Microsoft Security Updates March 2018 release overview
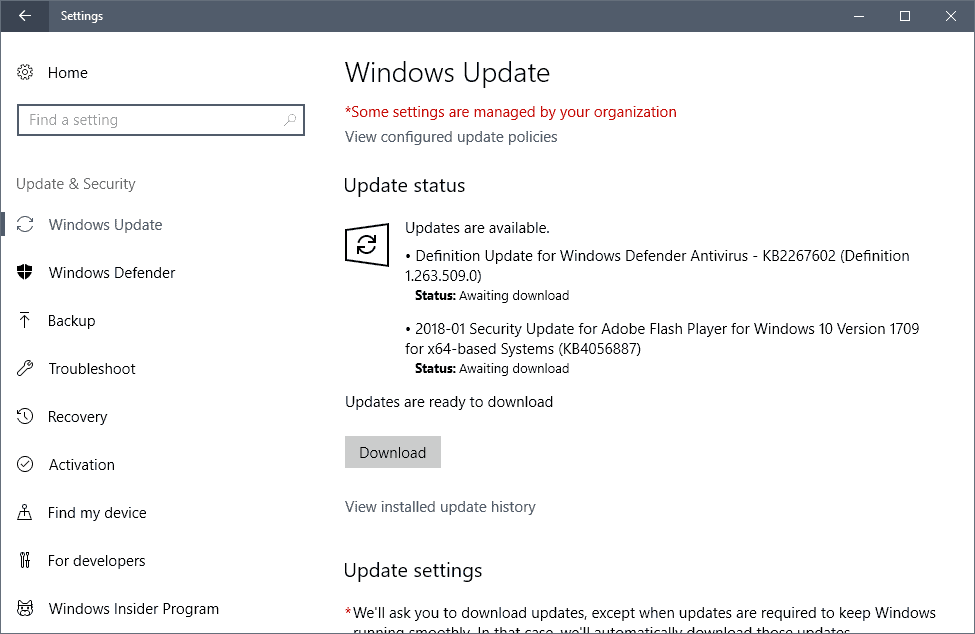
Today is Microsoft's Security Patch Day for March 2018. The company released security updates for all supported client and server versions of Windows, and other company products such as Microsoft Office, Microsoft Edge or Internet Explorer.
Our Microsoft Security Updates overview provides you with a detailed overview: it lists all released security and non-security updates, security advisories, and links to direct downloads and additional resources for research.
Note: We recommend that you back up Windows' system partition before you install any update released by Microsoft. You can use free backup tools like Veeam Endpoint Backup or Macrium Reflect for that, or one of the backup programs listed here.
Microsoft Security Updates March 2018
You may download the following Excel spreadsheet to your local system. It contains a list of all security patches for all Microsoft products released on this Patch Day. Click on the following link to download it: (Download Removed)
Executive Summary
- Security updates are available for all supported versions of Windows (client and server).
- Other Microsoft products with security updates are: Internet Explorer, Microsoft Edge, Microsoft Exchange Server, PowerShell Core, Adobe Flash, Microsoft Office
- No critical vulnerabilities for Windows versions but for Microsoft Edge and Internet Explorer.
- Microsoft lifted the antivirus compatibility check on Windows 10 version 1607, 1703 and 1709.
Operating System Distribution
- Windows 7: 21 vulnerabilities of which 21 are rated important
- Windows 8.1: 20 vulnerabilities of which 20 are rated important
- Windows 10 version 1607: 29 vulnerabilities of which 29 are rated important
- Windows 10 version 1703: 28 vulnerabilities of which 28 are rated important
- Windows 10 version 1709: 24 vulnerabilities of which 24 are rated important
Windows Server products
- Windows Server 2008: 21 vulnerabilities of which 21 are rated important
- Windows Server 2008 R2: 22 vulnerabilities of which 22 are rated important
- Windows Server 2012 and 2012 R2: 21 vulnerabilities of which 21 are rated important
- Windows Server 2016: 29 vulnerabilities of which 29 are rated important
Other Microsoft Products
- Internet Explorer 11: 7 vulnerabilities, 2 critical, 5 important
- Microsoft Edge: 16 vulnerabilities, 12 critical, 4 important
Security Updates
KB4088875 -- Windows 7 SP1 and Windows Server 2008 R2 Monthly Rollup
- Includes security updates for Internet Explorer, the Microsoft Graphics component, Windows Kernel, Windows Shell, Windows MSXML, Windows Installer, and Windows Hyper-V.
