- January 2021 Security Updates release notes
- List of software updates for Microsoft products
- List of the latest Windows Updates and Services Packs
- Security Updates Guide
- Microsoft Update Catalog site
- Our in-depth Windows update guide
- How to install optional updates on Windows 10
- Windows 10 Update History
- Windows 8.1 Update History
- Windows 7 Update History
Microsoft Windows Security Updates January 2021 overview
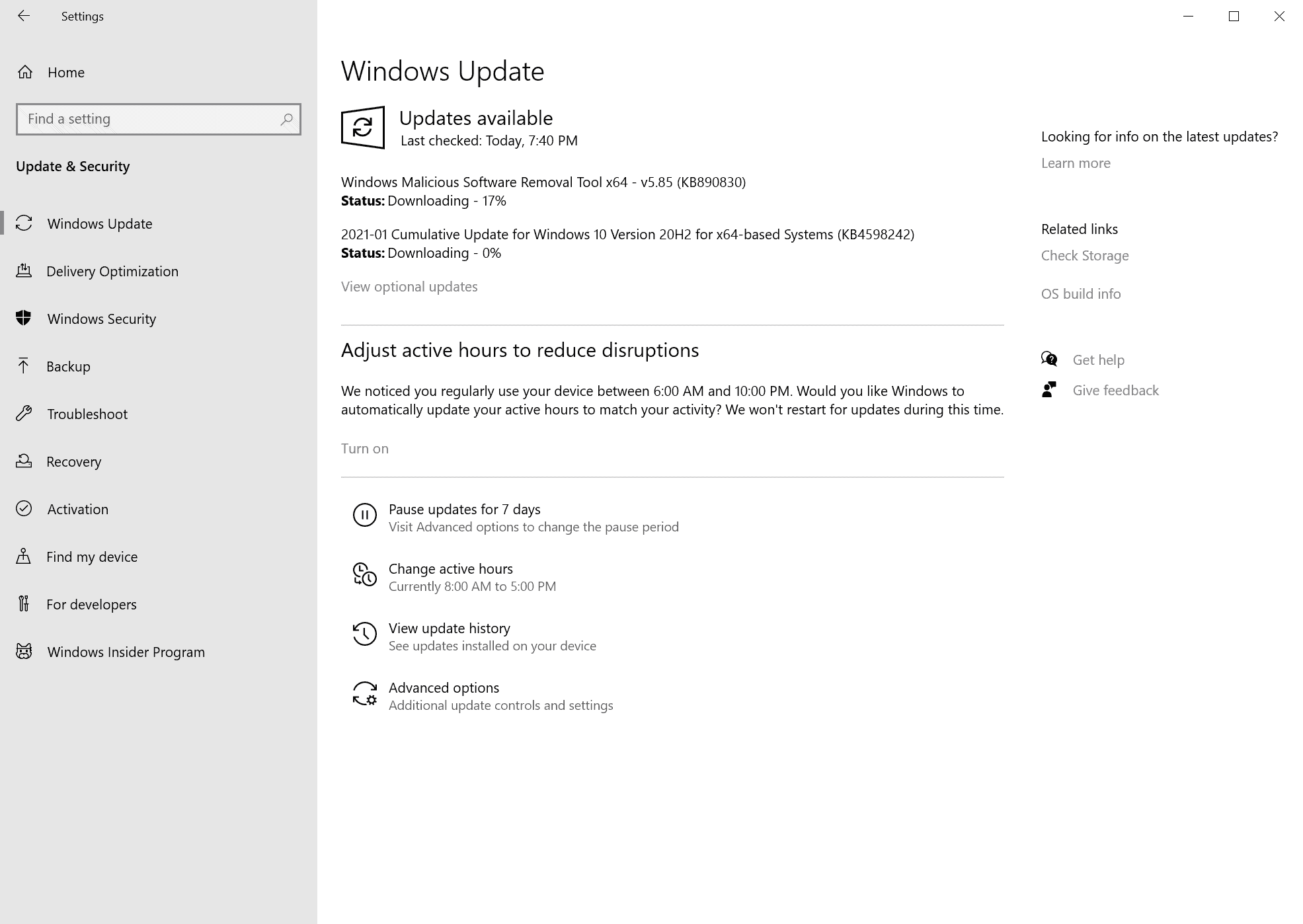
Today is the first patch day of the year 2021. Microsoft released security updates and non-security updates for the company's Windows operating system and other company products such as Microsoft Office.
