
Data Can Leak From Partially Encrypted Systems
A bunch of researchers, among them the famous Bruce Schneier, have discovered that features like Recent Documents list may reveal information about files on an encrypted partition even when used in conjunction […]

Gmail Has a Privacy Problem
You might have already read elsewhere that it is possible to reveal the real name of any Gmail user by sharing a calendar in Google Calendar with him. Let me explain how […]

Update on my PayPal Story
I noticed in the beginning of July that someone else transferred most of the money that had been in my PayPal account to an online hoster to buy six month access to […]
Gmail And Yahoo Mail Users Now Protected Against eBay And PayPal Phishing Mails
The award for the longest title ever could go to this one. But it's good news actually. Both Email services are "supporting email authentication standards including DomainKeys and DomainKeys Identified Mail (DKIM) […]
Overview of Online Virus Scanners
Scanning the computer from an online location provides several advantages over the classic local scan. The most prominent one is that the risk of a virus infection of the virus scanner is […]
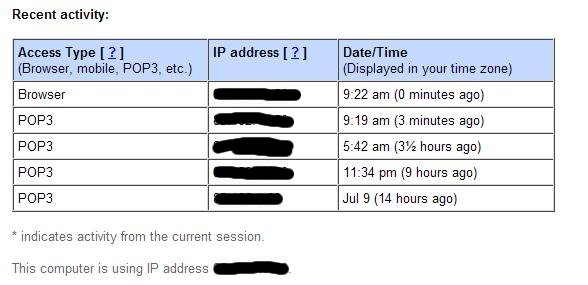
Tracking Gmail Account Usage
Google Mail introduced a new feature recently that can be helpful in finding out if someone else has or had access to your Gmail account. The function is a bit hidden in […]
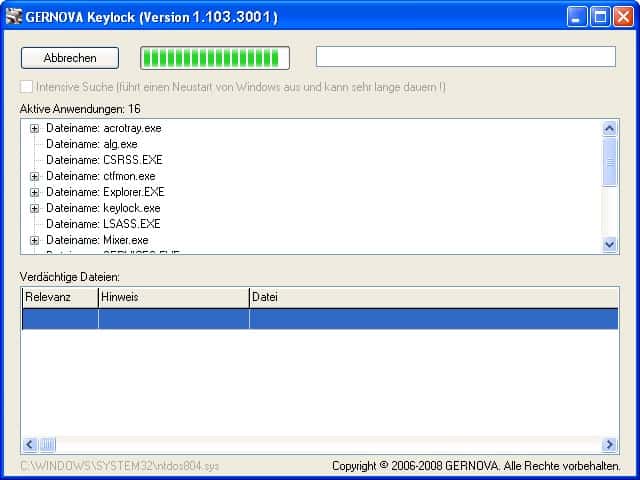
Gernova Keylock
Gernova Keylock is a specialized software to detect keyloggers on a system. Keyloggers are used to log user input which includes urls that the user enters as well as usernames, passwords and […]

Are you running the latest browser version?
In a recently released research paper Stefan Frei, Thomas Dübendorfer, Gunter Ollmann and Martin May analyzed Google Search Engine logs between January 2007 and June 2008 to understand web browser security. The […]

Unauthorized Payment Done With My PayPal Account
I usually check my emails right after I wake up and received a PayPal email receipt this morning that told me that the amount of $480 was transferred from my account. I […]
Haute Secure
The Internet can be a dangerous place. Especially for those users who do not care but simply use the computer. A click on the wrong website and the computer can be infected […]

You better stop using Internet Explorer for now
A security vulnerability came to light recently that affects Internet Explorer 6, Internet Explorer 7 and even Internet Explorer 8 that can be exploited to record keystrokes users even when that user […]

British Telecom Phorm report leaked
An internal British Telecom document was released two days ago on the Wikileak website that provides the results of British Telecom's validation of Phorm, also known as (aka 121Media) Deep Packet Inspection. […]
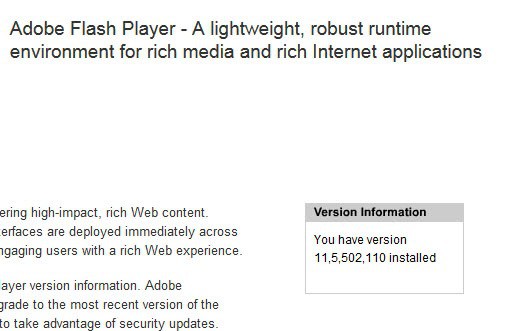
New Information about latest Flash Vulnerability
A report about a new Flash vulnerability that affected the latest two versions of Adobe Flash was spreading like fire on the Internet yesterday. The Flash Vulnerability was used on specially prepared […]

Use Netflix Watch Now on more than 3 PCs
Each Netflix subscription gives users access to a small movie library that can be accessed instantly from up to three PCs. All subscription plans except for the cheapest one include unlimited hours […]
Read 20 Digital Magazines for Free
Apple Iphone owners get more. They get free Wireless access at AT&T Hotspots, which no longer is that easy to defeat and now they also get to view free digital magazines of […]

