Twilio, the company that owns Authy, suffered a data breach
Twilio, the company which owns the popular 2-factor authentication service Authy, has revealed that it has suffered a data breach. An announcement published on its website states that some of its employees fell victim to a phishing attack.

Twilio data breach
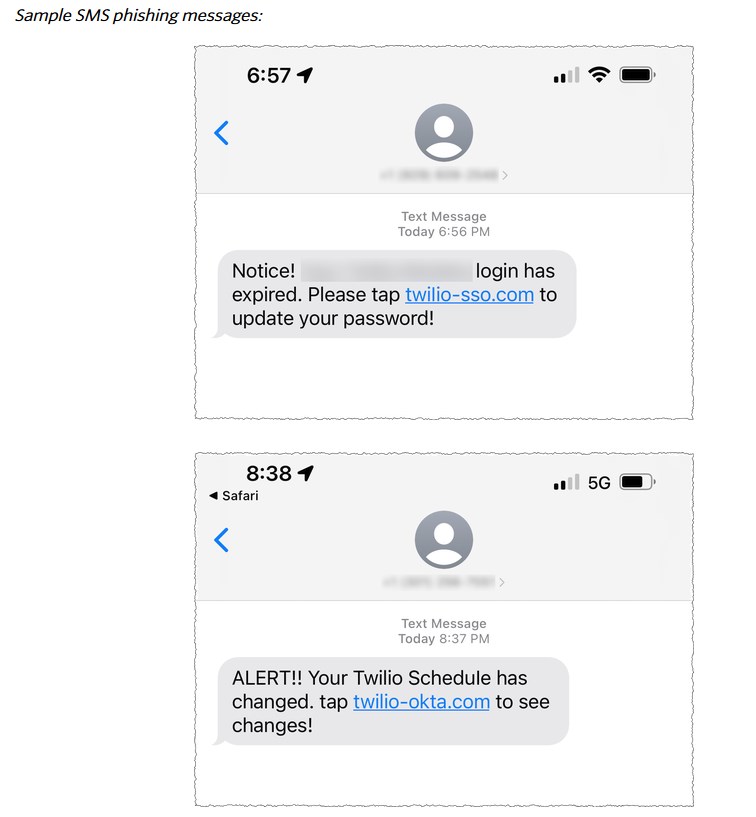
According to the report, hackers sent some text messages to current and former employees of the company. The message which originated in the U.S., was spoofed as being sent from Twilio's IT department, asked the users to update their passwords. A link, which accompanied the texts, directed the users to URLs controlled by hackers, who then stole the credentials to gain access to some of the company's internal systems.
The concerning part is that the attackers were able to access certain customer data. Twilio is investigating the attack, and will notify customers who were affected by the data breach. The company has already revoked access to the compromised accounts. It says that it worked with US carriers to shut down the threats, and has taken down the accounts belonging to the attackers on hosting providers that were used for the breach.
The transparency related to the data breach might be appreciated by users, but the company has not clarified what customer data was accessed. Twilio owns several products and services, Authy is just one of those, and is probably the most popular one of the lot. The attack will no doubt raise some eyebrows about the safety of Authy.
Are Authy users safe?
There is no official word whether user data from Authy has been stolen. I have seen a few reports on social media where users are panicking. But, I think it is safe to say that Authy users shouldn't be worried. Why is that?
1. Authy's login system
2. End-to-end encryption
Authy does not have a traditional login system, i.e. a username and a password. Instead, the service uses your phone number as your login ID. Let's say a hacker somehow knows your phone number, they can't associate it with your account's data. Since the TOTP service does not employ a password system, your credentials are not saved on the cloud, i.e. there is no password to be leaked. Authy uses a protection PIN (pass code) which serves as the encryption key to encrypt your data (2FA account tokens) on your device before it is uploaded to the cloud, this is known as end-to-end encryption. The only person who has access to this encryption key, is the user, without this key the data cannot be accessed by anyone, even Authy itself can't get the TOTP codes. Similarly, when you download Authy on a new device, you need to input the pass code to decrypt the data, before using the app for 2FA codes.
This end-to-end encryption is essentially similar to how cloud-based password managers work, for example, Bitwarden. Even if a hacker has managed to breach Authy, your data should theoretically be safe because the contents are encrypted. That's the whole point of encryption.
This is not an official explanation from the company, it's just based on my understanding of how end-to-end encryption works. Of course, it all depends on the proper implementation of the encryption system.
Some of my friends rely on Authy across platforms (iOS, Android), but I moved away from Authy a few years ago, to Aegis because I prefer offline and open source apps. I used this guide for importing the tokens.
Do you use Authy?




















This doesn’t surprise me.
Authy uses phone numbers. I just tried to set up an account on order to access my work payroll, and ended up in someone else’s account – a previous owner of my phone number.
There’s a backup password required, so I wouldn’t have been able to access his Gmail or Microsoft accounts, but I likely could have pwned his Twitch channel.
I wasn’t even *trying*.
And it gets better: the idiot service that requires Authy (and **only** Authy, or weak-ass SMS 2FA) says I must use my phone number to set up the Authy account!
It might be useful if the original owner could delete the account, and I think he tried – because guess who got his delete authorization code?
But no, it’s still there, and now I am forced to use SMS.
I’m amazed that there aren’t more breaches.
Don’t these people – any of them – think about this shit when they set this crap up?
