Extensions are still collecting and selling your browsing data
Browser extensions may be very powerful; they may add features to web browsers, make browsing more productive, and do all sorts of things. While most browser extensions are safe to use, there have always been some that are not.
A recently published analysis on the behavior of several popular browser extensions for Google Chrome and Mozilla Firefox provides evidence that these extensions used a sophisticated browser data collecting scheme.
Dubbed DataSpii by the researcher Sam Jadali, it uncovers how eight browser extensions installed by millions of users managed to get away with the data collecting for so long and how they did it.
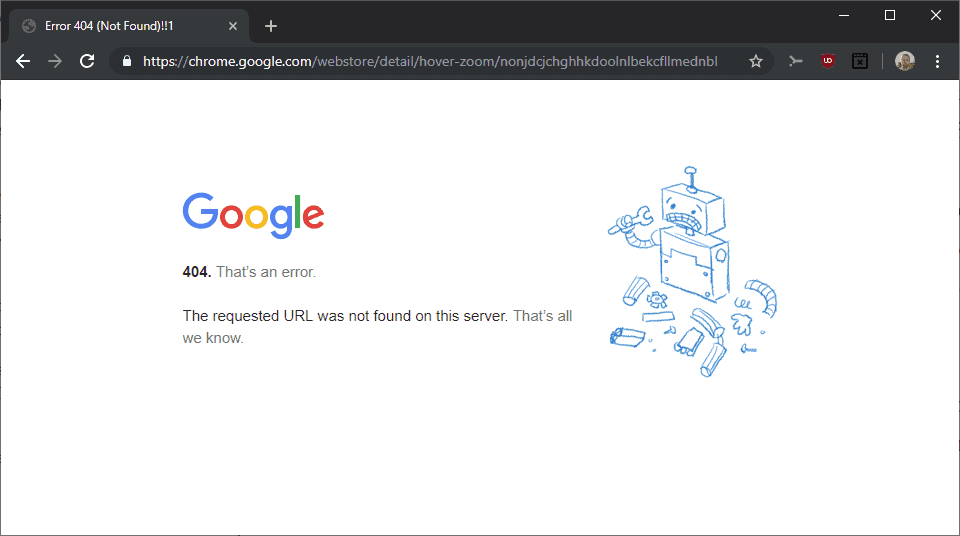
The extensions include Hover Zoom, an extension that was at the heart of a scandal in 2013 already, as well as SuperZoom, SaveFrom.net Helper, FairShare Unlock, and PanelMeasurement.
While some of the extensions started to collect data right away, others used an elaborate scheme instead. Extensions would not start to collect data right away and the researcher discovered that it took on average 24 days before the data collecting part was initialized for the first time.
The delay made detection much more complicated; users who installed the extension would not be pointed at it with a finger right away if they spotted something and researchers, including Google or Mozilla staff looking at the extensions, would not be able to find any code or traces of data collecting either after installation.
The researcher discovered that the extensions would download a JavaScript payload from Internet servers after that initial period that included the data collecting code. The developers of the extensions used various methods to obfuscate what they were doing, e.g. by using base64 encoding and data compression.
Jadali, who is the founder of the Internet hosting service Host Duplex, noticed that something was wrong when he found private forum links of clients published by analytics firm Nacho Analytics. He discovered that Nacho Analytics had information on internal link data of major corporations such as Apple, Tesla, or Symantec.
These private links should never have accessible by third-parties. After some investigation into the matter, he discovered that browser extensions were the most likely source of the leak.
Most of the extensions are available for Google Chrome only but three are also available for Firefox. The researcher found out that two of the Firefox extensions collected data only if installed from third-party sites and not Mozilla AMO.
A quick check of all eight extensions showed that they have all been removed from the Chrome Web Store; all return a 404 not found error.
You can check out Arstechnica's article on DataSpii for additional information.
Closing Words
There is not really any protection against this kind of behavior short of not installing any extensions in the web browser. Even trusted extensions may turn rogue, e.g. when they are sold to another company, a fact that is not highlighted to the user by any of the browsers.
It is still a good idea to verify Chrome extensions before you install them, it would not have helped you discover the shady nature of some of the extensions mentioned in this article as they started the data collecting weeks after installation.
Malicious extensions are discovered every now and then either by accident or by security researchers. Mozilla banned 23 snooping extensions in 2018 and a wave of malware extensions in 2019; Google removed four malicious Chrome extensions after researchers reported them to the company, and had to remove others throughout the years.