- Cumulative Spectre and Meltdown protections for 32-bit and 64-bit versions.
- Addressed Internet Explorer unresponsive issue when Browser Helper Objects are installed.
- Legacy Document Mode cell visibility update in Internet Explorer.
- Fixed Internet Explorer stopped working issue in printing scenarios.
- Fixed Internet Explorer stopped working issue when using Developer Tools.
KB4088878 -- Windows 7 SP1 and Windows Server 2008 R2 Security-Only Update
- Same security updates and cumulative Spectre and Meltdown protection updates as KB4088875.
KB4088876 -- Windows 8.1 and Windows Server 2012 R2 Monthly Rollup
- Same security updates and fixed issues as in KB4088875.
- Addressed sign-in issues to Windows 2012 R2 servers when using custom credential provider on a console or RDP.
- Fixed Internet Explorer issue that caused Outlook's web app to slow down.
KB4088879 -- Windows 8.1 and Windows Server 2012 R2 Monthly Rollup
- Same security updates as KB4088876 plus Windows 2012 R2 server issue.
KB4000825 -- Windows 10 version 1607 and Windows Server 2016
- Security updates to Internet Explorer, Microsoft Edge, Microsoft Scripting Engine, Microsoft Windows Search component, Windows Desktop Bridge, Microsoft Graphics component, Windows Kernel, Windows Shell, Windows MSXML, Windows Datacenter Networking, Windows Installer, and Windows Hyper-V.
- Addressed XML document printing issue in IE and Edge.
- Addressed stopped working issue in IE when using F12 developer tools.
- Updated legacy Document Mode cell visibility in IE.
- Addressed IE becoming unresponsive issue when installing Browser Helper Objects.
- Addressed issue that affected some antivirus software versions on which the antivirus updated the Allow Regkey.
- Addressed AD FS server issue causing WID AD FS database to become unusable after a restart.
- Fixed online video playback becoming unresponsive issue.
KB4088782 -- Windows 10 version 1703
- Same as KB4000825 for the most part plus..
- SMB shared files access issue with the error ERROR_INVALID_REPARSE_DATA resulting in errors when editing some group policies (The data present in the reparse point buffer is invalid. (Exception from HRESULT: 0x80071128)).
KB4088776 -- Windows 10 version 1709
- Same as KB4000825 for the most part plus..
- Fixed issue that prevented media and other apps from becoming unresponsive or failing during graphics drivers updates.
- Addressed "Check your account, you don't own this content" error when customers tried to play or install owned content.
- Addressed "We couldn’t download the Windows Mixed Reality Software" after installing KB4090913.
KB4089187 -- Cumulative security update for Internet Explorer: March 13, 2018
KB4088785 -- Security update for Adobe Flash Player: March 13, 2018
KB4056564 -- Windows Server 2008 and Windows XP Embedded update that fixes a CredSSP remote code execution vulnerability.
KB4073011 -- Windows Server 2008 update that fixes a Windows Hyper-V denial of service vulnerability.
KB4087398 -- Windows Server 2008 and Windows XP Embedded update that fixes a Windows Installer elevation of privilege Vulnerability.
KB4088827 -- Windows Server 2008 update that patches a Hyper-V information disclosure vulnerability.
KB4088880 -- Windows Embedded 8 Standard and Windows Server 2012 update -- security only update.
KB4089082 -- Windows XP Embedded patches Microsoft Video Control elevation of privilege vulnerability.
KB4089175 -- Windows Server 2008 and Windows XP Embedded addresses Windows shell remote code execution vulnerability.
KB4089229 -- Windows Server 2008 addresses Windows Kernel vulnerabilities.
KB4089344 -- Windows Server 2008 and Windows XP Embedded fixes elevation of privileges vulnerability in Windows Graphics Device Interface.
KB4089453 --Windows Server 2008 and Windows XP Embedded fixes Windows remote assistance information disclosure vulnerability.
