Check your passwords against the Pwned Passwords database
Is a password that you use actively to protect an account secure? The question is difficult to answer as it depends on your definition of secure.
Secure can mean, among other things, that it cannot be cracked in reasonable time, or that it is not already on a publicly accessible password list.
Pwned Passwords
The Pwned Passwords database of Have I Been Pwned has been updated recently with new password data sets.
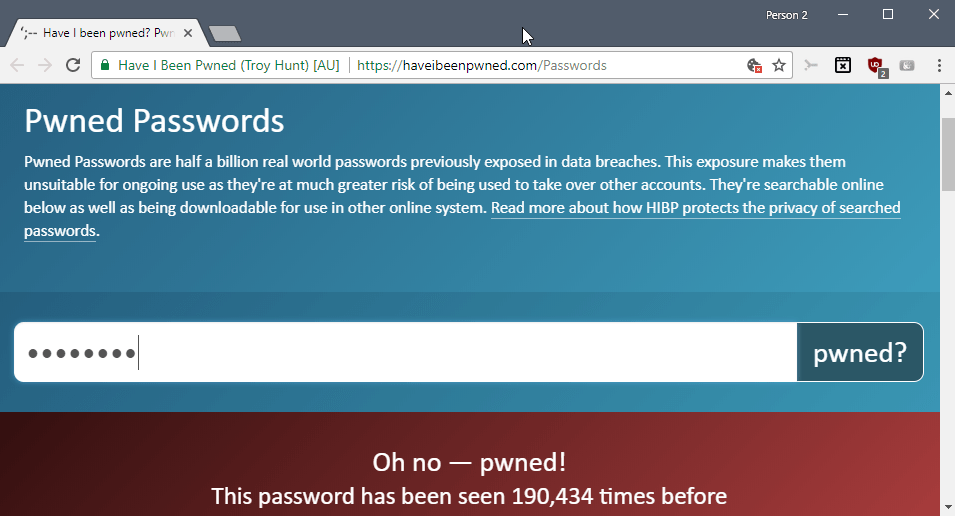
The service accepts a password and reveals whether it was found on any of the lists that powers the service's database.
All you have to do is type a password to find out whether it is available in the clear-text format on a public password dump list.
Some users may have reservations when it comes to typing passwords that they use on a site on the Internet. That site, in theory, could use the information for malicious activity. While it requires a username, usually that goes along with it, adding the password to a list to run dictionary attacks against services could have negative consequences for the user who entered it on the site.
That's one reason why you may download the entire database to your local system. It is available as a zipped torrent file; the torrent file has a size of 8.8 Gigabytes and contains a list of 501 million password hashes and password use counts. The archive extracts to a single 30 Gigabytes large text file that many text editors won't open.
Use a free program like Large Text File Viewer to open the text document on your system.
You need to compute the SHA-1 hash of your passwords and may use a free program like HashCalc for that which supports the computation of hashes from text strings among other things.
You'd then search the downloaded database file for that Sha-1 hash to find out if the password leaked before.
Attackers may use public password lists in attacks, especially if passwords are popular.
If a password is found in the database, it is advised to change it and use a password that is not found. Generally speaking, it is best to assume that any password that is listed in the database is known to attackers and should not be used anymore.
Now You: How do you make sure to select secure passwords for accounts?
Related articles
- Dashlane wants to automate passwords in 2018
- Encryption and Strong Passwords
- KeePass 2.36: detect duplicate or similar passwords
- Password Use Study: massive reuse of passwords
- You should not be using these passwords



















thx for this article, being able to check pws on the list without exposing anything anywhere. kr
I keep wondering what to say to this. Seen it mentioned on a couple forum sites an thought “huh”. Im going to go somewhere else now.
I typed the p/w my girlfriend uses and unsurprisingly (since it’s pretty weak), it appears to have been used twice before.
I’ll send here the link and hope the result teaches her a lesson.
I don’t see any cause for concern for others worried about typing their own passwords on the site since it’s using a EV certificate.
@TelV: “I don’t see any cause for concern for others worried about typing their own passwords on the site since it’s using a EV certificate”
While I don’t think this site is unusually risky, I did want to point out the using an EV cert should not give you a sense of security for this sort of thing. You’re still trusting that the site is handling your sensitive data properly. No cert in the world addresses that issue.
Apologies for the late response John. I’m afraid I only just received notification of it.
Anyway, the point I was trying to make with EV certificates is that to obtain one, the site owner has to comply with the more rigorous requirements to obtain one. Here’s a quote from Wikipedia on the subject:
“EV certificates are validated against both the Baseline Requirements and the Extended Validation requirements, which place additional requirements on how authorities vet companies. These include manual checks of all the domain names requested by the applicant, checks against official government sources, checks against independent information sources, and phone calls to the company to confirm the position of the applicant. If the certificate is accepted, the government-registered serial number of the business as well as the physical address are stored in the EV certificate.”
