Find out if your Windows PC is affected by Meltdown/Spectre vulnerabilities
Meltdown and Spectre are designed vulnerabilities in modern processors that allow attackers to read virtual memory arbitrarily. What this means is that attackers may read the memory of computer systems to steal passwords and other sensitive data.
The researchers that found the bug identified three variants of it. The first two variants, "bounds check bypass" and "branch target injection" go under the name Spectre, the last, "rogue data cache load," under the name Meltdown. Both vulnerabilities are described on the official Meltdownattack website. Research papers are linked on the website as well.
Affected are processors from Intel, AMD, ARM as well as operating systems and other software programs.
Microsoft released an operating system update yesterday to address the issue. It is required however that hardware firmware and other software programs are updated as well to protect against the vulnerabilities. Mozilla released a fix for Firefox 57, and patches for the latest versions of Edge and Internet Explorer are available already as well. Google will patch Chrome when Chrome 64 gets released on January 23, 2018.
Microsoft created a PowerShell script that returns whether your Windows PC is still vulnerable or if you don't have to worry about the vulnerabilities at all.
Here is what you need to do:
- Load an elevated PowerShell prompt. Tap on the Windows-key, type PowerShell, hold down the Shift-key and the Ctrl-key and select the PowerShell entry to load it.
- Type Install-Module SpeculationControl
- You may get a prompt stating that "NuGet provider is required to continue." Select Y to accept that.
- You may get a prompt stating that you are installing an "untrusted repository." Select Y to continue.
- Type Import-Module SpeculationControl.
- You may get an error stating that "running scripts" is disabled. If you do, type Set-ExecutionPolicy RemoteSigned. Repeat the command Import-Module SpeculationControl.
- Type Get-SpeculationControlSettings.
Tip: You can restore the default ExecutionPolicy setting by running the command Set-ExecutionPolicy Default.
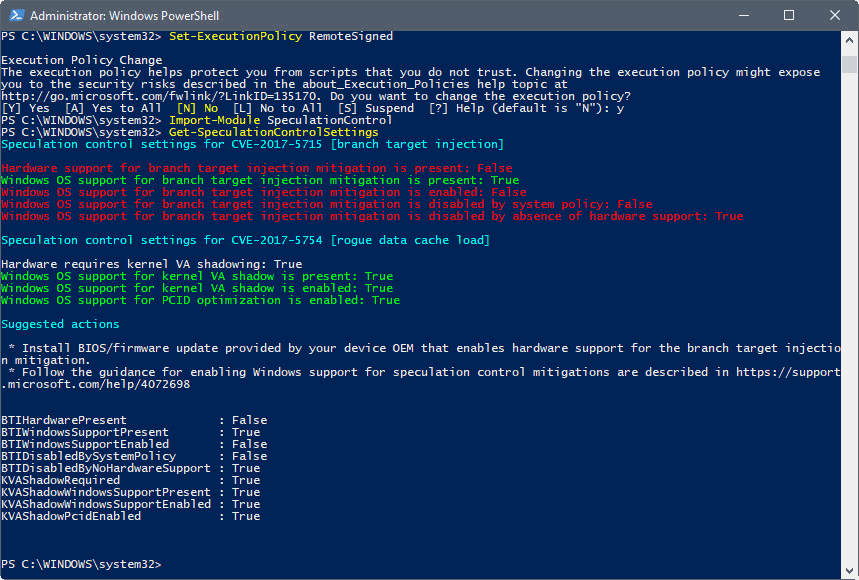
The PowerShell script displays information about the vulnerability and available (installed) mitigations at this point.

It is a bit hard to read, but true means that protection is available while false means that it is not. If you have installed yesterday's Windows patch already, you should see some "true" listings there.
The script lists suggested actions to mitigation the issues that are still active. It is required to install a BIOS/firmware update to address those. How that is done depends on the manufacturer of the device.
Microsoft published additional information here.



















To set the execution policy for current PowerShell session only (without affecting the registry), you can use this command:
Set-ExecutionPolicy -Scope Process -ExecutionPolicy RemoteSigned
This command does not affect the value in the registry. The variable and its value are deleted when the current session is closed.
@kronos & @MARTIN:
This would be a really useful change to implement to the article’s instructions. I checked my dad’s three laptops for Meltdown/Spectre vulnerabilities just yesterday, and I almost forgot to reset PowerShell’s execution policy to default on one of them. (I was doing a lot of other software maintenance on all three computers, hopping from one to the next to minimize downtime while an install, update, scan, or reboot proceeded. I was probably lucky that this was the *only* thing I almost forgot.)
By the way, the Lenovo ThinkPad X1 Yoga (with a Skylake chipset, I believe) running Windows 10 passed the test, and the Dell Latitude E6510 and E6500 (with much older chipsets) running Windows 7 need new BIOSes/firmware. The Latitudes are relatively durable “business-class” laptops that are still working fine, but they’re getting old. It will be interesting to see whether Dell issues updated BIOSes for them. My personal observation is that Dell issues firmware and driver updates for Latitudes considerably less often and for a shorter period of time than Lenovo does for ThinkPads.