Yet another example where stupid users clicked on links in emails they should not have. You can’t cure stupid. Whoever clicked the link in the email should be found and fired.
Roughly 90% of all data intrusions and ransomware attacks can be prevented from ever happening with $100 of user education and yet we spend billions on trying to fix stupid.
“Not USIng GoOgLE or MicRosOsft AuThenTicators Is BetTer”
The worst part is this company suffers a data breach and idiots are still like “It’s fine, I still think Google or Microsoft are worst because the fake sense of privacy I got brainwashed with by companies using that term as a marketing scheme when in reality I get no privacy anywhere in our out the internet”
This reminds me of people who say ” use Bitwarden because internal password managers are blablabla, yet, to make the it work like synchronization of an internal Browser password manager you need an account and trust their servers, so it is the same crap, you have to trust some 3rd party and their servers that can get a data breach and then they get access to your email and password and payment information (because you have to pay in some cases as well so much privacy when you need to submit your payment info).
What are you going to do when the same happens to Bitwarden and all the 3rd party companies that promise to be better than Chrome or Edge because some fairy tale like ‘privacy’?
I see, they will be like here “oh data breach is fine because it’s not Google or Microsoft” lol
Bitwarden is open source mate. That means anyone can check the code unlike Google or Microsoft options. Plus keeping a backup of your password manager is necessary incase server goes mayday.
“An announcement published on its website states that some of its employees fell victim to a phishing attack.”
Probably the same neinsteins who proudly proclaim “I work in IT”.
I have decided against Authy, because it’s incredibly complicated. Just reading the instructions gives me a massive headache.
There are multiple passwords (and I mean this in the wider sense, don’t start telling me about PINs, to me a PIN is just another password), several ways to use it, backup/no backup, enable this then disable it right afterwards, because you’re enabling it to make it more secure, but it makes it less secure so it’s more secure to disable it right afterwards…
Un-fucking-believably complicated. Good security is simple security. If I need a PhD in cryptography to know what buttons I need to push, you can get lost with your “software”.
I moved to Authy from Goggle & Microsoft apps. The real benefit is the ability to have access to the token on multiple devices, including my Apple watch. This is a huge productivity boost so that I dont need my phone in hand every time. I do believe, as Ashwin explained, that the codes are secure. In addition, any access to a site would need to start with username and password before the 2FA is required. The Aegis app seems to be Android only, a single device.
Actually, if you happen to be interested in the service this might become a good time to sign up. When a breach like this happens, the involved company will undergo a massive internal and third party review of its security systems (from experience with a company that has suffered such a breach I can assure you their insurer will require this), and upgrade them accordingly.
Of course this assumes that despite Ashwin’s sense that customers should probably not be overly worried, the breach was not somehow serious enough to truly jeopardize Authy’s/Twilio’s whole business. Presumably more details about exactly what happened and what was affected will emerge shortly.
Phone numbers should never be used for 2FA in the first place. Best option always is to generate tokens via key. Store that key in password manager and everything is fine. Data remains encrypted and hackers don’t have your phone number or even username and password.
I use Aegis as well(F-Droid). Offline, open source and keys(to generate tokens) are stored in Bitwarden.
Aegis is great, I agree.
Passwords:
Really poor concept, as they are easily stolen and easily phished.
Passwords with 2FA:
Still really poor concept, as they are still easily stolen and easily phished.
FIDO U2F:
Good concept (uses public/private key pair), not easily stolen or easily phished, but poor usability for the masses.
FIDO2:
Good concept (uses public/private key pair), not easily stolen or easily phished, but still poor usability for the masses.
FIDO multi-device credentials (passkeys):
Finally, we may get a secure and usable alternative to passwords for the masses. The sooner this is made available, the better. No matter haw many times I look into securing passwords, passwords have always been a poor concept, and always will be a poor concept.
I have been using the same password for 15 years, never got hacked. My tip: Don’t use ‘qwerty’ as password.
FIDO seems like just another excuse to collect telemetry, but with a unique identifier. Sure, they claim it is purposely designed to not be, but that is just not possible. It will be used as an identifier, and it will likely be abused. No thanks.
What happens if your physical passkey is lost, stolen, or destroyed? How do you get a new passkey setup if you change, say phones, ISP, or cell provider?
The problem isn’t passwords, themselves, it that most people use some variant of the most common passwords, like using password or 12345, etc. rather than something more secure.
Un-be-lie-va-ble. With the type of security services that Twilio provides, this should NEVER have happened. They need to up their act fast because this does NOT look good on them and their staff. They might loose a hefty number of customers over this major failure to protect their clients personal data.
It’s an embarrassment for sure, but I don’t think it’s a catastrophe. After all, as explained in the article Authy’s login system and encryption means your data is protected.
@ Ashwin,
Aegis looks like a good alternative, but my Android phone dates from 2016 and isn’t biometric. That means having to type in a password every time to authenticate 2FA and I positively detest using a phone’s keyboard. Doing anything on such a small screen is a pain in the posterior as far as I’m concerned and I don’t use Authy.
I was forced to consenting to Google’s use of 2FA, but beyond that I avoid it like the plague.
TelV,
Android + 2016 = more than likely no security updates (for a while), so “Authy vs Aegist” should be the least of your concerns brotha.
Customer data may be safe for now, but did the hackers get into Twilio networks? What if they are able to set up a MITM attack? Compromising a 2FA server would give them potentially endless access to services being accessed by customers.