AntiPhorm Software
One form of data mining is behavioral targeting which means that ads are served that fit into the surfing pattern of a user. Spending your time on teen forums will deliver advertisement […]

Select a country for your proxy
Finally an innovative proxy website. Web Proxies are all alike, mostly. They use the same four of five proxy scripts that are available, may have a slightly different design and tend to […]

Spy Tech: I see what you write
Two new techniques to spy on computer users have been revealed these days by two independent scientific studies conducted at the University of California, Santa Barbara, and at Saarland University in Saarbrucken, […]

Protect your data when travelling to the US
I personally think this is outrageous. Border Agents in the United States can not only search your laptop, mobile phone or any other electronic device that you might be carrying while traveling […]

Microsoft Security Updates May 2008
Microsoft released four security updates for various applications and operating systems that they produce. Three of the four updates are regarded as critical while one has a moderate risk level. To break […]

Another Antivir free premium promotion
Polymath send in the tip that another Antivir promotion is available that gives users access to Antivir premium for 180 days free of charge. The promotion form is available in English and […]

Computer Online Forensic Evidence Extractor
The Computer Online Forensic Evidence Extractor (Cofee) is a USB thumb-drive developed by Microsoft that was distributed to more than 2000 law-enforcement officers in 15 countries including the United States, Germany, New […]

Microsoft updates two critical security patches
It feels like I'm updating my computer every day in the last weeks. Microsoft issued yet another two security patches for Internet Explorer and the .net framework that can be downloaded from […]
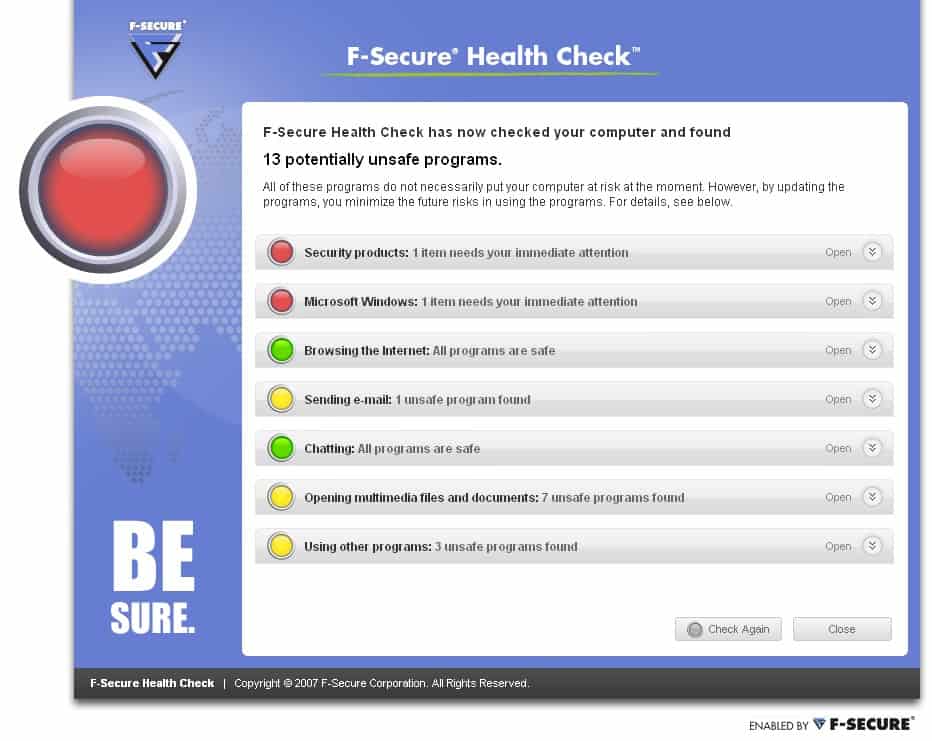
F-Secure Health Check
Many companies are producing tools that scan the computer for security vulnerabilities. Some provide their functionality on a website while others are applications that have to be installed on the computer. F-Secure […]

PayPal to Block Unsafe Browsers
If you run an old version of a browser attacks on it are more likely to succeed I think we can all agree on that. Recent browser versions include fixes for security […]
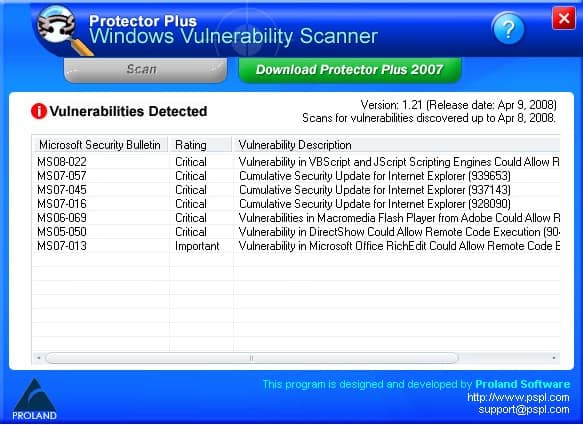
Windows Vulnerability Scanner
Windows is probably the operating system that is attacked the most, some say because it has the largest user base, some say because it is simply insecure. Whatever the reason may be, […]