MARTIN:
In step 6, I think you need to change “Import-Module SpeculationChannel” to “Import-Module SpeculationControl”.
Wow, you are right. Sorry for that and thanks for letting me know.
No worries, Martin — it did no harm and it was easy enough for readers to figure out. I myself make that kind of whole-word-substitution typo increasingly often, possibly because my mind jumps ahead to the next thought while I’m still typing, my fingers go on auto-pilot, and their speculative-execution cache contains the wrong data. ;-)
By the way, the “corrected” PowerShell commands worked fine for me, although as a first-time PowerShell user it did take me a second to figure out that of all of the PowerShell items returned by the Start Menu search, it was plain old “Windows PowerShell ISE” that I wanted and not the (x86) or Modules items.
Unfortunately, I will apparently need an updated BIOS and firmware for full mitigation and I’m not confident that Lenovo will provide them for an 8-year-old laptop, even though it’s a ThinkPad T-series. But my laptop also has the Intel Management Engine vulnerability, so the more, the merrier, right? *Sigh*
@A Different Martin – I did this, since I was getting an error on SpeculationChannel (“SpeculationChannell was not loaded because no valid file was found”). However, no results… just the cmd prompt (C:\WINDOWS\system32>) reappeared.
Resolved with re-running the commands yet again, as Martin B suggests immediately above.
Odd… I’m not getting past Import-Module SpeculationControl.
It gives me:
“Import-Module : The specified module ‘SpeculationControl.’ was not loaded because no valid module file was found in any module directory.
At line:1 char:1
+ Import-Module SpeculationControl.
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : ResourceUnavailable: (SpeculationControl.:String) [Import-Module], FileNotFoundException
+ FullyQualifiedErrorId : Modules_ModuleNotFound,Microsoft.PowerShell.Commands.ImportModuleCommand”
Anyone got a clue as to what goes wrong here?
Try re-running all commands. It seems that the download or integration was not successful.
Great article. I’ve done all the updates (bios etc) for my i7-8700k Asus-Z370 Win10 system but still have two unresolved issues listing as “False”, they are:
BTIDDisabledBySystemPolicy :False
BTIDDisabledByNoHardwareSupport :False
Any idea what these are and how they can be fixed? Or is it something which will have to come in a future bios or windows update? I’ve tried googling but it didn’t turn up much. Thanks.
The vulnerability can only be fixed if software and hardware are patched. You need to wait for the hardware manufacturer to release an update as well.
Question: Does the above apply to Windows 7 (Ultimate, X64, on a 2008 Tosh Satellite w/Intel)? I had same prob as Anonymous Nobody, top. I’ll send something in any case: VISA ok? This is so educationamal for a neophyte like moi. You guys keep my attention w/out cursing. You’re literate. 3rd such site I found today. Intelligence trending, or did I just get lucky?
I think this is the list of motherboards ASUS will update with the Intel fix:
https://www.asus.com/News/V5urzYAT6myCC1o2
Looks like my motherboard is already not in support.
I think many will be left vulnerable.
The vast majority of systems currently in use will not be patched. You’re out of luck if you’re using something more than 1-2 years old, and 2 is even stretching it. Extreme pressure would have to be put on these manufacturers to get them to do anything about systems older than that.
Ryzen is also reported to be affected by at least one of the three issues. So don’t be too smug.
Only Meltdown causes real performance loss and it only affects Intel. AMD has already released patches for Spectre, but those don’t cause drops in performance.
… So yeah, feels good to be on Ryzen. :P
Man it sure feels good to be Ryzen.
Is my backup laptop/pc 2006 Intel Core 2 Duo CPU HP Pavilion affected? Good thing I dont often upgrade my pc, last I bought was their 2nd Gen i7 CPU(2010/11) w/c sadly is affected….
Probably gonna move to AMD when I get a new powerbox pc and ditch the vulnerable 2010-2017 CPU’s.
There’s no CPU that isn’t affected, including AMD.
ADWcleaner and Rogue Killer are good scanners to use to clean out a system, after cleaning out all system temp files. Rogue Killer is slow as molasses, and might cause some people to lose patience.
And for Ubuntu LINUX PCs?
Anything we can/should do?
Thks!
Ubuntu users can expect updated kernels by the original January 9, 2018 coordinated release date, and sooner if possible.
https://insights.ubuntu.com/2018/01/04/ubuntu-updates-for-the-meltdown-spectre-vulnerabilities/
Thanks f/the quick reply, JoHN5.
The UBUNTU tech folks
will update 64-bit versions 1st (Jan 9…),
and later (HOPEFULLY SOON!),
will update the 32-bit versions of Ubuntu.
(no ETA for that yet).
