
How To Download Files From The Internet The Secure Way
Everyone who uses an Internet connection is downloading files from there. It can be automatic file transfers like downloading new emails or filling the browser cache when opening new websites but also […]
Recover Computer System After Malware Infection
Update: The program IClean has last been updated in 2007. While it may still work on your system, it is highly suggested to user a different program for the job. You can […]

Password Recovery Questions Make Online Accounts Vulnerable
Password recovery questions are great to recover a forgotten password in a matter of seconds. All that needs to be done is to answer the password recovery question to receive a new […]
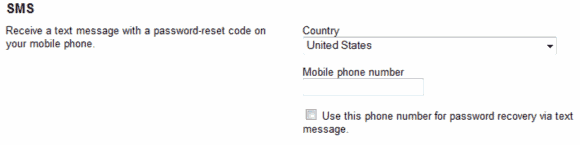
Secure your Google account with your mobile phone number
A Google account offers access to numerous popular and often times important services. This includes access to the popular Gmail email service, Google Docs for storing documents but also access to Google […]

Download Microsoft Security Essentials
You might have been one of the lucky ones who were able to download the beta of Microsoft antivirus software program Security Essentials. Chance is you missed the opportunity as Microsoft has […]

Antivirus Software Microsoft Security Essentials Tested
Microsoft has released a public beta of their new antivirus software Security Essentials a few days ago. The beta was limited to 75000 participants, a number that was reached quickly considering that […]

Adobe Fixes Critical Shockwave Vulnerability
Adobe has issues a security patch for the Adobe Shockwave software program that fixes one vulnerability that has been rated critical by Adobe Software. The vulnerability gives attackers, who can attack systems […]
Microsoft Security Essentials Beta Now Available
Microsoft has made available a public beta version of their new free antivirus software program Microsoft Security Essentials which was formerly known as Morro. The antivirus software is available for 32-bit editions […]
MSN Live Messenger Antivirus Script WLM Safe
Update: Windows Live Messenger has been discontinued by Microsoft and replaced with Skype. Windows Live Messenger, which is also called MSN Live Messenger or just MSN, is one of the most popular […]
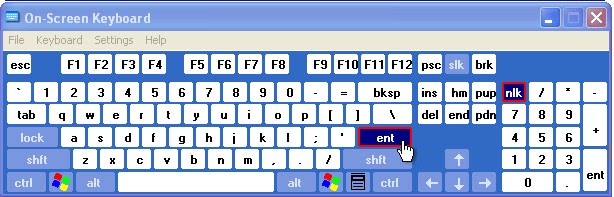
Computer Security Myth: Defeating Keyloggers With Onscreen Keyboards
I recently read a few articles that gave readers the tip to use onscreen keyboards to defeat keyloggers installed on the computer system. The idea behind the tip is to prevent that […]
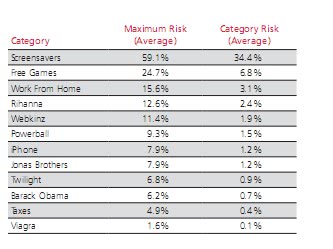
The Most Dangerous Web Search Terms
Which search terms would make it on the list if you would have to compile a list of the ten most dangerous web search terms? Most users would probably add search terms […]

Laptop Theft Recovery Software Prey
Prey is a program and service for desktop and mobile operating systems that enables you to keep track of the devices the software runs on. There are a few things that laptop […]