KB4089694 -- Windows XP Embedded patches Windows Wireless WPA pairwise encryption key reinstallation vulnerability.
KB4090450 -- Windows Server 2008 addresses speculative execution side-channel vulnerabilities.
Known Issues
- (Windows 7) SMB Servers may leak memory after installing the update -- Fix in the works.
- (Windows 7) Stop error on machines with the Physical Address Extension (PAE) mode disabled -- Update is not delivered to 32-bit systems with PAE disabled.
- (Windows 7) Stop error on machines not support Single Instructions Multiple Data (SIMD) Extensions 2 (SSE2) -- Fix is in the works.
- (Windows 7 and 8.1) No updates for systems without compatible antivirus solution or Registry key set -- Set Registry key:
- Key: HKEY_LOCAL_MACHINE"Subkey="SOFTWARE\Microsoft\Windows\CurrentVersion\QualityCompat
- Name: cadca5fe-87d3-4b96-b7fb-a231484277cc
- Type: Dword (32-bit) Value
- Data: 0x00000000
Security advisories and updates
ADV180005 -- all Windows version -- Document signing deprecation in XPS Viewer
Non-security related updates
KB4092077 -- Windows 10 version 1703 -- Fixes UI usability issues after installing the previous update for the operating system version.
KB4090913 -- Windows 10 Version 1709 -- This update fixes the "INACCESSIBLE_BOOT_DEVICE" issue and issue with some USB devices and onboard devices that stopped working.
KB4077525 -- Windows 10 Version 1607 and Server 2016 -- Huge update that fixes a large number of issues (mostly in Windows Server 2016)
KB4089848 -- Cumulative Update for Windows Server 2016, and Windows 10 Version 1709
KB4089938 -- Dynamic Update for Windows 10 Version 1709 -- Compatibility update for upgrading to Windows 10 Version 1709
KB4090007 -- Update for Windows 10 Version 1709 -- Intel microcode updates
KB4091663 -- Update for Windows 10 Version 1703
KB4091664 -- Update for Windows 10 Version 1607
KB4091666 -- Update for Windows 10 Version 1507
KB890830 -- Windows Malicious Software Removal Tool - March 201
Microsoft Office Updates
The Office March 2018 non-security updates were released last week. See Microsoft's list that includes Office 2007, SharePoint, Project Server and SharePoint Server patches as well.
Office 2016
KB4011665 -- Access 2016 update to prevent remote code execution attacks using specially crafted Office files.
KB4011727 -- Same as KB4011665 but for Excel 2016.
KB4011730 -- Same as KB4011665 but for Word 2016.
Office 2013
KB4011234 -- Access 2013 fix described in KB4011665
KB4018291 -- Excel 2013 fix described in KB4011727
KB4011695 -- Word 2013 fix described in KB4011727
Office 2010
KB4011673 -- Fixes a remote code execution vulnerability in Office 2010.
KB3114416 -- Access 2010 fix described in KB4011665
KB4011675 -- Excel 2010 fix described in KB4011727
KB4011674 -- Word 2010 fix described in KB4011727
How to download and install the March 2018 security updates

All security updates get released as cumulative updates for all supported operating systems. The primary method of distributing new security updates is via Windows Update, the built-in updating system of Windows.
Windows systems run update checks regularly but not in real-time. Users who want to download and install the updates the moment they are released can do so by manually checking for updates.
Note that it is advised to create a system backup before the installation of updates to have a third-party option to restore the old version.
Do the following to check for updates:
- Tap on the Windows-key, type Windows Update, and select the result from the list of items returned to you by Windows Search.
- Select "check for updates" or wait until the automatic update scan completes.
- Wait until the automatic downloading and installation of updates completes, or initiate the process with a click on the download button.
Updates can also be downloaded from Microsoft's Update Catalog website, or through other means, WSUS for instance for Windows Server updates.
Direct update downloads
You can download cumulative updates and rollup patches for Windows 7, Windows 8.1 and Windows 10, and the server operating systems Windows Server 2008 R2, Windows Server 2012 R2, and Windows Server 2016 from the Microsoft Update Catalog website.
