- September 2018 Security Updates release notes
- List of software updates for Microsoft products
- Security Updates Guide
- Microsoft Update Catalog site
- Our in-depth Windows update guide
- How to install optional updates on Windows 10
- Windows 10 Update History
- Windows 8.1 Update History
- Windows 7 Update History
Microsoft Windows Security Updates September 2018 release overview
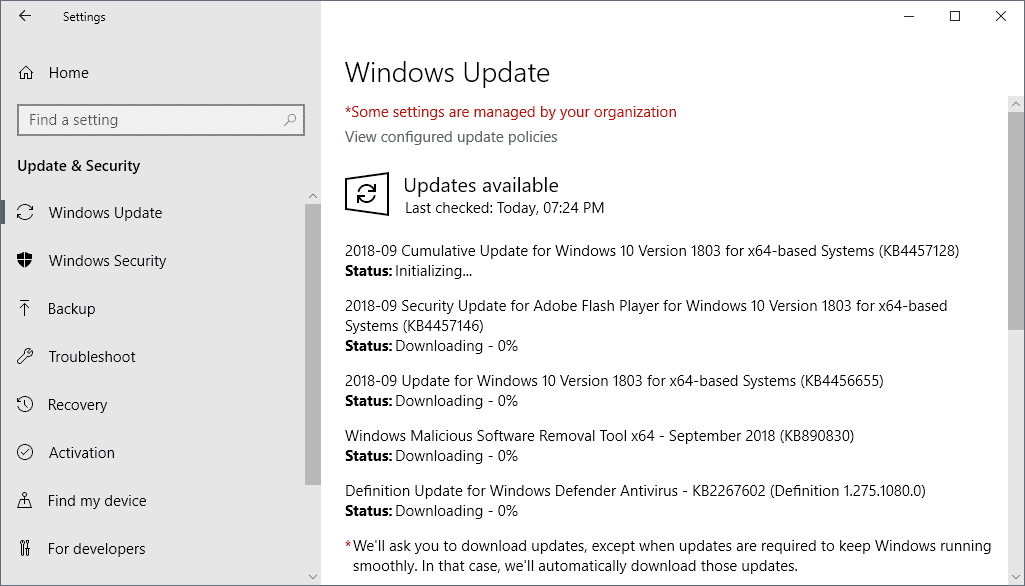
Today is the second Tuesday of the month and that means that Microsoft has just released security updates for all supported company products.
The August 2018 Patch Day was rather uneventful, especially if you compare it to the July 2018 Patch Day which introduced quite a few serious issues.
Microsoft released security updates for all versions of Windows the company supports officially, for Microsoft Office, and for other company products.
The updates are already available on Windows Update, the Microsoft Download Center, and through other means.
Our monthly series provides you with an overview of this month's security updates and non-security updates that Microsoft released. Links are provided to read up on particular patches on Microsoft's Support website and there is a handy resource listing at the end for deeper information.
Note: We recommend that you wait with the installation of updates until the dust settles. Updates may fix issues but they may also introduce severe issues that may cause all kinds of issues. In any case, we recommend that you create a backup of the system before you install Windows updates.
Microsoft Windows Security Updates September 2018
You may download the following Excel file that lists all released security updates for all Microsoft products in September 2018. Click on the following link to download the file to your system: (Download Removed)
Executive Summary
- Microsoft released security updates for all supported client and server versions of Windows.
- The following Microsoft products received security updates as well: Microsoft Edge, Internet Explorer, Microsoft Office, Adobe Flash Player, the Microsoft .NET Framework.
- Microsoft revealed this week that Enterprise customers may extend the support period of Windows 7 by three years.
- 127 individual patches according to Microsoft Update Catalog.
Operating System Distribution
- Windows 7: 18 vulnerabilities of which 3 are critical and 15 are important.
- Windows 8.1: 22 vulnerabilities of which 4 are critical and 18 are important.
- Windows 10 version 1703: 25 vulnerabilities of which 5 are critical and 18 are important. (extra critical is CVE-2018-0965)
- Windows 10 version 1709: 24 vulnerabilities of which 4 are critical and 20 are important.
- Windows 10 version 1803: 29 vulnerabilities of which 5 are critical and 24 are important. (extra critical is CVE-2018-0965)
Windows Server products
- Windows Server 2008 R2: 18 vulnerabilities of which 3 are critical and 15 are important.
- Windows Server 2012 R2: 22 vulnerabilities of which 4 are critical and 18 are important.
- Windows Server 2016: 25 vulnerabilities of which 5 are critical and 20 are important.
