- November 2020 Security Updates release notes
- List of software updates for Microsoft products
- List of the latest Windows Updates and Services Packs
- Security Updates Guide
- Microsoft Update Catalog site
- Our in-depth Windows update guide
- How to install optional updates on Windows 10
- Windows 10 Update History
- Windows 8.1 Update History
- Windows 7 Update History
Microsoft Windows Security Updates November 2020 overview
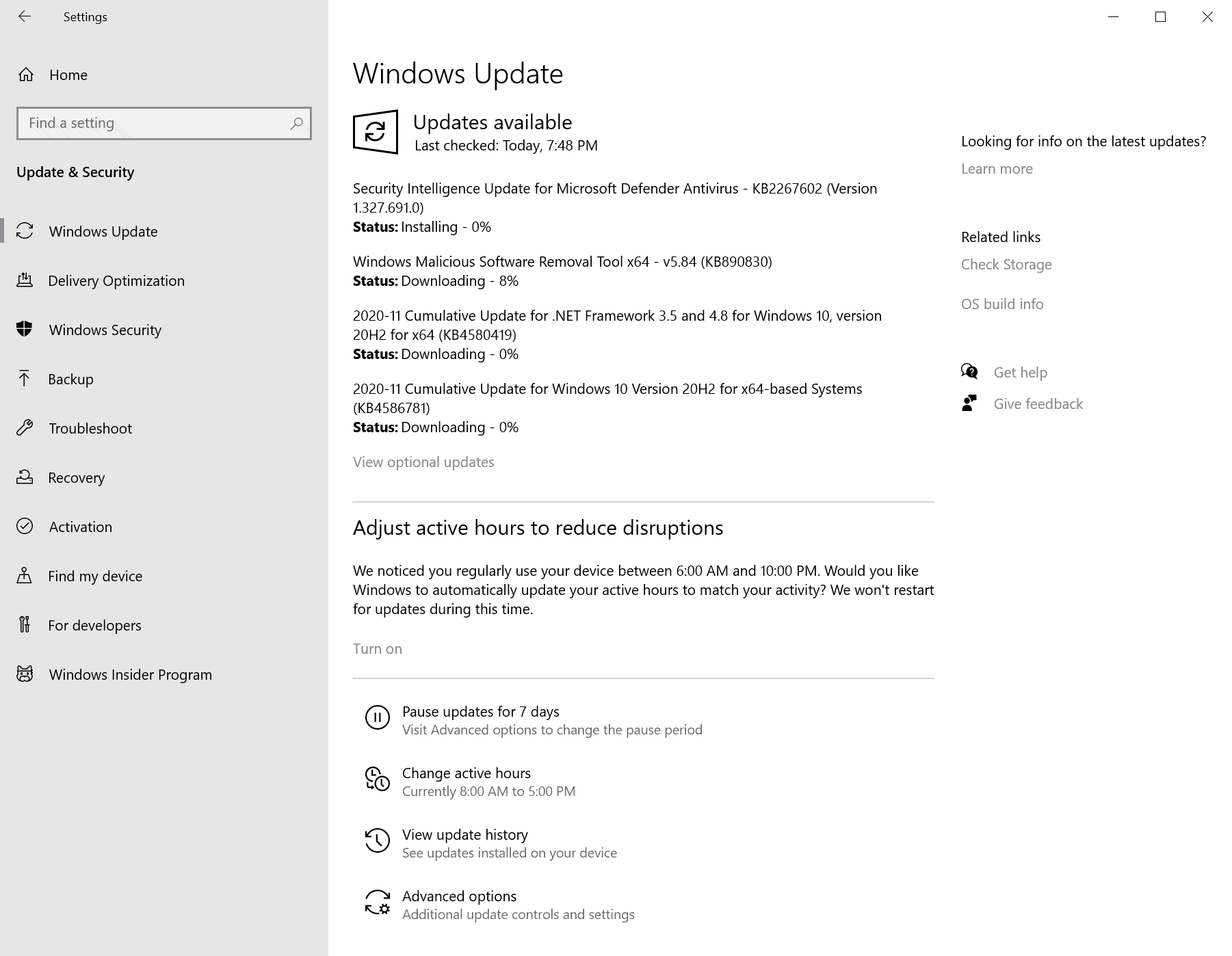
Microsoft has released security updates for all support client and server versions of Windows as well as other company products such as Microsoft Office, Microsoft Edge, and Internet Explorer.
Our November 2020 Patch Day overview provides you with details on the released patches. It begins with an executive summary listing the most important bits of information; this is followed by the operating system distribution, details about cumulative updates for Windows, other released security updates, download links, and lots of links to Microsoft support pages.
Check out the October 2020 Security Updates overview here in case you missed it.