Browser makers need to implement safeguards against this behavior as it is the only way to deal with the threat once and for all. Maybe add better logging to make things like downloaded payloads easier to detect.
Now You: How many extensions have you installed? Do you trust them all?






















Imagus is a reasonable alternative to hover zoom for those that may want or need it.
Martin, when you write an article like this, I don’t always want to know the babble. Don’t always have time. I just want to see an unordered list of the extensions in question so I can quickly check if I have any of those installed.
The web is increasingly broken. All we seem to see at least weekly is *some other way* that the web is broken. Who the flip has time to think about how and why? Maybe some of us do but may of us have systems we need to adjust and protect and just want to get on with whatever tweaks we now need to make so users can try to use the web for another week without being data raped by some nefarious filthy scumbag hiding in foreign, under-regulated corner of the world where data networks reach but no lawful jurisdiction has yet taken hold.
Please reformat future articles in such a way as to draw the eye to the critical details much easier.
I minimize this problem by being selective. The only extensions I routinely install are:
* Log My Keystrokes (with account and password parsing)
* Upload My Data Files (firewall-bypass edition)
* Turn On My Webcam and Watch Me (facial-recognition edition)
* Turn On My Microphone and Listen to Me (speech-to-text edition with advanced keyword-indexing)
* Hijack my GPU and Mine Bitcoins (please, be my guest edition)
* Use Me as a Distributed Peer-to-Peer Network Node (without telling me edition)
I may be forgetting a couple… ;-)
Hover Zoom seems vaguely familiar, the others, not at all. Users install so many weird extensions, none of this is surprising.
It’s not just “weird” extentions. Like Leo write, popular extensions going rogue. Like the very popular Stylish. To add insult to injury, the removal of the extensions just gave it exposure, which lead it to be even more popular. https://www.ghacks.net/2018/07/09/stylus-sees-large-user-increase-after-stylish-removal/
And how about popular programs like CCleaner suddenly adding some crap Browser.
Installing only known extensions won’t help. Also, every extensions starts as an unknown extension. Does it mean we can never have new things?
The good guy going rogue is the worst possible scenario. My four browser extensions are security/privacy related and all of them can see some of my data. Data gathering and selling (aka sharing) private data is done by the big tech companies and users have very little control over that, so one can see why an extension developer would try to do the same. Users are like wilder beasts on the Serengeti – when they cross that river to get to the greener pastures, the crocodiles will be waiting. Every thing has a price and a cost.
Assuming this idea isn’t already ongoing elsewhere, might it be an opportunity for this blog to take a stab at creating a living article collecting a list of known-good extensions? To the extent possible, anyway, understanding that one might be removed from the article at a later date due to its changing hands or for other reasons.
I’m not suggesting a comprehensive list, which would be impossible, but one geared toward extensions which meet certain logical criteria. Perhaps being open-source, not being new, from a well-known author, and whatever else makes sense. It would probably result in just a collection of famous extensions, but it would still be useful for many.
I have 24 extensions installed on Waterfox 56.2.11 together with the Classic Addons Archive. Most of them I’ve installed after reading Martin’s reviews of them on Ghacks so I assume he vetted them first.
Do I trust them? Yes, since I haven’t seen any info on the Web which makes me think otherwise. But the Ars Tech article certainly does raise concerns and I’ll keep a close eye on things from now on.
Chrome allows for remote code execution in extension context: https://twitter.com/gorhill/status/1151979001004646400 and follow-up thread https://twitter.com/dangoodin001/status/1151999791338889216
Unfortunately addon can’t see other addon network activities. so there is no way to block those requests.
The only way is to open addon console to take a look or block hostnames.
I mostly just use dark theme and ad blocker extensions these days, maybe camelizer on chromiums. Stopped using video downloaders because they stopped working most of the time. I just paste the video url on a vidripper site if I want a podcast or whatever.
Chrome is ubber data mining platform itself. You even don’t have to install any extentions at all.
I know everyone moans about google but to me they are the least bad of a bad bunch, which includes many web sites too. At least they’re upfront about it and don’t share/sell your data to anyone who wants it, it’s for their own use. I still avoid them but there are far worse companies out there.
And they are very open about it. Unlike all these extensions. The thing is I get much more from Chrome for giving my data, these extensions offer so little to allow them to get my data.
“The researcher found out that the Firefox extensions collected data only if installed from third-party sites and not Mozilla AMO.”
That is actually very interesting. Do you have any idea why that might be, Martin? Is it because AMO still has better checks and verification routines than Chrome’s Store?
