Here is what is new and changed in Firefox 88.0
Mozilla plans to release Firefox 88.0 Stable and Firefox 78.10 ESR to the public on April 19, 2021. The new stable version patches security and non-security issues, and introduces new changes to the browser.
All Firefox channels receive updates at around the same time. Firefox Beta and Developer are updated to Firefox 89, Firefox Nightly to 90, and Firefox for Android will be updated to version 88 as well, but the release will likely be delayed somewhat.
Check out our Firefox 87.0 release overview in case you missed it.
Executive Summary
- Firefox 88 and Firefox 78.10 ESR fix security issues in Firefox. The highest severity rating is high, the second-highest after critical.
- Firefox 89, the next stable version, will likely come with the new Proton interface design.
Firefox 88.0 download and update

All new Firefox versions are pushed via the browser's automatic update feature. Select Menu > Help > About Firefox to check the installed version and to run a manual check for updates.
Manual downloads are also available. The following pages list direct downloads for supported Firefox channels.
- Firefox Stable download
- Firefox Beta download
- Nightly download
- Firefox ESR download
- Firefox for Android on Google Play
New features and improvements
Window.name isolation privacy fix
Window.name data is limited to the website that created it in Firefox 88 to "protect against cross-site privacy leaks. The property was preserved previously throughout a tab's lifetime, and that meant that it could leak information and could potentially be abused for tracking.
Other changes
- FTP Support has been disabled in this release. FTP support can be enabled again in Firefox 88 and 89 by setting the preference network.ftp.enabled to TRUE using about:config. Support will be removed permanently in Firefox 90.
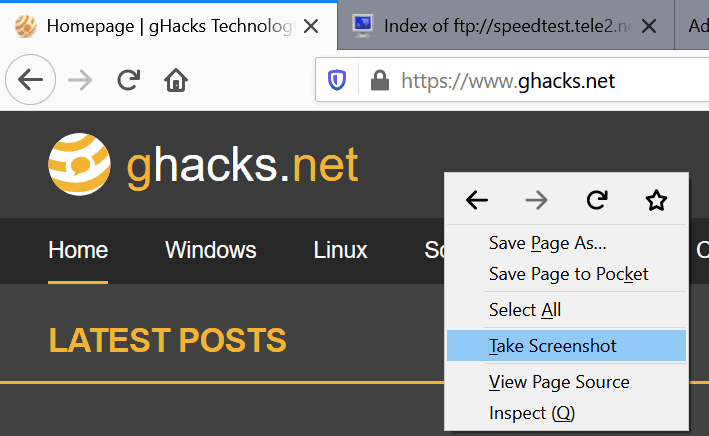
- Take Screenshot is no longer listed under Page Actions. Firefox users may either right-click on a page and select Take Screenshot, or use the customize menu to add a screenshot button to the toolbar.
- New grace period for camera and microphone access prompts. Firefox won't ask multiple times within 50 seconds if a request was granted to the same device, site and tab.
- Screen readers won't read content that is visually hidden on a webpage anymore.
- Localized print margins are now supported.
- PDF forms support JavaScript embedded in PDF files.
- Linux users get smooth pinch-zooming support on touch-devices.
- ShowHomeButton policy has been added. UserMessaging policy updated with new SkipOnBoarding option.
Developer Changes
- New toggle button to switch between raw and formatted response views.
- image-set() functional notation is enabled.
- Default monospace font on Mac OS changed to Menlo.
- RegExp match indices are now supported.
Known Issues
- The release notes list no known issues.
Security updates / fixes
Security updates are revealed after the official release of the web browser. You find the information published here after release.
Outlook
Firefox 89.0 will be released on June 1, 2021, two weeks later than originally scheduled.
Recently Reviewed Firefox extensions
- Subscription Info indicates if a Steam game is available on Xbox Game Pass, EA Play or Ubisoft+
- Customize your new tab page with random wallpapers, quotes with the Mue extension for Firefox and Chrome
- Switch between Firefox profiles with Profile Switcher for Firefox
- Improved YouTube! enhances YouTube in meaningful ways
- Open a URL from the clipboard with a hotkey using the Paste and Go Key extension for Firefox
- Web Translate is a Firefox and Chrome extension that displays the translation of the selected text
Recent Firefox news and tips
- Mozilla will remove Leanplum tracking from Firefox for Android and iOS
- Firefox's Drag Space Customize Option will be removed for most users
- Firefox for Fire TV and Echo Show will be discontinued
- Mozilla decides to hide Compact Mode in Firefox for new users but keep it for existing ones
- You can now test Firefox's local translation implementation
- Firefox Proton design refresh is almost ready: here is what is new
Additional information / sources
- Firefox 88 release notes
- Firefox 88 for Developers
- Firefox for Enterprise 88 - release notes
- Firefox Security Advisories
- Firefox Release Schedule






















No matter where they hid the view page info, you can’t d/l videos anymore. The link has been replaced with a blob on every single site. Excited? Yea….to find another browser
Firefox has been an epic fail since last year.
But go ahead….keep blaming then users until there are none left.
I’m not holding my hand on my arse, but FF w/o Developer Tools would be a footprint reduction worth noting. Call it EZ Fox or Net Fox, whatever. A lot of users are NOT webbies. Dev Tools should be an option, not an embed.
EVERY web browsers that open forced auto connections to remote servers, for whatever reason, ARE VIOLATING the user’s privacy because the user never asked for the browser to make that connection. And the web browser DOES NOT NEED to open any remote connections for providing basic web navigation functionality! Doesn’t matter how many autoconns each one opens! WAKE UP!
After upgrade 24/4/2012 Firfefox is very slow to start loading stuff from the web. It’s analysing or waiting something for maybe 20 secs. Windows 10 32bit.
after this update, i cant save pictures from instagram anymore, if it doesnt get fixed soon, ill probably look for another web browser, i used firefox 10+ years…
@Anon7:
I don’t understand your response. The most up-to-date comparison from the BSI clearly indicates that both Chrome and FF pass the requirements. Why would you refer me to an older version of the report from 2019?
@Shintoplasm
> The most up-to-date comparison from the BSI clearly indicates that both Chrome and FF pass the requirements. Why would you refer me to an older version of the report from 2019?
I already made a response to that.
But i will reiterate, those tests by the BSI shows that FF has a better more recent track record as regards security when compared to Chrome or Edge.
If the next test is done, i doubt Chrome will pass it because of FLoC.
Chrome is not as consistent as regards security as FF is.
In chrome you even have to use an extension to stop web rtc leaks. (At least the last time i looked) Its a mess.
Chrome is the flagship product of chromium, hence my criticism of it. I simply do not trust chromium. Wait and see with their removal of third party cookies and other stuff, lots of crap from upstream to deal with it.
Things break when things are removed, because chromium was never designed for privacy in mind.
@Anon7
You don’t know what “security” means. Security concerns things like sandboxing, memory allocator, process isolation etc. FLoC is a privacy issue but not a security issue.
The bureaucracy study that you spam here is very superficial, they look if certain security features are nominally present or not, but did not assess their quality or issues pertaining to them. Firefox’s sandbox is a joke compared to that of Chromium, but since both browsers superficially have a sandbox, they both get a pass in the test as if there was no material difference. This is the plain opposite of rigorous testing, but then, those are bureaucrats assessing the browsers, not developers…
What you say about WebRTC IP address leak in Chromium is still wrong. The leak can be reliably stopped, and extensions like uBlock Origin merely trigger an internal kill switch that is present in Chromium anyway. Browsers like Chrome lack a UI setting for this kill switch (hence their reliance on extensions like uBO to stop it), but some browsers, like Brave or Vivaldi, expose a Ui setting for this internal kill switch, in Brave’s case it is under brave://settings/privacy … You have no idea what you are talking about.
@ShintoPlasm, can you please deal with that guy from now on? I’m burned out at this stage and need time to recover.
> Browsers like Chrome lack a UI setting for this kill switch (hence their reliance on extensions like uBO to stop it)
This just goes to show why Chrome the flagship product of chromium was never built for privacy in mind. It does not take a genius to see that forking chromium would be a bad idea because chromium code is built around chrome with google dictates in mind.
It not a good open source project to fork simply because of google.
> @ShintoPlasm, can you please deal with that guy from now on? I’m burned out at this stage and need time to recover.
Get a life buddy.
Although i believe it wasn’t a big update. they add some small features that i will use or they enhance other things that I already been using. For example “Open image in new tab” is a great addition to the “view image” although a small thing. they improve other features that i know not the majority of the people using – but these who are – need it and will be glad for it. Anyway I’ve also tried first time the proton ui – browser.proton.enabled – (I’m aware it will be completed only in v89) and i like that it that the browser opens instantly without any shown delay (less than a blink of an eye as it seems).
about:config > layout.css.devPixelsPerPx > 0.85 to slim interface to the right size
“Open Image in New Tab” is a fantastic addition!
Hey you complete and absolute bunch of ……, what about the “View Image” thing for right click?
The hell is wrong with you guys? Each time I hesite to desactivate automatical update because I think you may fix stuff you’re made worse in past update, but no, it just keep getting worse and WORSE.
The removal of ” “View Image” completely ruins my user experience and this time I will be forced to give up on firefox
With version 88.0, some absolute clowns at Bug/Mozilla have decided to remove both “View Image” (replaced with “Email Image”, who would even use that for goodness sake?!) and “View Page Info” from the context menu.
Important to point this out as both should be reverted.
Page Info can still be viewed with Ctrl + I (which I have always preferred due to its speed compared to mouse clicks) and you can hide the annoying “Email Image” by adding to your userChrome.css:
#context-sendimage { display: none !important; }
Disabled People using a mouse and missing one arm, but Mozilla cares little about that or it’s spelling dictionary. So how about a large check box selector and GUI based to allow folks to choose what appears in their right click modal dialog menu options!
Firefox needs a Paste UN-formatted Text as well, especially when cutting and pasting into a Disqus forum box that has no option to force a Text only paste.
You forgot to mention “View Image” is gone from the right click menu on images, it’s replaced by “Open Image in New Tab” which makes it now impossible to open images in the current tab.
“which makes it now impossible to open images in the current tab”
Worse than that, it makes it impossible to see and save an image at its real sizee since what opens in a new tab is merely the thumbnail….
Literally a Firefox Article and some other browser shenanigans are again stucking their noses where it doesn’t belong.
Someone says he need to change thousand options to disable telemetry, that person is naive, it takes 978,673,576,657 options to change a single value in Firefox in dreams. In real world it takes 5-10 minutes to change everything which includes telemetry and many more things in about:config, but then different folks have different capabilities.
@Yash
> In real world it takes 5-10 minutes to change everything which includes telemetry and many more things in about:config, but then different folks have different capabilities.
Well said. It takes about a quarter of an hour MAX.
And its fun to mess around in about:config. It gives a nice sense of user control. Loads of thing to tweak.
@Anon7
> It gives a nice sense of user control.
It gives a nice sense of getting fingerprinted by advertisers. :D
@Iron Heart
You should take some reading lessons to understand words properly. When I commented on your few websites you always mention, you easily went back in your shell and said things which contradict your previous comments as well as next comments you made afterwards.
As for browser fingerprinting, I can say it confidently that your knowledge is limited in that subject.
@Yash
> As for browser fingerprinting, I can say it confidently that your knowledge is limited in that subject.
I agree Yash.
Iron Heart has no idea what he is on about as regards such matters.
He does not even recognise that there are many ideas and thoughts around that subject.
Try not to feed him too many lines, the dude is clearly obsessed with pushing ludicrous narratives.
@Anon7
> Iron Heart has no idea what he is on about as regards such matters.
But you have? You push the same bullshit over and over again. You have no idea about anything, lol. And pushing ludicrous narratives? I mean, look in the mirror, seriously…
@Iron Heart
Maybe you should stop pushing the same nonsense. In this article alone, you’ve shown you’re lying by saying that Firefox doesn’t use Tracking Protection in non-private windows which is laughable. Last time I installed Firefox, it showed me the option to set it up on startup and it ask which one I would like – Standard or Strict; and that Google is important – well said privacy and security advocate. That’s why malware apps finds a way to get into Play Store rather than F-Droid and Google without any advance notice removes some apps on Play Store without any apparent reason and then allowing them again after exhausting the developer in every possible way with Bots. You live in your world peacefully and stop spamming, unless this is the way to achieve peace in your world.
