Password Use Study: massive reuse of passwords
A recent password use study by the German Hasso-Plattner-Institute of roughly 1 billion user accounts concluded that 20% of users were reusing passwords. Additionally, 27% of users used password that were nearly identical with other account passwords.
User accounts and passwords are still the dominating method of authentication both locally and online.
While companies work on replacing passwords with other methods, think password pills and tattoos, or the increasing use of authentication apps and biometric authentication means, nothing is out there that has replaced the good old username and password combination yet.
The authentication scheme has its flaws. Three major ones are that passwords, or their hashes, may be stolen when servers are attacked successfully, that weak passwords are common, and that nothing is keeping users from reusing passwords.
These hacks happen frequently, and they hit smaller and larger companies. It is likely that some are not made public at all, but the list of companies that disclosed successful hacks recently includes Yahoo, Dailymotion, VK, MySpace, Friend Finder Network, or Brazzers.
Password Use Study: massive reuse of passwords
Researchers of the institute analyzed about 1 billion user accounts. The data came from 31 leaks that were made public either by the attackers themselves or by buyers.
About 68.5 million email addresses appeared multiple times in the database; that is about 20% of all user accounts found in the data according to the researchers.
About 27% of all users selected passwords were at least 70% identical to other passwords that the user's used. This indicates minor changes to a core password, for instance by using "princess" as the core password, and variations such as "pr1ncess", "princess1" or "princ3ss".
These variations are sometimes used if a site's password policy requires special characters, numbers, or other characters that are absent in the core password.
The most common passwords are "123456", "123456789", "111111", "qwerty", and "12345678" according to the study.
Check your email address
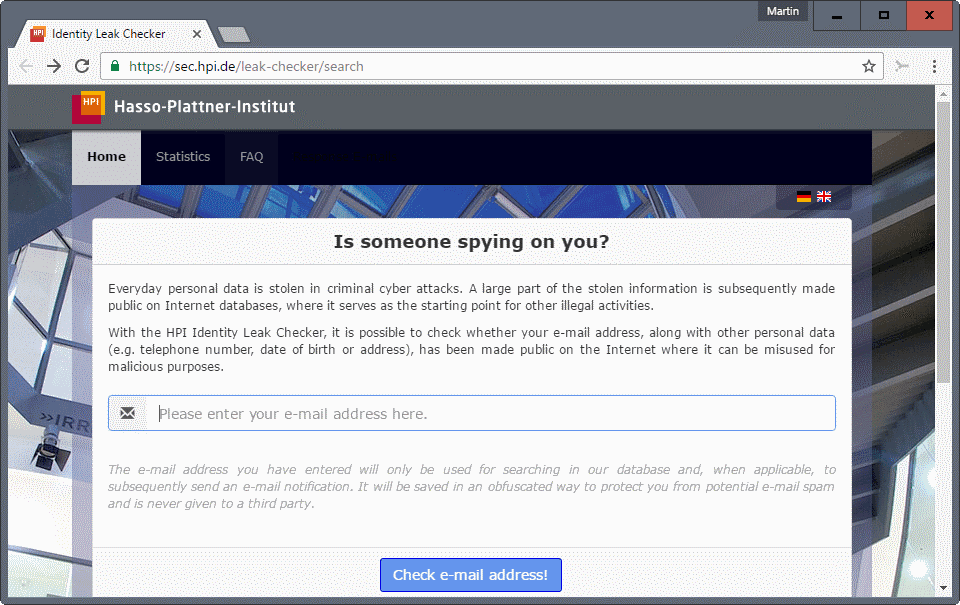
The institute runs an email checker that you may use to find out if the entered email address appeared in one of the leaks.
All you need to do is enter your email address, click on the check button, and wait for the results to arrive in your email inbox.
If that is the case, it is suggested to change the password immediately to avoid abuse. Also, it is recommended to change the password at other services if you have reused it.
The institute is bound to German (privacy) laws. The (German) press release that announced results of the study is available here.
Now You: How do you handle passwords?


















nexusmods … majorgeeks.com … Gamigo … Do people actually use their real email addresses for commercial websites? I use a throwaway address for online forums, etc. and my real email address for conducting serious business, and ne’er the twain shall meet.
That’s what I do as well, that’s what we should all do, when many, too many users provide a true email address and a childish password moreover… and are surprised with breaches, spam …
Also, beware of cookies, some sites don’t encrypt their cookies — YOUR cookies for that site — so clean your cookies and login next time. Fight for your privacy or don’t complain. From there on we have of course users who’ve done it all and still get their data compromised, like when a site has been hacked : again, with a DEA a clean Sunside Strip is one-click away : remove the DEA, create a new one and modify your login consequently : no problem, no fuss.
This study is as good as the study done to find out if you get more or less wet while running or walking in the rain.
ofcourse people are going to reuse password’s as its safer when compared to accidently being locked out of your ac & losing all your data & being hassled by the companies to assist in retrieval of ac, even though at present the ac retrieval process is much safer & more friendlier to the user. the issue remains.
The reason it persists is because companies are not liable for your safety online. & the reason for this is YOU.
when we (YOU) chose the internet to be free, we give up the right to be protected by it.
i am a strong proponent for open source software, but if you use a service & its free then you are participating in open source development, hence are not legally viable to be protected by the service in case of a fault.