In this guide, you will get a full overview of everything that is important in regards to the released updates. We provide you with an executive summary, links to support pages, download links, the list of known issues, the vulnerability distribution of each operating system version that is supported, and more.
Check out the December 2020 Patch overview in case you missed it.
Microsoft Windows Security Updates January 2021
You can download the following Excel spreadsheet to your system; it contains a list of released security updates for Microsoft's Windows platform. Click on the following link to download it to your system: Security Updates 2021-01-12-083940pm
Executive Summary
- Microsoft released security updates for all supported client and server Windows products.
- No critically rated vulnerabilities for client and server versions of Windows.
- Security updates are also available for Microsoft Office, Microsoft Edge, Azure, Visual Studio, Windows Codecs Library, SQL Server, Microsoft Malware Protection Engine, .NET Core, .NET Repository, and ASP .NET
Operating System Distribution
- Windows 7Â Â (extended support only): 5 vulnerabilities: 0 critical and 5 important
- Windows 8.1: 7 vulnerabilities: 0 rated critical and 7 rated important
- Windows 10 version 1809: 13 vulnerabilities: 0 critical and 13 important
- Windows 10 version 1903 and 1909: 13 vulnerabilities: 0 critical and 13 important
- Windows 10 version 2004 and 20H2: 13 vulnerabilities, 0 critical, 13 important
Windows Server products
- Windows Server 2008 R2 (extended support only):5 vulnerabilities: 0 critical and 5 important
- Windows Server 2012 R2: 8 vulnerabilities: 0 critical and 8 important.
- Windows Server 2016: 8 vulnerabilities: 0 critical and 8 important.
- Windows Server 2019: 8 vulnerabilities: 0 critical and 8 important.
Other Microsoft Products
- Internet Explorer 11: nothing listed
- Microsoft Edge (classic): 1 vulnerabilities: 1 critical
- CVE-2021-1705 --Â Microsoft Edge (HTML-based) Memory Corruption Vulnerability
- Microsoft Edge (Chromium)
- see here (latest security patches from the Chromium project)
Windows Security Updates
Windows 7 SP1 and Windows Server 2008 R2
- Monthly Rollup: KB4598279Â
- Security-only:Â KB4598289Â
Updates and improvements:
- Fixes a security bypass in Printer Remote Procedure Call. See Managing deployment of Printer RPC binding changes for CVE-2021-1678 for additional information. (monthly-rollup only)
- Fixes a security vulnerability issue in HTTPS-based intranet servers. HTTPS-based intranet servers cannot use a user proxy to detect updates by default after installing the update. The behavior needs to be configured if desired. See "Scan changes and certificates add security for Windows devices using WSUS for updates" for details. (monthly-rollup only)
- Security updates.
Windows 8.1 and Windows Server 2012 R2
- Monthly Rollup: KB4598285Â
- Security-only: KB4598275Â
Updates and improvements:
- Fixes a security bypass in Printer Remote Procedure Call. See Managing deployment of Printer RPC binding changes for CVE-2021-1678 for additional information. (monthly-rollup only)
- Fixes a security vulnerability issue in HTTPS-based intranet servers. HTTPS-based intranet servers cannot use a user proxy to detect updates by default after installing the update. The behavior needs to be configured if desired. See "Scan changes and certificates add security for Windows devices using WSUS for updates" for details. (monthly-rollup only)
- Security updates.
Windows 10 version 1809
- Support Page: KB4598230
Updates and improvements:
- Same security bypass and security vulnerability issue fix as in Windows 8.1 and Windows Server 2012 R2
- Fixed an issue that could send print jobs to the wrong print queue.
