KpRm is a post-disinfection program that can find and delete malware removal tools and their remnant files
Manually deleting file and folder leftover by an uninstallation, is quite the chore. I have used various uninstaller tools in the past to clean the remnants to keep systems clean and tidy.

You probably already know about my stance on registry and system cleaning tools.
We're not going over the same topic now. Rather, we will be looking at a new open source program called KpRm, which can detect and remove a ton of malware tools. This can be helpful after you have disinfected malware from a system. The name of the program probably stands for Kernel-Panic removal (tool?), because Kernel-Panic are the developers of the program. The application does not detect or delete real-time antivirus programs, it only removes the standalone malware removal tools that are listed on its official page.
Note: I used a Windows 10 VM for testing KpRm for 2 reasons. One, because you need to disable your antivirus when using the program, otherwise it could potentially cause issues and I wasn't comfortable with this on my main OS. Two, it's never a good idea to test security related programs on your primary computer.
Let's dive in to KpRm. I decided to use the program to remove AdwCleaner, Autoruns, and Emsisoft Emergency Kit, all of which I have used in the past on systems. All of these are portable applications.
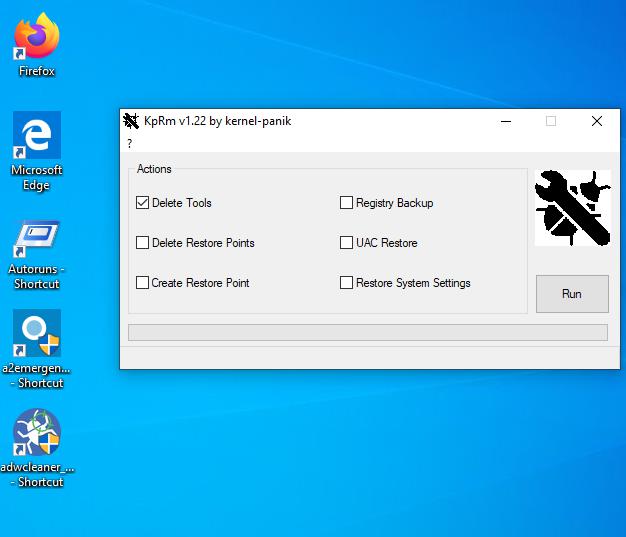
KpRm has a simple interface. The main window has a few options that you can select, the primary of which is "Delete Tools"; select it and hit the run button. The program will begin scanning for the malware removal tools on your computer, and delete them. Once the process is completed, KpRm opens the report file that it saves to document the process. This is a text document that contains the log of what actions were taken by the program including the names and folders of the malware tools that were detected and deleted.
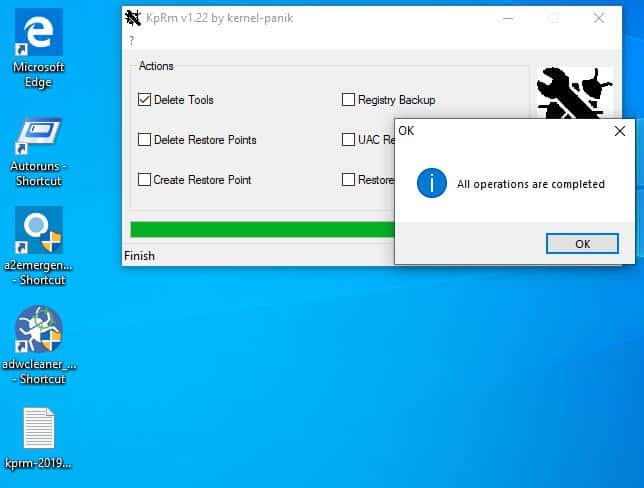
One odd thing that I noticed during the testing process was that KpRm deleted its own executable (KpRm) after finishing the cleaning operation. This was really annoying since I had to copy it over and over while testing it.
An interesting observation
KpRm failed to delete the Emsisoft Emergency Kit folder and its contents in my test.