What You Should Do After Buying A New Computer System
Dante send me a link to another "malware found on purchased laptop" story. The new M&A Companion Touch netbook did not ship with one or two malicious programs, no a total of […]
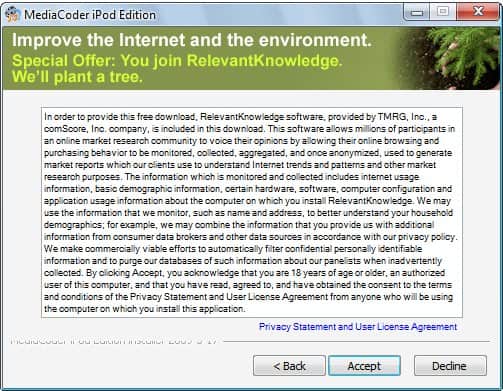
About Relevant Knowledge
Relevant Knowledge came to my attention for the first time when Transcontinental mentioned that the latest version of the popular software updater SUMO contained the software as an optional component. I soon […]
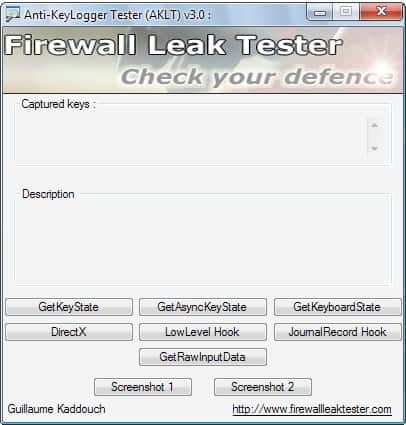
Anti KeyLogger Tester
Anti-KeyLogger Tester is a free program for devices that run Microsoft's Windows operating system to test the PC's anti-keylogging protection. Key Loggers are one of the most dangerous threats that computer users […]

How to wipe a dedicated server before you stop renting it
System administrators may not have physical access to dedicated servers, especially when it comes to hosting websites on the Internet using servers. These servers are usually hosted by a web hosting company […]
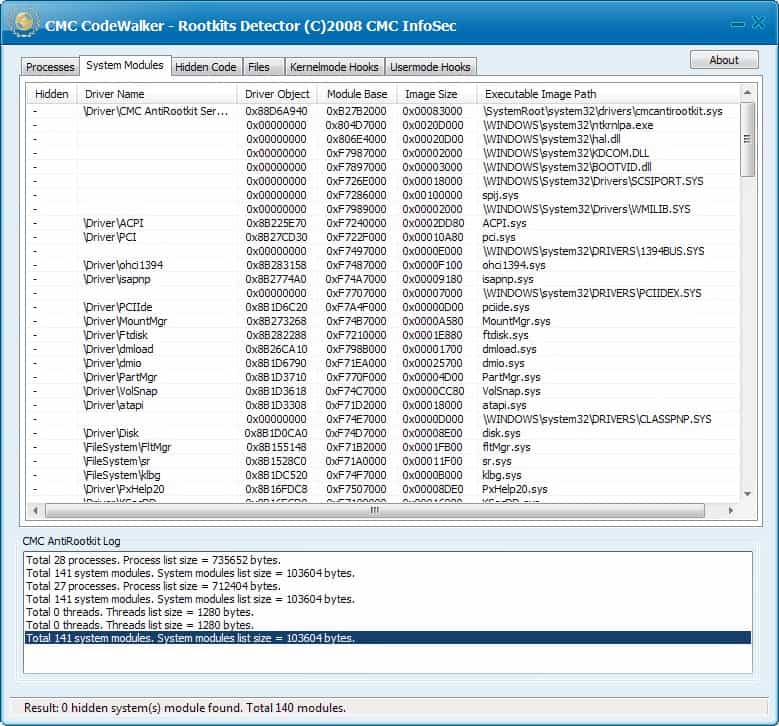
Rootkit Detection Software Codewalker
Most computer users may have heard about rootkits for the first time when the Sony BMG rootkit scandal exploded in the news. Sony BMG back then added rootkit-like behavior to select commercial […]

Internet Privacy: Start Panic Tells You Where You Have Been
Start Panic is a free online service designed to highlight privacy issues in browsers by detecting sites visited in the past. Internet privacy (also know as online privacy or web privacy) has […]

AVG Antivirus Linkscanner
Update: AVG Linkscanner is no longer available. AVG has released Secure Search however which offers an extended feature set. It does scan every link and display ratings for them like Linkscanner did, […]

Anti Virus Software Removal Tools Overview
Uninstalling anti virus software on a computer system is sometimes not a trivial task as security software tends to add components deep into the system to provide protection from various threats PC […]

