
Building a better Password
Most people tend to use passwords that they can rememeber easily. If you take a deeper look many use the same password for most of their password protected activities which is a high security risk. Break one, get access to all.

11 things to do after a hack
Lets assume your system has been hacked. What steps would you undertake after the hacking attempt ? The article written at techtarget.com tries to answer the question and presents a checklist of things to do after being someone hacked into your system. Its more of a checklist for corporate networks than for individual computers but it would not hurt to take a look and probably get some new ideas that you did not think about.

Home PC Firewall Guide
I know that some of you are using a firewall and therefor the home pc firewall guide site might be worth a visit. The website has more sections than I can list here so i stick with some interesting ones and leave the rest to you. To start with a good one, Installig Security Products, a guide on how to install security type software on a new windows operating system.
How to detect and remove spyware
This guide will provide you with the means to detect and remove spyware that is installed on your system. Before we start we should define the term spyware. There are different categories of spyware, like adware and malware, that make it difficulty for the user to distinguish between them and select the right tool for their removal.

How to Secure your Wireless Network
A friend of mine moved to a new house and had to change his internet provider as well. The room with the computer and the one with the phone line were not close to each other and he decided to buy a wireless lan router and use it to connect to the internet.
We had to do a scan of the surroundings of course and found lots of unsecured wireless lan networks. I don´t know why people keep these unsecured, maybe its laziness, maybe they simply don´t know the risks involved. Its like leaving your doors open when you leave your house. Lots of things can happen..
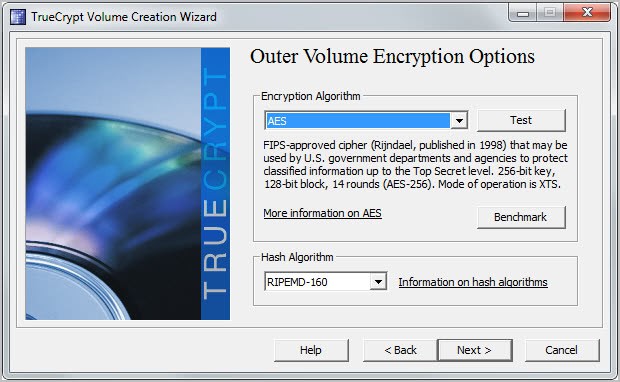
Securing your PC with True Crypt
Only a few days ago I wrote a first small article about true crypt and recommended it. Back then I bought a usb 2.0 hard drive with 300 GB capacity and encrypted its entire partition with true crypt. This was done to test the programs functionality but also to see if it would slow down my main computer (athlon 64 3000+, 1 gb ram).
To my great suprise it did not slow down the pc and I decided to expand the encryption to cover all my hard drives. Let me tell you why and how i did this and why you should also be considering this.
Clam Win Antivirus
After a lot of people told me that I forgot one of the best anti-virus freeware products out there I decided to take a look at Clam Win to get a better judgement on the claims made. The good thing besides that its free is that it´s also Open Source which makes it more transparent than the rest of the free antivirus programs.

