Conficker Worm Detection And Removal
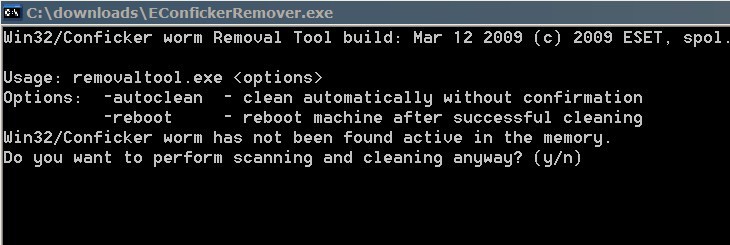
By now you might have heard about the latest worm that is plaguing Internet users world wide. It goes by the name of Conficker (or Downadup)and comes in the variants A,B and C with c being the most evolved variant. To put it simple: Conficker uses a Windows vulnerability that was discovered in September 2008 and a patch was released by Microsoft that fixed it. The first worm that used the vulnerability was discovered in November 2008.
Conficker C will initiate a number of processes on infected host systems including opening a random port which is being used in the distribution process of the worm.
The worm will then patch the security hole on the computer system that allowed it to attack the system in first place. This prevents other viruses from exploiting the vulnerability while keeping a backdoor open for newer variants of the Conficker worm.
The worm will block certain strings from being accessed on the Internet. Domain names making use of those strings cannot be accessed unless the IP is used to do so. Among the strings are domains of various security companies like microsoft, panda or symantec but also generic strings like defender, conficker or anti-. This is to prevent users from accessing websites that contain information and removal instructions to find out more about or remove the worm.
While this is surely a nuisance for the user, it does mean that the worm itself is not harming the user system in any way other than the methods described above. The real danger comes from the updating mechanism of Conficker C. The worm will try to retrieve new instructions on April 1, 2009. A very sophisticated updating mechanism has been implemented by the author. The worm will generate a list of 50K domain names and append a list of 116 top level domains to them. It will then select 500 randomly from the list and try to connect to them. If new instructions are found on one of the urls it will download them and execute them on the computer system. This process will be repeated every 24 hours.
The easiest way of detection is by accessing a site like microsoft.com or symantec.com and comparing the results with accessing the site using the IP addresses (207.46.197.32 and 206.204.52.31). While this usually gives a good indication, it is better to check the computer system with tools that have been specifically designed to detect and remove the Conficker variants.
A few tools that can be used to detect and remove Conficker variants are ESET Conficker Removal Tool, Downadup from F-Secure or KidoKiller by Kaspersky.
Excellent information about Conficker detection and removal instructions are available at Sans.org.



















I cleaned my PC with a tool from bitdefender, you can find it at bdtools.net . They have 2 versions, one for single pc and one for network admins.
Now we are ready for “April Mop” attack from Conficker.C :D
Found great removal step by step , had luck removing stuff!
http://www.livecrunch.com/2009/03/31/tips-and-tricks-how-to-remove-conficker-worm/
That’s because this one has a countdown timer, and a big “to be continued” sign on it.
I love the Panda Vaccine. It’s awesome and free (my favorite). I have it on every piece of removable storage media I own, (SD cards, External HDD, MP3players, etc) not just the USB.
I am observing a lot of people know about this worm well in advance as compared to any other threats in the past.
Thanks to the media and the hype created for this worm.
I use all this tools on a network to find and remove the Conficker.
And I Like this ESET Conficker Removal. It´s really cool.
I have just found this article .:
Containing Conficker – Tools and Infos
at .: http://iv.cs.uni-bonn.de/wg/cs/applications/containing-conficker/
And it is really useful with some tools that can help to find if a computer or even a network is infected.
I Hope it helps…
Panda USB Vaccine is also a free solution designed to protect against this threat.
http://www.pandasecurity.com/homeusers/downloads/usbvaccine/