@Yash
> Maybe you should stop pushing the same nonsense. In this article alone, you’ve shown you’re lying by saying that Firefox doesn’t use Tracking Protection in non-private windows which is laughable. Last time I installed Firefox, it showed me the option to set it up on startup and it ask which one I would like – Standard or Strict;
I was CLEARLY referring to the desktop version of Firefox in that comment, and yes, this one doesn’t block tracking content in non-private windows, non-private “ordinary” windows have tracking protection set to normal, which excludes tracking content, while private windows have the tracking protection to “strict”, which includes tracking content. I believe the Android version asks during setup whether you want private or strict in non-private windows, but the desktop version doesn’t. Not that it matters, Firefox’s default tracking protection is shit anyway as it only uses the weak Disconnect list.
Listen, I don’t have to deal with toxic people who don’t know what they are talking about yet accuse me of lying. This is highly offensive.
> and that Google is important
Yes, they are important for any Chromium-based browser because they are the main contributor of Chromium which is the basic browser other companies build on (btw, Mozilla has the same kind of importance for Firefox forks). That doesn’t mean non-Google Chromium variants (so basically anything excluding Chrome) can’t be private. Just like most Android custom ROMs have no privacy issues, but take most of their basic code from Google. This discussion is very, very dumb. I hope you realize that.
> That’s why malware apps finds a way to get into Play Store rather than F-Droid and Google without any advance notice removes some apps on Play Store without any apparent reason and then allowing them again after exhausting the developer in every possible way with Bots.
Not good, but unrelated. Don’t use the Play Store then, there is F-Droid.
> You live in your world peacefully and stop spamming, unless this is the way to achieve peace in your world.
I think the ones who have no clue are the actual spammers, and this includes you. You are wasting my time.
@Iron Heart
Me as a spammer, good analysis DH who tried to stick his nose where it didn’t belong in the first place. Get a new job which doesnot include spamming, idiotic posts and contradictory texts literally every single time.
@Anon7
Yeah I guess I have to leave him in his default settings and if he thinks its a better approach, let him have it.
Sometimes when some folks say default settings are better, I don’t know it just doesn’t feel right, its like me giving my address to someone else, and I didn’t mention the house number in the hope that all houses look same in my neighbourhood and that colony is bigger so it would be impossible to find me. But that’s never the case.
If I have to hide something I would not reveal exact details and even if someone thinks he caught up to me, little he knew he was trying to catch the smoke all the time or that he didn’t find anything meaningful. Afterall that’s the point of taking measures against Browser fingerprinting as any browser has to reveal something but the less it is, the better are the measures.
@Yash
> Yeah I guess I have to leave him in his default settings and if he thinks its a better approach, let him have it.
It’s always the better approach provided that the browser has fingerprinting defenses enabled by default. If there are no fingerprinting defenses, then the defaults are harmful, but flipping fingerprinting defenses on as a minority solution (which is what FF users do) is also harmful.
You should use a browser that has fingerprinting defenses on by default, if you really want to prevent fingerprinting. Tor is best for this, followed by Brave.
Hiding information can do more harm than good if what you are hiding is not a strong identifier to begin with (like connection type, or timezone). Why would you hide weak identifiers at the cost of sticking out as a result? Makes no sense. Even strong identifiers vs. hidden info yields no improvement if you opt for hiding (randomization or static fake values are preferable).
@Yash
> you easily went back in your shell and said things which contradict your previous comments as well as next comments you made afterwards.
No, I actually didn’t. In fact, I am consistent with myself. Laughable that I have to actually state this.
> I can say it confidently that your knowledge is limited in that subject.
You disagree with people like Whonix devs and Daniel Micay, these are leading devs and privacy advocates and they think what you are doing is between ineffective and harmful:
“No, you can’t just solve browser fingerprinting by changing a few settings. The way you configure Firefox would be unique to you and fingerprintable.
A browser that would properly defend against fingerprinting would be one that is configured by default and the users don’t change it e.g. the Tor Browser or Brave.”
source: https://old.reddit.com/r/privacytoolsIO/comments/glr63n/brave_hardened/fr0to0n/
These guys are developing this:
https://www.whonix.org/
“Providing the offer to disable features to reduce attack surface can be useful. Doing it to prevent fingerprinting is utter nonsense since by changing any settings that sites can detect you have made yourself far more easily fingerprinted. Disabling WebRTC and WebGL would make you far easier to fingerprint, not harder. These sites encouraging things like that is a problem.”
source: https://old.reddit.com/r/GrapheneOS/comments/ciizae/vanadium_and_bromium_privacy/ev6m2ot/
This guy is developing this:
https://grapheneos.org/features
Then there is the Tor project which specifically advises its users NOT to touch the default settings because it will destroy their pre-configured anonymity… I am sure they are doing this just for fun, yeah.
* [Editor: removed, please no personal attacks]
@Iron Heart
Tor Browser says to not change default settings because it is already providing the privacy protection to help its users to remain anonymous and its effective at that for the most part. More often than not if a certain user tinker in about:config settings, without knowing what is he doing, that user often disables certain protections without even noticing it.
I don’t know what the hell you said that came in personal attack category.
About Browser fingerprinting – I use two phones currently. First one is fairly new as Android 11 is supported on that model and the second one is on Android 5 and yeah its ancient in today’s world, but because I was curious how it would perform after years I gave it a try. I kicked things off in January last year and so I first ran Play Store on it and found some popular apps and then specifically tried to found reviews from this device model but I didn’t find any latest reviews within a year – no surprise there. Now if I use a browser in that phone and updated one at that, by your definition because of default settings, I can safely say I would stick out very easily in terms of fingerprinting as that phone doesn’t even support 4G and it would be visible in connection type without forgetting old Android version, up to date Browser and other entropies. To make it stop I use RFP on both my devices in Firefox and both produce same fingerprint in terms of User Agent, connection type and more. That’s why your definition of Browser fingerprinting does not hold its ground in the vast ocean of different Device model from various manufacturers without forgetting different roadmap of OS updates.
Default settings can only be good if they are done properly, in Brave’s default setting it introduces random values in some test but reveals true values in User Agent, connection type and that introduces more entropy which easily reveals its not a Chrome even if user agent is same and so different device models and all of a sudden Brave users are not private anymore. Bromite hides user agent but still reveals connection type because its not just a Brave or Bromite thing, its the Chromium problem, and the way some toggles have been removed from Chrome like WebGL, WebRTC it leaves hole for more entropy, not now but in future as well. When you say you’re giving more information or increasing your fingerprint by using RFP, its not as simple as that. Every browser needs to provide some sort or value whether static like Firefox or randomized like Brave, but its only effective, to a certain extent, if it can’t be linked back to the Browser type in the first try and it doesn’t matter how much someone is altering values if its revealing main things in the first place – its like preventing yourself in winter by only opening your door and window all the time with all sorts of clothes on. By using certain protections, the whole fingerprint of two different models can look like same. Now its not perfect like Tor, but its way too far ahead of Chromium browsers(default or modified) and even default Firefox.
Just don’t ask why I’m using an old device because I’m not using an old device but rather a new one and an old one.
@Yash
> Tor Browser says to not change default settings because it is already providing the privacy protection to help its users to remain anonymous and its effective at that for the most part.
That they are satisfied with their own config is not the only reason; another reason why you shouldn’t change any settings is uniformity of output. All Tor Browser Bundle users have RFP enabled, they do not differ in this. FF users don’t have RFP enabled, you stick out of the crowd when you enable it, because you have altered output compared to other FF users (and RFP’s output is known to advertisers by now, they can tell you have it enabled).
> Now if I use a browser in that phone and updated one at that, by your definition because of default settings, I can safely say I would stick out very easily in terms of fingerprinting as that phone doesn’t even support 4G and it would be visible in connection type without forgetting old Android version, up to date Browser and other entropies.
Yeah you are fairly unique if you use an old device which hardly anyone else uses, connecting via 3G is also not that common anymore. But if you hide the device and the connection type in response to this perceived problem, you are not in fact solving any problem. You seem to forget that “no result”, “nothing returned”, or “0” is also a recordable value. So, you are fairly unique with “3G”, but you are also fairly unique with “connection type hidden” which is a result that the adversary records, just like “3G” is a result which the adversary records. Typically, 4G would provide a much greater crowd to hide in, and there is no reason to hide “4G”. Again: While 3G is not optimal, hiding the connection type does not solve the problem. Might in fact make it worse since there might be more “3G users” than “connection type hidden” users.
While “old device XYZ” is similarly not optimal, hiding the model (which might be detectable still via other means) does not solve any problem. Might in fact make it worse, there might still be more user of an old device (especially Galaxy etc.) than there are Bromite users, “device hidden” is a unique characteristic of Bromite’s user agent. If you think that there are more users of your device left than there are Bromite users, what Bromite does might not help you (notwithstanding the fact that advertisers can detect your model anyway, even without it being mentioned in the UA, if they put in enough effort).
You fail to understand that “no result” is, somewhat ironically, also a result that goes into your fingerprint just like any other value.
> old Android version
Lesser issue. There are still enough devices who share this version. Also solvable via custom ROM in case you need a newer version to hide in. However, a custom ROM might be detrimental in terms of fingerprinting, if your device did not officially support the Android version the custom ROM uses, you might be fairly unique(!) with your device running a higher Android version than what was officially supported by the manufacturer.
> up to date Browser
Good, you share this with many others.
> To make it stop I use RFP on both my devices in Firefox and both produce same fingerprint in terms of User Agent, connection type and more
RFP is supposed to output a uniform type of fingerprint, however, RFP’s output is known to advertisers and you are within a very small crowd of people (those few and far between FF users that bother to enable RFP), which is bad by definition. It is very important that the browser does these things by default, so that one avoids the “too small a crowd to hide in” issue. Firefox will never enable these defenses by default and is thus, contrary to Brave or the Tor Browser Bundle, unfit for purpose. Why don’t you understand this?
> That’s why your definition of Browser fingerprinting does not hold its ground in the vast ocean of different Device model from various manufacturers without forgetting different roadmap of OS updates.
My definition does hold up. You either randomize (create a new unique fingerprint for every session) or you follow the uniform fingerprint approach – let everyone produce the same type of fingerprint (which in FF’s case, is partially randomized and partially static). Both methods should work and are applicable to every device. But it is important that browsers do that BY DEFAULT, you see.
> Default settings can only be good if they are done properly, in Brave’s default setting it introduces random values in some test but reveals true values in User Agent, connection type and that introduces more entropy which easily reveals its not a Chrome even if user agent is same and so different device models and all of a sudden Brave users are not private anymore.
User agent is the same as that of any other Brave user (which is not that small of a crowd anymore in 2021) if you keep your browser current, this is hardly usable for advertisers. Why they reveal the connection type I don’t know, generally this should be 4G or WiFi for most people and is therefore also a weak identifier even when revealed, once again you are hiding in a big crowd there. I don’t know if it’s even possible to reliably hide the connection type because each connection type has specifics that might be detectable indirectly.
Brave can’t hide that it isn’t Chrome to begin with. Brave has an adblocker which can be detected via its behavioral patterns. Brave randomizes the fingerprinting output which is also detectable (but despite the fact that it is detectable, there is still an inherent value, which is the impossibility of the emergence of a canonical fingerprint that is based on the true values). Brave can’t credibly pose as Chrome unless the adversary is stupid and looks no further than the user agent; however, this is not strictly necessary. Brave is a growing browser and there is quite a crowd of Brave users to hide in by now, so even if a website detects that it’s Brave and not Chrome, chances are that you are not the only Brave user visiting the website and that this specific identifier is not very strong.
Hiding the device model is difficult because the model can be detected indirectly in so many ways, advanced hardware fingerprinting (with or without hiding the model in the user agent, doesn’t matter here) would need lots of spoofing. Whether or not trying to hide the model would be beneficial if you use a popular model is debatable, too.
> Bromite hides user agent but still reveals connection type because its not just a Brave or Bromite thing, its the Chromium problem,
What do you mean “hides the user agent”? Bromite does produce a user agent which excludes the smartphone model, which is IMHO a pointless exercise because the device can still be detected indirectly by probing for stuff like screen resolution, amount of RAM, hardware concurrency etc. Might even be harmful considering that not many people use Bromite, with “device hidden” being a unique characteristic of Bromite’s user agent. You are sticking out with this.
You are still subscribing to the “Reduce attack surface = Lower fingerprinting risk” which is dead wrong because “no result” for whatever value is also a result that goes into your fingerprint. And since nobody else bothers to disable features, you are fairly unique with this. As long as you subscribe to this false idea / equivalency mentioned before, I can’t help you and any discussion is pointless.
> and the way some toggles have been removed from Chrome like WebGL, WebRTC it leaves hole for more entropy
You think disabling WebGL and WebRTC (diverging from the defaults in the process) solves any kind of problem? It doesn’t. You are generating uniqueness for yourself but not much else.
> When you say you’re giving more information or increasing your fingerprint by using RFP, its not as simple as that.
