DOS Vulnerability in uTorrent and Bittorrent
A vulnerability in uTorrent and Bittorrent, which is using uTorrent's core, was discovered today that effects the BitTorrent 6.0 client,
uTorrent 1.7.x, uTorrent 1.6.x and uTorrent 1.8-alpha-7834. The Denial of Service vulnerability is made possible by the way the clients handle user data.
Basically said, uTorrent will crash if a user connects to it that sends a software version that is to long to be handled. This results in a crash of uTorrent. The attacker does not need to use Bittorrent at all to do that, a connection to the port that is being used by Bittorrent sending the to-long software version and a valid torrent hash is enough.
Code execution on the other hand is not possible. The uTorrent team reacted in less than one day and published a new version of their software 1.7.6 that handles the DOS vulnerability and three minor issues as well.
While it is not very likely that someone will actually exploit the vulnerability it is still advised to update immediately.
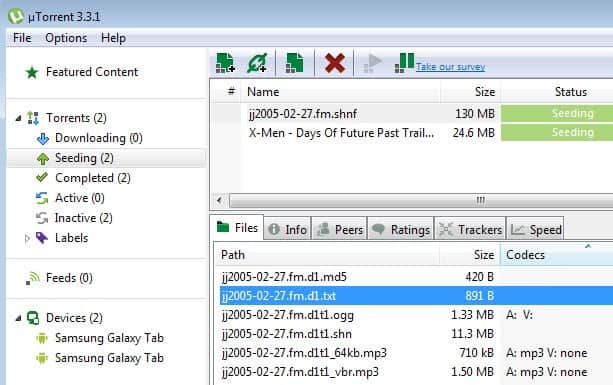
By default both the clients have the “Detailed Info†window active with the “General†section visible in it where are reported various informations about the status of the torrent and the trackers in use.
In this same window near “General†there is also the “Peers†section which is very useful since it showes many informations about the other connected clients like the percentage of availability of the shared torrent, their IP address, country, speed and amount of downloaded and uploaded data and moreover the version of their client (like “BitTorrent 6.0″, “Azureus 3.0.3.4″, “uTorrent 1.7.5″, “KTorrent 2.2.4″ and so on).
When this window is visualized by the user the unicode strings with the software versions of the connected clients are copied in the relative static buffers used for the visualization in the GUI through the wcscpy function.
If this string is too long a crash will occur immediately or in some cases (like on BitTorrent) could happen later or when the user watches the status of another torrent or leaves the “Peers†window. Code execution is not possible.
For exploiting the problem is enough that an external attacker connects to the random port opened on the client and sends the long client version and the SHA1 hash of the torrent currently in use and watched
on the target. Note that all these parameters (client IP, port and torrent’s hash) are
publicly available on the tracker.
Update: The vulnerability has been fixed officially. All you need to do is download the latest version form the official website or use the in-client update functionality to update uTorrent to the latest release version.
Advertisement










Join/push history/android
Confirmed this bug works…
But will not work with privte tracker, you need to copy the SHA-1 hash manually from the torretn page you are downloading.
Not consenting to data being shared