
ePassports Make Terrorist Dreams Come True
Did you notice that many governments who are very keen of introducing new electronic means of identification have virtually no idea of what they are actually introducing? They claim it will make […]
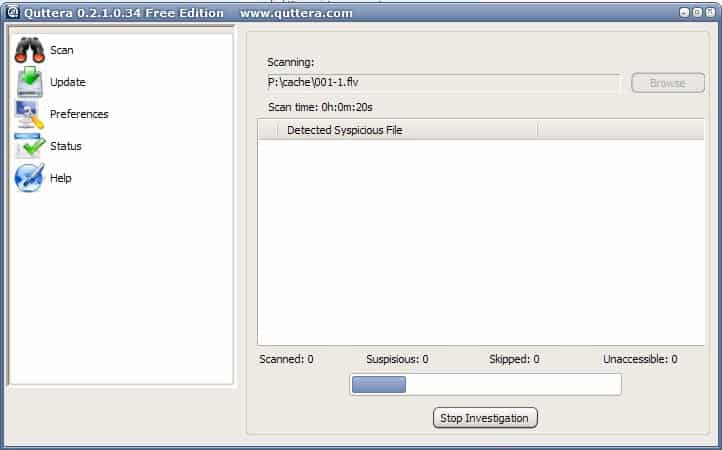
Computer Virus Protection Quttera
Quttera is not your usual computer virus protection program. It will only protect the computer from viruses spread in multimedia or data files including but not limited to audio, video or text […]
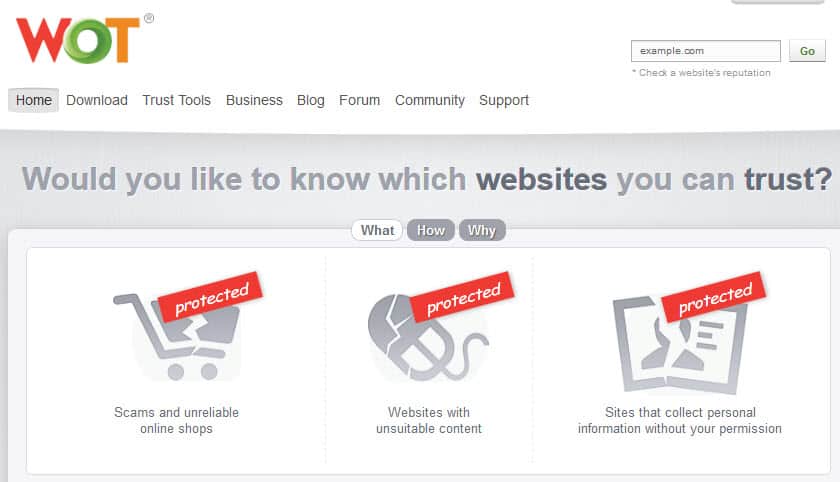
Web of Trust: collaborative online security
Most systems which warn of unsafe websites, like OpenDNS and Google, work in mysterious, non-transparent ways and websites are often deemed as unsafe for reasons other than safety. Web of Trust is […]

New Google Mail Security Vulnerability Emerges
News about domain hijackings came to light in the last weeks. The commonality was that all victims were using Google Mail as the primary email address of their websites. Yesterday a proof […]

PayPal Mobile Security Keys
VeriSign sent me a free PayPal Security Key after I mentioned that an unauthorized payment was done from my PayPal account. The security key acts as a new layer of defense as […]

US Military Bans Removable Media To Stop Computer Worm
The online edition of the computer magazine Wired has published an article three days ago about a ban of removable media by the US Military to stop a computer worm from spreading […]
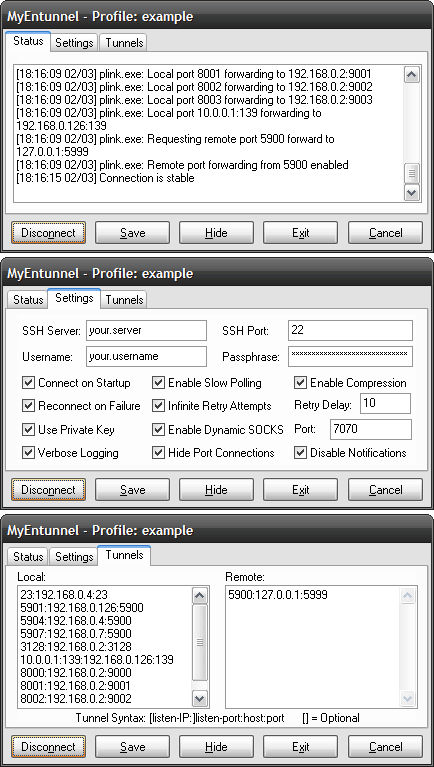
My Encrypted Tunnel
My Encrypted Tunnel is a basic System Tray application that can be installed as a Windows Service to establish and maintain TCP SSH tunnels. Here is a short explanation of what SSH […]

