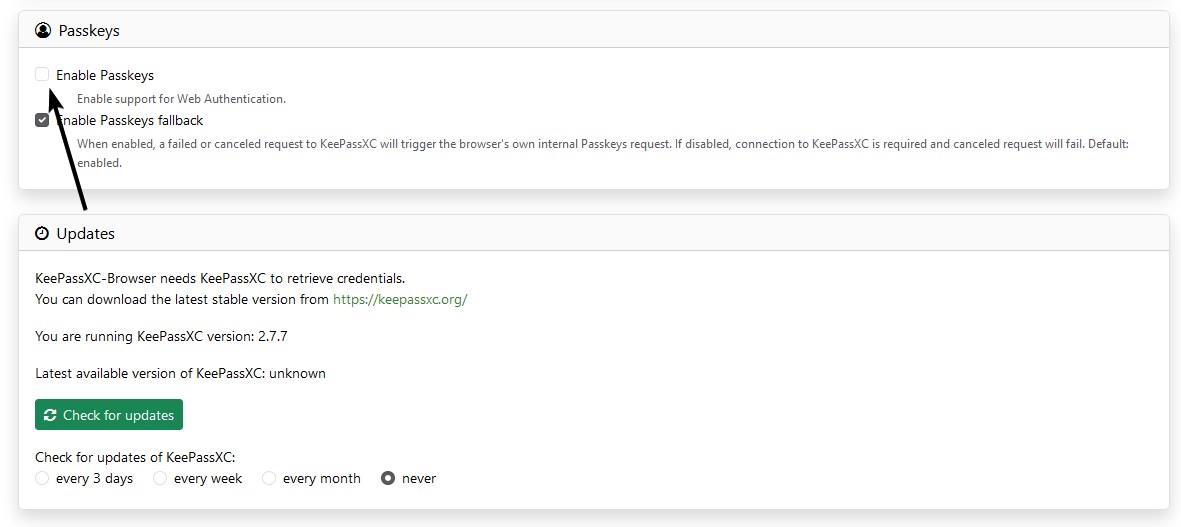
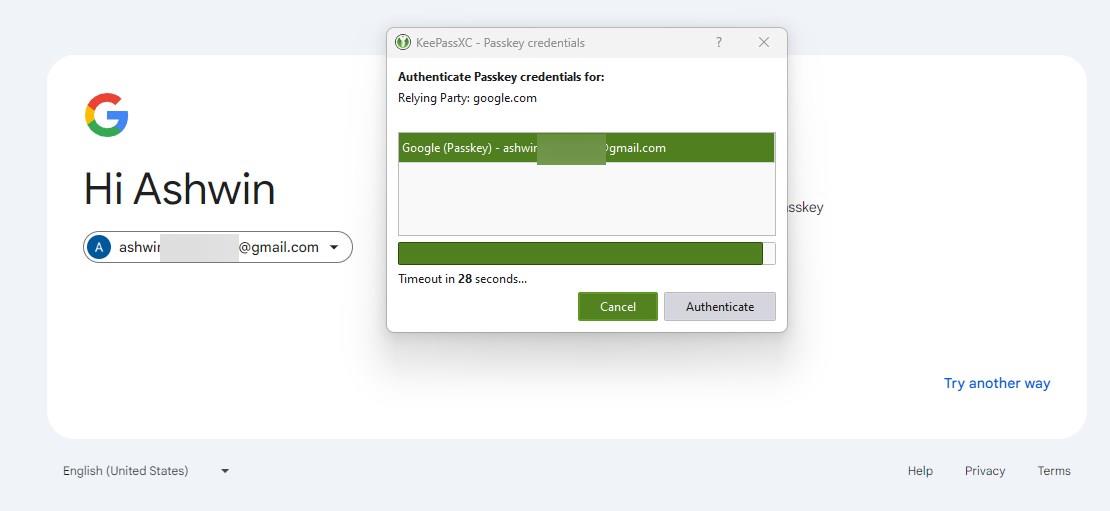
In order to use it, you will also need to "Enable Passkeys" in the extension's settings. To access the Passkeys stored in the application, head to the Database > Passkeys. Go to a website that supports Passkeys, for example, Google. Choose the "create a passkey" option, and select "Use another device". You should see a pop-up from the KeePassXC browser extension that asks you to save the passkey, click on "Register".