UK. Sensitive Information. Need We Say More?
The massive increase in data collection throughout the world has not led to responsible data storage laws. That is an imbalance that becomes obvious especially in one country in these days. The […]

Home Video Surveillance System Utilizing Webcams
Ugolog is a free and commercial online service that turns any webcam installed in your home into a basic home video surveillance system. Home video surveillance systems can cost thousands of Dollars. […]
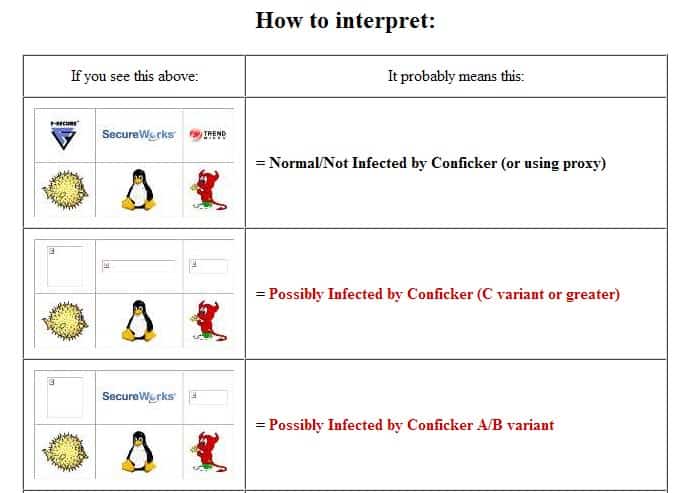
Test Possible Conficker Infection In Your Web Browser
Conficker Eye Chart is a free page on the Internet that helps you determine whether a PC is infected with a variant of the Conficker worm. While the Conficker worm did not […]
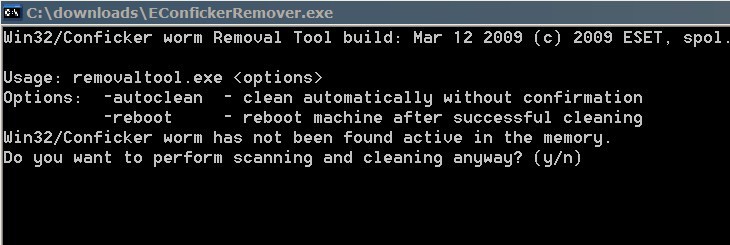
Conficker Worm Detection And Removal
By now you might have heard about the latest worm that is plaguing Internet users world wide. It goes by the name of Conficker (or Downadup)and comes in the variants A,B and […]
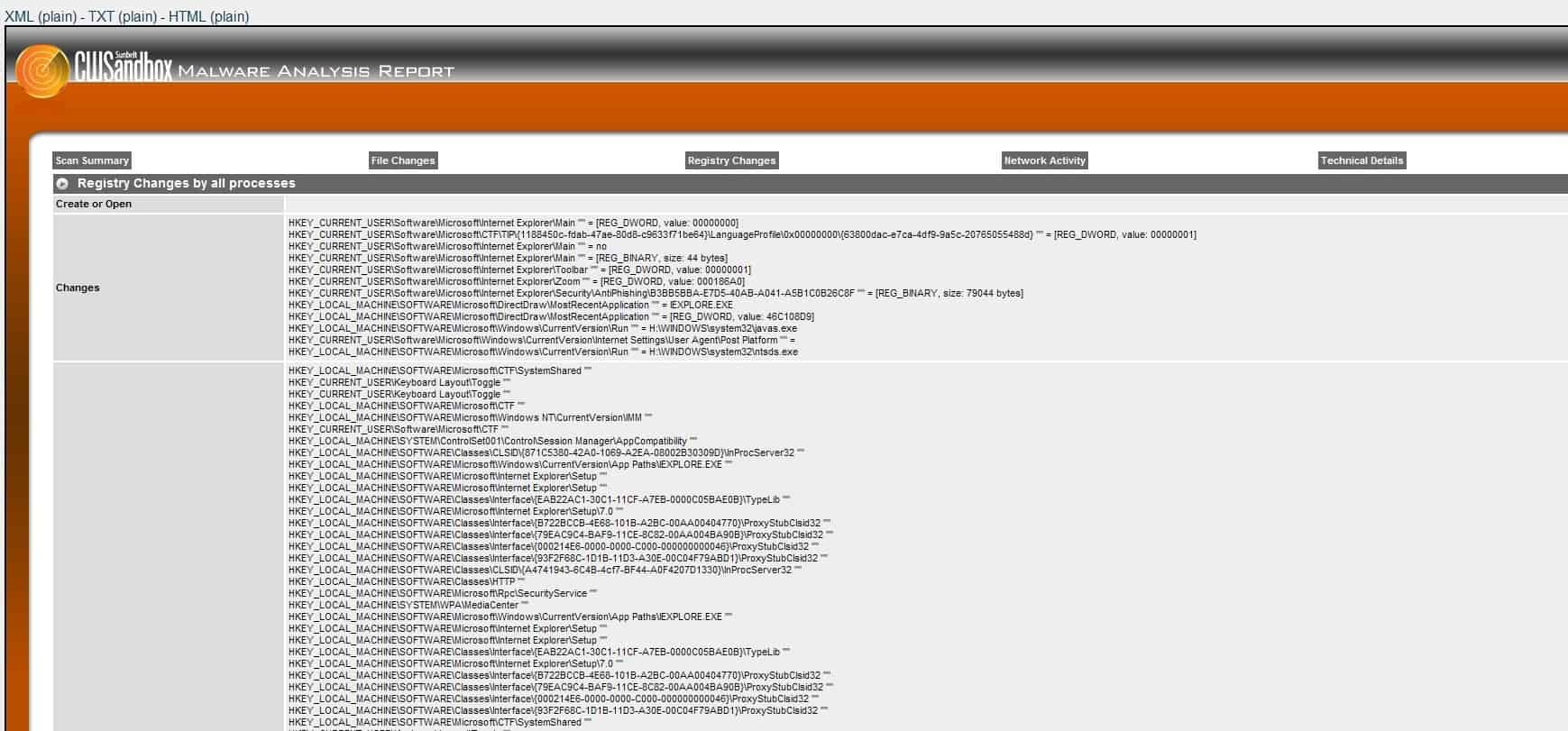
Analyse Software In A Remote Secure Environment
Several remote services are available on the Internet that let you analyze submitted software programs or files for malicious content. It is like an online virus scanner so to speak. Among them […]