Windows 7 SP1 and Windows Server 2008 R2 SP
- KB4088875 — 2018-03 Security Monthly Quality Rollup for Windows 7
- KB4088878 — 2018-03 Security Only Quality Update for Windows 7
Windows 8.1 and Windows Server 2012 R2
- KB4088876 — 2018-03 Security Monthly Quality Rollup for Windows 8.1
- KB4088879 — 2018-03 Security Only Quality Update for Windows 8.1
Windows 10 and Windows Server 2016 (version 1607)
- KB4088787 — 2018-03 Cumulative Update for Windows 10 Version 1607 and Windows Server 2016
Windows 10 (version 1703)
- KB4088782— 2018-03 Cumulative Update for Windows 10 Version 1703
Windows 10 (version 1709)
- KB4088776 — 2018-03 Cumulative Update for Windows 10 Version 1709
Additional resources






















Thanks for this info! A quick question though…I knew there were dynamic updates, standalone updates, and cumulative updates out there, and variations for x86/x64/ARM etc. But I didn’t realize there were different cumulative updates for different classifications. For example, if I go to the Microsoft catalog and do a search for “2018-03 cumulative update for windows 10 version 1709”, I see six results. It’s the x64 ones I’m interested in of which there are two. So there are:
2018-03 Cumulative Update for Windows 10 Version 1709 for x64-based Systems (KB4090913) “Updates” classification, 688.8 MB
2018-03 Cumulative Update for Windows 10 Version 1709 for x64-based Systems (KB4088776) “Security updates” classification, 703.8 MB — which you linked to above.
To clarify, I take it both would be required here? Cumulative updates are only cumulative for their respective categories? Thanks.
Didn´t I see a list somewhere here of updates not to install
because they contained telemetrie and
other spyware? I´m on Win 7 btw.
Sorry for asking. Did the search with “NOT telemetri”. Not many
results for “telemetri” showing up. :-)
I run Windows 7, too, I install “security only” updates alone, and I always run WPD after updating to make sure unwanted telemetry and diagnostics have not been snuck in or turned back on. And if they have, I use WPD to disable them. It definitely happened to me at least once, back in August or September 2017, I think.
Just use Simplewall and enable filtering in whitelist mode so only the apps you allow can access the internet.
github.com/henrypp/simplewall
It doesn’t matter how much unwanted telemetry/spywares Microsoft adds if telemetry/spywares can’t access the internet.
Supposedly, there are reports that one of this Patch Tuesday’s quality updates and one its security-only updates, can zap static IP address settings in Windows Server 2008 and *maybe* Windows 7 as well. I and everyone I look after use DHCP so I didn’t look into it any further, but in case any of you do, here’s the article I saw:
Patch LOSE-day: Microsoft secures servers of the world. By disconnecting them • The Register
https://www.theregister.co.uk/2018/03/14/microsoft_secures_the_servers_of_the_world/
Users complain of static IP issues, world of admin pain
By Richard Speed 14 Mar 2018 at 16:30
I’m not sure why but after applying the update for Windows 7 it seemed to have cause a minor slow down when booting up and shutting down.
@Anon_Prime:
I know that for Server 2008 updates (for those applying such updates to Vista), two updates have been made ready for Spectre and Meltdown. And for Server 2012 (for updates on Windows 8) the rollup and security-only patches include similar mitigating strategies. So maybe Windows 7 was also affected.
Don’t such updates (for Spectre and Meltdown), defeat some or all of the CPU cache usage?
No one cares the “Spectre and Meltdown” patch(es) would slow down the system now?
http://news.softpedia.com/news/microsoft-confirms-meltdown-and-spectre-updates-slow-down-windows-pcs-519297.shtml
Over 75 vulnerabilities found in Windows 10.
theregister.co.uk/2018/03/13/patch_tuesday_march_2018/
How-to-Geek is reporting (via Bleeping Computer) that people who are still running Windows 7 without any antivirus installed on their system will not receive security updates, as a result of the recent mess caused by Spectr and Meltdown.
Windows will look for a specific key in the regsitry and if it does not find that key, you will receive a blocked error message from Windows Updates.
The key is generally applied by most antivirus programs – such as Windows Defender and Microsoft Security Essentials – along with a number of mainstream antivirus programs.
The article at HTG provides a workaround to manually enter the key your self in the registry if you really prefer running your Windows 7 system without any antivirus protection at all.