- Fixed an issue with chkdsk /f potentially damaging the file system.
- Security updates.
Windows 10 version 1903 and 1909
- Support Page: KB4598229Â
Updates and improvements:
- Same security bypass and security vulnerability issue fix as in Windows 8.1 and Windows Server 2012 R2
- Fixed an issue with chkdsk /f potentially damaging the file system.
- Security updates.
Windows 10 version 2004 and 20H2
- Support Page: KB4598242Â
Updates and improvements:
- Same security bypass and security vulnerability issue fix as in Windows 8.1 and Windows Server 2012 R2
- Security updates.
Other security updates
Client
KB4598231 -- 2021-01 Cumulative Update for Windows 10 Version 1507
KB4598243 -- 2021-01 Cumulative Update for Windows Server 2016 and Windows 10 Version 1607
KB4599208 -- 2021-01 Cumulative Update for Windows 10 Version 1703
KB4598245 -- 2021-01 Cumulative Update for Windows 10 Version 1803
Server
KB4598287 -- 2021-01 Security Only Quality Update for Windows Server 2008
KB4598288 -- 2021-01 Security Monthly Quality Rollup for Windows Server 2008
KB4598297 -- 2021-01 Security Only Quality Update for Windows Embedded 8 Standard and Windows Server 2012
Known Issues
Windows 7 SP1 and Windows Server 2008 R2
- Certain operations such as rename may fail on Cluster Shared Volumes. A long standing issue. Microsoft suggests to run operations from a process with elevated privileges, or from a node that does not have CSV ownership.
- Updates may fail if the system does not support ESU.
Windows 8.1 and Server 2012 R2
- Certain operations such as rename may fail on Cluster Shared Volumes. A long standing issue. Microsoft suggests to run operations from a process with elevated privileges, or from a node that does not have CSV ownership.
Windows 10 version 1809
- Long-standing issue with Asian language packs and the error "0x800f0982 - PSFX_E_MATCHING_COMPONENT_NOT_FOUND". Microsoft suggests to remove and reinstall the language packs and install the latest updates. If that does not help, a restore is Microsoft's second suggestion.
Windows 10 version 1903 and 1909
- System and certificates may be lost when updating from Windows 10 version 1809 or later to a newer version of Windows 10. Microsoft suggests to go back to the previous version of Windows if the issue is experienced already.
Windows 10 version 2004 and 20H2
- System and certificates may be lost when updating from Windows 10 version 1809 or later to a newer version of Windows 10. Microsoft suggests to go back to the previous version of Windows if the issue is experienced already.
- Using the Microsoft Japanese Input Method Editor may result in the wrong Furigana character being returned.
Security advisories and updates
ADV 990001Â -- Latest Servicing Stack Updates
Non-security related updates
KB4586875 -- 2021-01 Cumulative Update for .NET Framework 3.5 and 4.7.2 for Windows Server 2019 and Windows 10 Version 1809
KB4586876 -- 2021-01 Cumulative Update for .NET Framework 3.5 and 4.8 for Windows Server, version 20H2, Windows 10 Version 20H2, Windows Server, version 2004, and Windows 10 Version 2004
KB4586877 -- 2021-01 Cumulative Update for .NET Framework 3.5 and 4.8 for Windows Server 2019 and Windows 10 Version 1809
KB4586878 -- 2021-01 Cumulative Update for .NET Framework 3.5 and 4.8 for Windows Server, version 1909 and Windows 10 Version 1909
KB4597247 -- 2021-01 Cumulative Update for .NET Framework 4.8 for Windows Server 2016 and Windows 10 Version 1607
KB4597249 -- 2021-01 Cumulative Update for .NET Framework 4.8 for Windows 10 Version 1803 and Windows Server 2016
KB4598499 -- 2021-01 Cumulative Update for .NET Framework 3.5 and 4.7.2 for Windows Server 2019 and Windows 10 Version 1809
KB890830 -- Windows Malicious Software Removal Tool
KB4597238 -- 2021-01 Security and Quality Rollup for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows 8.1 and Windows Server 2012 R2
KB4597239 -- 2021-01 Security and Quality Rollup for .NET Framework 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows Embedded Standard 7, Windows 7, Windows Server 2008 R2, and Windows Server 2008