No, RFP would be beneficial – if it were a default, which it isn’t. RFP’s usual output is known to advertisers and you are in a very, very small crowd which bothers to enable this in Firefox, this is just bad. Tor avoids this by enabling RFP by default and Brave also avoids this by enabling their fingerprinting defenses by default (which are not RFP, but rather randomization).
> if its revealing main things in the first place
What are “main things”, in your opinion? Browser type and version, smartphone model, connection type, and timezone are not “main things”, neither of those are strong identifiers because you are hiding in a huge crowd in each case.
> By using certain protections, the whole fingerprint of two different models can look like same.
Good that RFP produces the same type of fingerprint for two different devices, as it’s supposed to. But you are overlooking something very important: RFP is not the default of Firefox, YOU enabled this. Hardly anyone else does, and Firefox and Tor (which does enable it by default) can be told apart at the network level, so the existing Tor crowd doesn’t help you there. You are a very special snowflake with this no matter where you go. It is therefore very important that browsers enable such protections by default, people like madaidan from the Whonix project understand this, but you sadly don’t.
> Now its not perfect like Tor, but its way too far ahead of Chromium browsers(default or modified) and even default Firefox.
It’s bad, not because it somehow fails to work, but rather because it’s not the default of FF. I’ve already explained why this is detrimental.
You have two fundamental errors of thought:
1) You underestimate the importance of defaults. Fingerprinting protections need to be enabled by default in whichever browser you choose, because if they aren’t, you can safely assume that hardly any other user of the browser you use will bother to enable them. Most people stick with the defaults, which is “RFP = turned off” in Firefox’s case, and the crowd who don’t stick with the defaults is extremely small. This creates a very serious threat of uniqueness for you, wherever you go, if you are among this extremely small crowd.
3) Reducing the attack surface is not the same(!) as reducing the fingerprinting risk. Reducing the attack surface INCREASES the fingerprinting risk if the small attack surface is not the default. See above. You are subscribing to a false equivalency here.
Away from all this discussion, FFUpdater has now included Bromite as well along with other browsers – Brave, Iceraven, Firefox, Firefox Beta, Firefox Focus/Klar, Firefox Nightly, and a different product Firefox Lockwise. I haven’t installed that FFUpdater yet(no problem with app), I just look for browser updates directly from websites so was not aware of Bromite inclusion yet, though Bromite has its own custom repo so there are multiple ways of installing. And one thing whether one uses Brave or Firefox, all of them are better than Chrome, Opera, Edge and many more.
Firefox Lite is not on FFUpdater list and it’s based on Android Webview like DuckDuckGo browser so better use any other Firefox Browser which doesn’t depend on Android webview component, and avoid Firefox Lite even if get listed on FFUpdater app in the future.
@Anon7
You said it correctly, its very fun to mess around in about:config, I don’t know about many folks but when I do it I feel like a child again who is instructed to not do a particular thing from parents and teachers but that child still does that, Its just a liberating feeling. For tinkering I use gHacks *coughs* Arkenfox user.js file in read only state for smartphone and applying absolutely necessary changes, as its made primarily for Desktop, but then Firefox for Desktop is a different animal(no pun intended) from its smartphone counterpart like desktop in general is.
Mozilla removed View Image from the context menu with this update: https://bugzilla.mozilla.org/show_bug.cgi?id=1699128
This is the ONE feature I consistently used ever since the beginning of Firefox. Now it’s gone for the stupidest of reasons: “The context menu’s behaviour is now also more compatible with other browsers”
Go fuck yourself Mozilla.
> Mozilla removed View Image from the context menu
Hey, @Anon. How about you go * [Editor: removed, please stay polite]. It’s right there as “Open Image in New Tab”
OP literally tells Mozilla to “go fuck yourself”. Reply tells OP, ironically and satirically, to “go fuck yourself”… and yet it’s edited. Has happened to me with words like “stupid”. The inconsistency burns
Quote: “Go fuck yourself Mozilla.”
This insult is the usual tactic to engage you in an ad hominem polemic and trigger moderation. While Anon will claim “It is my opinion” and protetect by law, the moderation considers your ironically reply as a personal attack. Both wash their hands in innocence.
The goal is to frustrate and discourage you!
This forum is flooded with dirty subversive tricks like that and a very unhealthy place to exchange credible information let alone honest and fair opinons.
>>> The inconsistency burns
Even worse, comment approval get’s overly delayed or not approved at all. I am not the first to witness such a skewing of the argument in favor of the usual suspects. But what they don’t realize, in the long run, they screw them self … trustworthy and technically knowledgeable commentators will give this swamp of misinformation and propaganda a wide berth.
Don’t let it get you down … remember that ol’ Marley song?
“Sun is shining, the weather is sweet
Make you want to move your dancing feet
To the rescue, here I am
Want you to know ya, where I stand!”
Good bye … auf Wiedersehen, ghacks forum!
Proton interface is when I uninstall Firefox from all my devices.
Cool story bro. * [Editor: removed, please stay polite] over some UI changes, and forgo all the privacy and customization tweaks. Maybe you can ask Iron Heart how to set up hundreds of profiles to stop 3rd party tracking
ui change is more than enough…ever heard of windows 10? or windows 8 at least?yeah i know privacy is important too, but customization tweak? that died when ff quantum was released.
Anyone still use Firefox? Used to use it exclusively from when it first came out. Stopped using it as daily 2-3 years ago and removed it from all my PCs a while ago.
To use what? Why?
FF might not be perfect out of the box but it is eminently configurable to make it so plus keeping the prying eyes of Alphabet Inc. out of my affairs is mandatory in my book.
@Bowsr
> but it is eminently configurable
And this configuration is eminently fingerprintable.
https://madaidans-insecurities.github.io/browser-tracking.html#configuring-the-browser
> so plus keeping the prying eyes of Alphabet Inc. out of my affairs is mandatory in my book.
Firefox using Google’s location services and FF sharing download hashes with Google would be to differ, lol. Plus, the internal use of Google Analytics. Whereas, you know, e.g. Ungoogled Chromium doesn’t connect to Google at all. Engine isn’t everything, despite the whole make believe nonsense FF diehards tout here.
> Ungoogled Chromium doesn’t connect to Google at all.
It was downloading google voice recognition in 2015, a huge privacy invasion.
“We are at the point in 2017 where if you’re not a target and/or you know exactly what you’re doing, FF is fine. Actually: all of Edge/FF/Chrome are.”
https://nitter.snopyta.org/tqbf/status/930861421260402688#m
Firefox has totally borked Disqus with its 3rd party tracking cookie protection for all websites and has caused me to have to utilize a dysfunctional custom cookie setting just to be able to upload content to a Disqus forum post. I have to chose a custom allow third party cookies only for sites visited to be able to upload content but each time that I reload the page or move to another page at the same website I have to re-login to Disqus, but that’s a one click operation as my sign-in credentials are still held in the browser’s cache.
But this has been an issue for me ever since FF started blocking all 3rd party tracking cookies and if I use FF’s standard strict settings for 3rd party cookies I do not have to re-login to Disqus with every page reload or different page at the same website, but I can no longer upload content to any Disqus managed forum!
“Window.name isolation privacy fix”
Were they not supposed to have fixed that problem already in Firefox 82 ?
https://developer.mozilla.org/en-US/docs/Mozilla/Firefox/Releases/82#dom
says “The window.name property is reset to an empty string if a tab loads a page from a different domain, and restored if the original page is reloaded (e.g. via the “back” button).”
From
https://blog.mozilla.org/security/2021/04/19/firefox-88-combats-window-name-privacy-abuses/
“Firefox isn’t alone in making this change: web developers relying on window.name should note that Safari is also clearing the window.name property, and Chromium-based browsers are planning to do so”
Not a privacy initiative from Mozilla, just following Google & Apple instructions as usual. Users have been asking Mozilla to stop this privacy leak for at least 13 years (age of that bug https://bugzilla.mozilla.org/show_bug.cgi?id=444222), but the billions of web users are only data cattle for Mozilla Corporation’s real customers, what matters to them is what the Big Brothers ask them to do. No amount of them punishing digital rights activists will be enough to hide the obvious.
———–
“PDF forms support JavaScript embedded in PDF files.”
Running code just by opening my documents ? No thanks:
pref(“pdfjs.enableScripting”, false);
But the pref or its effect will probably not live long, it’s safer to simply stop opening pdfs with Firefox. With the malicious garbage browsers have become anyway, it’s often better when one is pushed to stop using them for something.
It’s also one of the reasons why I use SumatraPDF instead of Adobe trashware, pdf scripting is disabled.
Still need to trawl through a thousand about:config entries to disable telemetry. At least that remains a constant…
99.9999999999% of all telemetry is controlled by a single checkbox in preferences
You’re conveniently forgetting that Chromium browsers have had most of this stuff for ages.
> Chromium browsers have had most of this stuff for ages.
a FLoC-load of bullshit
– TCP (aka dFPI): only Firefox has this
– ETP shims: only Firefox has this AFAIK
– network partitioning: only Firefox has done this to the full degree possible
– oxidation/rust: Firefox is miles ahead of anyone else, e.g all of servo for starters
– warp/stencil: warp is unique to Firefox and outperforming chromium in many tests, and generally the equal in others
– webrender: I don’t see other browsers using the GPU
maybe
– HTTPS only mode: chromium is still behind on this, but only a few releases
sure
– fission: can’t wait: will help those 0.0000000000000001% of website visit cases when needed
It’s irrelevant if other browsers have them or not. What is relevant is that Firefox has them.
I love how you laid out the bate so obviously for the resident Brave shill.
@Tony the FF diehard
Actually, it’s a nice collection of buzzwords without any kind of meaning attached to them. You may wish to make use of them in some of your next posts, lol.
Multirow tabs + Proton ===> it sucks!
So much wasted space with Proton.
WTF?!
EVERYTHING IS AWESOME … FIREFOX IS SO AWESOME :)
Loving Firefox more and more every day.
– Total Cookie Protection improvements
– ETP shims enhanced
– HTTPS only mode improvements
– super comprehensive network partitioning
– more oxidation with rust components
– more warp and stencil improvements
– webrendering enabled for more devices
– fission moving along nicely
– proton and non-native themes
It just keeps getting better every release. So excited. Absolutely the best browser ever. SO AWESOME :)
I agree. I try other browsers from time to time, but something with the Blink engine just doesn’t seem right on my machines. I get glitches here and there. Firefox has never let me down. I can use Firefox without have to think about it. Those who know use it for a reason, and those who don’t just seem to follow what is pushed in so many “Try Chrome, Try Edge, Try Brave” ads I see all over. I don’t remember ever seeing “Try FIrefox”. I guess if you care about privacy you do research, and end up with Firefox anyway.
@Bobby Phoenix
> I guess if you care about privacy you do research, and end up with Firefox anyway.
You likely end up with Tor, or if you need a general use browser, Brave:
https://old.reddit.com/r/privacytoolsIO/comments/glr63n/brave_hardened/fr0to0n/
Firefox doesn’t defend itself against fingerprinting by default, and when you enable the related settings, you stick out among the crows of Firefox users, because hardly anyone else bothers. You will never be able to hide among Tor Browser Bundle users, either, because Tor and FF can be told apart at least at the network level. People who recommend Firefox for privacy are blatant fools who don’t understand that: reduction of attack surface ≠reduction of fingerprinting risk. Reducing the attack surface creates permanent uniqueness, which is counterproductive as far as fingerprinting is concerned.
> Reducing the attack surface creates permanent uniqueness
You clearly know nothing about how entropy works
@Anonymous
> You clearly know nothing about how entropy works
Tell me your version.
“Providing the offer to disable features to reduce attack surface can be useful. Doing it to prevent fingerprinting is utter nonsense since by changing any settings that sites can detect you have made yourself far more easily fingerprinted. Disabling WebRTC and WebGL would make you far easier to fingerprint, not harder. These sites encouraging things like that is a problem.”
source: https://old.reddit.com/r/GrapheneOS/comments/ciizae/vanadium_and_bromium_privacy/ev6m2ot/
Refute it. I’m waiting. “You don’t know blah blah etc.” isn’t enough of an argument.
LIE1:
You said Firefox does nothing for fingerprinting by default. It blocks known fingerprinting scripts by default. That is not nothing.
