Windows Malware Effects Remediation Tool
Successful malware attacks may make modifications to the systems, usually to decrease the chance of detection or removal of malicious processes. Even after a successful cleaning, effects of the malware attack may still limit access to certain features and tools on the operating system.

While it is often better to reinstall the operating system from scratch, or using a backup, some users prefer to remove the malware from the running system and deal with the fallout of that without doing so.
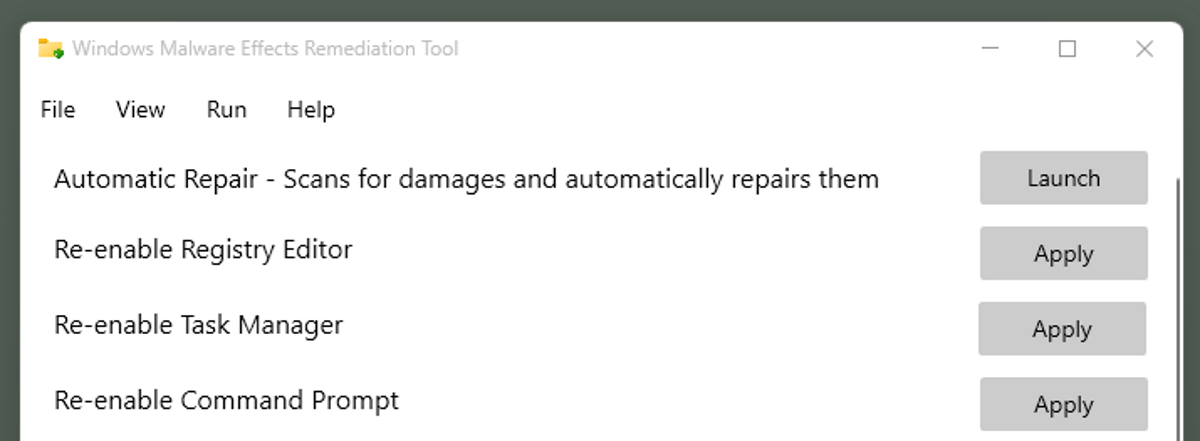
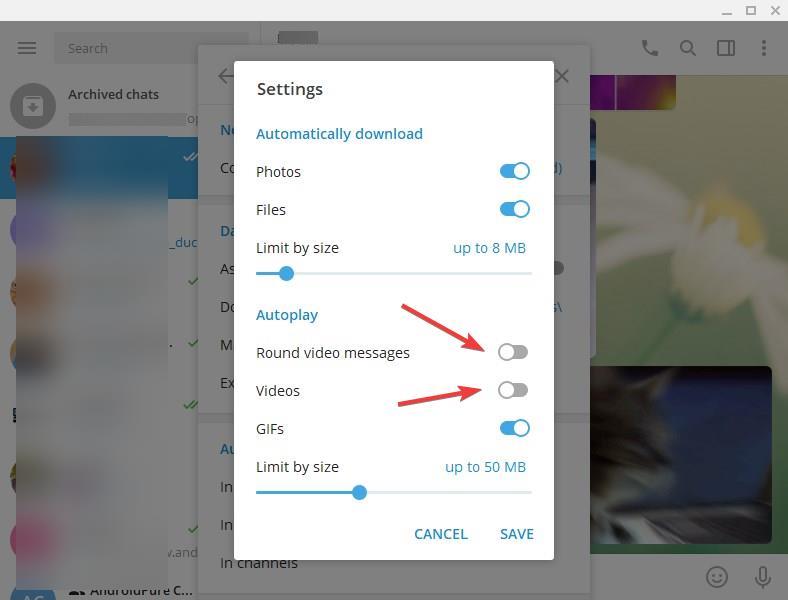
Windows Malware Effects Remediation Tool is an open source program that assists administrators in restoring functionality. It is as simple a tool as it gets: run the application, click on some buttons and you are done.
As far as system requirements are concerned. The program runs best on Windows 10 and above according to the developer, but it should also work on Windows 7, 8.0 and 8.1. The app requires the Microsoft .NET Framework 4.7.2 or later, and runs on 32-bit and 64-bit versions of Windows.
Note: Windows SmartScreen may display a warning page when you run the program. It throws these windows when new programs are launched, among other things. Five of Virustotal's antivirus engines detected a threat, but mostly lesser know engines, with the exception of Sophos.