KB4597252 -- 2021-01 Security and Quality Rollup for .NET Framework 4.8 for Windows Embedded 8 Standard and Windows Server 2012
KB4597253 -- 2021-01 Security and Quality Rollup for .NET Framework 4.8 for Windows 8.1 and Windows Server 2012 R2
KB4597254 -- 2021-01 Security and Quality Rollup for .NET Framework 4.8 for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4598500 -- 2021-01 Security and Quality Rollup for .NET Framework 3.5.1, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4598501 -- 2021-01 Security and Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows Embedded 8 Standard and Windows Server 2012
KB4598502 -- 2021-01 Security and Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2, 4.8 for Windows 8.1 and Windows Server 2012 R2
KB4598503 -- 2021-01 Security and Quality Rollup for .NET Framework 2.0, 3.0, 4.5.2, 4.6 for Windows Server 2008
Microsoft Office Updates
You find Office update information here.
How to download and install the January 2021 security updates

Client versions of Windows will download and install security updates automatically by default. Systems may be configured otherwise, and administrators may run manual checks for updates to download the updates. The updates are provided via update management services such as WSUS as well.
Note: we recommend that systems are backed up before any update is installed on them. Windows does come with restore functionality, but it is not 100% reliable at times and it is better to have a safeguard in place in case something goes wrong during the updating.
To run a manual update check, do the following:
- Select Start, type Windows Update and load the Windows Update item that is displayed.
- Select check for updates to run a manual check for updates.
Direct update downloads
Below are resource pages with direct download links, if you prefer to download the updates to install them manually.
Windows 7 and Server 2008 R2
- KB4598279 -- 2021-01 Security Monthly Quality Rollup for Windows 7
- KB4598289 -- 2021-01 Security Only Quality Update for Windows 7
Windows 8.1 and Windows Server 2012 R2
- KB4598285Â -- 2021-01 Security Monthly Quality Rollup for Windows 8.1
- KB4598275Â -- 2021-01 Security Only Quality Update for Windows 8.1
Windows 10 (version 1809)
- KB4598230Â -- 2021-01 Cumulative Update for Windows 10 Version 1809
Windows 10 (version 1903)
- KB4598229Â -- 2021-01 Cumulative Update for Windows 10 Version 1903
Windows 10 (version 1909)
- KB4598229Â -- 2021-01 Cumulative Update for Windows 10 Version 1909
Windows 10 (version 2004)
- KB4598242 -- 2021-01 Cumulative Update for Windows 10 Version 2004
Windows 10 (version 20H2)
- KB4598242 -- 2021-01 Cumulative Update for Windows 10 Version 20H2
Additional resources






















I ran into more hitches than usual (on Windows 10 1909) this Patch Tuesday, but they were in connection with Belarc Advisor and WSUS Offline Update, *not* with the Windows updates per se. Plus, the hitch I ran into with WSUS Offline Update [WOU] was *my fault*, as I had initially forgotten to re-enable Windows Update in Sordum’s Windows Update Blocker before running WOU’s installation stage. I’m still waiting to hear back from Belarc on the problem with Belarc Advisor (false positive on 1903 end of life, no listing of missing 1909 security updates).
As for the updates themselves, once I’d re-enabled Windows Update, it was a first manual run of the WOU installer followed by a first manual reboot, followed by a second manual run of the WOU installer followed by a second manual reboot, followed by three *automatic* reboots — which had me getting a *little* worried about a never-ending loop until I saw that the third reboot mentioned only *two* installation stages instead of the previous *three* — followed by everything working just fine. Since I don’t run Windows Update natively, I won’t be able to double-check whether I have a clean bill of health security-wise until I get that Belarc Advisor problem fixed, but WOU’s installation log suggests I should be good.