Other Microsoft Products
- Internet Explorer 11: 6 vulnerabilities, 3 critical, 3 important
- Microsoft Edge: 13 vulnerabilities, 7 critical, 6 important
Windows Security Updates
Note: Some Windows 7 systems hit by error 0x8000FFFF when trying to install KB4457144. Best to avoid until resolved.
KB4457144 -- Windows 7 SP1 Monthly Rollup
KB4457145 -- Windows 7 SP1 Security-only Rollup
- Security updates for various components such as Windows media, Windows Shell, Windows kernel, or Windows MSXML.
KB4457129 -- Windows 8.1 Monthly Rollup
KB4457143 -- Windows 8.1 Security-only Rollup
- Same description as for Windows 7 SP1.
KB4457138 -- Windows 10 version 1703 cumulative update
- Security updates to Internet Explorer, Microsoft Edge, Microsoft scripting engine, Microsoft Graphics Component, Windows media, Windows Shell, Device Guard, Windows datacenter networking, Windows kernel, Windows hyper-V, Windows virtualization and kernel, Microsoft JET Database Engine, Windows MSXM, and Windows Server.
KB4457142 -- Windows 10 version 1709 cumulative update
- Security updates to Internet Explorer, Microsoft Edge, Microsoft scripting engine, Windows graphics, Windows media, Windows Shell, Windows cryptography, Windows virtualization and kernel, Windows datacenter networking, Windows hyper-V, Windows Linux, Windows kernel, Microsoft JET Database Engine, Windows MSXML, and Windows Server.
KB4457128 -- Windows 10 version 1803 cumulative update
- Protection against CVE-2017-5715, a Spectre 2 variant for ARM64 devices.
- Fixed excessive processor usage by the Program Compatibility Assistant service.
- Security updates to Internet Explorer, Microsoft Edge, Microsoft scripting engine, Microsoft Graphics Component, Windows media, Windows Shell, Windows Hyper-V, Windows datacenter networking, Windows virtualization and kernel, Windows Linux, Windows kernel, Microsoft JET Database Engine, Windows MSXML, and Windows Server.
KB4457131 -- Windows Server 2016 cumulative update -- Requires Servicing Stack Update KB4132216
- Security updates to Internet Explorer, Microsoft Edge, Microsoft scripting engine, Microsoft Graphics Component, Windows media, Windows Shell, Device Guard, Windows Hyper-V, Windows catacenter networking, Windows kernel, Windows virtualization and kernel, Microsoft JET Database Engine, Windows MSXML, and Windows Server.
KB4457426 -- Internet Explorer 11 cumulative update
KB4338381 -- Windows Embedded POSReady 2009 and Windows Embedded Standard
- Information disclosure vulnerability. See CVE-2018-8271.
KB4457046 -- Windows Embedded POSReady 2009 and Windows Embedded Standard
- .Net Framework 4.0 Security-only update
KB4457058 -- Windows Embedded POSReady 2009 and Windows Embedded Standard
- .Net Framework 3.0 Security-only update
KB4457140 -- Windows Embedded 8 Standard and Windows Server 2012
- Security Only Quality Update
KB4457146 -- Security Update for Adobe Flash Player
KB4457163 -- Windows Embedded POSReady 2009 and Windows Embedded Standard
- Elevation of privilege vulnerability. See CVE-2018-8468 for details.
KB4457914 -- Security Only Update for .NET Framework 3.5.1 for Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4457915 -- Security Only Update for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows Embedded 8 Standard and Windows Server 2012
KB4457916 -- Security Only Update for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows 8.1 and Windows Server 2012 R2
KB4457917 -- Security Only Update for .NET Framework 2.0 for Windows Server 2008
KB4457918 -- Security and Quality Rollup for .NET Framework 3.5.1 on Windows Embedded Standard 7, Windows 7, and Windows Server 2008 R2
KB4457919 -- Security and Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows Embedded 8 Standard and Windows Server 2012
KB4457920 -- Security and Quality Rollup for .NET Framework 3.5, 4.5.2, 4.6, 4.6.1, 4.6.2, 4.7, 4.7.1, 4.7.2 for Windows 8.1, Windows RT 8.1, and Windows Server 2012 R2
KB4457921 -- Security and Quality Rollup for .NET Framework 2.0, 3.0, 4.5.2, 4.6 for Windows Server 2008
KB4462774 -- Security Only Update for .NET Framework 4.0 on WES09 and POSReady 2009
KB4457984 -- Security Only Quality Update for Windows Server 2008
KB4458000 -- Security Update for WES09 and POSReady 2009
KB4458001 -- Security Update for WES09 and POSReady 2009
KB4458003 -- Security Update for WES09 and POSReady 2009
KB4458006 -- Security Update for WES09 and POSReady 2009
KB4458010 -- Security Monthly Quality Rollup for Windows Server 2008
KB4458318 -- Security Update for WES09 and POSReady 2009
Notes
- ADV180022
- ADV180023
- CVE-2018-8315
- CVE-2018-8331
- CVE-2018-8336
- CVE-2018-8419
- CVE-2018-8424
- CVE-2018-8429
- CVE-2018-8430
- CVE-2018-8433
- CVE-2018-8434
- CVE-2018-8442
- CVE-2018-8443
- CVE-2018-8444
- CVE-2018-8445
- CVE-2018-8446
- CVE-2018-8452
- CVE-2018-8474
Known Issues
-> Windows 7 SP1 and Server 2008 R2
Network interface controller may stop working after the update is installed.
