Verify Google Chrome extensions before you install them
Google Chrome extensions can extend the functionality of the web browser or make life easier while browsing the Web. While that is the case, they may also be abused by companies to track users across the Internet, display advertisement or download malicious code to the user system.
This article provides you with the means to verify Chrome extensions before you install them. It is important to do so before the extension gets installed in the browser as it may already be too late after installation.
While you can set up a test environment for browser extensions, for instance in a Sandbox and with a network traffic monitor like Wireshark, it may not really be something that most users feel comfortable with.
Part 0: What you should not trust
The Chrome Web Store may appear like a secure location for all your extension needs, but it is not. Google uses automated checks that scan extensions that developers upload to the store. These checks catch some but not all forms of privacy-invasive or outright-malicious functions.
Trend Micro discovered for instance malicious browser extensions in the official Web Store in 2014, and it is not the only company that did so.
A common method used by extensions to pass all security checks is to include a script that will load the malicious payload.
The extension itself does not contain it when submitted to the Chrome web store. Thus, the extension passes the check and is added to the store where all Chrome users can download it.
If you are interested in one nasty recent example, check out the malware in the browser article by Maxime Kjear.
The description is created by the developer of the extension and is therefore not to be trusted without verification.
User comments may highlight problematic extensions, but that is not always the case. Therefore, they are not to be trusted either in this regard without verification.
Last but not least, you should not trust recommendations blindly, or offers to install an extension because it is needed for something or advertised to you.
Part 1: The description