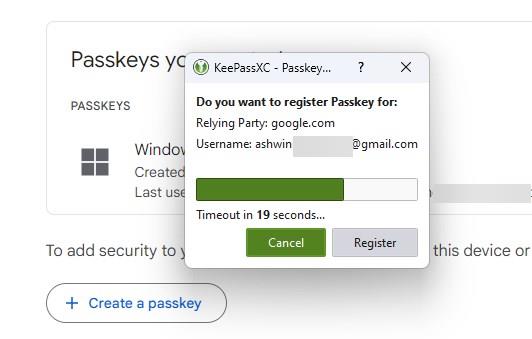
This will save the digital security key to your vault, you can find it saved as a new entry in your database, it has the word "Passkey" in the name. In the test scenario, it was saved as KeePassXC-Browser Passwords / Google (Passkey).
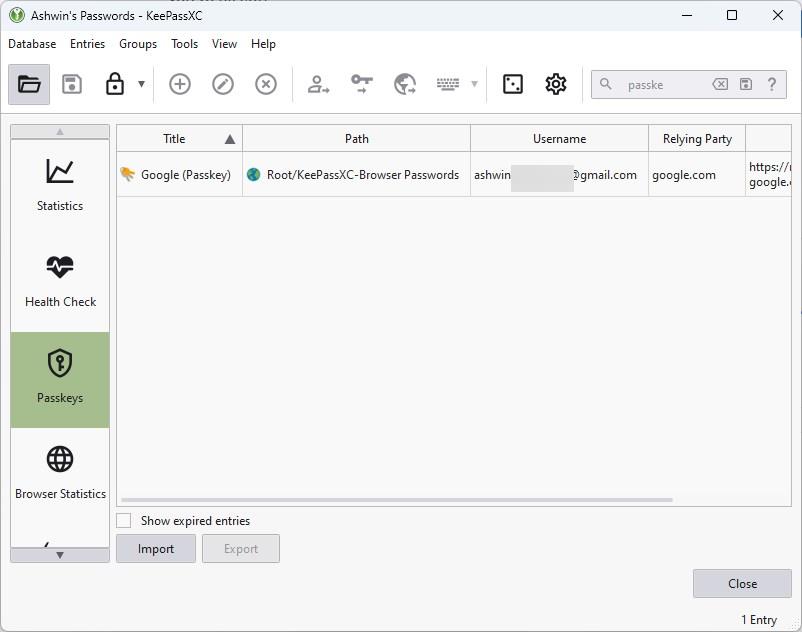
The password manager app also allows you to import existing Passkeys stored on your computer (.Passkey files). Once you have saved a Passkey in KeePassXC, you will be able to log in to websites without using a password.
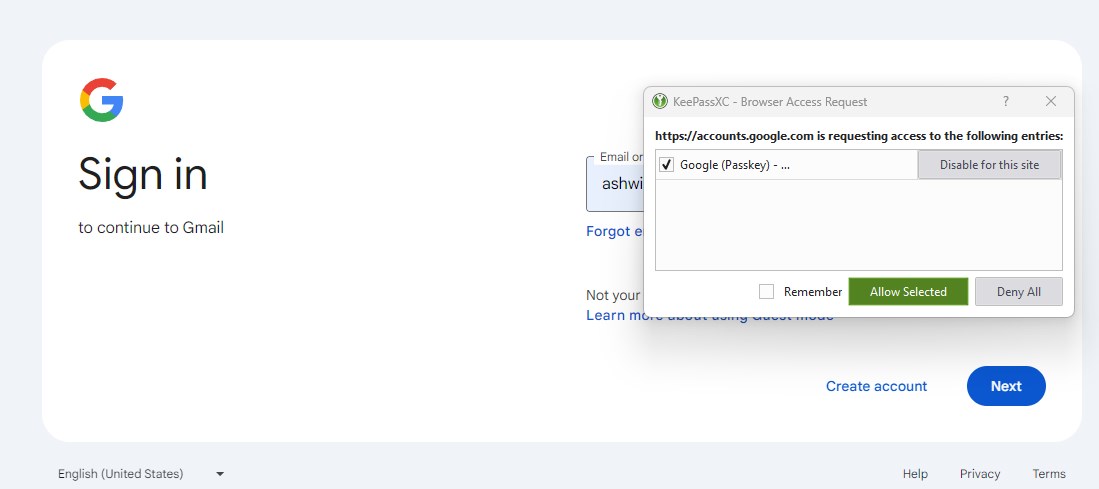
This works across browsers, so if you created a Passkey using the KeePassXC add-on for Firefox, it will be available in Chrome or Edge, as long as you have the extension for the browsers and have connected them to the vault. Refer to the official documentation for more details about the feature.