Microsoft Windows Security Updates November 2020
You can download the following Excel spreadsheet that includes information about the released security updates in November 2020. It is provided as an archive that you need to extract on the local system. A viewer such as Microsoft Excel or LibreOffice Cacl is needed to open the spreadsheet.
Click on the following link to download the spreadsheet to your system: Security Updates 2020-11-10-070727pm
Executive Summary
- Microsoft released security updates for all supported client and server versions of Windows.
- All server and client versions of Windows are affected by the same two critical vulnerabilities.
- Security updates are also released for Microsoft Office, Internet Explorer, Microsoft Edge, Microsoft Exchange Server, Microsoft Dynamics, Microsoft Windows Codecs Library, Azure Sphere, Windows Defender, Microsoft Teams, Azure SDK, Azure DevOps and Visual Studio.
- Products with known issues: SharePoint Server 2016 and 2019, Windows 10 versions 2004, 1903, 1809, Windows 7, Windows 8.1, Windows Server products and Microsoft Exchange Server
Operating System Distribution
- Windows 7Â Â (extended support only): 20 vulnerabilities: 2 critical and 18 important
- CVE 2020 17042 -- Windows Print Spooler Remote Code Execution Vulnerability
- CVE 2020 17051 -- Windows Network File System Remote Code Execution Vulnerability
- Windows 8.1: 33 vulnerabilities: 2 rated critical and 31 rated important
- CVE 2020 17042 -- Windows Print Spooler Remote Code Execution Vulnerability
- CVE 2020 17051 -- Windows Network File System Remote Code Execution Vulnerability
- Windows 10 version 1809: 48 vulnerabilities: 2 critical and 45 important, 1 low
- CVE 2020 17042 -- Windows Print Spooler Remote Code Execution Vulnerability
- CVE 2020 17051 -- Windows Network File System Remote Code Execution Vulnerability
- Windows 10 version 1903 and 1909: 53 vulnerabilities: 2 critical and 54 important, 1 low
- CVE 2020 17042 -- Windows Print Spooler Remote Code Execution Vulnerability
- CVE 2020 17051 -- Windows Network File System Remote Code Execution Vulnerability
- Windows 10 version 2004 and 20H2: 52 vulnerabilities, 2 critical, 49 important, 1 low
- CVE 2020 17042 -- Windows Print Spooler Remote Code Execution Vulnerability
- CVE 2020 17051 -- Windows Network File System Remote Code Execution Vulnerability
Windows Server products
- Windows Server 2008 R2 (extended support only):Â 20 vulnerabilities: 2 critical and 18 important
- CVE 2020 17042 -- Windows Print Spooler Remote Code Execution Vulnerability
- CVE 2020 17051 -- Windows Network File System Remote Code Execution Vulnerability
- Windows Server 2012 R2: 34 vulnerabilities: 2 critical and 22 important.
- CVE 2020 17042 -- Windows Print Spooler Remote Code Execution Vulnerability
- CVE 2020 17051 -- Windows Network File System Remote Code Execution Vulnerability
- Windows Server 2016: 40 vulnerabilities: 2 critical and 38 important.
- CVE 2020 17042 -- Windows Print Spooler Remote Code Execution Vulnerability
- CVE 2020 17051 -- Windows Network File System Remote Code Execution Vulnerability
- Windows Server 2019: 46 vulnerabilities: 2 critical and 44 are important
- CVE 2020 17042 -- Windows Print Spooler Remote Code Execution Vulnerability
- CVE 2020 17051 -- Windows Network File System Remote Code Execution Vulnerability
Other Microsoft Products
- Internet Explorer 11: 3 vulnerabilities: 3 critical
- CVE 2020 17052 -- Scripting Engine Memory Corruption Vulnerability
- CVE 2020 17053 -- Internet Explorer Memory Corruption Vulnerability
- CVE 2020 17058 -- Microsoft Browser Memory Corruption Vulnerability
- Microsoft Edge (classic): 4 vulnerabilities: 3 critical, 1 important
- CVE 2020 17048 -- Chakra Scripting Engine Memory Corruption Vulnerability
- CVE 2020 17052 -- Scripting Engine Memory Corruption Vulnerability
- CVE 2020 17058 -- Microsoft Browser Memory Corruption Vulnerability
- Microsoft Edge (Chromium)
- see here (latest security patches from the Chromium project)
Windows Security Updates
Windows 7 SP1 and Windows Server 2008 R2
- Monthly Rollup: KB4586827
- Security-only: KB4586805Â
Updates and improvements:
- Corrects DST start date for Fiji Islands to December 20, 2020
- Security updates
Windows 8.1 and Windows Server 2012 R2
- Monthly Rollup: KB4586845Â
- Security-only: KB4586823Â
Updates and improvements:
- Corrects DST start date for Fiji Islands to December 20, 2020
- Security updates
- Administrators may enable "Save Target As" in Group Policy for Microsoft Edge IE Mode (Monthly Rollup only).