—
IGNORANCE1:
You seem to think fingerprinting is a binary object/outcome. There is no such thing as a guarantee to defeat fingerprinting – there is only making it harder and harder, bit by bit (in various enviroments)
—
IGNORANCE2:
You are confusing Brave’s Shields default on vs Firefox’s RFP default off as some sort of effectiveness measure. This is ignorant to say the least.
backstory
– Firefox cannot make RFP default on for compat reasons because it was designed for Tor Browser. When they do, it will be in private window mode or a super private window (tor mode) where end users are educated about what to expect such as latency and breakage, and it may indeed be changed somewhat to fix compat issues that are more prevalent these days (such as the rise of canvas use). YOu can’t just throw RFP in it’s current state at 220 million users
– Brave on the other hand has been adding protections piecemeal, with compat in mind from day one, to a much smaller audience that has been specifically and constantly called out to as “privacy” people. Their user’s expectations are being considered e.g. with a Shield setting per site
So there is a very large difference in approach with audience/design/purpose/implementation-period here. Trying to compare them in this manor is useless. What you should be looking at is the actual effectiveness when used (see ignorance point 1) in different situations (see next paragraph)
Both Brave and Firefox are _MORE_ effective when used by large numbers of users, and even MORE still when the protections are enforced and cannot be changed (prefs, extensions), but that does NOT mean that they are useless when used in isolation. In fact, RFP is more effective than Brave’s Shield in this regard
—
LIE3:
You keep saying that it is impossible to improve the fingerprinting defenses of Firefox by hardening it, which is false.
Just by enabling RFP, you randomize canvas and defeat almost all naive scripts (some naive scripts do not use canvas). Studies have shown that almost all scripts in the wild are naive. This is no worse than Brave’s protection. Brave has repeatedly said that it is only interested in defeating naive scripts, which is why they randomize. Tor Browser and RFP on the other hand have to be robust and handle anything thrown at them, so they also handled advanced scripts. Again, this is a difference in strategy: it does not negate the effectiveness.
Brave default Shield on is NO BETTER than RFP, despite being default off: all Brave can do is fool naive scripts (which RFP does)
—
LIE4:
You keep claiming that Brave’s protection is better. It’s NOT.
Brave still leaks canvas. While they also randomized webGL, they then fucked around with meaningless items like audio (there is basically no entropy in chromium in audio) and trivial shit like user agents and plugins. For fucks sake, canvas still fucking leaks. And then to boot, some of the highest entropy items left like fonts, screen metrics, devicePixelRatio, languages and so on haven’t even been touched.
Any half-decent advanced script can run rings around Brave right now. Until it get s some sort of parity, I wouldn’t go crowing about it being superior, when it clearly is NOT.
—
IGNORANCE3:
You keep claiming that changing a metric makes you unique. But you don’t _know_ that, you’re just extrapolating from what someone else said about how changes from default stick out. Not all changes can be detected. But sure, those that can, it depends on the metric
quote “Disabling WebRTC and WebGL would make you far easier to fingerprint, not harder”. This is false
WebGL is not covered by RFP (yet). Luckily, in Brave, it is covered. In Tor Browser they disable it. If you knew anything about how WebGL fingerprints are done, and what causes the variations, and what can be added to them to increase entropy, you would know that they are very high entropy: almost if not defintely unique. It’s around 98%+. Identical machines are not the same, there are still variations, especially desktop/laptop, and they don’t tend to stay identical for long. Mobile is a little more stable. By disabling the API (because no solution is available), this is a net gain, not a loss. Same with WebRTC: i.e leaking your IP vs not leaking it. (see ignorance 1)
Lets take an advanced script (naive ones are already fooled)
– RFP + NOT disabling WebGL/WebRTC: you are more easily fingerprinted, if not actually unique. You may have revealed your real IP. This is the exact opposite of what you claim. If people listened to you they would be fucked
– RFP + disabled WebGL/WebRTC: at least with the attack surface removed, you stand a chance (until RFP does something about it and RFP gets more mainstream)
– Brave + Strict Shields: it is compromised: canvas leaks, languages leak, device pixel ratio leaks, fonts leak, timezone leaks, locale leaks, and so on – and all those are enough to fuck Brave. Brave doesn’t stand a chance (for now)
YES, an enforced set of users, like Tor Browser, makes this _more_ effective, but it doesn’t mean it _isn’t_ effective and not a better solution that giving away a unique value or your real IP
If you learn ONE thing from all this: learn this: The key to fingerprinting protection is to not leak real values. AQnd the higher the potential entropy of those values, the higher the priority. This is why disabling WebGL and WebRTC is imperative (since they’re not covered by any built-in browser protection)
—
SUMMARY
Extensions are useless: they all leak their API meddling (moreso in chromium). The only solution is via built in browser protections. This is your only choice
– Both RFP and Brave’s Shields protect from naive scripts
– Default on protection helps against advanced scripts
– Hardened protection from extension changes and end-user fiddling also help
– Only RFP + a couple pref changes has a show of beating advanced scripts (hopefully Brave catches up soon: it just lacks too many protections)
– e.g Tor Browser is “RFP + a couple of pref changes”, Tor Browser is also an enforced set of users who are told not to make changes
Both Brave and Firefox want to be like Tor Browser
– Brave needs more protections (they already have 25mn users and a default on), and they have better compat (toggling shields per site, subtle canvas)
– Firefox needs to improve compat (canvas, allow site exceptions), add WebGL, and expose it (UI, add to PB mode)
So neither are “perfect”, but you claiming that RFP is useless, that changing any API is useless, and that Brave is better, is a massive FLoC of runny shit
@”Anonymous”
Your post is written in a very sensationalist (LIE1, IGNORANCE1 etc. blah blah) manner meant to damage me, but kudos, professionally made to sound convincing. However, you are both misrepresenting what I said, you misrepresent what Brave is and their efforts, and sometimes you are putting words in my mouth.
– Firefox by default blocks a very, very limited set of fingerprinting scripts that you can find on the weak Disconnect list. That is “nothing” in my book, especially when the EasyPrivacy list is available and could have been used. Disconnect is a joke.
– I never said that there is a “guarantee to defeat fingerprinting”, that is sensationalist nonsense I would never claim and have never claimed. Please don’t put words in my mouth.
– I am perfectly aware of the fact that there are web compat reasons for why Firefox can’t enable RFP by default, but if they can never do that(?), then Firefox users enabling this will always be a small minority group and this will make them stick out. So the question is, why is RFP even in Firefox if the “too small a crowd to hide in” issue can never be satisfactorily resolved? That means that RFP should have stayed in Tor where it belongs.
– It’s not useless to compare Brave’s fingerprinting protections and Firefox’s fingerprinting protections, despite the difficulties Mozilla has in making RFP the default. Brave and FF are the only general use browsers with fingerprinting protections and some FF users do enable this in the wild. The consequences of enabling this vs. using Brave can be discussed just fine.
– Fingerprinting protections are useless when you have no crowd to hide in + perhaps make other changes that make your fingerprint unique again.
– FF’s “robustness” causes the very web compat issues you cited as a reason for why RFP will never be enabled by default. Defeating anything more than naive scripts in a general use browser is likely an unattainable goal (because the defenses required to defeat advanced scripts create a miserable browsing experience) and you know that perfectly well. Brave is just being realistic here, and thus develops their fingerprinting defenses in a way that allows them to be enabled by default. They avoid the small crowd issue with this and I am fine with that overall goal, because, as said, it’s realistic.
– Just like @Anon7, you ride the Canvas leak to death. Yes, it is an issue worthy of criticism. No, that does not mean that it will never be fixed. No browser is leak-free, this is nonsense, Firefox also has heavy leaks e.g. extensions and WebGL.
– You say that they do not work on other important items, this is clearly false going by their GitHub, and you know that damn well, for you are also on GitHub and monitor their repo. Also, I don’t know what you expect from an implementation in its infancy? They are even calling it a work in progress officially.
– It’s true that WebGL leaks in Firefox (so much for leaks, and how well Firefox deals with naive scripts, WebGL is the second most checked item after Canvas), but disabling it solves no problem. Web compat issues this creates aside, “no value given” is, ironically, also a recordable value in and of itself, and since all other Firefox users would leak a value normally, “no value” (which is effectively a value just like any other) would stick out, that’s <1% of all FF users (if that). Tor circumvents this by disabling WebGL by default and having a large enough crowd under its belt, so it doesn't matter there. I understand that trying to hide the real values is desirable, disabling WebGL without that being the default solves no problem however. You suggesting otherwise is dangerous, users will still be unique if they really follow that advice.
– The list of different alternatives you provide is erroneous. Sure, if WebGL and WebRTC is kept at defaults, the real values leak, however, disabling them ( but you claiming that RFP is useless
I never said that the idea behind them is wrong or that their implementation is faulty (despite potential for improvement, e.g. WebGL leak). I said that it is useless to enable it in practice, however, since it is not (and will likely never be, because of web compat implications) the default of Firefox. The people enabling them amount to that changing any API is useless
Same as above with RFP, disabling WebRTC and WebGL solves no problem when only a minuscule amount of people does that. Mozilla should arrive at the conclusion that farbling is the only way here since it causes less breakage, unless they modify RFP to go more or less into the “Brave direction”, it will never get enabled by default and thus go mainstream beyond a minuscule crowd. I don’t see how the “small crowd issue” can be resolved in any other way besides Brave’s approach. Of course Tor would be unhappy about it, Mozilla and Tor would likely move into different directions then (because Tor’s implementation, forever disabled by default in Firefox, attempts to do more than beat naive scripts, which is not feasible in a general use browser(!) that aims to have some defense enabled by default).
> and that Brave is better
They have realistic goals, develop their fingerprinting protections along those lines, and therefore can enable them by default. My money is on them. You will never leave the small crowd of Firefox users who cares about this stuff, and therefore you will stay highly unique (about as bad as if you just let the real values leak) everywhere you go, in an attempt to beat uniqueness. Sorry if I don’t follow you down that path.
PS: I saw that you already got the applause of @Anon7, not sure if that is a good sign.
the Iron Heart IGNORANCE and DELIBERATE LIES continues
– still confusing implementation with effectiveness
– there are very few compat issues: canvas, timing and keyboard is it, out of hundreds of protected values with canvas being about 95% of the problem
– canvas can be bypassed per site (permanently or for session), so 95% of breakage is now solved. This is not as ideal as subtle randomness (different implementation from years apart), but as a per-site _and_ per-canvas relaxation is better than completely throwing out all protections (or large chunks of them) like Shields’ toggles
Your whining and bitching over compat has nothing to do with effectiveness
> Fingerprinting protections are useless when you have no crowd to hide in + perhaps make other changes that make your fingerprint unique again
Still a huge overflowing bucket of runny shit. You were just TOLD that RFP alone, without a default on, beats naive scripts. Yet you persist in claiming your words are twisted, that you never said things, and then you do just that, and repeat LIES.
You cannot be trusted when you REPEATEDLY and KNOWINGLY LIE
At this point one can only surmise that you have been sucked down the Brave rabbit-hole so deep that you have been indoctrinated
@Anonymous
> still confusing implementation with effectiveness
???
It’s evident to anyone who can read from my post that I am clearly making a distinction here. RFP is a valid implementation but is IMHO ineffective as long as it’s not the default. I understand that you don’t want the real values to leak but to enter into a group of there are very few compat issues: canvas, timing and keyboard is it, out of hundreds of protected values with canvas being about 95% of the problem
It’s a miserable browsing experience, why don’t you just admit that: https://old.reddit.com/r/firefox/comments/mvz21z/privacyresistfingerprinting_being_true_causes/
RFP will never get enabled by default for that reason, and thus the “too small a crowd to hide in” issue of Firefox will never get resolved. Those defenses should have stayed in Tor where this level of breakage is acceptable, as it’s an anonymity tool.
Mozilla will either create defenses closer to those of Brave and enable them by default (eliminating the “too small a crowd to hide in” issue) or everything stays as it is and Firefox’s RFP will remain placebo because hardly anyone bothers to enable it.
> canvas can be bypassed per site (permanently or for session), so 95% of breakage is now solved. This is not as ideal as subtle randomness (different implementation from years apart), but as a per-site _and_ per-canvas relaxation is better than completely throwing out all protections (or large chunks of them) like Shields’ toggles
So no Canvas protection then, to resolve the problem of the miserable browsing experience? LOL, I prefer Brave’s approach.
> Your whining and bitching over compat has nothing to do with effectiveness
It has, indirectly. Bad web compat means that RFP will never get enabled by default, lowering its de facto effectiveness for users because there is no sizable crowd to hide in. Plus, as said, one would still have to protect the network level at which point you might as well just use Tor.
> You were just TOLD that RFP alone, without a default on, beats naive scripts.
OK, but where is the advantage compared to e.g. Brave here then? You achieve the very same thing with a more miserable browsing experience on FF, how does that make sense?