Many extensions that use analytics, click-tracking, tracking of your browsing history and other tracking forms highlight the fact in the description of the extension.
You may not see this one first glance as Google favors style over substance in the store. The description field is tiny and you often need to scroll to read it all.
Check out the popular Awesome Screenshot extension for instance. Looks legitimate right? Lots of positive reviews, more than 580,000 users.
If you take the time and scroll through the description, you will eventually stumble upon the following passage:
Usage of the Awesome Screenshot browser extension requires granting it permission to capture anonymized click stream data.
Want another example? How about Hover Zoom, an extension with more than 1.2 million users that has been criticized in the past for tracking integration? Scroll down and you find..
Hover Zoom requires that extension users grant Hover Zoom permission to collect browsing activity to be used internally and shared with third parties all for use on an anonymous and aggregated basis for research purposes
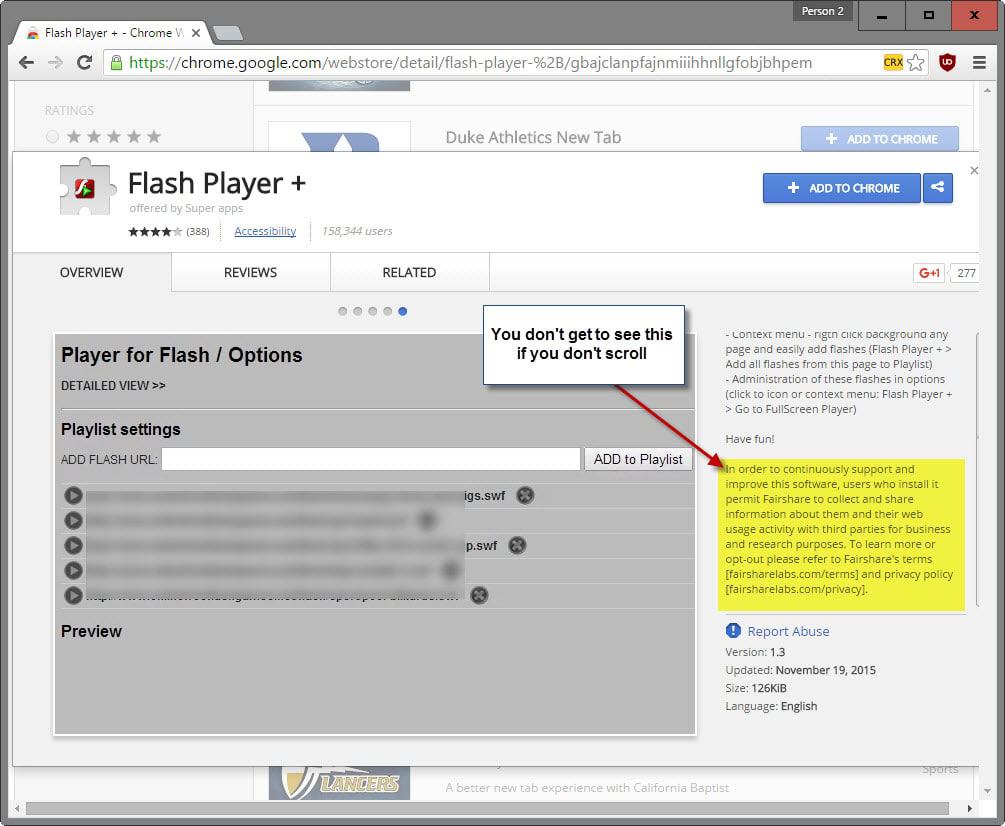
Flash Player+ is another extension that highlights in its description that it records data and shares that data with third-parties.
In order to continuously support and improve this software, users who install it permit Fairshare to collect and share information about them and their web usage activity with third parties for business and research purposes
A quick way to find these extensions is to search for phrases used in those descriptions. A search for opt-out for instance reveals many of them in the search results (next to legitimate extensions). Many use the same description which means that a search for "to collect and share information about them" will reveal extensions that use this kind of tracking for instance.
Part 2: Direct information
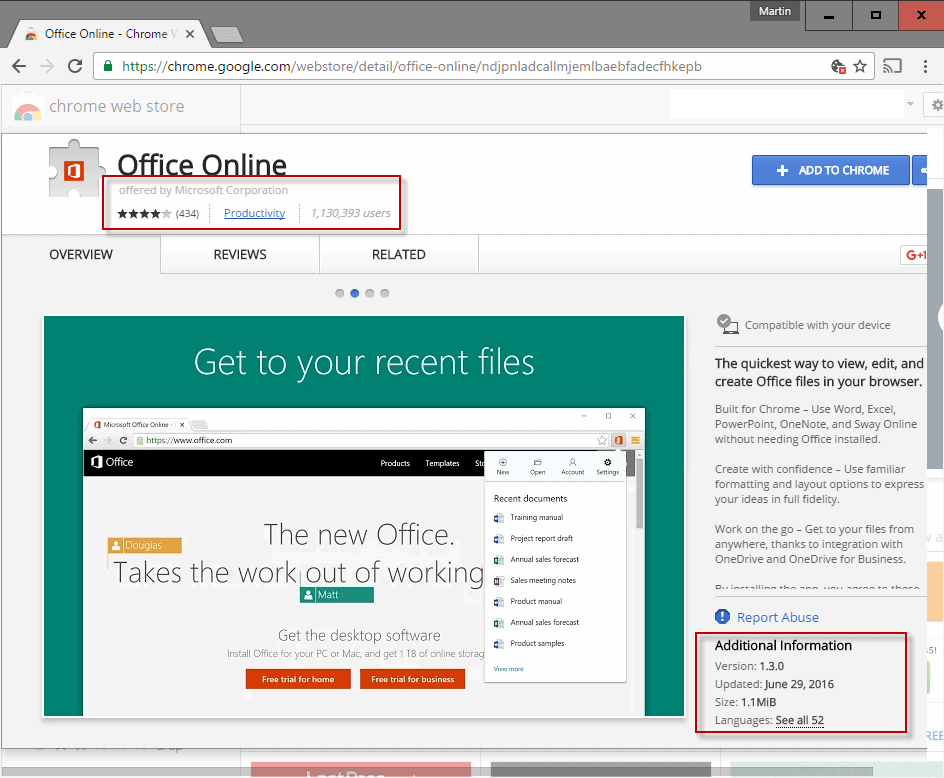
The following information are displayed on the extensions' profile page on the Chrome Web Store:
The company or individual that created it / offers it.