Adobe Flash Security Scan
While Adobe Flash offers many exciting possibilities to web developers and users alike, it also introduces several additional security risks to computer systems. We already discussed the impact of so called Flash […]
Norton Security Scan
It is usually not a good idea to operate more than one security software of the same kind on a computer system. This is especially true for antivirus software solutions but also […]
Internet Advertising: Opt-Out Of Behavioral Targeting
There are many forms of Internet advertising that you encounter while you are browsing the Internet. One that has raised privacy concerns in the past is the so called behavioral targeting that […]
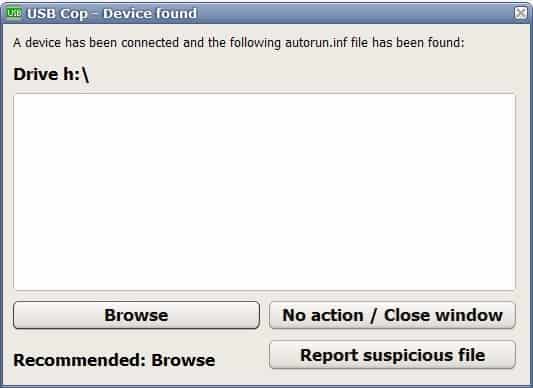
Increase USB Security With USB Cop
The Autorun feature is a big security risk on the Windows operating system. It is a risk even if you are the only person accessing the computer. Remember the Sony rootkit incident […]
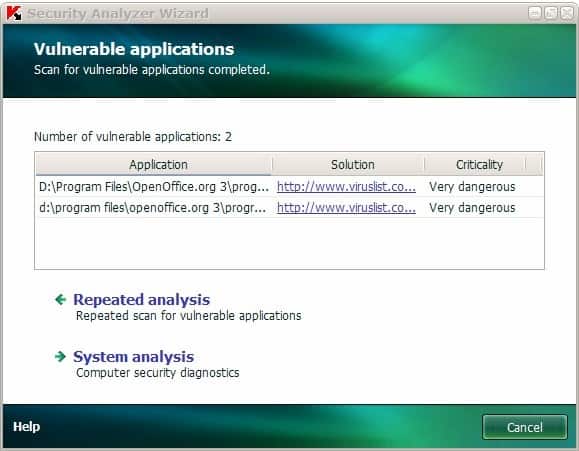
Kaspersky Application Vulnerability Analysis
We usually do not cover commercial software here at Ghacks. There are only a few exceptions to that rule. One is if we got our hands on the software and are allowed […]