Ask The Readers: Recommended Security Software
We have been writing about great free software programs for more than three years now here at Ghacks and it is finally time to create a list of programs that we can […]

Used Hard Drives Still Haven For Identify Theft
Sellers are currently offering 3807 used hard drives on eBay.com alone. Add 5303 used desktop PCs, 975 Apple Desktops and thousands of other used devices like digital cameras or mobile phones that […]

Of Cracks, Hacks And Jailbreaks
What a day. It started with news that hackers managed to circumvent controls in the T-Mobile G1 Android mobile phone that allowed them to install new programs and even a new operating […]

Hacking Horror Story…
Joe’s post today was about the importance of backing up your blog, and it’s something which I now realize can never be taken too seriously - only this week another website I […]

Another USB Stick With Important Data Lost In The UK
Living in the United Kingdom has one major downside which became apparent recently. The government likes to collect all sorts of data about citizens and visitors but seems incapable of securing that […]
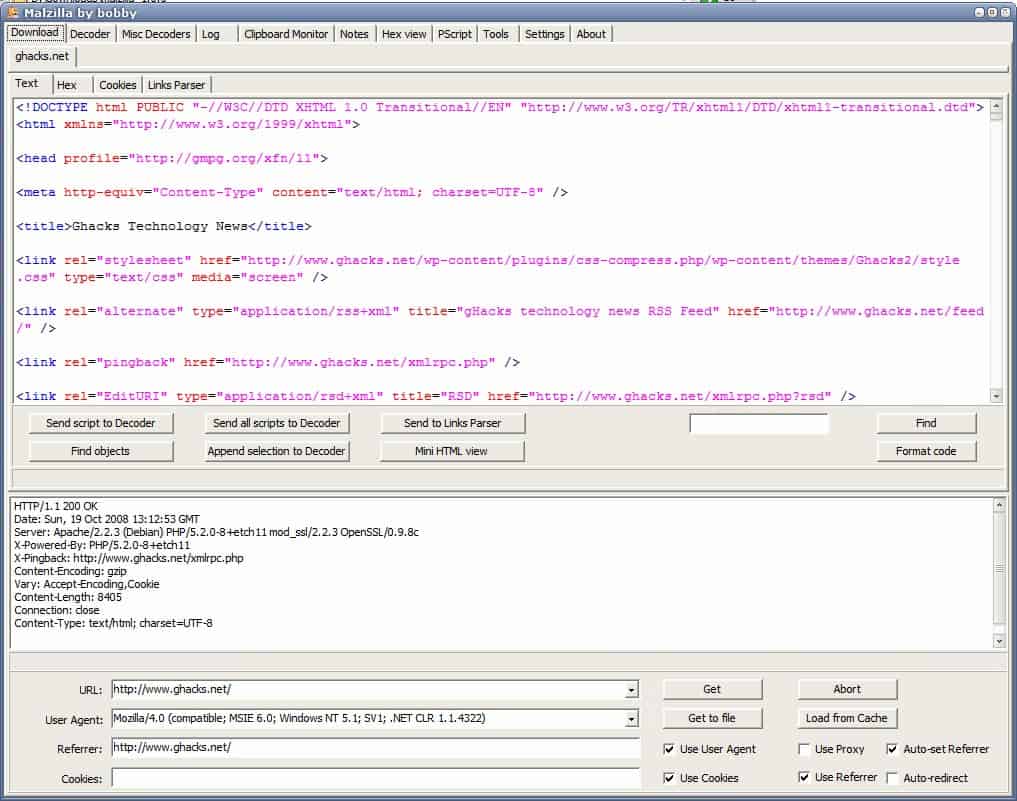
Identify And Analyze Malicious Webpages
Update: Malzilla hs not been updated since 2008 which indicates that the project has been abandoned by its developers. While still available for download, it may not be up for the task […]

Apple Might Be Watching You
What is good customer service? Customers would usually state that good customer service means fast and effective solutions for difficulties with a product of a company. What about a company that actively […]
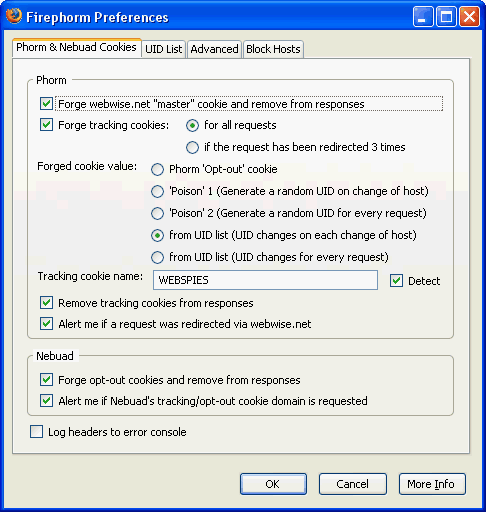
Firephorm - the anti-phorm Firefox extension
We have covered Phorm before here on Ghacks. It is a very scary cooperation between several Internet Service Providers and advertising companies. The Internet Service Providers install tracking cookies on user systems […]