> Yet you persist in claiming your words are twisted, that you never said things,
Of course I do, because you do bring up very stupid things I have clearly never said like “100% guarantee to beat fingerprinting” and similar BS, or misrepresent my argument by implying that I call RFP a bad implementation, which I didn’t do at all, I am just questioning the effectiveness of RFP seeing how almost nobody enables it in FF, and seeing how FF and Tor can be told apart at the network level (so the Tor crowd doesn’t help you here, you can’t hide in that one). IMHO, in an attempt to squash your uniqueness (FF leaking the real values, the default), you end up in a very very small group of FF users who have RFP enabled, which is hardly any better. That is a placebo solution and will remain one because, as said, RFP is not the default (default would of course enlarge the crowd using it), the Whonix devs and D. Micay understand this, but you don’t.
> You cannot be trusted when you REPEATEDLY and KNOWINGLY LIE
Strong words after you have deliberately misrepresented by argument, repeatedly.
> At this point one can only surmise that you have been sucked down the Brave rabbit-hole so deep that you have been indoctrinated
???
I think the indoctrinated ones are the people who push “hardened Firefox”, with is an absurdly small crowd of people doing this, as a solution to fingerprinting. Fingerprinting can only be fought when you have a large enough crowd to hide in, and that’s only achievable via defaults! Tor is the best solution overall, Brave is the best solution as far as general use browsers are concerned. Hardened Firefox is nonsense placebo.
You need to refrain from thinking you know how fingerprinting protection works
> Fingerprinting can only be fought when you have a large enough crowd to hide in
> RFP is a valid implementation but is IMHO ineffective as long as it’s not the default
ABSOLUTE BULLSHIT man. This is about the 50th time you have you claimed this. Brave is not hiding in a fucking crowd, it’s randomizing. So by your logic, Brave’s fingerprinting protection does not work. Do you get it now?
RFP (even if only one person in the world uses it): naive script fooled
Brave (even if only one person in the world uses it): naive script fooled
What is the difference? Why is RFP useless, but Brave works? You’re confusing why Brave has a default on. It was never to hide in a crowd, it was to give all its users protection.
> I am just questioning the effectiveness of RFP
Flip that: “I am just questioning the effectiveness of Brave’s fingerprinting protection”. It seems it can do no better than fool naive scripts, which RFP also does. So if RFP is useless, then so is Brave. Iron Heart logic.
You just don’t understand any of this, do you? Fooling naive scripts does NOT require a fucking crowd
> but where is the advantage compared to e.g. Brave here then
At it’s very BEST, Brave can only fool naive scripts (for now). RFP at it’s WORST is the equivalent of Brave, and at it’s best can fool more advanced scripts.
You’re also making a lot of assumptions, when in reality you should look at a range of possibilities. Not every advanced script will defeat RFP, but they sure as hell can defeat Brave (for now)
> It’s a miserable browsing experience, why don’t you just admit that
You’re also confusing allowing a canvas-only exception on a few sites as being able to linkify traffic. First, only a few sites would have exceptions, second it’s only one value not the whole lot (canvas is high entropy, but not that high), and third, the script would have to be universal.
Your reddit link only mentions canvas. After years of use in Tor Browser, and in Firefox, Bugzilla reports that breakage comes down to about three things, of which canvas is almost all of it. When canvas was added four years ago, it wasn’t used like today. It was also imperative that nothing be left to chance (this was designed for Tor Browser) and the simplest way was to return a blank canvas: solved. Maybe not the best solution: but an effective and easy solution. At the time they could not set up a per eTLD+1 random seed (budget, time constraints, this was around the Quantum building phase), and there were legit concerns over this method (still are).
Fast forward to today: canvas use has grown: e.g. just to upload a picture, or view a qr code (they don’t have to be, but this is what has evolved). RFP may adapt to a subtle randomness for canvas, and that would be good, because anything that reduces breakage is good. But it doesn’t stop all breakage: even Brave causes breakage: this is what happens when you deliberately break web standards. This is why Brave has a per site toggle for Shields. Does that make Shields a miserable browsing experience?
So if that is your entire argument that RFP is a miserable experience (you do not even use Firefox: I do and have with RFP for years), then you’re mistaken. A reddit post does not prove anything: all it does is confirm that breaking web standards can break web sites. And of course, you’ll never see anyone posting that the other 100+ RFP protections work flawlessly.
The answer is NOT that it is a miserable experience, the answer is 1) user education 2) lessening the breakage
RFP/Tor Browser already have ideas for lessening canvas breakage which do not include subtle randomizing – because there is a real concern that subtle randomizing is bypassable. Brave’s initial randomizing was so weak it could be bypassed. That was only just fixed last month. It’s new randomizing is better but can still be bypassed with enough time. Tor Browser wouldn’t stand for that.
You see, RFP is not Brave, it is built as a ROBUST solution
– RFP’s problem is to _NEVER_ reveal the real value – so no weaknesses allowed
– Brave problem is not the same as Tor Browser’s – Brave just wants to fool naive scripts. Brave also doesn’t want to leak the real value, but is happy to COMPROMISE for easy compat wins: it’s risk/reward
You seem to think RFP’s canvas implementation is flawed: it’s not. Brave’s implementation is a compromise. Do you understand this now? Implementation vs effectiveness. Both work, both have different implementations, but one is more “secure” than the other.
@8:13
Irony Heart clearly has reached its brain limit by even discussing RFP, and when he mentioned RFP results in miserable browsing experience, at that moment he showed he has never used Firefox in his life, heck all he knows about Firefox came from those stupid websites he mentions which recommends Windows over Linux, Pixel 3 over any phone(laughable), Https over VPN and other idiotic things.
@Yash
> and when he mentioned RFP results in miserable browsing experience, at that moment he showed he has never used Firefox in his life,
https://old.reddit.com/r/firefox/comments/mvz21z/privacyresistfingerprinting_being_true_causes/
https://old.reddit.com/r/firefox/comments/8og1nb/is_using_privacyresistfingerprinting_worth_it/e03ix10/
https://old.reddit.com/r/firefox/comments/80yqnx/google_apps_privacyresistfingerprinting_problems/
https://old.reddit.com/r/firefox/comments/mjwfv7/experience_with_privacyresistfingerprinting/
Where do all these complaints come from? Are they all my sock puppets? You are being ridiculous.
> heck all he knows about Firefox came from those stupid websites he mentions which recommends Windows over Linux,
The website doesn’t do that. It just analyzes the exploit mitigations that are in place in Windows vs. Linux. In practice, there is less malware for Linux because it is so obscure.
> Pixel 3 over any phone(laughable)
Except that he doesn’t recommend the default ROM.
> Https over VPN and other idiotic things.
LOL, don’t think so.
You are misrepresenting what the website says in malicious ways. Please stop with that type of bullshit. You now have someone to cheer on with “Anonymous” who heroically defends stuff like user.js files that have no actual use case for the reasons I mentioned above. Someone to get behind indeed, if it weren’t for your biases, you’d likely see the ridiculousness of the argument “Anonymous” makes. But hey, biases are biases and I am not here to convince you of anything.
IGNORANCE #100-billion: the breakage myth
You continue to overstate the the breakage. You added nothing new to what was already said
The four reddit links:
– link1: canvas: note reply stated use of a per site override for canvas only – education
– link2: says nothing: someone’s personal opinion with zero information – lack of education
– link3: keyboard spoofing: already mentioned
– link4: prefers-color, timezone: these are not breakage
Reddit is not scientific. Try to be more professional. Do you hear of any of the other 100+ RFP metrics failing? As already stated, all breakage is already known and documented at bugzilla. Canvas, keyboard and timing have already been stated as the root causes of “breakage”, with canvas being 95% of it. No one is saying to not try and reduce breakage, but that comes down to implementation. RFP chooses to fully randomize canvas for security reasons. Get over it.
IGNORANCE #100-billion+1: Breakage vs Usability
Breakage is when something is rendered useless: e.g.
– fully randomized canvas
– timing protection causing jank in a game
– disabling a web API
Usability is when the result does not match user outcome. This is not the same as compat: compat implies breakage: the solutions here are fully compatible: e.g.
– timezone is not their own
– pages are loaded in a different language
– formats (datetime, currency etc) are not in the expected locale
– returning something like prefers-color: user expected dark, got light
IGNORANCE #100billion+2: Usability issues are universal
When it comes to usability on those same metrics, Brave has the same issue. They cannot successfully change the users timezone, language, locale, prefers color and other CSS4 options, etc without all web pages changing the expected result
IGNORANCE #100billion+3: Education
The key is education, which you have rubbished. You seem to think Brave can lie about everything without consequences. Brave also cannot successfully lie about these (usability issues) without the end user having some inconvenience. Until they do (they can’t) then your silly argument is just that: silly. When they add these, I presume to Strict mode only, they are going to have to educate their users about it.
—
You keep making up arguments against the wisdom and knowledge of a decade+ of thousands and thousands of Tor and Mozilla devs, independent researchers, tests, the-entire-world, studies, papers. So who is right – them or the mighty ignorant Iron Heart?
Ladies and gentlemen, Iron Heart has done it again, as soon as I said he has never used Firefox, his stupid links came soon after. Hey Iron Heart * [Editor: removed, please stay polite], if you’ve never used a thing in your life like Firefox or better RFP in Firefox, its better for you to STFU because all you’re doing right now is showing complete and utter stupidity. These two things from you – 1. ‘To prevent browser fingerprinting you need a large enough crowd to hide in and that’s only possible in default settings’ is nonsense. You haven’t got a clue of what Browser fingerprinting really is, Kid.
2. RFP results in miserable browsing experience – good statement from a so called Default setting browser fingerprinting expert like you which is BS. Clearly you haven’t used anything apart from Brave and that includes Tor, as Tor has RFP enabled and browsing experience is not miserable even in Safest setting.
An advice to you * [Editor: removed, please stay polite]- The time has come for you to remove your blanket, leave your bed, your room, your house and walk outside and feel fresh air, do some workout, see things happening around you, it’ll help. That’s the advice I’ve given * [Editor: removed, please stay polite] and it worked well.
Hey I didn’t knew saying a word which describes age group between young ones and grown ups is censored, but okay, it was my mistake along with making fun of his name, I should be more polite and not lose my cool especially for a guy like Iron Heart who doesn’t know anything about Browser Fingerprinting. The discussion between Iron Heart and Pants(thanks @anonymous 9:34 a.m. for providing that) was interesting to say the least. Atleast I now know I don’t have to write essays to explain anything to Iron Heart as he ain’t got a clue.
@Anonymous
> ABSOLUTE BULLSHIT man. This is about the 50th time you have you claimed this. Brave is not hiding in a fucking crowd, it’s randomizing. So by your logic, Brave’s fingerprinting protection does not work. Do you get it now?
Whom are you trying to fool here? Brave users form a crowd because all of them are randomizing, websites see randomized output for all Brave users. They all have the same type of fingerprint, the very same behavioral output even though the concrete values differ, as is intended for randomizing! Firefox has RFP disabled by default, and only a minuscule amount of people enable RFP. The minuscule crowd that has RFP enabled is not big enough to hide in, because websites can tell that you are not using Tor (so you are not hiding within the Tor crowd).
> RFP (even if only one person in the world uses it): naive script fooled
> Brave (even if only one person in the world uses it): naive script fooled
Yeah, and? That’s the only realistic goal and both get it done.
> Why is RFP useless, but Brave works?
You are still misrepresenting what I said, lol. RFP as an implementation is not useless, but its effectiveness in the wild is limited because hardly anyone enables it.
Plus, even with RFP, your real IP address would still be known to websites, rendering this effort useless, unless you also introduce network-level protection. At this point with FF + VPN or FF + onion routing, you might as well just use the Tor Browser Bundle.
> You just don’t understand any of this, do you? Fooling naive scripts does NOT require a fucking crowd
I understand this. It follows from this that RFP is not a pro-Firefox argument, because Brave can do the same thing (fooling naive scripts), with a less miserable browsing experience to boot. For advanced scripts you need a crowd and RFP (disabled by default) can never provide that outside of Tor.
> At it’s very BEST, Brave can only fool naive scripts (for now). RFP at it’s WORST is the equivalent of Brave, and at it’s best can fool more advanced scripts.
You need a crowd to hide in for advanced scripts, so nope. Plus, no network-level protection in FF. Face it, there is no use case for RFP outside of the Tor Browser Bundle, where it actually belongs.
> Not every advanced script will defeat RFP, but they sure as hell can defeat Brave (for now)
Brave is a general use browser. They do not want a miserable browsing experience for their users. However, advanced defenses so far create a miserable browsing experience. Beating advanced scripts is therefore not a realistic goal for general use browsers and should be left to special tools like the Tor Browser Bundle.
Advanced scripts also run circles around FF + RFP (small crowd) + no network-level protection, and FF + RFP + network-level protection = Tor Browser Bundle. There is no use case for RFP in FF that exceeds fooling naive scripts (which Brave can also do).
> You’re also confusing allowing a canvas-only exception on a few sites as being able to linkify traffic. First, only a few sites would have exceptions, second it’s only one value not the whole lot (canvas is high entropy, but not that high), and third, the script would have to be universal.