I don’t know. I guess Chrome’s market share places a role and also the way add-ons are vetted before allowed in the Store. I don’t know if there is a huge difference when it comes to that and whether Mozilla would have detected the “shadiness” of the add-ons during inspection since at least some of them did not start the nasty behavior immediately.
I think the sample size is too small to come to a conclusion. Also, I just verified again and one of the extensions was indeed on AMO but removed by Mozilla.
I’ve never heard of those extensions, and generally people who install such obscure extensions also install all sorts of crap on their computers, so really those extensions are the least of their worries.
That being said, the only time I’ve myself dealt with a rogue extension was mozilla’s own telemetry enabler extension, which was forcefully installed on every browser restart. And this is a bigger issue in my opinion as I was not aware of this malware running on my PC – it just happened that I was browsing CCleaner’s tabs and opened the browsers extensions tab, which revealed mozilla’s shady practice; on the other hand, installing these extensions requires explicit user action.
Bizarre logic; the fire still burns but not as hot.
CCleaner, when it wasn’t total malware was useful for easily disabling or removing browser extensions, there was no “event” when Mozilla decided to use telemetry, it was there for ages and reinstalled at each update, you just found out what was happening and know how to fix it, but…
Those who installed the extensions in the article are no more guilty of stupidity than someone who installs FF. The big difference is those rogue extensions laid low until forgotten, then began sending user data to a third party. Meanwhile chrome is sending everything you do, even data when the browser is closed, to google, to sell to, uh, third parties.
Mozilla gets “caught,” Google just makes up nonsense about what they do, blaming the users’ desire for a “rich experience(blech!)” At least FF users seem to be savvy enough to understand their browser and can lock it down to a high degree; chromia users can’t unless they utilize a proxy, a la Brave, a VPN or system wide tracking blocker.
Of all those companies mozilla is the only one which claims. loud and clear, with every single ocasion, that they care about user’s privacy. They themselves set this standard, which they willingly decided to not hold it anymore. You don’t get to compare yourself to Google when you make such bold claims about yourself. Google tells you upfront they will sell all your information on the very first ocasion – which is fine, you get to decide whether you want to use their products or not, way before you get to hit the install button.
Hoverzoom for example is a fairly well known one (and has been shady in the past), all because you haven’t heard of them doesn’t automatically make them obscure.
Chrome 76 will make it easier to see what extensions are up to.
https://techdows.com/2019/07/chrome-76-to-make-it-easier-to-track-extension-activities.html
Very people will understand api calls and even many of those that understand the concept won’t have a clue what to look for. What api calls do you look for if you’re trying to spot telemetry/spying?
@itsMe…
In this case, as Martin notes, it was discovered by someone (Jadali) who found his customers data for sale online. The amount and types of data being stolen and sold was staggering – everything from “usernames, passwords and GPS coordinates” to medical records and tax documents and “top -secret stuff” from corporations.
I suspect that detecting it directly could be tough. A better solution – don’t put info you want to keep private on an internet connected computer.
It’s nearly impossible to do that though unless you’re ok stopping doing online shopping, banking etc basically just read stuff.
Perhaps there needs to be a way to only let extensions access servers if you give them permission. Or better yet google and mozilla need to manually validate extensions, as mozilla always used to do. The number that that automated systems miss is becoming silly.
Can’t you just disable browser extensions when you want to do online banking etc? Or would it be necessary to fully remove the extensions?
@Alby:
I think there are ways of starting most browsers with all add-ons (including extensions) temporarily disabled just for that particular browsing session. In most Firefox-family browsers, this is called “safe mode,” and you can do it by holding down the shift key when you launch the browser, or, if it’s already running, by doing “Help > Restart in Safe Mode” in the application menu. (In Firefox-family browsers, at least, hardware acceleration is also disabled in safe mode.) I *think* that should be good enough, even for “hybrid” extensions that hand off browser input to a non-browser component. (I’m pretty sure I’ve come across a Firefox download-management extension that does this, but I don’t remember what it’s called.)
@itsMe
Martin suggested: Maybe add better logging to make things like downloaded payloads easier to detect.
Browser makers could set up browsers constantly connected to the internet and monitor for any attempts to download or upload – allowing only for upgrades. That would catch any time-delay mechanisms coded to prevent detection. It’s extra work for the browser makers but that could work.
You write…
Perhaps there needs to be a way to only let extensions access servers if you give them permission.
That might work. However, some extensions, like ad-blockers, access servers to update block lists. What crooks could hide in downloads like those might selectively turn off other protections in the browser or computer.