Workaround:
- Load devmgmt.msc the Device Manager and check under Other Devices.
- Select Action > Scan for Hardware Changes.
-> Windows 10 version 1803
Listed as having issues in the release notes but no known issues listed on the KB support page.
-> Exchange Server 2010 SP3
A manual install of the security update in normal mode and double-clicking on the update file causes some files to be updated incorrectly.
Security advisories and updates
ADV180022 | Not yet published
ADV180023 | September 2018 Adobe Flash Security Update
Non-security related updates
KB4023057 -- All Windows 10 editions -- Reliability update, check this article.
KB4456655 -- Windows Server 1803 Servicing stack update
KB890830 -- Windows Malicious Software Removal Tool - September 2018
Microsoft Office Updates
Microsoft released non-security patches for Microsoft Office last month. You can check out our coverage of the September 2018 Office non-security updates here.
Office 2016
KB4092460 -- Excel 2016 security update that protects against a remote code execution vulnerability. See CVE-2018-8429.
Kb4092447 -- Word 2016 security update that protects against a remote code execution vulnerability. See CVE-2018-8430 for information.
- Word 2016 specific: fixes issues that lead to the error messages "The export failed due to an unexpected error.", "Word couldn't send mail because of MAPI failure:"Attachment not found".", and "A table in this document has become corrupted.".
Office 2013
KB4032246 -- Word 2013 security update. Same as for Word 2016.
KB4092479 -- Excel 2013 security update. Same as for Excel 2016.
Office 2010
KB4227175 -- Excel 2010 security update. Same as for Excel 2016.
Other Office Products
Kb4092466 -- Microsoft Office Compatibility Pack Service Pack 3
KB4092467 -- Excel Viewer 2007
KB4092459 -- SharePoint Enterprise Server 2016
KB4092470 -- SharePoint Enterprise Server 2013
KB4022207 -- SharePoint Server 2010
How to download and install the September 2018 security updates

All security updates are released via Windows Update, the Microsoft Update Catalog, and various services that are available only to
Updates scans are made regularly by the operating system but they don't happen in real-time. You can run a manual check for updates at any time in the following way on client versions of Windows:
- Tap on the Windows-key or activate the Start button with the mouse.
- Type Windows Update and select the program from the list of search results.
- Select check for updates to run the manual check.
Windows 7 SP1 and Windows Server 2008 R2 SP
- KB4457144 -- 2018-09 Security Monthly Quality Rollup for Windows 7
- KB4457145 — 2018-09 Security Only Quality Update for Windows 7
Windows 8.1 and Windows Server 2012 R2
- KB4457129 — 2018-09 Security Monthly Quality Rollup for Windows 8.1
- KB4457143 — 2018-09 Security Only Quality Update for Windows 8.1
Windows 10 and Windows Server 2016 (version 1607)
- KB4457131 — 2018-09 Cumulative Update for Windows 10 Version 1607
Windows 10 (version 1703)
-  KB4457138 — 2018-09 Cumulative Update for Windows 10 Version 1703
Windows 10 (version 1709)
- KB4457142 — 2018-09 Cumulative Update for Windows 10 Version 1709
Windows 10 (version 1803)
- KB4457128 — 2018-09 Cumulative Update for Windows 10 Version 1709
Additional resources






















In blog, any information about KB3177467 is not mention.
Please see https://news.thewindowsclub.com/microsoft-explains-why-windows-7-update-kb3177467-failed-93281/ and https://www.askwoody.com/2018/solution-for-the-error-0x8000fff-in-windows-7/ .
I am running Windows 10, version 1709, x64.
Windows update did not detect/download/install KB4457142, a security update.
Windows update installed the following on September 12th
KB4457146 Security update for Adobe Flash Player
KB4023057 for update reliability
Just picked up KB4090007: Intel microcode updates today on September 16
How did I know I didn’t install KB4457142?
I ran Belarc Advisor. Belarc is a good tool to use since Secunia was retired.