UPDATE: Belarc looked into my problem and fixed it with a new definitions update. Two thumbs up for responsiveness.
hello guys, did anyone have any problems with the RDP service stop working on windows server 2016 and 2019? I also didn’t find the kb4535680 article.
Someone win 7 user had unexpectedly reboots or bsod after install kb4598289 or kb4598279?
Yes we have faced this error
Why can’t I custom resize my windows anymore after the update instead of having to have this bar down the middle and no ability to adjust the height of each window individually? If I can, how do I do so? I do not like this at all.
Settings > System > Multitasking
https://i.imgur.com/lMok0xm.png
KB4598229 update is for 1909 only, Martin.
it’s not applicable to 1903 since that version went EOL in Dec 2020
Hi Martin,
I think you omitted a security update namely KB4535680. I can’t find it the article anyway. Here’s the catalog link to it: https://www.catalog.update.microsoft.com/Search.aspx?q=KB4535680
It appears to be related to secure boot DBX according to sites around the Web.
Odd though that in Windows Update it’s only 90k whereas on the catalog site it’s 251k.
They only send you delta changes you need for your system via WU, taking into consideration all previous updates. Probably superseeds something from the past. On catalog they have all delta changes since the first public stable release of any given build.
Thanks Yuliya.
By the way, I was looking at W10 LTSB since you often recommend it on here. But from what I’ve read so far it can only be obtained by private individuals for a $7 monthly fee which is a bit steep for my liking.
Otherwise it’s only possible to download it for an evaluation period of 90 days after which you get bombarded with nag screens with the system shutting down every hour apparently.
Has that been your experience too?
data configuration for my Android device has been shaky but I presume it’s probably cause of inconsistent loading usage, I hereby request for an automatic internet web programming set up with every necessary downloads incured
Respectfully Martin,
I think you have to either change the title which reads: “Non-security related updates” or create a second category for a few .NET Framework updates since kb4578953 which is a download incorporated into kb4598502 does address a security vulnerability in NET Framework 3.5 for Windows 8.1 for example. https://support.microsoft.com/en-us/help/4578953/kb4578953
I almost skipped it, but decided to read the relevant KB document since the word “Security” is included in the download title.
Thanks anyway for taking the trouble to list them all.
I’m using Microsoft’s own classification of updates; it is without doubt problematic for a number of reasons. The “monthly-rollup” updates for Windows 7 and 8.1 include two security fixes as well that are not listed in the security-only updates. Quite confusing.
We have a case open with MS about .Net updates that are cataloged as “Updates” but include security updates inside. They keep saying that when new security updates are first released they are in “Security Updates” but when a security update is not new they are included in the rollups labeled “Updates”.
We use ADRs for each OS that include all “Security Updates” for each OS each month and all applicable (not expired) updates remain in the SUG each month, we just remove expired and add new updates from Patch Tuesday. But we still end up with systems that are missing updates as shown by our Security Scanning Tools. So we end up periodically having to manually import an “Update” into our WSUS catalog and then manually downloading and deploying to fix Security Vulnerabilities in the .Net Framework.
I think the folks at MS are as confused as we are and the product teams are not playing nice with the folks that keep our updates flowing right. It is a sad state of affairs that having ADRs downloading and deploying all “Security Updates” each month still leaves MS Servers with security vulnerabilities we can only detect with 3rd party products and manually address to patch.
Updated LTSC. All went well :)
hi,
There is no critical patch on windows 10 1809 ?
Already fixed/rolled out to 2004 automatically and 20H2 so nothing left to fix there. Didn’t realize it was still a lingering issue with older builds though or maybe they are just covering their bases?
i thought the chkdsk thing affects 20h2. is that not fixed, not an issue, or a totally different chkdsk issue that got fixed in the older win10?
Curious about this too. I thought I was relatively ok sticking with 1909.