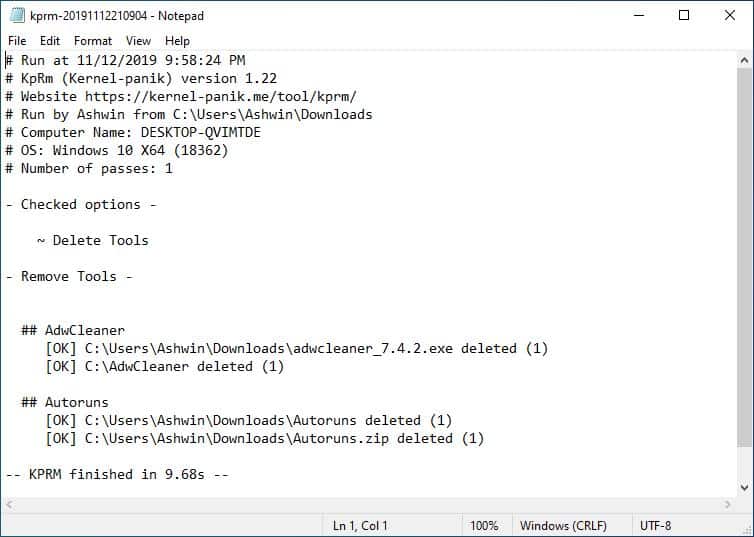
That's probably because I copied the EEK folder from my main Windows 10 to the virtual machine's downloads folder. But, the other tools were located in the Downloads folder too, so why did KpRm delete those and completely miss EEK? My guess was KpRm is probably set to detect the "EEK folder" inside its default location C:\EEK\, which is why it didn't scan the Downloads directory.
To put this to the test, I copied the Emergency Kit folder to the C drive, and then ran KpRm again. And this time it found and deleted it just fine. Based on this, we can assume that the application only searches known locations where the malware removal tools usually run from and deletes them.
Advanced options
KpRm has some additional tools which can be handy. However, I'd advise not using these unless absolutely necessary. You can use the restore point options to delete or create system restore points. It also has a registry backup tool but to restore it you'll need to use a different tool called KPLive (also from the same developers).
The final option is the Restore system settings toggle which is sort of a post-malware disinfection tool that resets the DNS, Winsock, hides hidden and protected files, and displays known file extensions.
Closing Words
I would have preferred it if the tool had a scan for tools option, rather than deleting them outright. EEK for example can be updated without re-downloading the entire package, and serves as a secondary scanner. A scan option and a results page much like the quarantine option in antivirus programs which you can go over, and delete items from manually, would make KpRm even better.
Another thing that I think is missing is a dry-run mode to determine what the program will do when it is run in earnest.























Hello,
I am the developer of KpRm and I have just published a new version that includes your comments.
Thank you
AutoRuns by Sysinternals can help you clean up left-over elements that some programs leave behind.
Some of these repair tools make more harm than good.
Wait, Ashwin! The experiment used all portable programs, yes?
A truly portable program, according to John Haller, known for the Portable Apps site where one can safely download and use numerous programs, never leaves a trace of itself upon removal or even during use. That’s why portable programs can run on a USB without the need for the mother OS.
If the programs used were AdwCleaner, Autoruns, and Emsisoft Emergency Kit, all one needs to do is delete the folder made during unpacking. No registry entries are created; they are basically a sandboxed program. Much like those made using Cameyo.
Unless . . . the programs weren’t truly portable.
Soft Organizer works perfectly for cleaning out residual software files/reg keys used for one time purposes with a simple “tracing” method. Load Soft Organizer, click on trace, install program, use once, finish the tracing.
When it comes time to uninstall, click on the “traced” program and the loads of garbage files are deleted.
And Soft Organizer isn’t an “optimizer,” but it sure keeps a machine clean.
Once infected I cannot trust that machine anymore. OS needs to be wiped and reinstalled clean (or restored from a known clean state, from a backup) and everything else thoroughly scanned.
An alternative to full system wipe / format:
A reasonable check with a good antivirus, malware checker then a registry cleaner to remove the remnants. After, chkdsk and sfc followed by a utility to clear/overwrite slack space with a mild encryption to prevent any lingering code from coming back.
If that doesn’t work…Plan B
Throw out the entire machine! The keyboard, mouse, monitor…All those devices were somewhat tainted by the infection and therefore should be considered no longer trustworthy. I think an eyewash station should also be employed since you might have looked at the virus during its removal. Acid bath for your fingers since they did touch the keyboard during infection and that should do the trick!
@Yuliya,
Exactly.
I tried Panda Free Antivirus…which for me, was too resource heavy. I could not remove all remnants. So, I wiped and won the battle.