I downloaded it manually from the update catalog http://www.catalog.update.microsoft.com/Search.aspx?q=KB4457142
On Patch Tuesday I successfully installed all offered KBs for my Windows 10 x64 laptop. However today 2018-09-14 Windows Update offered and successfully installed KB4100347. Version and build numbers stayed the same.
I used WSUS Offline Update to install security-only updates for Windows 10 Enterprise 1709 Semi-Annual, Windows 7 SP1 Enterprise, Windows 7 SP1 Pro, Office 2016, and Office 2010 (plus updates to Microsoft Silverlight on all computers and to the Remote Desktop Client on the Windows 7 computers). Maybe I was just lucky, but everything seems to have gone okay. (And according to Windows Privacy Dashboard, no unwanted telemetry or diagnostics got switched back on.) I still have two more Windows 7 computers with Office 2010 on them left to update, but I’m not too worried. If that network-interface-controller problem crops up, the workaround — which I hope means “durable one-time fix”! — looks pretty easy.
I am in the clear, no updates yet for my Windows 10 Pro semi-annual-channel (not targeted).
Error 0x8000FFFF when trying to install KB4457144 on Windows 7:
Check installed updates to see whether KB3177467 (the Servicing Stack Update issued September 2016) is installed.
If not, then download and install it, restart, then try installing KB4457144.
KB3177467 for all versions of Windows 7 can be downloaded from: https://support.microsoft.com/en-us/help/3177467/servicing-stack-update-for-windows-7-sp1-and-windows-server-2008-r2-sp .
It also works for me.
Thanks Martin you’re a Godsend
I’ve not been able to install the Quality Update on my Windows 7 computer since the July debacle. I can individually install the Security Updates, the .Net updates, and so forth, but every attempt to install the Quality Update fails completely. I’ve tried every fix except reinstalling Windows to get it to work. No, I’m not reinstalling Windows 7 for this, I’d rather not risk Windows 10 trying to push itself onto this computer.
More and more I’m looking at a Linux pre-installed computer to replace this computer when it finally begins to fail.
“Note: Some Windows 7 systems hit by error 0x8000FFFF when trying to install KB4457144. Best to avoid until resolved.”
I have this error, too. No Intel cpu.
*Clap,clap* Microsoft, how do you earn you money?
thx4info. and the first time the “windows update mini tool” – mentioned here – was used (while windows updates are disabled by default). perfect.
On my Windows 8.1 x64 system, installed the following updates without any mishaps:
* KB4457143 (security only update)
* KB4457426 (IE11 cumulative)
* KB4457056 (.NET Framework 3.5 – security only)
* KB4457028 (.NET Framework 4.5.2 – security only)
* KB4457146 (Flash player update for IE11)
* This month’s MSRT update (via Windows Update)
I’m not sure why, but I always thought Flash updates for IE11 were only available through Windows Update. But I see now that they’re available via the Catalog as well.
Thanks anyway Martin for all the hard work.
Thanks Martin for the updates’ details.
I installed security only updates without problem on Win 7 & 8.1.
Thank you very much !
The last thing one should do on Windows 10 is manually checking for updates! Otherwise, unwanted updates, such as previews and other half-backed nonsense, may get installed leaving the system in an unpredictable state! Windows 10 was designed as a service delivering updates without user interaction and letting Windows Update doing its job guarantees that only Patch Tuesday and crucial out-of-band updates get installed. So, don’t touch the switch, don’t touch the button, don’t touch nuttin’.
Just the opposite. Leaving Windows 10 on auto update will guaranty the user of unwanted updates, previews , half-backed nonsense, fake drivers, ‘better experiance’ updates, telemetry updates…
The only way to update Windows 10 is manually or better still blocking updates for ever.
Installing patch Tuesday Windows Update successfully updated me to Windows 10 version 1803 (OS Build 17134,285) , However observing the process in progress caused KB4457128 to be downloaded 3 times and installed twice. Windows Update History for KB4457128 is marked (2) and was successful.
I could not download Martin’s SecurityUpdates.xlex file using latest Chrome, even trying an incognito window to eliminate extensions. The download attempt just retried for a minute or two without success. I then tried IE11 and got the excellent download without a problem.
Thanks to TelV whose comment has not yet migrated here, Microsoft WU takes care of installing prerequisite KB4456656 if needed before installing KB4457128. I missed inferring this from https://support.microsoft.com/en-us/help/4457128/windows-10-update-kb4457128 .
@chesscanoe,
This update behaviour occurs if KB4456655 which is a servicing stack update wasn’t installed prior to installing KB4457128: https://borncity.com/win/2018/09/12/patchday-issues-with-updates-wsus-september-11-2018/#more-6957 (See paragraph: “Update KB4457128 installed twice”)
Thanks a lot for the information !