Microsoft Releases Security Patches for December 2011
Yesterday's Patch Tuesday brought 13 security bulletins fixing a total of 19 different vulnerabilities affecting Microsoft products.
The majority of security patches have been released for Microsoft's Windows operating system and Microsoft Office, with a cumulative security update released for Internet Explorer as well.
The updates are already available on Windows Update and via the Microsoft Download Center for users who prefer to download them separately. A DVD Iso image has also been released with December's security updates.
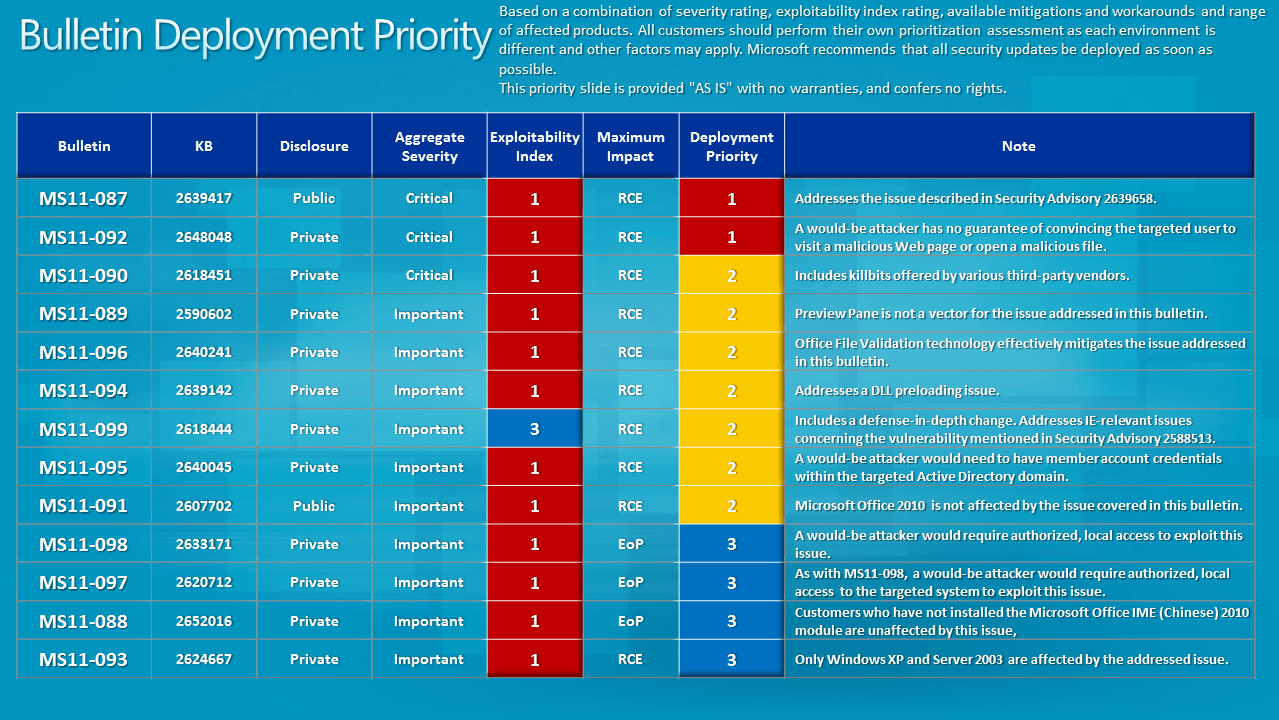
Microsoft recommends to focus the attention on the MS11-092 – Windows Media and MS11-087 – Windows critical updates before installing the remaining patches.