We have a slew of PCs
running 32-bit UBUNTU just fine
but cannot afford to change all our hardware
to run 64-bits…
SO, hoping for soon…
My prospects are undesirable for the time being, the latest update for the UEFI from the manufacturer of the computer I use is from last year
many thanks for bring this to our attention Martin
“vulnerabilities in modern processors”
First I don’t even know from what time a processor is called “modern”.
@Lee
No, it can’t be fixed with Bios and firmware. The only way is to flush the CPU micro-code and re-install new code, which of course can’t be done by users.
ASUS has not released a BIOS update for my board yet :(
My ASUS laptop does not have a firmware fix available either, as expected. I have an unanswered request for more information awaiting ASUS response.
This has nothing to do with Bios and can’t be fixed by firmware update.
To be fixed you need a new CPU (for your PC, Smartphone, Tablet, SmartHome device..), without a bug, None is available, and won’t be for a long time.
Those OS patches are just circumventing the bugs, not fixing anything.
And yes, it can be fixed with BIOS and firmware updates. In fact, that is the ONLY way to fix it.
There is no CPU to purchase that is not affected, and it will probably be five years before one hits the market. Good luck.
https://www.asus.com/News/ last dated 2018-01-05 simply says “ASUS is aware that the current Intel® microcode version might be subject to recently identified security vulnerabilities.” ( Stay tuned….)
How come the nuget repo is untrustworthy, if this is a script written by Microsoft?
Maybe it’s an unstable/testing repo.
What does that have to do with SSL Certificates?
Indeed
For people having issues getting step 6 to work, specifically with “Set-ExecutionPolicy RemoteSigned” command, you can follow instructions below to set it using Group Policy Editor.
https://stackoverflow.com/questions/27753917/how-do-you-successfully-change-execution-policy-and-enable-execution-of-powershe
The matter of PCID is curious here, where I know a given CPU has it (e.g. i5-2500k), and tools like Coreinfo show that it’s there, but this script shows that line as False (and SpecuCheck, a similar utility to MS’s script, agrees).
Will the command “Set-ExecutionPolicy RemoteSigned” make a permanent change or a temporary one?
If it’s not temporary, how do we disable the running of scripts again?
I think (not confirmed) you should be able to run “Set-ExecutionPolicy Bypass -Command Import-Module SpeculationControl” for a temporary alternative.
Ignore my previous comment if it doesn’t work, but this command below should only make a temporary change until you close the Powershell window, still not confirmed to work in the articles context though sorry.
Set-ExecutionPolicy Bypass -Scope Process
You can restore the default value with the command Set-ExecutionPolicy Default.
Thanks for the reply.
FYI: As others have commented, even though I subscribe to “Replies to my comments” in the drop down below, and enter a valid email, I never get any notifications.
The NY Times is suggesting that people run an ad blocker for Meltdown/Spectre.
========
What should I do as a consumer?
Keep your software up-to-date. That includes your operating system and apps like your web browser and antivirus software. Microsoft, Mozilla and Google have already released patches for Internet Explorer, Firefox and Chrome to help address the problem.
Installing an ad blocker on your web browser is also a safeguard, according to security experts. Even the largest websites do not have tight control over the ads that appear on their sites — sometimes malicious code can appear inside their ad networks. A popular ad blocker among security researchers is uBlock Origin.
“The real problem is ads are dangerous,†said Jeremiah Grossman, the head of security strategy for SentinelOne, a computer security company. “They’re fully functioning programs, and they carry malware.â€
https://www.nytimes.com/2018/01/04/technology/meltdown-spectre-questions.html
You may need to update to a newer version of PowerShell first. I ran the script on a Windows 10 machine and it worked fine on it. See: https://docs.microsoft.com/en-us/powershell/scripting/setup/installing-windows-powershell?view=powershell-5.1
1.
You have to uninstall Win Mgmt Framework
wusa /uninstall /quiet /kb:2506143
https://docs.microsoft.com/en-us/powershell/wmf/5.1/install-configure
2.
Install WMF 5.1
Download and install WMF 5.1
https://docs.microsoft.com/en-us/powershell/wmf/5.1/install-configure
3.
Run the save
Save-Module -Name SpeculationControl -Path
and run the install
Install-Module -Name SpeculationControl
Installed latest PS 6.00RC on Win8.1-64, same “The term ‘Install-Module’ is not recognized…” problem
Maybe Win10 only?
Oops, wasn’t running PS 6. Have to explicitly ask for 6, just running PowerShell runs the old one.
Yes, PS6 works this on Win8.1-64
On Windows 7 Ultimate it returns this
The term ‘Install-Module’ is not recognized as the name of a cmdlet, function, script file, or operable program. Check
the spelling of the name, or if a path was included, verify that the path is correct and try again.
At line:1 char:15
+ Install-Module <<<< SpeculationControl
+ CategoryInfo : ObjectNotFound: (Install-Module:String) [], CommandNotFoundException
+ FullyQualifiedErrorId : CommandNotFoundException