Microsoft publishes new Registry security mitigation for Intel processors (Spectre)

About six years ago, vulnerabilities were discovered that affected most Intel and AMD processors. The vulnerabilities, Spectre and Meltdown, can be exploited to read sensitive data from attacked computer systems.
Intel released an update for one of the Spectre variants, disclosed officially on March 8, 2022. Microsoft implemented mitigations in client and server versions of Windows as a response to this.
These are disabled by default. The main reason for this seems to be potential performance impacts that comes with the implementation.
This guide walks you through the steps of configuring Windows to enable the mitigations and finding out if your processor is affected.
Is your processor affected?
The very first thing you may want to do is check if your processor is on Intel's list of affected CPUs.
- If it is on the list, you may enable the mitigation to protect the system against potential attacks.
- If it is not on the list, you can skip the remainder of the article.
Here is how you find out:
- Open Start > Settings > System > About and check the listed processor.
- Load the following two resource websites: Nist.gov and Intel's Affected Processors website.
Check to see if the installed processor is listed on these websites. You may want to use the browser's search to find the information quickly.
Microsoft's Registry tweak to protect against the vulnerability
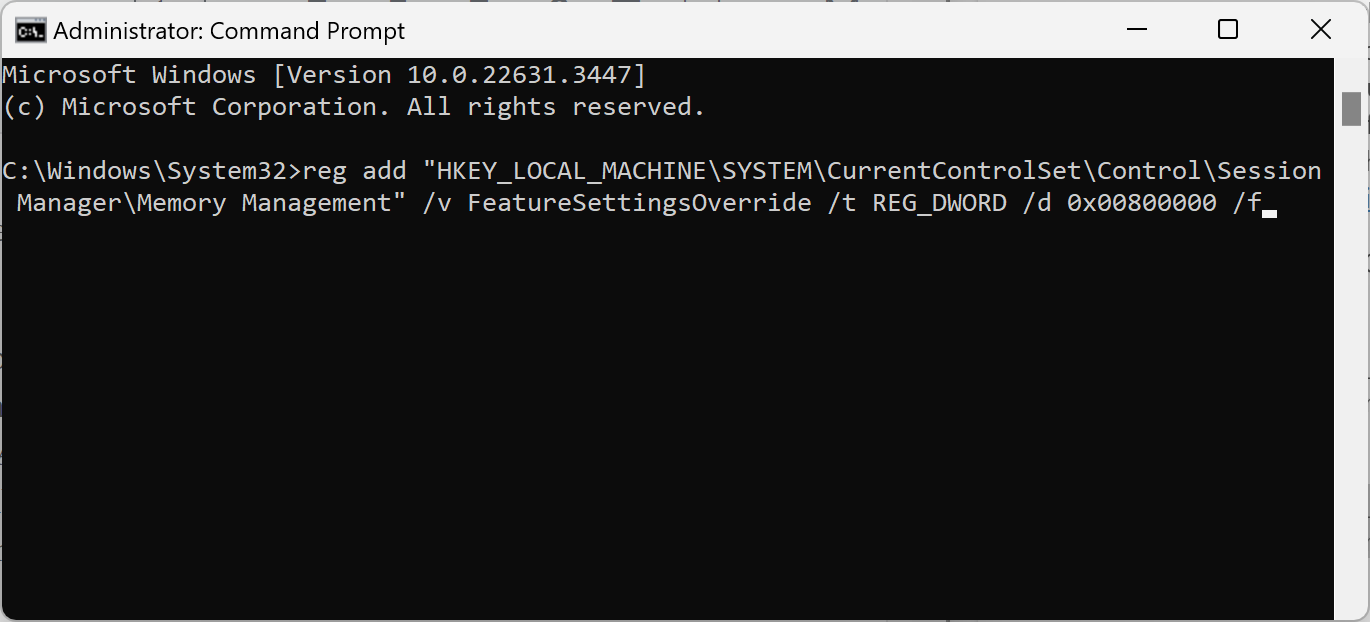
If your processor is on the list, you may change the Registry keys to enable the mitigations.
Note: implementation may affect performance. While I cannot recommend not enabling these mitigations, the risk of attacks against home PCs is most of the time neglectable.
Backup: it is highly recommended to back up the system drive before implementing the mitigation. Not with Windows' Backup App, which is useless for the purpose, but with a full backup program like Paragon Backup & Recovery Free.
Here is what you need to do on Windows devices and clients to mitigate CVE-2022-0001:
- Open Start, type CMD, and select Run as administrator. This launches an elevated command prompt window.
- Confirm the UAC prompt by selecting yes.
- Execute the following two commands by pasting them and pressing the Enter-key after each:
- reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverride /t REG_DWORD /d 0x00800000 /f
- reg add "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management" /v FeatureSettingsOverrideMask /t REG_DWORD /d 0x00000003 /f
- Restart the computer after both Registry keys have been added.
Tip: you may want to monitor performance to make sure that day-to-day operations are not severely impacted by the mitigation.
Interestingly enough, Microsoft has also revealed how Linux users may mitigate the vulnerability: "Specify spectre_bhi=on on the kernel command line".
Closing Words
While it may be critical for organizations to implement the mitigation, risks of attacks are relatively low for home users.
What about you? Have you implemented Spectre / Meltdown mitigations on your PCs? (via Neowin)





















Note that the intel list link only goes back to 2018 processors. Older ones, like sandy bridge 2nd gen Core i3’s are affected to some extent as well. They should have a patch out by now. Uknown if this would slow down your processor like some have reported in the past.
My XEON E5-1620 is not on the lists :-)
Martin, interesting use of “neglectable.” The word is archaic and practically useless; however, the way it’s used in the article wouldn’t be incorrect–maybe awkward for many readers when most writers would use “negligible.”
Other sites claim the flaw, “Affects most Intel CPUs since 2015.” I’ll just enter those registry hacky things and see what happens.
No, I think I’ll leave my registry alone.
I won’t enable it on any of my PC’s. Never felt the Spectre or Meltdown was that much of a real world attack vector.
Thanks for the article, Martin.
Forgot to mention that when I contacted Acer (the laptop is an Aspire V3-772G with an Intel Core i5 4200m CPU) about this mysterious machine and gave them the SNID they said the machine doesn’t exist even after using their own CPU identification app.
I bought it from Dixons in Amsterdam back in 2014 and at €850 it seemed a good deal at the time, but about six months later they went out of business in the Netherlands.
Still running Windows 8.1 Home after using GRC’s Never10 app to avoid the Windows 10 installation.
Whenever I’ve checked in the past and have tried to install the updates for my Haswell CPU it always results in the message “Processor unknown” and exits the setup.
Mitigate this, mitigate that, cripples the processor performance, then go buy a new/faster processor to do your work like a human being (aka spend more money). Thanx but no thanx.
Agreed. So many packages you have to install to “stay safe”. And some of them have their own impacts.
These mitigations should be enabled by default.
Thanks for the article! :]
No I won’t implement that. I think it is better to make an image once a week, sometimes more. I start Macrium with a bootable USB stick, then make the image. It never has let me down. But to each his own.