94 Essential Tips for Staying Safe
Pc Magazine wrote a article with such a long title that I had to cut it to make it fit, the article "Maximum Security: 94 Essential Tips for Staying Safe" has some useful tips for everyone that wants to have a secure as possible computer. They divided the article into several categories, system, networking and wireless, e-mail, Web surfing, malware, and mobile.
Beginners Guide to Securing a Pc
You´d probably heard this before. Everyone should secure his personal computer. You read stories like this in every other computer mag, your geeky friends probably tell you the same and even name some programs that you should use because they are the best and most secure. I know that you would like to have a secure computer, well a secured computer, there is nothing like 100% security if you are on a network or the internet. Keep that in mind.
Atelier Web Firewall Tester
Did you ever ask yourself if your firewall is secure enough for your internet activities ? The major concern nowadays is related to pieces of software installed in your computer which may contact and exchange information with the outside World without being authorized and noticed by you.
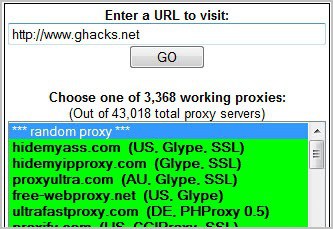
Web Proxy List November 2005
Its always a good idea to have some web proxies at hand. You can use them to hide your own ip when you navigate to a site that should not have your IP in their logs. You can use them to
bypass web restrictions / censorship from schools, universities and business and also use them if your country is one of those that likes to prevent its people from collection information on their own.
Change your Windows XP Password even though you can't remember it
I found an interesting article over at logicalexpressions.com that presents an astonishing solution if you have forgotten your windows xp password. This is clearly a security hole because everyone is able to change the passwords, the only requirement would be to have the original windows xp cd at hand.
Prevent Google Analytics from tracking your visit
Today google launched their free tracking tool for webmasters. It keeps track of visitor movements and clicks on the webmasters site. There are probably some visitors who don´t like their movements and clicks to be analyzed in detail.

How to remove the Sony - XCP DRM Rootkit
This article explains it all. It provides links to consumer made cd listings that contain the rootkit software, shows how cds with the rootkit software look like, explains how one can check his personal computer for the rootkit and finally gives a detailed walkthrough on how to remove the rootkit software manually from your computer.

Sony halts production of 'rootkit' CDs
After lots of controversy about their rootkit music cds Sony announced today that it will halt the production of rootkit music cds. It seems that consumer and media backlash finally paid off.

First Trojan using Sony DRM spotted
The first trojan using Sony´s rootkit software to hide itself has been discovered by anti-virus companies.

Sony and the rootkit, the story continues
The news spread like fire last week: Sony has a installer on some of their music cd´s that might install a rootkit on customers pc´s if they put them into their personal computer. The rootkit software could not be uninstalled by normal means and has already been used by hackers to hide World of Warcraft cheat scripts from being detected by Blizzards Warden client.
New online proxy.
Here is another of those online proxy sites that allow you to surf without revealing your ip at the destination site. Its available at xanproxy.be

Universal Music Group Music Cds may also install rootkits
And another player joins the rangs of the companies that might install spyware with their Music Cds when you put them into your pc drives. "Fontana Distribution, part of Universal Music Group and distributors for Upstairs Records Inc., are encouraging the independent records labels they distribute to use content protection on their CDs. "Twelve Eighteen", featuring the hit song "Summer Nights", carries the same content protection currently being used by Sony BMG.
John Lopez of Upstairs Records commented: "we are very pleased with the seamless production of the album. The media player on the CD has a good user experience and we intend using the technology on more new releases."
Freeware MyPlanetSoft Anti-Keylogger
Most banks in Europe offer a new service on their internet pages. When a user has to enter his login data he has the option to enter the password using a keypad that is displayed on the screen using a java applet. The user then clicks on the numbers and they appear in the password field. This is done to prevent the keylogging of the password.
The Anti-Keylogger does the same thing, only difference is, that its a tool that is started like every other windows program. After the tool is started you simply use the displayed keys to enter your passwords or other data on websites or even local programs.

Sony music cds might install spyware on your system
A few minutes ago I read a news article written by Brian Krebs who described how some Sony Music Cds try to install a software on pcs that could be labeled as spyware.
It seems that we have reached a new level in the fight between the record companies and its consumers. If you put a music cd in question into your drive a installer will popup. If you agree to install the software you won´t find a uninstall feature anywhere on your pc.
Apparently all Music Cds labeled "Content enhanced & protected" have the installer on the CD, make sure you check this before you buy a cd you would want to hear using your pc.

NSA Operating System Guides
The National Security Agency offers Operating System Guides on their websites. These guides are currently being used throughout the government and by numerous entities as a security baseline their systems.