“Only a few websites” – I doubt, because a great many websites use Canvas, i.e. “canvas use has grown”, so there would have to be lots of exceptions because of the sheer amount of breakage. And also, the fingerprinting scripts are usually distributed by advertisers and are not first party scripts for the most part, so they are also universal more often than not.
> But it doesn’t stop all breakage: even Brave causes breakage: this is what happens when you deliberately break web standards. This is why Brave has a per site toggle for Shields. Does that make Shields a miserable browsing experience?
Brave’s FP defenses don’t cause a lot of breakage for Canvas because they are at least outputting something: randomized output. Tor and FF return blank which causes the breakage you see in the link I’ve shown you. It’s fairly miserable for end users (until eventually fixed).
> So if that is your entire argument that RFP is a miserable experience (you do not even use Firefox: I do and have with RFP for years), then you’re mistaken.
I actually have Firefox + arkenfox user.js applied here and it’s a shitty experience.
> A reddit post does not prove anything: all it does is confirm that breaking web standards can break web sites
Randomized output would prevent most breakage.
> The answer is NOT that it is a miserable experience, the answer is 1) user education 2) lessening the breakage
You can educate as much as you want, this breakage is not acceptable and will never be acceptable in a general use browser, if the goal is to have RFP enabled by default eventually (to do away with the small crowd issue). Period. So “lessening the breakage” (by adopting randomizing that is closer to what Brave does, lol) is the only way.
> Brave’s initial randomizing was so weak it could be bypassed. That was only just fixed last month. It’s new randomizing is better but can still be bypassed with enough time. Tor Browser wouldn’t stand for that.
Brave is a general use browser and only a certain degree of breakage is acceptable there. The same goes for Firefox, Firefox would have to modify RFP to reduce breakage eventually, too. Breakage is more acceptable in special tools like Tor which strongly prioritize privacy over web compatibility.
> RFP’s problem is to _NEVER_ reveal the real value – so no weaknesses allowed
You are in a small crowd + they have your IP address. There is no use case for this, might as well use the Tor Browser Bundle at this stage.
> Brave problem is not the same as Tor Browser’s – Brave just wants to fool naive scripts. Brave also doesn’t want to leak the real value, but is happy to COMPROMISE for easy compat wins: it’s risk/reward
So what you describe is a general use browser, LOL. RFP in its current form has no place in Firefox – as it is, it will never get enabled by default (they’d have to make adjustments that are very close to what Brave does), therefore the people who have it enabled by their own volition will remain a minuscule crowd + no network level protection anyway. It shows that this was designed for Tor, you see.
> You seem to think RFP’s canvas implementation is flawed: it’s not.
It achieves its intended goal but causes breakage. This is the reason why it isn’t enabled by default.
> Brave’s implementation is a compromise. Do you understand this now? Implementation vs effectiveness.
The practical effectiveness of RFP against advanced scripts is hampered by the fact that hardly anyone uses it and because there is no network-level protection (they still have your real IP address). The obvious and only solution for this is Tor, but that means that there is no actual use case for RFP in Firefox that would exceed fooling naive scripts – which is the same thing Brave does, except that they don’t create a miserable browsing experience in the process that should only be acceptable for Tor (which is where RFP comes from).
Brave is the best general use browser (fools naive scripts + browsing experience is acceptable), all those user.js files imitating Tor’s config have no use case to them (small crowd issue, no network-level protection, breakage caused). The breakage RFP causes is not acceptable for general use and if you are afraid of advanced scripts, you’d likely also protect the network level and would thus just use Tor. There is no point in Tor mimicry, there is no point to user.js files.
You just continue to show your absolute ignorance. You read something that seems to fit your narrative, then you take it and warp it into an argument in order to attack Firefox. And you just will not stop even in the face of proof. You DELIBERATELY KEEP LYING.
> Tor and FF return blank
They do no such thing. It’s randomized. Fucking hell. What is this, baby school? Learn to read and understand your subject (however, it is clear that you are incapable of this)
> Randomized output would prevent most breakage
jesus fucking h christ. It (canvas in RFP) is already randomized. That’s not how it works. Randomizing is not the reason for breakage or non-breakage. The same goes for spoofing a static value. The method is not why breakage occurs.
> Brave users form a crowd because all of them are randomizing
You truly have the intellect of a three year old. The whole point of randomizing is to not be in a crowd. Brave users are NOT IN A CROWD. Hello, is anyone home?
Despite mathematical proof that 1+1=2, you keep arguing that it equals magic pixie dust or something.
Everything you have spammed over and over again on ghacks about fingerprinting is so fucked up. You clearly have zero knowledge on the subject. You have shown time and time again that you do not understand
– web and browser APIs
– fingerprinting methods
– fingerprinting defenses
– entropy
– linkability
– the list is endless
You are not an expert on anything, your knowledge is horrifically abysmal. * [Editor: removed]
@”Anonymous”
> You DELIBERATELY KEEP LYING.
And you keep being insolent, but whatever. Contrary to you, I am not complaining because from prior exchanges, I really expect no different.
> They do no such thing. It’s randomized. Fucking hell. What is this, baby school? Learn to read and understand your subject (however, it is clear that you are incapable of this)
Decide:
> Your reddit link only mentions canvas. After years of use in Tor Browser, and in Firefox, Bugzilla reports that breakage comes down to about three things, of which canvas is almost all of it. When canvas was added four years ago, it wasn’t used like today. It was also imperative that nothing be left to chance (this was designed for Tor Browser) and the simplest way was to return a BLANK CANVAS(!!!): solved. Maybe not the best solution: but an effective and easy solution. At the time they could not set up a per eTLD+1 random seed (budget, time constraints, this was around the Quantum building phase), and there were legit concerns over this method (still are).
Fast forward to today: canvas use has grown: e.g. just to upload a picture, or view a qr code (they don’t have to be, but this is what has evolved). RFP MAY ADAPT TO A SUBTLE RANDOMNESS FOR CANVAS,
Anyway, even if the Canvas protections switched from “blank” to “strong randomness”, this does not really invalidate the argument I am making: It still causes breakage.
> jesus fucking h christ. It (canvas in RFP) is already randomized. That’s not how it works. Randomizing is not the reason for breakage or non-breakage. The same goes for spoofing a static value. The method is not why breakage occurs.
So? Tell me your story, what causes the breakage then? Can’t be the real values (no breakage), so if it isn’t caused by randomness… what causes it?
> You truly have the intellect of a three year old. The whole point of randomizing is to not be in a crowd. Brave users are NOT IN A CROWD. Hello, is anyone home?
They are. They all return random values (of course not the same values), and this randomness can be detected. This randomness also makes them recognizable as Brave users. They have the same behavioral fingerprint.
> You have shown time and time again that you do not understand
Cool, and you don’t understand that there is no actual use case for placebo user.js files when Tor already exists.
> You are not an expert on anything, your knowledge is horrifically abysmal.
So? You still don’t seem to understand that if there is no (behavioral) crowd to hide in, fingerprinting defenses are rendered ineffective against advanced scripts. Against naive scripts, both Firefox and Brave can defend. Tor is the only way to beat advanced scripts because it delivers a sizable crowd to hide in + has network-level protection. People like the Whonix team and Micay understand that, and you don’t. Or perhaps you just don’t want to admit it because that would reveal a certain project that is done for self-gratification as pointless. Who knows, not my problem.
You have been told numerous times that RFP changed to a fully random canvas per execution. You have been told numerous times that RFP fools naive scripts BECAUSE canvas is being randomized
– Do you not understand that this: “When canvas was added FOUR years ago… blank canvas”
– Do you not understand the difference between Brave’s _subtle_ (per eTLD+1 random seed) vs RFP’s _fully_ (per execution, every pixel, totally random values for all channels)
You kept claiming (dozens and dozens of times) that RFP did nothing in Firefox… and here we are quote you “Against naive scripts, both Firefox and Brave can defend” – and that’s only because you were told dozens and dozens of times.
Your claim about compat has zero to do with effectiveness.
Your claim about being in a crowd has zero to do with naive scripts.
You argued over and over in previous article comments that Brave’s farbling couldn’t be rendered to static results. NOW, you actually agree, quote you “and this randomness can be detected” – but only because you had to be told dozens and dozens of times
You claimed Brave’s raising entropy was the best, and you attacked RFP as useless and you even attacked Tor Browser’s implementation. You claimed that lowering entropy doesn’t work. But NOW you realize that randomizing can be bypassed in advanced scripts, because someone had to tell you dozens of times, and that ultimately everything is lowered entropy
You claimed that a single Tor Browser user who visits a site means their traffic on that site is linkable because they are the only Tor User to visit that site – the site cannot know that when hundreds of thousands of users have the same fingerprint
You have even argued that “gibberish” such as Brave’s plugins is superior as a solution. And above you have claimed that static vs randomized values is the root cause of breakage. What causes the breakage is the limitations of the API and how it is used. Each API/metric will differ.
Not once have I disagreed with Whonix or Micay. In fact I agreed with them. I said that when it comes to advanced scripts (i.e randomness is detected, i.e not naive), that a crowd is required. See above where I said Firefox and Brave want to be like Tor Browser
– Brave’s default on (or crowd) is useless until they get more metrics protected
– Firefox’s RFP is far more advanced, but needs “some” uptake (and webGL: webRTC)
– Right now Brave’s default on means ZERO, because it lacks protection.
—
the mythical “crowd”
You have claimed things like fonts and screen metrics aren’t a big deal
– https://www.ghacks.net/2021/02/10/brave-browser-adds-native-support-for-ublock-and-fanboy-annoyances-lists-and-social-list/#comment-4485851
– quote: “You can’t generalize the uniqueness of the real values like that. If I use Firefox on a Windows 10 PC, only the default fonts (or whatever comes with MS Office) installed, popular processor, popular screen resolution, popular GPU etc., the uniqueness of these values, the real values I mean, is not too great”
The truth is the uniqueness of those can be evaluated, because there are studies. After you shit on pants, who you hounded for her credentials and after Martin confirmed her as an expert, you simply said something like “I don’t care, she’s wrong” – you just discard experts and proof when it doesn’t fit your twisted narrative
Here is a mozilla engineer, who has worked on Tor Uplift, confirming what pants said
– https://lists.torproject.org/pipermail/tbb-dev/2021-January/001180.html
– “window size + fonts + canvas – and maybe just two or even one of those – are enough to uniquely identify a user”
Here is a real world study, again confirming what pants said
– https://yinzhicao.org/fpmeasurement/imc20.pdf
– fonts alone is 115 thousand distinct groups
– languages is 14 thousand
– pixel device ratio (a screen metric) is another 2 thousand
Brave is fucked in your so called “crowd”: fonts, pixel device ratio, languages, timezone, screen, available screen, and the still leaking canvas = FUCKED. Brave is years behind
A “crowd” only matter with advanced scripts. A “crowd” only matters when you protect enough metrics
Brave’s being in a crowd is not even a thing. That’s not criticizing Brave, that’s criticizing you and your ignorance on the subject
In the same comment you said
> Against naive scripts, both Firefox and Brave can defend
> there is no actual use case for placebo user.js files when Tor already exists
You’re CONTRADICTING yourself. Your whole argument against hardening Firefox is that it changes your fingerprint and therefore is a waste of time. But you have just, finally, agreed that Firefox’s RFP being enabled gives extra protection. It’s a net gain.
Also
– What about all the naive scripts it defeats?
– What about all the advanced scripts it defeats: not all scripts are the same
– What about all the sites where a fingerprinting script fails or never runs
– Not all preference changes can be fingerprinted
– Firefox users are not trying to be Tor Browser
– Firefox without Tor protocol has advantages (latency, non-Tor-exit node blocking)
– There’s a thing called a threat model: look it up
– Doing nothing you are already unique
– By your own admission, you make changes to your setup that are fingerprintable (e.g DRM)
– The network has nothing to do with JS fingerprinting: it is an assumption that your IP is protected. Why is Brave any different to Firefox in this regard. Stick to the topic and stop bringing up red herrings
> Tor is the only way to beat advanced scripts
FALSE. You only ever think in binary terms. Fingerprinting is about degrees – not all advanced scripts are the same. RFP is 95% of the way there on it’s own.