An aggregate rating, and the number of users who rated it.
The total number of users.
The last updated date.
The version.
The information give you clues but they are not sufficient to judge an extension. Many can be faked or inflated artificially for instance.
Google fails to provide a link to all extensions of a company or individual, and there is no option to get validation.
While you may use the search to find other extensions by a company or individual, there is no guarantee that the results list them all.
Part 3: Permissions
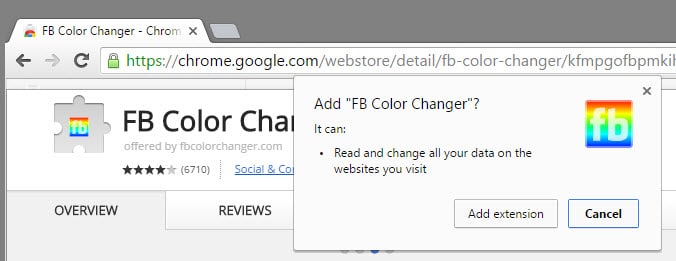
It is usually not possible to determine if an extension is legitimate, tracking you or outright malicious based on the permissions that it requests alone.
There are indicators however of that. For instance, if an extension that improves Facebook requests to "read and change all your data on the websites you visit", you may come to the conclusion that you better not install the extension based on that. Since it should only work on Facebook, there is no need to give it far-reaching permissions to see and manipulate data on all sites.
This is just an indicator however but if you use common-sense, you may be able to avoid installing problematic extensions. Usually, there is an alternative available that offers similar functionality but without the wide-reaching permission requests.
You may want to check these permissions for all installed extensions as well. Load chrome://extensions/ and click on the details link underneath each extension. This display all permission requests of that extension again as a popup in the browser.
Part 4: The Privacy Policy
Provided that the extension links to a Privacy Policy page, you may find information in it that reveal whether users are tracked by it or not. This won't work obliviously for outright malicious extensions.
For example, if you check out the Fairshare Privacy Policy linked from extensions such as Hover Zoom, you find the following passage in it:
The Company may use browser cookies, web and DOM storage data, Adobe Flash cookies, pixels, beacons, and other tracking and data collection technologies, which may include an anonymous unique identifier.
These technologies may be used to collect and store information about your use of the Services, including without limitation, web pages, features and content you have accessed, search queries you have run, referral URL information, links you have clicked on, and advertisements you have seen.
This data is used for business purposes such as providing more relevant ads and content, and market research
Part 5: The source code
Going through the source code may be the best option that you have to find out if an extension is tracking you or malicious.
This may not be as technical as it sounds and it is often possible to determine that with rudimentary HTML and JavaScript skills.