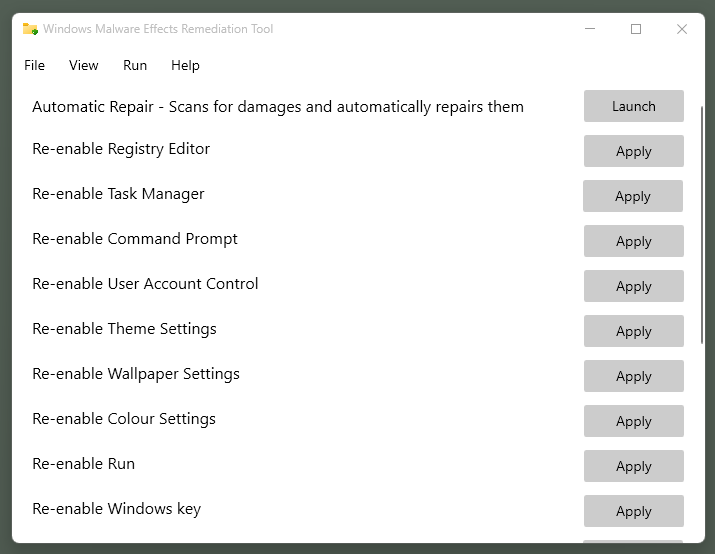
Here are the features that the tool supports:
- Enable the Registry Editor.
- Enable the Task Manager.
- Enable the Command Prompt.
- Enable User Account Control.
- Enable Theme Settings.
- Enable Wallpaper Settings.
- Enable Color Settings.
- Enable Run.
- Enable the Windows-key.
- Strip "critical process" property from applicaton.
- Reset .exe and .txt icons.
- Reset Shell key.
- Reset Userinit key.
- Remove keyboard restrictions
- Toggle primary mouse button.
Each reset option is available individually in the program interface.
Windows Malware Effects Remediation Tool supports an automatic repair feature that checks for any of the issues to reset them automatically.
The menus at the top list several additional options. You find options to launch the Registry Editor, the Task Manager, or an elevated command prompt under File, and options to run the program with elevated or system rights under Run.
Closing Words
Windows Malware Effects Remediation Tool is a useful open source tool for Windows. While its main purpose is the remediation of malware effects on Windows devices, it may come in handy for other use cases to restore functionality.
Now You: install system from scratch or remove malware from the running system, how would you handle this?
























Clean installing windows 10 from a usb to SSD takes mere minutes these days. It’s all the tweaking after that that takes the rest of the day.
Tools like the one above tend to set windows back to it’s original state as well.
If one can’t find a tool designed to remove the specific malware that got them, which is often available, I’d reccomend a wipe and reinstall after confirming the absence of root kits since any decent malware will drop a load in the backups too.
I’ve only been hit by a virus once, back in the day when I thought I didn’t need A/V. Remember the chernobyl virus?
It got both me and my room mate at the time. Even back then I had nothing but the OS on C: and I didn’t lose any data. My room mate however had a single drive system and had lost the system disk that came with it. We had to go buy a new windows OS disk to fix that one.
The saddest part was that a new unopened McAfee box was sitting on the floor next to the desk, we just hadn’t installed it yet.
Ask yourself, do you want the easiest fix or the best fix?
I have never had a malware infection before I believe because of using layered security measures (an ounce of prevention…). But if I ever did, I would not trust the system even after using a tool like this. Instead I would take 10 minutes to wipe the hard drive and restore the system from the latest Macrium image that I know is clean.
I’ve never installed the OS from scratch.
I’d first try a repair tool (I had at one time the ‘HitmanPro’ application which I no longer use).
Never encountered a malware issue, once only a real, true, authentic system failure (BSOD and Win7’s repair tools unsuccessful) : AOMEI Backupper restored successfully the system disk.
My greatest fear : a malware infecting the BIOS …
Never suffered the effects of malware on my PC since the 80s but always take precautions. The main precaution is all data is stored on cloud (but I also use offline disks). If malware strikes and when Windows goes awry, I’d be more inclined to do a complete reset.
:)
Usually I’d try the tool before reinstalling from scratch until later to potentially save inconvenient downtime.
It seems a powerful tool indeed. Thanks! :]