I trust that clarifies the matter.
“How do you make sure to select secure passwords for accounts?”
I use a password generator to generate random passwords, a different password for every login*.
*I do cheat a little on this — with my own servers and services, I have a single “internal password” that I use to access systems that you already have to be in my VPN to get to. That password gets changed about ever 90 days, and is never used for any other purpose. It’s a compromise, to be sure, but one that I’m OK with since you must have already subverted my VPN in order for it to be useful.
1Password/AgileBites uses the pwned password database
And don’t forget to change your password after that ;)
And don’t create a same password than the one you’ve submitted for checking…
With these conditions such a site remains valid IMO essentially in two scenarios,
1- You’ve been hacked, was it possibly related to a password? Check it out and, whatever the answer, change it as o_O above recommends to do so;
2- Curiosity. Submit passwords to evaluate the correlation between their build and their availability on the site’s database… but don’t use those submitted afterwards. I wouldn’t, anyway. In this regard, a good application, filled with information and various detailed password strength analysis, called “Strong Passwords Need Entropy” : excellent IMO.
Isn’t this exactly what the Pwned Password wants in order to just grow more its database? To provide them with our passwords by checking them up?
Heh we said long time goodbye to sincerity now did we?
“Now You: How do you make sure to select secure passwords for accounts?”
Who, me? :) I use unique 32 characters alpha-numeric + custom passwords (32 or less if the site limits the length to <32). I don't provide a usual name for my favorite pet or mom's name but instead another 32chrs. password. Password managers nowadays are legion and the only effort is in finding the best suitable for our expectations.
Concerning the online Pwned Passwords checking I wouldn't check (online) a password I use, but I could test new ones, just to see. After all there's only the user who knows if the password he's checking in elaborated from imagination or factual.
Hi
If you have 30GB to spare on your HardDisk and you have Python installed (or you are willing to install it), you can download the DB with hashed passwords from https://downloads.pwnedpasswords.com/passwords/pwned-passwords-2.0.txt.7z and my script from https://github.com/STech-Ics/pwnedPasswordsLocal and you can check all your passwords locally, without any connection to Internet.
The python script is not so polished, but it works fast and for lists of passwords too.
Cheers!
PS: Thanks Martin for the article. Now I can demonstrate to my wife how bad she is at inventing passwords :)
Troy Hunt the owner of this and HaveIbeenPawned, in his blog post: https://www.troyhunt.com/ive-just-launched-pwned-passwords-version-2/#cloudflareprivacyandkanonymity
does state he does not necessarily want to encourage people to plug their passwords into any third party service. I quote:
[QUOTE]Getting back to the online search, being conscious of not wanting to send the wrong message to people, immediately before the search box I put a very clear, very bold message: “Do not send any password you actively use to a third-party service – even this one!” [/QUOTE]
That was from the above post and was referencing version 1. However he comments further on this and partially justifies why he is doing this:
[QUOTE]As much as I don’t want to encourage people to plug their real password(s) into random third-party sites, I can guarantee that a sizable number of people got a positive hit and then changed their security hygiene as a result. One of the biggest things that’s resonated with me in running HIBP is how much impact it’s had on changing user behaviour. Seeing either your email address or your password pwned has a way of making people reconsider some of their security decisions. [/QUOTE]
Interesting to find that my old password I used to use everywhere (terrible practice) has not been leaked :) It was a relatively unsafe password, but it wasn’t a word.
Remember: you shouldn’t be able (or need) to remember your passwords.
I tried my WLAN and router’s passwords there, I was curious.
WLAN: Good news — no pwnage found!
router: Oh no — pwned! This password has been seen 24 times before
Interestingly enough, in my mind, the pass that I set for my router is stronger than the one I set for my WLAN.
I won’t try any of my accounts passwords, even though I am aware of who Troy Hunt is. Still, interesting..
Entering your password in a site like this puts your password in a list that potentially could be used for brute force attacks. Hackers are so resourceful. Instead of creating their own lists, they masquerade as a password checking facility, and get everyone else to add words to their list.
Don’t do it.
I’m not pasting my passwords into any site but the one I wish to log in to. However, I am grateful that this website exists to check my email for pwnage. So thanks for that.
I use Keepass and change my passwords regularly.
That’s a fully reasonable position (and one that I share). This service appears to be trustworthy, but nobody should expand their attack surface regardless of how trustworthy the service is if there isn’t a good reason to expand it.
As I see it, the utility of this service is really for people who have poor password habits — namely, people who use the same password with multiple services/sites. If you are strict about never reusing passwords, then this service is of limited value.
So my recommendation is: generate a new (and completely random) password for each site and service you use.
If you’re unwilling to do that, then this service is actually important, so that you have an indication that you need to go change the passwords for all the other sites/services that use the same one.
Absolutely ditto MarkCB.
I’d love to know, but this is counter-intuitive to everything I’ve learned about security.
There’s a KeePass plugin for it: https://github.com/andrew-schofield/keepass2-haveibeenpwned