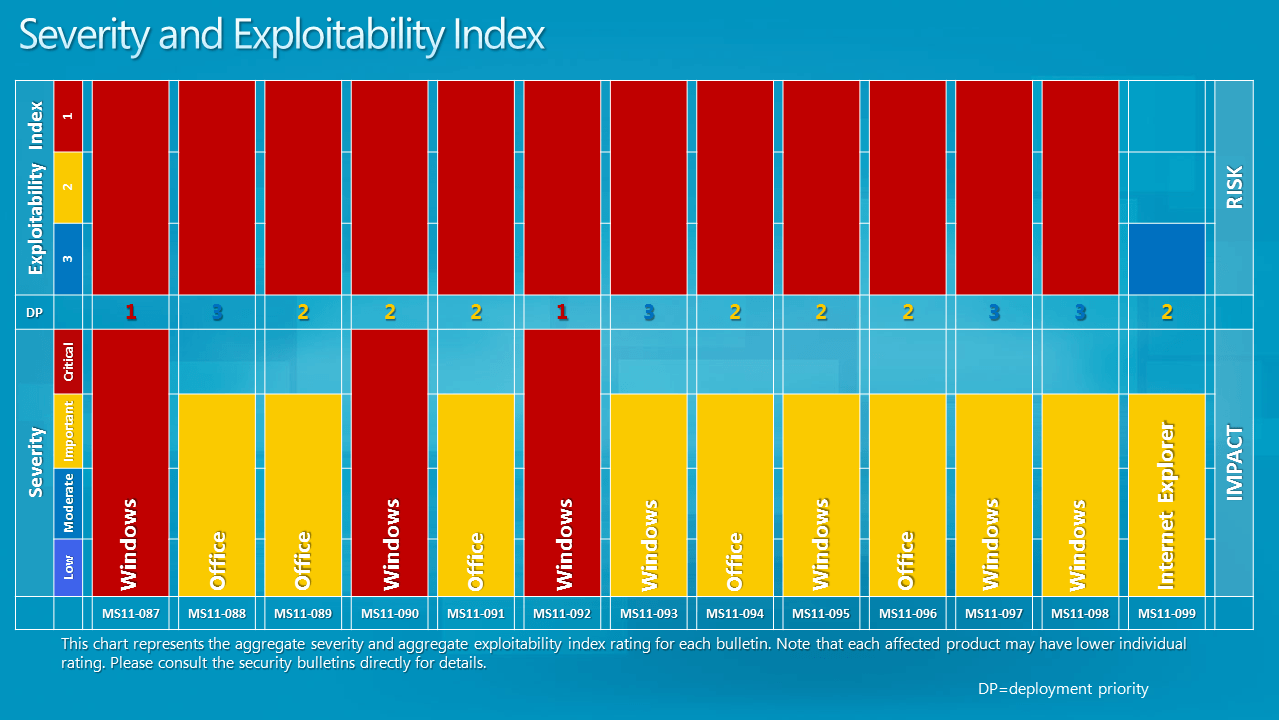
The bulletin deployment priority table, and severity and exploitability index provide further assistance.
Here is a list of all bulletins released in December 2011 by Microsoft.
- MS11-087 - Vulnerability in Windows Kernel-Mode Drivers Could Allow Remote Code Execution (2639417) - This security update resolves a publicly disclosed vulnerability in Microsoft Windows. The vulnerability could allow remote code execution if a user opens a specially crafted document or visits a malicious Web page that embeds TrueType font files.
- MS11-090 - Cumulative Security Update of ActiveX Kill Bits (2618451) - This security update resolves a privately reported vulnerability in Microsoft software. The vulnerability could allow remote code execution if a user views a specially crafted Web page that uses a specific binary behavior in Internet Explorer. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. This update also includes kill bits for four third-party ActiveX controls.
- MS11-092 - Vulnerability in Windows Media Could Allow Remote Code Execution (2648048) - This security update resolves a privately reported vulnerability in Windows Media Player and Windows Media Center. The vulnerability could allow remote code execution if a user opens a specially crafted Microsoft Digital Video Recording (.dvr-ms) file. In all cases, a user cannot be forced to open the file; for an attack to be successful, a user must be convinced to do so.
- MS11-088 - Vulnerability in Microsoft Office IME (Chinese) Could Allow Elevation of Privilege (2652016) - This security update resolves a privately reported vulnerability in Microsoft Office IME (Chinese). The vulnerability could allow elevation of privilege if a logged-on user performed specific actions on a system where an affected version of the Microsoft Pinyin (MSPY) Input Method Editor (IME) for Simplified Chinese is installed. An attacker who successfully exploited this vulnerability could run arbitrary code in kernel mode. An attacker could then install programs; view, change, or delete data; or create new accounts with full administrative rights. Only implementations of Microsoft Pinyin IME 2010 are affected by this vulnerability. Other versions of Simplified Chinese IME and other implementations of IME are not affected.