————-
I’m going to bring expand on this to show just how silly your arguments are
FP IGNORANCE #743: doesn’t understand that solutions need to be universal
– https://www.ghacks.net/2021/02/10/brave-browser-adds-native-support-for-ublock-and-fanboy-annoyances-lists-and-social-list/#comment-4485851
– quote Iron Heart: “You can’t generalize the uniqueness of the real values like that. If I use Firefox on a Windows 10 PC, only the default fonts (or whatever comes with MS Office) installed, popular processor, popular screen resolution, popular GPU etc., the uniqueness of these values, the real values I mean, is not too greatâ€
even if you think YOUR setup has enough users to hide in, everyone else is still fucked
FP IGNORANCE #i-lost-count: the mythical “identical” system
– setups like that described above, e.g. factory resets, do not exist for long. Changes such as system scaling, system text size, system themes + accessibility, browser default zoom and text size and default font, GPU changes such as drivers etc – additional fonts is a real killer – to name but a few
– even your so called “identical systems” have differences that can be exploited if you dig deep enough
————-
You seem convinced that Firefox will never get the same degree of fingerprinting protection as Tor Browser
In (JS) fingerprinting, Tor Browser is essentially RFP + a couple of pref changes. Firefox is the only browser capable of adding a Tor Mode window. This is 95% done – has been for 2+ years
Did you know that there was a prototype system addon developed over three years ago, that added a Tor Mode window to Firefox? When used, it created a new window with a temp Tor Mode profile, exactly the same as Tor Browser. The only reason it’s not there yet, is because they can’t just throw 220 million potential users at the Tor network. That said, all RFP needs to be a standalone feature in Firefox (without Tor), is a couple more changes (such as per site toggling, webgl) and user education (expectations)
“Tor Uplift” took a pause for several years: with higher priorities and bigger payback: finishing webrender, warp+stencil, major backend build changes, fission, dFPI + network partitioning, non-native themes (which is a fingerprint vector this solves) and other more immediate results. Fingerprinting is not the threat you think it is. Scripts need to be universal (for multi-site linking)
Now that those more immediate things are well under way and/or wrapping up, after two years, RFP is being looked at again, with REAL and ROBUST solutions – moreso given third party cookies are being phased out. Expect fingerprinting in the wild to expand and get more sophisticated
Brave on the other hand, will NEVER gain a crowd to hide in
– they only care about naive scripts
– they CANNOT protect everything they need to because they lack the ability to do so (it would require major re-engineering) and some of 100+ metrics RFP protects against, Brave has the same issues and won’t do it, because they favor usability over protection
Brave: naive only, don’t make anything too hard for users to understand (limited protection)
RFP: _never_ give in, real robust solutions, educate users
You keep thinking Brave can lie about everything and that everything will still work as expected. You’re wrong. The cannot successfully change a user’s timezone without the end user getting times different to their own: there are almost 450 timezones. They cannot successfully change the primary language and locale without the end user getting all languages requests and formatting to be different to their own.
You keep rubbishing the notion of educating users: but that is what is actually key: managing their expectations and training them to work within it. Tor Browser, RFP, Mozilla know what they are doing: no compromises, education.
Brave is not trying to be like RFP or Tor Browser, because they can’t, and they never will
Why are you so angry about Tor Browser, about RFP, about Mozilla, about Firefox? Why do you do this?
> ???
Seems like a very apt reply since you do not understand how fingerprinting works
> ???
You did it twice. Go to a comprehension school
@Anonymous
Just admit that you have no clue and promote clear placebo solutions here because you are in love with a brand while hating on another.
@Anonymous
> So neither are “perfectâ€, but you claiming that RFP is useless, that changing any API is useless, and that Brave is better, is a massive FLoC of runny shit
Iron Heart has not a clue what he is talking about as regards fingerprinting. No essays with his walls of text would prove otherwise.
He does not even recognise that there are many theories and thoughts around it aswell. He paints everything black and white with no dynamic thought at all. Its very narrow sighted.
See this comment here from him. No idea what he is on about. He does not understand that if you do not disable WebRTC it leaks IP address.
IP address is an accurate form of fingerprinting.
> Disabling WebRTC and WebGL would make you far easier to fingerprint, not harder.
ClownWorld stuff from him as usual.
Wow just wow. You said all things correctly but unfortunately some people who don’t understand the marketing gimmicks and all sorts of adverts especially when coming from a software which promote itself by not saying things fairly, but by throwing mud at some others; and some basic fingerprinting protection are still gonna find an excuse and garbage to ignore all this.
The Mozilla marketing department strikes again, using many buzzwords they don’t understand, describing features that are not even exclusive to FF in most cases.
Desperate because 4% market share is closer to 0% than anyone can be comfortable with?
@Iron Heart – Things that been written for the favor of firefox done probably by real users that love the browser and they unpaid by no one. But all your thousands of scrolls about bashing Firefox to the favor of your ad company browser’s brave are something no real user have time to write or read.
@Iron Heart: Brave marketing department strikes again.
> Desperate because 4% market share is closer to 0%
Imagine someone hating a browser so much that they have to comment with extreme negativity on any FF related article just for spite, to refute any positive FF comment just for spite.
Imagine hating a browser developer so much that someone would want to see their market share go to 0%.
Christ.
0% market share is a rounding error #BRAVE2024
@Iron Heart,
how is your livinig nowadays with a browser, that has actually 8 times lower market share than FF, close to that 0%?
What makes your rants especially funny, is that you say sooo much about how brave is so privacy oriented, how much they fix in chromium, close down googly spying here and there, and place it against a browser group (ff, tor, pm, iceweasel, iceraven, waterfox etc) that don’t have to fix loopholes made by google and that actually focus and develop active safety and privacy features. What Brave is doing It’s like using makeup on pimples on googles face… the ugly truth is still down there. An example from last week – FloC. Chrome and chromium are products that serve one primary purpose – income through advertising and mass collection of data. Ability to render pages is just a neccessity here. You can’t even say that Mozilla has it bacwards, because there is NO hidden mass data colection and resale, no advertising income. There is browsing only. Mozilla eventually may gather money but by other means, one being a contract with google. And believe me, out of hundreds of employees there would be at least one wistleblower if there was a clause in contract that would make mozilla play by google directions. Ask that Brendan-advertising-first guy about that, he worked there.
And every time you make assumptions that are simply not true: that google is directing through funding what FF does with their browser; that Mozilla has nothing to say in W3C (remember that Brave and others have actually nothing to say); that brave can be tweaked more than FF (no it can’t be, it can be as much tweaked as google lets it at the moment for THEIR purpose – I’m not saying evil, but still); that pocket and clicks FF bad, in brave good; that telemetry is bad (no, it’s not).
And so many times you were answered and proved wrong here, I guess elswere (reddit?) similar. And you repeat same lies, misinformation, twist facts to fit your points of view, use years old links to some niche, not recognised blogs. Who cares? Firefox is a good browser, it pushed internet from a boring IE era to sth better. The only thing you managed so far is that you scare people away from ghacks comments. Because your theories stink. Simple as that. I am so uncomfortable with your rants here, probably you are the same knowing your browsers market share.
There was a funny theory few days ago – that Brave is talking with Mozilla about switch to gecko. That would be a funny day for you, would it?
@m3city
> and place it against a browser group (ff, tor, pm, iceweasel, iceraven, waterfox etc) that don’t have to fix loopholes made by google and that actually focus and develop active safety and privacy features.
The browsers you mentioned except for Firefox, that is, Pale Moon, IceWeasel, Iceraven, and Waterfox, actually have to fix the privacy issues of Firefox in their own builds, hence why they even exist as forks. *facepalm*
> What Brave is doing It’s like using makeup on pimples on googles face… the ugly truth is still down there.
That’s also the case with Firefox forks, your point being?
> Chrome and chromium are products that serve one primary purpose – income through advertising and mass collection of data.
Firefox serves the purpose of acting as Google-dependent fake opposition allowing the same thing by default. Firefox’s default config is NOT privacy-respecting:
> It shares your location and download hashes with Google. it uses Google Analytics internally. It has a weak tracking blocker (using the shitty Disconnect lists). It allows most forms of prefetching. Fingerprinting defenses are inactive by default. It installs system level telemetry that spies on your default browser even if it isn’t Firefox. It has a backdoor that allows for remote code execution (called “Firefox Experiments†/ Normandy). Its Sync requires E-Mail addresses. Leaks unique extension IDs via simple fetch requests. Connects speculatively to websites as you type addresses in the address bar. Uses Cloudflare for DoH (I am sure the DNS entries are safe in their hands!) etc.
> You can’t even say that Mozilla has it bacwards, because there is NO hidden mass data colection and resale
LOL:
https://www.zdnet.com/article/firefox-tests-cliqz-engine-which-slurps-user-browsing-data/
https://old.reddit.com/r/privacy/comments/blt6ft/mobile_firefox_app_shares_your_data_with/
https://blog.mozilla.org/press/2018/08/firefox-offers-recommendations-with-latest-test-pilot-experiment-advance/
Wake up.
> And believe me, out of hundreds of employees there would be at least one wistleblower if there was a clause in contract that would make mozilla play by google directions.
You don’t need a whistleblower. Suffices that you take a look at FF’s default config which most of its users never change. It allows most spying methods by default.
> Ask that Brendan-advertising-first guy about that, he worked there.
Brave pioneers a new, privacy-respecting model of advertising and is self-sufficient with this. They do not need to leech Google with all attached consequences.
> that google is directing through funding what FF does with their browser; that Mozilla has nothing to say in W3C (remember that Brave and others have actually nothing to say);
Prove to me that this is not the case using about:config, and by citing all the Google proposals Mozilla has successfully opposed so far. Your clueless colleague @Anon7 couldn’t do it, perhaps you can.
> that brave can be tweaked more than FF (no it can’t be, it can be as much tweaked as google lets it at the moment for THEIR purpose – I’m not saying evil, but still);
I didn’t say that, I said that Brave doesn’t need to be tweaked as much as Firefox by default, which is a good thing re. fingerprinting, what you FF users do is to fingerprint yourself:
“Providing the offer to disable features to reduce attack surface can be useful. Doing it to prevent fingerprinting is utter nonsense since by changing any settings that sites can detect you have made yourself far more easily fingerprinted. Disabling WebRTC and WebGL would make you far easier to fingerprint, not harder. These sites encouraging things like that is a problem.”
source: https://old.reddit.com/r/GrapheneOS/comments/ciizae/vanadium_and_bromium_privacy/ev6m2ot/
> hat pocket and clicks FF bad, in brave good;
LOL, I never said that. Wouldn’t even make sense.
> that telemetry is bad (no, it’s not).
Hahaha, depends on how invasive the telemetry is. For example, Firefox collects telemetry about the users who have opted out of telemetry(!) and has this setting hidden, Firefox installs system level telemetry spying on your default browser even if it isn’t Firefox. There should be limits, you know.
> And so many times you were answered and proved wrong here, I guess elswere (reddit?) similar.
OK, where? I have no Reddit account, by the way.
> And you repeat same lies, misinformation, twist facts to fit your points of view, use years old links to some niche, not recognised blogs. Who cares?
You should care unless you can actually credibly refute anything I say. Until then, I suppose I will just have to take up with your weak ad hominems and your bickering.
> Who cares? Firefox is a good browser, it pushed internet from a boring IE era to sth better.
FF at one point respected user choice, user agency, and user privacy. If it still did, I would still respect Firefox. Times change. Deplatformingfox is a more recent development, haha.
> There was a funny theory few days ago – that Brave is talking with Mozilla about switch to gecko. That would be a funny day for you, would it?
Unsubstantiated bullshit touted by @Anon7, he had no source to present when I asked him for one. Look, people can pull whatever they wish out of their collective behinds, that doesn’t make it credible, unless it’s being substantiated.
> how is your livinig nowadays with a browser, that has actually 8 times lower market share than FF, close to that 0%?
You should be much more worried than you are at this point:
https://brave.com/25m-mau/
https://calpaterson.com/mozilla.html
Besides, Chromium, which Brave builds on, actually has 80% of the browser market under its belt, which is 20 times the users of Firefox. Brave doesn’t need its engine to succeed, it already has succeeded. They only need to be financially self-sufficient as a company.
jesus fucking christ, give it a rest Iron Heart
@another anon
Make @Anon7 quit his bullshit claims and I will. I promise.
You can take over from here on, if you wish.
@Irony Heart.
> The browsers you mentioned except for Firefox, that is, Pale Moon, IceWeasel, Iceraven, and Waterfox,
Most if not all those browsers rely on the hard work of mozilla devs. Without mozilla they would not exist. Therefore mozilla are important.
> That’s also the case with Firefox forks, your point being?
His point being is that in chromium it is more difficult to stop the crap from upstream google.
Mozilla forks do not have to deal with so much crap. Because chromium is primarily used for closed source big tech browsers. Gecko is different.
> Firefox’s default config is NOT privacy-respecting:
Mr Fear Merchant strikes again. Default Firefox is still secure and private with a few toggles turned off in the GUI, tracking protection on and the search engine changed.
Telemetry is nowhere near as bad as you make out nor is the google hashes or analytics, as they are basically anonymised on requirement from mozilla.