Right To Search Laptops To Be Limited On US Borders
The right of US border guards to search the laptops will be limited today according to a news post on the Internet news site Vnunet (article no longer available). The current policy […]
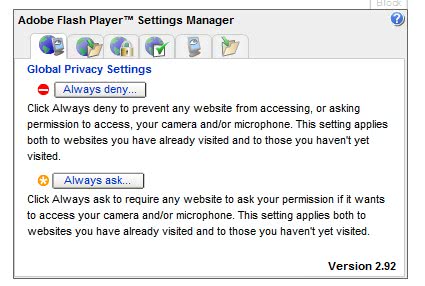
Adobe Flash Player Clickjacking Vulnerability
Dante send me a link to an interesting article that describes the latest Adobe Flash Player vulnerability. Adobe published a security advisory yesterday that describes a clickjacking vulnerability. In short: An attacker […]

Time To Look For A Skype Alternative
The voice over IP client Skype never got off of the radar of privacy activists. There were always rumors about backdoors in the voice communication software and that several organizations were allowed […]

The Brits Surely Know How To Spread Confidential Data
Living in the United Kingdom surely has its bright sides: you got the IT Crowd, Cider and James Bond. On the downside, British government officials have been known for their lax data […]
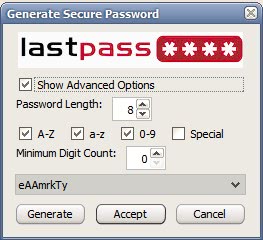
One Password Management Software To Rule Them All
Choosing secure passwords is important to protect the user accounts from being accessed by unauthorized users. The problem that arises for all users is that secure passwords are harder to remember. Writing […]

PeerGuardian Error Contacting URL
PeerGuardian is an IP (Internet Protocol) blocker for Windows which is highly popular in the file sharing community but also with security and privacy interested users. The software works by providing access […]

The iPhone Home Button Is A Security Risk
Now that makes for an interesting opening. When a user taps the iPhone's home button it shrinks and disappears which is a nice looking effect. The problem is that the iPhone is […]

Windows Security Updates September 2008
Microsoft has released four Microsoft Security Bulletins for September 2008. All updates are rated critical and it is recommended to update the computer system running Windows operating systems or Microsoft software as […]
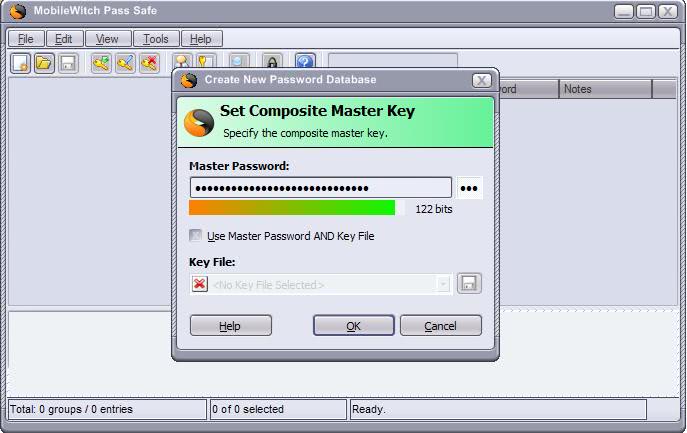
Password Software
Keeping track of all the different user accounts, passwords, security questions and emails associated with them is quite a daring task. Some users create all accounts with the same data, while others […]
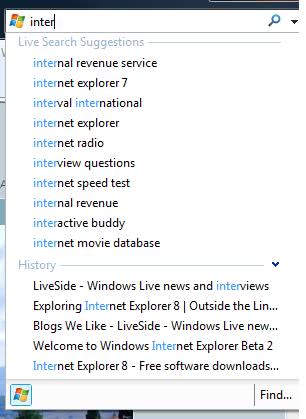
Take Back Your Privacy By Disabling Auto Suggest In IE8
The fact that Google Chrome is sending information about anything that the user types into the Google Chrome Omnibox seems to have caused quite a stir on the Internet with reports about […]

Hacker Breaks into FEMA Phone System, Makes $12,000 Worth of Calls
I just came across an amusing news excerpt about the Federal Emergency Management Agency or FEMA, which is a part of Homeland Security. For those of you who don't know, Homeland Security […]