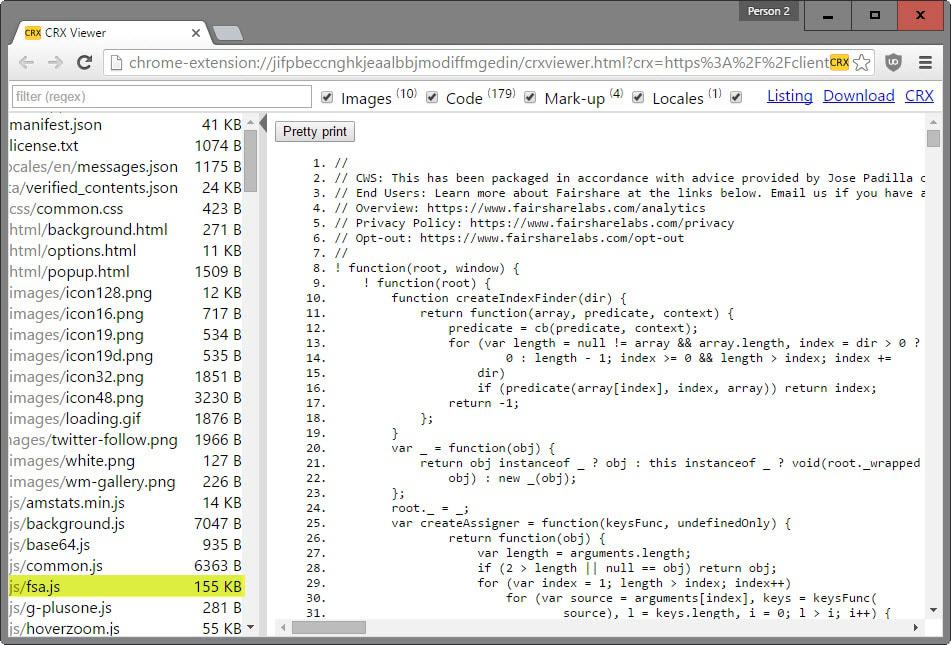
First thing you need is an extension that enables you to grab the source code of an extension without installing it. Chrome extension source viewer is an open source extension for Chrome that helps you with that.
An alternative to that is to run Chrome in a sandboxed environment, install extensions in it to gain access to their files.
If you use the extension source viewer, you may click on the crx icon in the address bar on Chrome's Web Store to download the extension as a zip file or view its source right away in the browser.
You may ignore all .css and image files right away. Files that you should take a closer look at have the .js or .json extension usually.
You may check the manifest.json file first and check the content_security_policy value to see a list of domains there but that is usually not enough.
Some extensions use obvious names for tracking files, ads for instance so that you may want to start there.
You may not be able to tell if you don't know JavaScript however if that is not the case.
Now You: Do you run Chrome extensions? Have you verified them before installation?



















>>First thing you need is an extension that enables you to grab the source code of an extension without installing it. Chrome extension source viewer is an open source extension for Chrome that helps you with that.<<
Upon trying to install said extension I see in the Permissions box said extension requires Browser History access. WHY? It as ZERO business access my history for giving source code access to webstore extensions.
Or am I wrong? Please elaborate!
“Many extensions that use analytics, click-tracking, tracking of your browsing history and other tracking forms highlight the fact in the description of the extension.”
That’s certainly nice of them.
Is there any extension to verify before/after adding an extension in Chrome?
You have no choice when using a Chromebook, but I found it strange that you have to be careful even when getting extensions even from their CHROME STORE???!!!
This following is located in part 0:
“A common method used by extensions to pass all security checks is to include a script that will load the malicious payload.
The extension itself does not contain it when submitted to the Chrome web store. Thus, the extension passes the check and is added to the store where all Chrome users can download it.”
Since I read that and figured it was a significant point, I figured others would too. I’m not associated with ghacks, the author, any internet service provider. I’m just a simple guy trying to be safe online.
I have some Chrome extensions but have verified nothing. I rarely use Chrome anyway. I generally use FF and PM.
But from this write-up, it sounds like you’d have to be crazy to use Chrome as your primary browser….
I wouldn’t say so. You don’t need to use dozens of extensions. There are many reputable ones. How many chances that uMatrix is a rogue one ? or Dark Reader ? or HTTPS Everywhere ? We know they aren’t.
If you venture into less essential territory, you might encounter trouble. But should you add hundreds of “nice to have” features, just for the heck of it ? Some restraint is in order.
what about Firefox extensions? how safe are they?
According to Detectify, not much better at all.
http://labs.detectify.com/post/133528218381/chrome-extensions-aka-total-absence-of-privacy
I find this puzzling, considering that Mozilla checks every add-on submitted to the store before it is allowed.
I’d say it is a bit better but you should verify Firefox add-ons as well.
If Google made it like setting permissions for extensions like with apps on Android Marshmallow it would be much better