And with simple hardening, 15 minutes max you get more privacy.
> https://www.zdnet.com/article/firefox-tests-cliqz-engine-which-slurps-user-browsing-data/
Old news! That also did not affect the majority of FF Users.
> Wake up.
People are awake to your BS and FUD.
Hows your time Irony Heart? Want to post an attempt to refute and waste hours of your time again?
This is your priority in life right?
> FF’s default config
Yawn.
> Brave pioneers a new, privacy-respecting model of advertising and is self-sufficient with this. They do not need to leech Google with all attached consequences.
Attached consequences? yeah sure, funny how they were messing with an internal ad-blocker which broke their tor windows for months. But thats what happens when a so-called privacy browser is RELIANT on crap from google upstream (chromium)
Try again Irony Heart. I await your essay. Lulz.
> Google proposals Mozilla has successfully opposed so far.
I don’t see mozilla having to deal with chromium FLoCK from chromium.
Brave will certainly have a job to do when google starts embedding it more strongly into the code of chromium in future releases.
Oh apparently there are rumours of Brave switching to gecko as some posters have commented on?
If that happened, i doubt you would use your current handle posting here.
> fingerprinting,
Brave leaks canvas. Enjoy the poor fingerprinting defenses of your beloved.
Come on Iron Heart? Thats another essay for you to type up.
> : https://old.reddit.com/r/GrapheneOS/comments/ciizae/vanadium_and_bromium_privacy/ev6m2ot/
FUD!
A more unique fingerprint shows that a browser is not using a more insecure set up, = more security usually. And hardened FF is very secure.
Many ideas of thought on fingerprinting. The link you spam is only an opinion nothing more.
You spam it every article? obsessed much?
> Firefox collects telemetry about the users who have opted out of telemetry
Their telemetry is not malicious, all it collects is how the browser is interacted with. They use it to improve itheir browser. And it can all be turned off anyway.
Another essay for that comment? get a life buddy.
> And you repeat same lies, misinformation, twist facts to fit your points of view, use years old links to some niche, not recognised blogs. Who cares?
+1 m3city
> FF at one point respected user choice, user agency, and user privacy.
They still do.
> Deplatformingfox
Who have they deplatformed? As i said before your comparisons of mozilla to google is absurd. MOzilla is not google therefore can not deplatform anyone.
Another essay? feel free to waste more of your time buddy.
> Brave is talking with Mozilla about switch to gecko.
It was Emil who started that talk. I would not be surprised at all if its true.
A good day for brave if they do change to gecko.
Another essay? lol
> Chromium, which Brave builds on, actually has 80% of the browser market under its belt, which is 20 times the users of Firefox.
Google code is what brave builds on.
There is a correction for you buddy.
I await your essay.
Chuckles.
@Anon7
Why should I write an essay in response to your usual old one liners? One liners deserve no more than one liners in response.
> Irony Heart.
Kindergarten.
> Most if not all those browsers rely on the hard work of mozilla devs. Without mozilla they would not exist. Therefore mozilla are important.
Most if not all those browsers rely on the hard work of Google devs. Without Google they would not exist. Therefore Google are important.
> Default Firefox is still secure and private with a few toggles turned off in the GUI, tracking protection on and the search engine changed.
LOL, no. Why do you think those Firefox mitigation guides are much longer than this? Just for fun?
> nor is the google hashes or analytics, as they are basically anonymised on requirement from mozilla.
:…………D
You have access to those Google servers? Were you privy to their contract clauses? No? Then stop speculation and assume a privacy intrusion unless proven otherwise. Assuming the worst for Brave (who luckily actually anonymize e.g. SafeBrowsing requests via proxy, while Mozilla can’t be bothered) but assuming the best for Mozilla is biased idiocy.
> Old news! That also did not affect the majority of FF Users.
Ah, so it’s old news here, but you bring up the Ungoogled Chromium incident (that was not even deliberate, while Mozilla acted deliberately), which is even older? LOL.
But hey, we can also talk about the Mr. Robot add-on or the Mozilla-LaserLike partnership…
> Yawn.
Unfortunately not “Yawn” when most people use their browser with the defaults, plus the defaults of other browsers are better (Brave), why can’t Mozilla do the same? Care to elaborate?
> Attached consequences?
Firefox’s inaction against Google spying. Their tracking protection doesn’t even block trackers in non-private windows, which is ridiculous for the “privacy browser”. But then, why would they? They are already using Google Analytics internally, so…
> funny how they were messing with an internal ad-blocker which broke their tor windows for months.
Resolved fixed:
https://github.com/brave/brave-browser/issues/12575
It worked normally with Shields turned off, by the way. Since you accept deviations from the defaults in comparisons, I could just go down the same route and say that the users could have just turned Shields off, which would have resolved the problem for them, right? But I am not that stupid, take problems seriously, and actually expect the Brave devs to fix privacy issues, and they did. Yeah, they actually fix their stuff, contrary to some other companies that can’t be bothered to look at similar leaks after 4 years…
https://bugzilla.mozilla.org/show_bug.cgi?id=1405971
https://bugzilla.mozilla.org/show_bug.cgi?id=1372288
> But thats what happens when a so-called privacy browser is RELIANT on crap from google upstream (chromium)
Tor also has to deal with leaks introduced by Mozilla on a frequent basis. But hey, ignorance is bliss.
> I don’t see mozilla having to deal with chromium FLoCK from chromium.
They will implement Web Bundles which is even worse. Wait and see.
> If that happened, i doubt you would use your current handle posting here.
Won’t happen, it’s just a baseless rumor crafted by two “real experts”, namely you and @Emil Brausewetter. No company wants to base their browser off a dying engine, that’s just an unrealistic wet dream of yours.
> Brave leaks canvas. Enjoy the poor fingerprinting defenses of your beloved.
Firefox leaks extension IDs (unique per user). By default, Firefox leaks all canvas values. If you deviate from the defaults, you will be very unique wherever you go. How is that better, you fool?
Brave’s implementation is also still in its infancy, it will be fixed (hopefully they won’t take 4+ years like Mozilla).
> FUD!
I am afraid not. The guy is perfectly reasonable (a quality you never seem to espouse), you just don’t like what he says and you can’t refute him.
> You spam it every article? obsessed much?
Of course I do. Why? Because YOU come up with the same asinine ideas under every article, which Micay soundly refutes in his post.
> Their telemetry is not malicious
“No.” means “No.” which Mozilla doesn’t seem to respect, collecting telemetry about users who have explicitly disabled telemetry? Really? LOL. Firefox also installs system level telemetry and is the only browser that does this AFAIK. It’s also the only browser using embedded third party trackers on Android. :D
> They still do.
Nope, they have removed about:config (together with most add-ons, haha) on Android and recently introduce connections for which they don’t provide about:config switches on the desktop. How is that respecting user choice and user privacy?
> Who have they deplatformed? As i said before your comparisons of mozilla to google is absurd. MOzilla is not google therefore can not deplatform anyone.
https://twitter.com/mozilla/status/1347633954497548289
“Turn on by default the tools to amplify factual voices over disinformation.” – I guess whatever Mozilla’s Google cronies decide is a factual voice, is in fact a factual voice. Mozilla is supportive of censorship and you supporting them is moral bankruptcy, plain and simple.
> A good day for brave if they do change to gecko.
Switching to a dying technology is a good day? Said no one ever. But then, it’s still a baseless rumor which you pulled out of your behind, no sources presented.
> Google code is what brave builds on.
Google money is what Mozilla needs to even exist.
@m3city
Best we not feed the FF hater too much lines so he can fill up the comment section with walls of his gibberish.
FF was audited in Germany by cybersecurity experts the “Bundesamt für Sicherheit in der Informationstechnik, or BSI.
The BSI advises government agencies and private sector companies on what browsers are safe to use.
FF passed all their tests. The rest failed the minumum requirements.
Among the desktop web browsers that were audited were Google’s Chrome, Microsoft’s Edge, and Mozilla’s Firefox, only Firefox pass all minimum requirements for mandatory security features.
FF is the most secure browser. Many privacy tech sites recommend it as being the most private aswell.
@Anon7:
That’s inaccurate. According to the latest available comparison table (h t t p s ://w w w .bsi.bund.de/SharedDocs/Downloads/DE/BSI/Mindeststandards/Browser-Abgleich_Mindeststandard_Web-Browser_V2_1a.pdf?__blob=publicationFile&v=1) both Firefox and Chrome passed their minimum requirements.
@Shintoplasm
Latest available? Lulz
FF has a better track record.
The test where chrome and edge failed was in 2019.
So yes FF does have a better track record regarding security that was audited by german cybersecurity experts.
@Anon7
You think Firefox is safest because some bureaucracy in Germany says so, the comparison points being Chrome and old Edge? LOL.
Firefox is definitely not the most secure browser, in terms of exploit mitigations. This was never evaluated in the old comparison you mention (without giving a source as always, I just had to dig it out somewhere). Firefox is a security disaster:
https://www.whonix.org/wiki/Dev/Chromium#Firefox_and_Chromium_Security
> Many privacy tech sites recommend it as being the most private aswell.
Many “privacy tech sites” also recommend that you basically make yourself highly unique by cluelessly modifying about:config entries that alter the fingerprint. Says it all.
> You think Firefox is safest because some bureaucracy in Germany says so
bureaucracy? nice way to direct from the truth Mr fear merchant. State level IT experts know what they are talking about, you do not!
These are only some of the criteria that FF has met in the BSI Test and passed easily.
-Organization admins must be able to configure or block browsers from sending telemetry/usage data. Browsers must support a mechanism to check for harmful content/URLs.
-Must run after its initialization with minimal rights in the operating system. Must support sandboxing. All browser components must be isolated from each other and the operating system. Communication between the isolated components may only take place via defined interfaces. Direct access to resources of isolated components must not be possible.
So clearly Iron Heart and his spamming of whonix attention seekers are out of their depth when giving security advice. They are not state level IT experts.
They have not a clue what they are on about.
See here this comment from Irony Heart
> Firefox is definitely not the most secure browser, in terms of exploit mitigations. This was never evaluated in the old comparison you mention
Actually according to the BSI its security is pretty much impeccable. A range of tests were carried out regarding its security. A proven track record it has.
I told you before Iron Heart, you are full of shit. Why would anyone care what you say have to say? when they can just listen to the advice of professional state level cybersecurity experts? I told you before that whonix are a joke, not to be taken seriously. So please stop spamming madaidans FUD!
whonix would not be using FF in its tool if it was not secure. So get lost with the hypocrisy and silly theatre.
Bundesamt für Sicherheit in der Informationstechnik is the German upper-level federal agency in charge with the task of managing computer and communication security for the German government.
Its areas of expertise includes the security of computer applications, critical infrastructure protection, Internet security, cryptography, and certification of security products and the accreditation of security test laboratories.
One of the many tasks of the BSI include:
-To warn of malware or security holes in IT products and services
– Protection of federal level german governmental computer infrastructure.
They gave FF the all clear.
Irony Heart knows better than these experts apparently.
Some troll from whonix knows better than state level IT experts too apparently.
They have not a clue what they are talking about as i have said many times before when Irony Heart starts spamming FUD about the security of the VERY Secure FF.
@Anon7
I do not trust a bureaucracy over the Tor developers, the Whonix developers, or Daniel Micay, these people are DEVELOPING software which people rely on for their privacy / anonymity worldwide. The study you cite, which Chrome, the privacy disaster, also passed recently, did use dumb criteria for the most part, and in the parts where it didn’t, it didn’t look deep into the code at all. One example? Firefox has a sandbox, Chrome has a sandbox, so the bureaucracy checks the “sandbox” checkbox and is done with the comparison. That Firefox’s so called sandbox is weak ass shite with trivial escapes is not being discussed, they are done when they see that there is a sandbox at all.
Such comparisons are BULLSHIT.
calling others as mozilla marketing department person and not accepting himself as the one from brave. sigh what an irony
@someone
Except I never write such idiotic marketing posts. If I ever did, please show me.
@Iron Heart
> Except I never write such idiotic marketing posts.
Why are you so jealous of Firefox? Why the need to hang around FF articles posting walls of text if you dislike it?
Why so triggered because of the Emmet comment?
If you believe FF is so bad then why are you giving it so much of your attention and time?
You have a serious inferiority complex/overcompensation thing going around the FF browser.
It does not take a genius to see it.
Their upcoming new UI is pretty yuck, though.
Another Firefox article, another FLOC-load of huge never-ending page-encompassing Iron Heart spam and lies. Nothing much changes
@Anonymous
Care to, you know, actually refute anything I say, or do you just close your eyes when faced with the facts, hoping that it will soon be over (lol)?
Yep, change for change sake — stop hiring Micro$oft rejects