Read the HTG via the link below:
“Microsoft Blocks All Windows 7 Security Updates Unless You Have Antivirus”
https://discuss.howtogeek.com/t/microsoft-blocks-all-windows-7-security-updates-unless-you-have-antivirus/69605
KB2976978 for Windows 8.1 is doing the rounds again I note and appears as an “Important” update in this month’s Patch Tuesday updates so I guess Microsoft is trying a different approach by using the “Important” flag to try and persuade users to install it.
Same with KB2952664 for Windows 7. Failed installing on most of my monitored systems, because a previous “version” is already installed!
The direct links to IE patches are wrong, they point to last months updates.
Which links exactly?
I have, with these updates and with previous updates in Windows 10, had problems either loading or installing the update, even after going to the microsoft update page and downloading the update after the built in automatic updater failed (the built in ‘retry’ never helps – also Microsoft help pages almost never help with anything). Here are 2 things that worked for me on different occasions: 1) remove any non essential usb drives (keeping keyboard and touchpad plugged in), and/or 2) close all applications and then install the update. I figure there may be some other things I don’t know about to try if these don’t work, but so far these have helped me.
BTW, Microsoft is busy at every startup putting micro updates in that we have no control over (You can see them if you type ‘reliability’ after clicking ‘start’). In February they caused my boot time to increase from about 30 seconds to about 50 seconds, and killed Bluetooth functionality on both my Lenovo and Dell laptops with these micro updates. Way to go Microsoft!
Thanks a lot for the great article !
Trust Microsoft to make things as confusing as possible. The link on the ghacks site to KB4089187 takes you the Microsoft security bulletin for the March release for IE11. No problem there.
However, the link in article to the Catalog site loads the file links for the February IE11 update KB4074736. To get the KB4089187 link you have to enter that in the Search field on the same site.
Here’s the actual link to save you the trouble if you’re running Windows 8.1/Server 2012: https://www.catalog.update.microsoft.com/Search.aspx?q=kb4089187
Why make things easy when you can make them difficult eh?
Meanwhile, Tails Linux v.3.6 has been released:
https://tails.boum.org/
I really appreciate these meticulously organized and usefully documented Patch Tuesday reports, Martin. Thank you.
I run Windows 7, and just to put my mind at rest I ran HWInfo64 to make extra sure my system supports PAE and SSE2, whose absence can apparently cause problems. I’m good. I’m still going to wait a few days — for Belarc Advisor to update its database, for WSUS Offline Update to get its ducks in a row, and for problem reports to start popping up on the Web — before I actually update. I’m pretty sure I quit doing same-day updates to Windows not long after Microsoft released GWX, back in 2015. (You know what they say: “Fool me once, shame on you. Fool me twice, you don’t get fooled again.” ;-)
The data usage viewer works before rebooting, it no longer works. Some update broke it.
Martin Brinkmann, your summaries of Microsoft’s monthly patches every Patch Tuesday are simply outstanding! Your ability to make sense of and synthesize the various Microsoft security bulletins is amazing! I eagerly look forward to your summary of Microsoft’s security updates every month. Keep up the outstanding work!! No one does it as quickly or as well!
Thanks for helping me with guiding me to update main Windows 10 pro. operating system to version 16299.309.
I am (especially) also very pleased with the M.S.Excell spreadsheet this is also ferry handy.
Because i find it quite useful to have a complete overlook over the complete 1313 items holding update list because then I can search much faster for a specific o.s update.
And then with main DuckDuckgo search engine, I always search for more information if the by me needed information is not already mentioned in your like always excelent written and also ferry informative montly update articels.
Norton Setup & Installation
After visiting the http://www.norton.com/setup , still facing problem call 1888 406 4114 or chat our technical experts they will help you.Norton setup
I found after installing Patch Tuesday fixes today for Windows 10 Home, and restarting, I was at Version 1709 (Build 16299.309) as expected. However doing an immediate subsequent manual Check for Updates grabbed one more update for Defender, an unexpected surprise.
Hi, Windows server 2008 R2, 2 vulnerabilities where 22 are rated important.
should that be 2 ? or 21 like the others or indeed 22 of which 22 are important ?
It is 22, sorry for that.