- MS11-089 - Vulnerability in Microsoft Office Could Allow Remote Code Execution (2590602) - This security update resolves a privately reported vulnerability in Microsoft Office. The vulnerability could allow remote code execution if a user opens a specially crafted Word file. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS11-091 - Vulnerabilities in Microsoft Publisher Could Allow Remote Code Execution (2607702) - This security update resolves one publicly disclosed vulnerability and three privately reported vulnerabilities in Microsoft Office. The most severe vulnerabilities could allow remote code execution if a user opens a specially crafted Publisher file. An attacker who successfully exploited any of these vulnerabilities could take complete control of an affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS11-093 - Vulnerability in OLE Could Allow Remote Code Execution (2624667) - This security update resolves a privately reported vulnerability in all supported editions of Windows XP and Windows Server 2003. This security update is rated Important for all supported editions of Windows XP and Windows Server 2003. Windows Vista, Windows Server 2008, Windows 7, and Windows Server 2008 R2 are not affected by the vulnerability.The vulnerability could allow remote code execution if a user opens a file that contains a specially crafted OLE object. An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS11-094 - Vulnerabilities in Microsoft PowerPoint Could Allow Remote Code Execution (2639142) - This security update resolves two privately reported vulnerabilities in Microsoft Office. The vulnerabilities could allow remote code execution if a user opens a specially crafted PowerPoint file. An attacker who successfully exploited either of the vulnerabilities could take complete control of an affected system. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS11-095 - Vulnerability in Active Directory Could Allow Remote Code Execution (2640045) - This security update resolves a privately reported vulnerability in Active Directory, Active Directory Application Mode (ADAM), and Active Directory Lightweight Directory Service (AD LDS). The vulnerability could allow remote code execution if an attacker logs on to an Active Directory domain and runs a specially crafted application. To exploit this vulnerability, an attacker would first need to acquire credentials to log on to an Active Directory domain.
- MS11-096 - Vulnerability in Microsoft Excel Could Allow Remote Code Execution (2640241) - This security update resolves a privately reported vulnerability in Microsoft Office. The vulnerability could allow remote code execution if a user opens a specially crafted Excel file. An attacker who successfully exploited this vulnerability could gain the same user rights as the logged-on user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. Installing and configuring Office File Validation (OFV) to prevent the opening of suspicious files blocks the attack vectors for exploiting the vulnerabilities described in CVE-2011-3403.
- MS11-097 - Vulnerability in Windows Client/Server Run-time Subsystem Could Allow Elevation of Privilege (2620712) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application designed to send a device event message to a higher-integrity process. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability.
- MS11-098 - Vulnerability in Windows Kernel Could Allow Elevation of Privilege (2633171) - This security update resolves a privately reported vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to an affected system and runs a specially crafted application designed to exploit the vulnerability. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability. The vulnerability could not be exploited remotely or by anonymous users.
- MS11-099 - Cumulative Security Update for Internet Explorer (2618444) - This security update resolves three privately reported vulnerabilities in Internet Explorer. The most severe vulnerability could allow remote code execution if a user opens a legitimate HyperText Markup Language (HTML) file that is located in the same directory as a specially crafted dynamic link library (DLL) file.
The next upcoming scheduled security update will be on the 10th of January 2012.
Advertisement

















Interesting. When browsing through Windows 7 update history ALL updates, even the critical, are marked as Important.
Originaly there were 14 update packages but no. 14 braked third party applications so it was omitted.
Patch MS11-087 is the trojan Duqu patch and it brakes creating PDF files !!!.
Oh the typos :-)
Break… of course.
Actually, I got 16 Patches at 94.4mb, which I found to be totally ridiculous!!!
Fortunately, I only installed 10 of them, which I deemed to be necessary, while the others were totally bogus!!
At the rate Microsoft is going, users will need a 1tb hard drive, just for Windows, by the time Windows 9 is released and another hard drive for the programs and apps!!
If they build their O/S right the first time and made it more secure, none, if very few of these monthly Patches would be necessary!
Thanks, Martin, for the detailed info. I had not heard before that it was recommended to apply MS11-092 and MS11-2087 before the others.
I think that I have read somewhere that this year Microsoft again had a significant raise of patches. It sure feels like it. Anyway 13 patches is a least leas than the 19 Microsoft was expecting this month. Thanks again for this mount overview.
Great, just updated!!!!