Microsoft February Security Updates
Microsoft has released a cumulative security update for Internet Explorer 7 and 8 that fixes several critical vulnerabilities in the web browser. It is recommended to update Internet Explorer as soon as […]

Another Story From The Land Where Everything Is Possible
The favorite country of many for funny tech stories has to be the United Kingdom in recent time. Government officials seem to lose confidential data all the time, be it in front […]

Fport Maps Ports To Applications
Fport is a portable command line utility that will report all open TCP and UDP ports to the user. The port analyzer maps each open port to an application which distinguishes it […]

January 2009 Microsoft Security Bulletin
Microsoft has the habit of releasing security patches on one Tuesday each month. Time critical patches can be delivered out of schedule but that did not happen that often in the past. […]
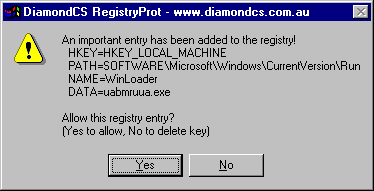
Windows Registry Protection
Update: Registry Prot is no longer available. We suggest you use either Tiny Watcher or MJ Registry Watcher which offer similar functionality. Both monitor the Windows Registry and alert you when changes […]
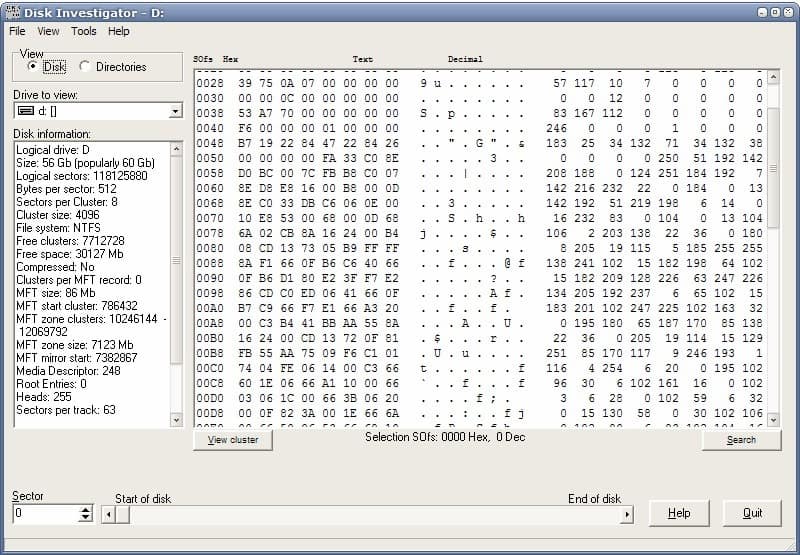
Hard Drive Data Retrieval
Update: Disk Investigator has not been updated in recent time. It is only compatible with XP and previous versions of Windows and not usable on later versions of the operating system. A […]