- Fixes an issue with LDAP session authentication (Monthly Rollup only).
Windows 10 version 1809
- Cumulative Update: KB4586793
Updates and improvements:
- Corrects DST start date for Fiji Islands to December 20, 2020
- Security updates
Windows 10 version 1903 and 1909
- Cumulative Update: KB4586786
Updates and improvements:
- Corrects DST start date for Fiji Islands to December 20, 2020
- Fixed an issue with the package frame launcher.
- Security updates
Windows 10 version 2004 and 20H2
- Cumulative Update: KB4586781Â
Updates and improvements:
- Corrects DST start date for Fiji Islands to December 20, 2020
- Security updates
Other security updates
KB4586768 -- 2020-11 Cumulative Security Update for Internet Explorer
KB4586807 -- 2020-11 Security Monthly Quality Rollup for Windows Server 2008
KB4586817 -- 2020-11 Security Only Quality Update for Windows Server 200
KB4586808 -- 2020-11 Security Only Quality Update for Windows Embedded 8 Standard and Windows Server 2012
KB4586834 -- 2020-11 Security Monthly Quality Rollup for Windows Embedded 8 Standard and Windows Server 2012
KB4586787 -- 2020-11 Cumulative Update for Windows 10 Version 1507
KB4586782 -- 2020-11 Cumulative Update for Windows 10 Version 1703
KB4586785 -- 2020-11 Cumulative Update for Windows 10 Version 1803
KB4586830 -- 2020-11 Cumulative Update for Windows Server 2016 and Windows 10 Version 1607
Known Issues
Windows 7 SP1 and Server 2008 R2
- Updates will uninstall if the system is not subscribed to ESU (Extended Security Updates).
- Certain rename operations may fail on Cluster Shared Volumes. Workarounds available.
Windows 8.1 and Server 2012 R2
- Certain rename operations may fail on Cluster Shared Volumes. Workarounds available.
Windows 10 version 1809
- Some Asian language packs may throw the error "0x800f0982 - PSFX_E_MATCHING_COMPONENT_NOT_FOUND". Microsoft suggest to remove the language packs and reinstall them, update Windows to the latest version, or Reset the PC.
Windows 10 version 1903, 1909, 2004, 20H2
- System and user certificates may be lost when updating from Windows 10 version 1809 or later to a newer version of Windows 10. This happens mainly when managed devices are updated using outdated bundles or media according to Microsoft. Devices that use Windows Update or Windows Update for Business are not impacted. Microsoft suggests to go back to the previous version of Windows to fix the issue.
Security advisories and updates
ADV 990001 -- Latest Servicing Stack Updates
Non-security related updates
KB4497165 -- 2020-09 Update for Windows Server, version 1909, Windows 10 Version 1909, Windows Server 2019 (1903), and Windows 10 Version 1903
KB4558130 -- 2020-09 Update for Windows Server, version 2004 and Windows 10 Version 2004
KB4580419 -- 2020-11 Cumulative Update for .NET Framework 3.5 and 4.8 for Windows Server, version 20H2, Windows 10 Version 20H2, Windows Server, version 2004, and Windows 10 Version 2004
KB4580980 -- 2020-11 Cumulative Update for .NET Framework 3.5 and 4.8 for Windows Server, version 1909, Windows 10 Version 1909, Windows Server 2019 (1903), and Windows 10 Version 1903
KB4585207 -- 2020-11 Cumulative Update for .NET Framework 4.8 for Windows Server 2016 and Windows 10 Version 1607
KB4585208 -- 2020-11 Cumulative Update for .NET Framework 4.8 for Windows 10 Version 1703
KB4585210 -- 2020-11 Cumulative Update for .NET Framework 4.8 for Windows 10 Version 1803 and Windows Server 2016
KB4586082 -- 2020-11 Cumulative Update for .NET Framework 3.5, 4.7.2 and 4.8 for Windows Server 2019 and Windows 10 Version 1809
KB4589198 -- 2020-11 Update for Windows 10 Version 1507
KB4589206 -- 2020-11 Update for Windows 10 Version 1803
KB4589208 -- 2020-11 Update for Windows Server 2019 and Windows 10 Version 1809
KB4589210 -- 2020-11 Update for Windows Server 2016 and Windows 10 Version 1607
KB4589211 -- 2020-11 Update for Windows Server, version 1909, Windows 10 Version 1909, Windows Server 2019 (1903), and Windows 10 Version 1903
KB4589212 -- 2020-11 Update for Windows Server, version 20H2, Windows 10 Version 20H2, Windows Server, version 2004, and Windows 10 Version 2004
KB890830 -- Windows Malicious Software Removal Tool
KB4585204 -- 2020-11 Security and Quality Rollup for .NET Framework 4.6 for Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, and Windows Server 2008
KB4585205 -- 2020-11 Security and Quality Rollup for .NET Framework 4.8 for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4585211 -- 2020-11 Security and Quality Rollup for .NET Framework 4.8 for Windows Embedded 8 Standard and Windows Server 2012
KB4585212 -- 2020-11 Security and Quality Rollup for .NET Framework 4.8 for Windows 8.1 and Windows Server 2012 R2
KB4585213 -- 2020-11 Security and Quality Rollup for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows Embedded 8 Standard and Windows Server 2012
KB4585214 -- 2020-11 Security and Quality Rollup for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows 8.1 and Windows Server 2012 R2
KB4586083 -- 2020-11 Security and Quality Rollup for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4586084 -- 2020-11 Security and Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows Embedded 8 Standard and Windows Server 2012
KB4586085 -- 2020-11 Security and Quality Rollup for .NET Framework 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows 8.1 and Windows Server 2012 R2
KB4586086 -- 2020-11 Security and Quality Rollup for .NET Framework 2.0, 3.0, 4.5.2, 4.6 for Windows Server 2008
Microsoft Office Updates
You find Office update information here.