Is Your ISP Injecting Ads on websites you visit?
Internet users have to cope with all kinds of things when they are online. Malware, security vulnerabilities, tracking, phishing, traffic shaping and some, as it seems (thanks Dante for the link), even […]
Avira AntiVir Personal 8
Avira AntiVir Personal 8 was released today and I thought it would be nice to write about this new release since AntiVir is one of the most popular free antivirus applications available. […]
Test my PC Security
Is your computer secure? Is the firewall that you have installed working properly? Those questions are rather hard to answer even for users with lots of PC experience. Many users simply use […]
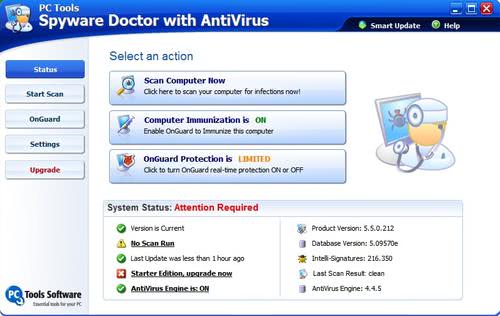
Free Spyware Doctor 5.5 Starter Edition
The security tools developers seem to be in a race currently to throw free versions of their products on the market in an effort to increase market share and brand awareness. The […]
Avira AntiVir Rescue System
Users looking for rescue systems distributed on CDs or DVDs have really no shortage of finding one. The major problem that inexperienced users face is the same that they face when asked […]

German interior minister's fingerprint replicated
What's a good way of catching the attention of someone who is advocating the use of biometrics? German interior minister Wolfgang Schäuble is pushing biometrics and data collection in Germany all for […]
Hide Antivir Scans, Updates and Advertisement
You might remember that I'm not a huge fan of antivirus software and have none installed on my computer. While some call this foolish it does make sense for me. I did use Antivir for some time to check it out and see what it can do and think it is a fine piece of security software. What bothered me a lot were the update windows and daily scheduled scans that would pop up in inappropriate moments.
Virus Total Uploader
Virus Total is one of the many services that let you upload files to their server which are then scanned for viruses and malware. One major advantage of Virus Total over a single antivirus solution installed on the user's pc is the fact that it uses almost every known antivirus engine to scan the files which could not be done on a single system because those applications would surely interfere with each other.

Real Player Internet Explorer vulnerability
Internet Explorer with an installed version of Real Player beware. A vulnerability has been discovered recently which could allow remote code execution. According to Zdnet users should either switch browsers for the […]

Microsoft Security Bulletin March 2008
Microsoft released their monthly Security Bulletin yesterday which consisted of four critical issues all affecting various editions of Microsoft Office. All four patches fix remote code execution vulnerabilities and it is recommended that they are installed as soon as possible if Microsoft Office is installed on the computer.

Say no to Drugs Virus
I received an email today from a reader who told me of a problem that he encountered lately on his computer. The message Say no to drugs appeared whenever he clicked on a shortcut to the My Documents folder. This sounded clearly like a virus and a quick search revealed that it indeed was the I Love Her virus.

Defeating Disk Encryption
I discovered an interesting video at Hack a Day from the University of Princeton demonstrating how to break disk encryption using so called RAM Dumps. This basically takes into account that the encryption key is stored in RAM. While most disk encryption mechanisms are vulnerable while the computer is on or in sleep mode some are even vulnerable when powered off.
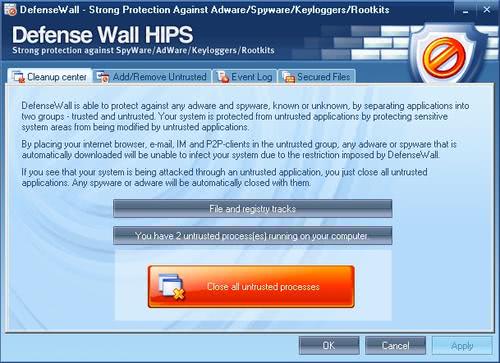
DefenseWall HIPS
I have been in contact with the creator of the excellent DefenseWall HIPS application for some time now and he was so nice to give away ten copies of his software to Ghacks readers. Let me first explain what the software does. DefenseWall HIPS is a Host Intrusion Prevention System that uses sandboxing and virtualization to protect the computer from dangers that are not stopped by anti-virus applications.
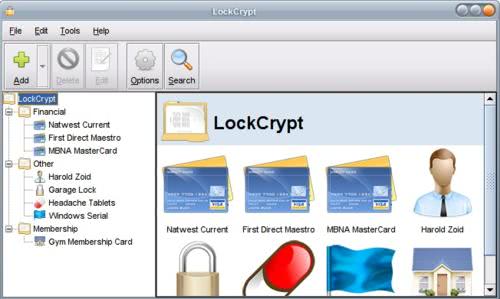
Lockcrypt Password Safe
Where do you store your usernames and passwords ? In a text document on your computer ? In your wallet ? Storing sensible information like passwords, but also other type of data like information about medication or credit card numbers, unencrypted is a security risk. If someone is after those information he immediately knows how to use them against you.