Google's Browser Security Handbook
Google has publicly released a Browser Security Handbook on Google Code. The handbook "is meant to provide web application developers, browser engineers, and information security researchers with a one-stop reference to key […]
Private Browsing Not So Private After All
The last year or so has been filled with announcements about private browsing, a new option implemented in modern web browsers to improve the privacy of users that are browsing the Internet. […]
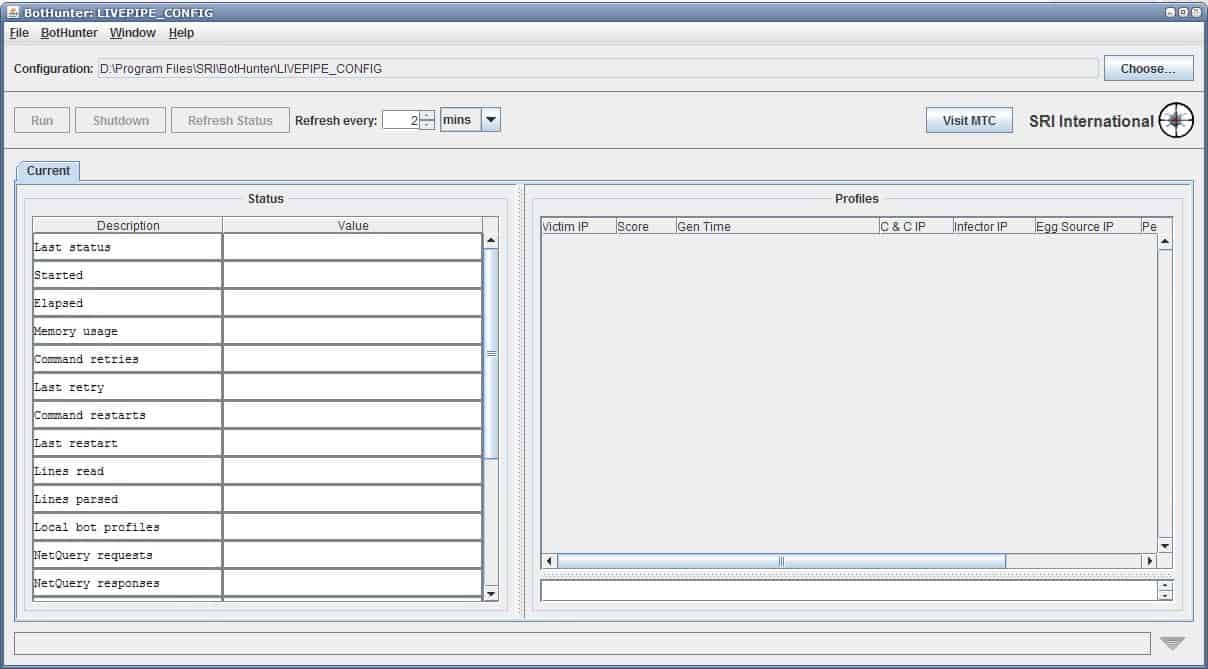
Network Security Software Bothunter
Bot networks are still a huge threat on the Internet. They are usually established with the use of computer worms that exploit old and new security vulnerabilities, trojans, and other malicious software. […]
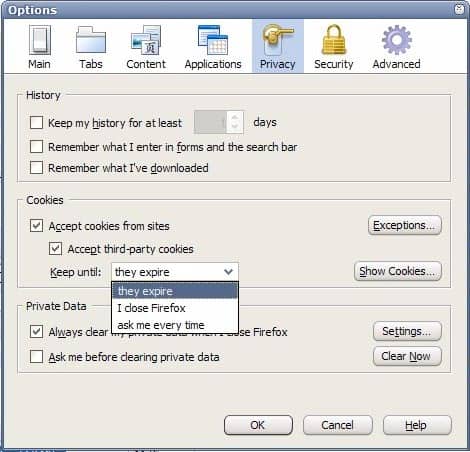
Effective Secure Cookie Management
How would an effective and secure cookie management look like? Most users would probably answer that it would make use of whitelists, blacklists and temporary cookies. The whitelist would contain trusted sites […]