How to download and install the November 2020 security updates

The November 2020 security patches are already available for all supported versions of Windows and other Microsoft products. Home users get these via Windows Updates or direct downloads, business customers and Enterprises get these via update management systems such as WSUS predominantly.
Updates are installed automatically by default on Home systems, but you can run a manual check for updates to download and install these earlier.
Note: we recommend that you create a backup of important data, better the entire system, before you install updates.
Do this to manually check for updates:
- Open the Start Menu of the Windows operating system, type Windows Update and select the result.
- Select check for updates in the application that opens. Updates may be installed automatically when they are found or offered by Windows; this depends on the operating system and version that is used, and update settings.
Direct update downloads
Below are resource pages with direct download links, if you prefer to download the updates to install them manually.
Windows 7 and Server 2008 R2
- KB4586827 -- 2020-11 Security Monthly Quality Rollup for Windows 7
- KB4586805 -- 2020-11 Security Only Quality Update for Windows 7
Windows 8.1 and Windows Server 2012 R2
- KB4586845 -- 2020-11 Security Monthly Quality Rollup for Windows 8.1
- KB4586823 -- 2020-11 Security Only Quality Update for Windows 8.1
Windows 10 (version 1809)
- KB4586793 -- 2020-11 Cumulative Update for Windows 10 Version 1809
Windows 10 (version 1903)
- KB4586786 -- 2020-11 Cumulative Update for Windows 10 Version 1903
Windows 10 (version 1909)
- KB4586786 -- 2020-11 Cumulative Update for Windows 10 Version 1909
Windows 10 (version 2004)
- KB4586781 -- 2020-11 Cumulative Update for Windows 10 Version 2004
Windows 10 (version 20H2)
- KB4586781 -- 2020-11 Cumulative Update for Windows 10 Version 20H2
Additional resources






















Anyone here find a fix to the printer spooler issue caused by the Windows 10 updates? 19041.630 build
Finally had the chance today to create a system image then install the monthly rollup (KB4586845) on my Win8.1 Pro. No issues to report, all telemetry tasks/services are still disabled and all Flash files are still gone (removed Flash last month via KB4577586).
Systemsettings.exe ctd’s… The neverboring inOS strikes again! lol
my access to a shared network printer (HP Laserjet 1010) is not working since this update
Thanks @Martin, very useful and awesome complete information as always, awesome work! :]
All is fine in LTSC land :3
We all know that you run a pirated copy of the same ol’ Windows 10 everyone else uses. Give it a rest.
Thanks again for helping me understand what I was doing before I update to the latest version for me this is Windows 10 pro version 2004, build 19041.630.
Any thoughts from you Martin (Or anybody else who maybe knows this) when the automaticly update to the 20H2 version will kick in and install, at te latest given point in time?
I’m all updated with no issues, on an old system that just keeps on going.
As for you folks having issues, perhaps you should move to Linux, Chrome, or Apple.
Otherwise you can keep coming here to complain about MS and hope for the best, as if that’s going to help. Ha.
No problem with Security Only Quality Update for Windows 8.1.
Thank you Martin.
My pc is now stuck in an install loop with KB4585786, installed it 9 times so far and then starts again. Thanks m$
10th time was the charm.. sigh of relief..
Let this be a lesson to everyone: No pc beats windows update 10 times in a row!
What’s wrong @ Microsoft? Following updates in less than a month :
KB 4586781 – KB4579311 (once for windows10 2004 and again for windows10 20H2) – KB4578968 – KB4580325..
WIth so many updates being published nobody will be updated.