Freedom Stick Is Better Than Freedom Fries
No, I'm not referring to something called French Fries that has been renamed to Freedom Fries to punish the French for not siding with the US in the country's war against terror. […]

A New Vulnerability Discovered in μTorrent
As far as file-sharing protocols go, BitTorrent has emerged as one of the leading P2P technologies being used. μTorrent is one of the most popular BitTorrent apps around, largely because of its […]

Microsoft August 2008 Security Updates
Microsoft has just released the security patches of the August 2008 Patch Day, a total of eleven updates for various Microsoft operating systems and products that are recommended updates. Six of the […]

Apple Can Remove Apps From iPhones
The public outcry would be loud and ear-deafening if someone would have discovered that Microsoft was able to remove installed applications from a Windows operating system. But it is Apple this time […]

Customs Proofing A Laptop
I Discovered the article Security guide to customs-proofing your laptop over at Cnet and thought it would be worth sharing it. It does not really add anything new to the discussion and […]
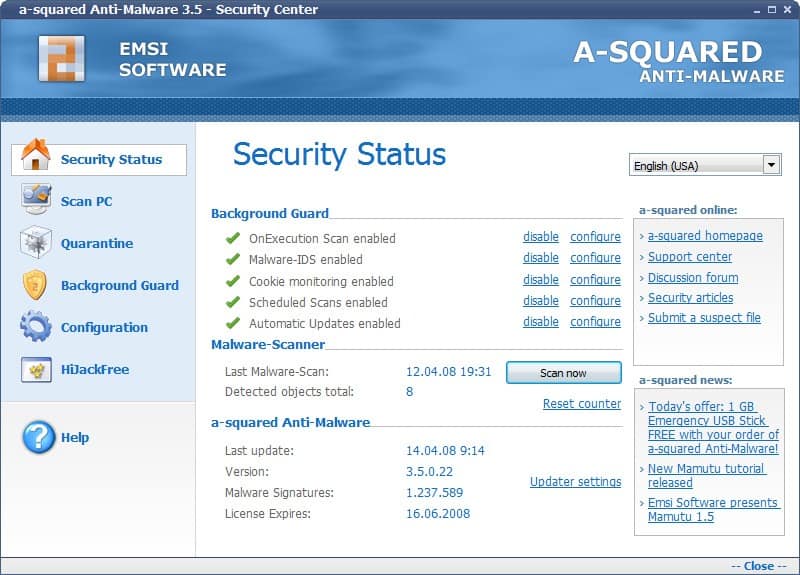
Free A-Squared Anti-Malware
The Giveaway of the Day website is offering some very nice software packages from time to time. Today's offer is A-Squared Anti-Malware in version 3.5 from Emsisoft which can be freely downloaded […]
New Phishing Emails Emerge
The usual phishing email still claims that "action" is required because of something that just happened. This can be a fake eBay purchase, PayPal transfer, a bank account transaction or someone offering […]

New Attack: Combine Files With Jar Scripts
A new attack, dubbed Gifar by their creators named after the two file types that they mixed to create the attack (Gif and Jar), was mentioned in a Black Hat Sneak Preview […]
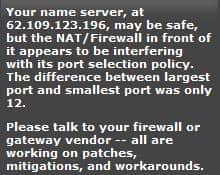
Check If Your DNS Is Vulnerable
Humans are not good with numbers. At least not many are. That's why the DNS, the Domain Name System, is in place. It translates the addresses that we enter in the browser […]
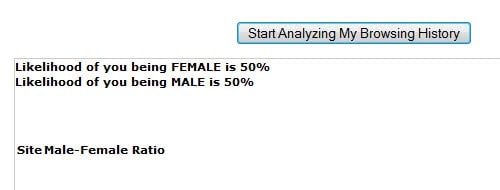
Male or Female? Your Browser's History Might Tell
A website should not be able to read the the history of websites that a visitor to the site has visited previously in the web browser. An ingenious CSS hack and some […]

42 Kilobytes Unzipped Make 4.5 Petabytes
In 2001 reports about Zip Bombs or Zip of Death attacks made the round on the Internet and I thought it would be nice to write about one shiny harmless example of […]

Skype Backdoor Speculations
The well respected German website Heise Online has fueled speculations about a backdoor that is implemented in the Voice over IP software Skype. According to Heise the Austrian interior minister revealed at […]

Protect PayPal Accounts With VeriSign Identity Protection Devices
I had a rather unpleasant experience with PayPal lately where someone transferred all the money from my account. PayPal was not very forthcoming and I do not know until today how this […]

Data Can Leak From Partially Encrypted Systems
A bunch of researchers, among them the famous Bruce Schneier, have discovered that features like Recent Documents list may reveal information about files on an encrypted partition even when used in conjunction […]