Import passwords from Bitwarden
KeePassXC now allows you to import your database from Bitwarden. The option to add the JSON format is available under a new Import Wizard that you can access from the Database > Import menu.
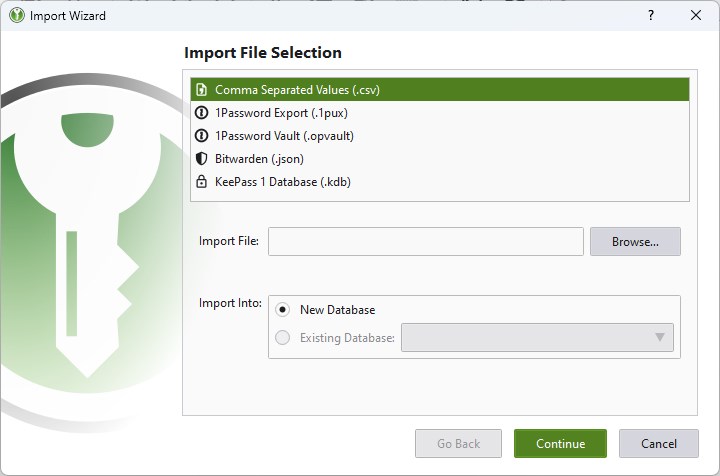
KeePassXC has allowed users to migrate from 1Password for a long time, but the older versions of the password manager used the OPVault format to import the data. The latest version of KeePassXC adds support for 1Password's export format, 1PUX. You may choose to import the data to an existing database, or create a new one. Other options that are available in the import wizard include support for CSV and KDB formats.
Easier database unlock for hardware keys
The announcement for KeePassXC 2.7.7 says that the program has improved the database unlock experience for hardware security keys such as YubiKey, OnlyKey. You no longer need to choose the hardware key or key file after entering your master password, in fact, the fields for both options have been removed from the login pop-up. The program now detects the devices automatically, all you need to do is plug in your hardware key into your computer. The feature also supports NFC readers and key files, though you will need to use the "select file" option to unlock the vault.
Download KeePassXC 2.7.7 for Windows, macOS and Linux from GitHub. You can also get it from the Microsoft Store.
Do you use a password manager for Passkeys?


















Why would you trust an open source program with your passwords? Anyone interested can go look at the code and find vulnerabilities, it’s much more secure to obscure things and make people who are interested in breaking through software like this actually work for it instead of getting everything they need on a platter.
1. The same can be said for all password managers, open or closed source. If it’s closed source you don’t know what’s going on, you just have to trust the company’s intentions.
2. That’s not how Keepass works. Only a user with the master password can access the vault of passwords. And you know this is true because the code is public.
Historically, FIDO private keys were stored on secure hardware (such as TPM or Yubikey) that were not assessable to the user or software running on the device.
Where are the private keys stored with KeePassXC and how are they protected?
The Passkeys are saved directly in the password database. You can export the key as a .Passkey file, but the documentation says that the extracted data is unencrypted. https://keepassxc.org/docs/KeePassXC_UserGuide#_advanced_usage_2