If you paid for a service, & there is a breach or fault you are legally protected irrespective of the terms & conditions, as when you pay there is a reasonable expectation of protection to be provided in case of failure
Guess what, if people sued for ac hacks & password dumps from paid services, the companies would be bending backward to secure login system, by even go so far as to do way with using passwords & issuing unique login devices.
let me share with you an experience, some months back i had to send an email with a mathematical equation about some statistical analysis. i never use my email(gmail) to email anybody i personally know, for personal email i use a private service, but the same time i maintain a gmail ac to receive some email from acquaintances & i do recieve spam & other junk.
So after sending this particular email, had to been replied back with some updates & corrections from my friend, after a few back & forth emails i logged out, after 2 days i had a response from a friend 2 spam mail & 1 ad for a statistical software, i ve never seen any spam any where for statistical software ever.
so now you know, gmail is corporate open source, but only on paper, in reality they are just like face book a DATA MINE to sell MINED DATA for ad revenue.
want to change that?, then invest in paid services, as they are legally bound not to profit from your DATA as you pay for their services.
Be wise & make a choice thats Sound, Dont mindlessly click that like button, click on Delete-My-account after you understand why.
That’s two different things : the quality of your passwords and the E-mail server. You’re evoking a webmail provider : why not choose an alternative? Several excellent Webmail providers are avilable, most requiring around 1$/month which is worth it. Of course we’re omitting here desktop email clients.
I don’t have one spam, not one. My option is DEA (Disposable Email Address), a good one for which I pay about 1$/month as well, and for which I’ve provided moreover an alias of one of my email accounts as my true email address.
A broken email address can originate with a site, or with the email intercepted (even encrypted : that’s why your choice of a “private service” is good) or — the most likely — because your correspondent got hacked himself (mainly on a desktop email client). I face a risk only with the last scenario, up to now no problem.
Risk zero doesn’t exist but it may be seriously reduced. Partitioning, compartmentalizing is the master idea, to minimize as mush as possible a link to the source (you, me, us) by setting several entries.
What a paradox it would be to use a computer without using this computer for a task it excels in : managing data.
What a pity it would be to try to remember dozens, hundreds of logins, names and passwords rather than leaving this up to the computer.
All browsers nowadays manage logins and there are as well several excellent password managers available. Why not use them? Too complicated? Then use the browser’s built-in password manager, you’ll still have to invent passwords by yourself but the limit will be those of your imagination together with the site’s requirements, never your memory.
Like most of us, yet not as all of us as explained in the article, I never use simplistic passwords and I always ude a different password.
Not simplistic passwords means I start (using a password generator) on the basis of 32 characters mixing small and capital letters, digits and special characters. Some sites have an upper limit as well, such as the number of characters and only some of the special characters. If so, we build the password with those limits.
Nowadays it is so easy to manage an unlimited number of complex and unique logins that my bet to explain the behavior of users corresponding to what is noted in the article, is not that they’d be ignorant, or simple-minded, but just that they haven’t understood the consequences of a password driven towards the clouds of the Web : they haven’t perceived the cause to consequence relationship.
It’s about time they do get aware. Like on roads, misconducts may harm many more than the driver only.
I have a friend who works at the local public library. There are a LOT of people who use the public library computers, because they don’t have/can’t afford their own.
I suspect a very large chunk of the simple/repeated passwords are drawn from that demographic. You don’t get to use the computer to manage your passwords, because it’s not *your* computer. Plus, a lot of these people are really low on the “computer literate” list. My friend has stories about people who need to ask for help using the mouse (admittedly an extreme example, but poor computer literacy is hardly uncommon).
When people are asked to create pin numbers for their library card, the single most used value is ‘1234’. They can’t carry around a password manager with them, so they just use passwords that are so stupidly simple that they don’t have to worry about losing or forgetting them.
So yeah, recognize that there’s a lot more that’s relevant to these issues than the easy-to-blame targets.
Tom, it’s not a paradox to me to not use a computer to manage passwords. Instead it’s an avoidance of a logical endless loop or nested recursion.
I am a big fan of KeePass for passwords to “less important” or “non-critical” sites. Works great, and I appreciate the effort that goes into that software. I also like that the passwords I trust to KeePass are stored locally, and are not sprayed all over creation onto a server somewhere, like the cloud-based password managers do.
But when it comes to my important or critical passwords, they are not stored on my computer at all. They are in a pencil and paper form. Here is where the recursion is avoided. If my computer did get hacked, the passwords stored on my computer would then open up a world of mischief. But the pencil and paper records are hard to identify and find, much less machine read and decrypt.
Some of the password choices made here depend a lot on your daily habits. If you need a 32 character sign-in several times a day, the computer is definitely a convenience. If, like me, you might need a password once a month, like for a bank statement, then it is a good exercise in typing, and not too big a burden, to key it in from paper.
The general public is not interested in passwords. Soon enough we will be bar-coded at birth, so the problem will go away. The movie “Idiocracy” shows some of the possibilities, for example how a fugitive is spotted by a soda machine as he walks by it on the street. Londoners will be pioneers in this.
Best choices in life are always based on rules tempered by exceptions. Real-Politik, pragmatism, absence of demagogy hence liberty as opposed to binary restrictions.
What I mean here concerning passwords is that you and I will agree on the fact that there is no contradiction between a general rule which is to use a password manager to handle strong and unique passwords and a few exceptions regarding critical data. This is as well my policy, and having half a dozen passwords stored only in brains (with a paper backup elsewhere than on a post-it) is not a problem, given the very few, to memorize (with an original logical structure).
The best of different worlds, in fact. As in life, as I see it.
“pills and tattoos”
People that have no better things to do at home so they try to show the world the genius inside them. Nothankyou, I’ll remember a 20+ random characters string.
Ugh…. at least 5 sites. Nexusmods, Linkedin and Gamigo.
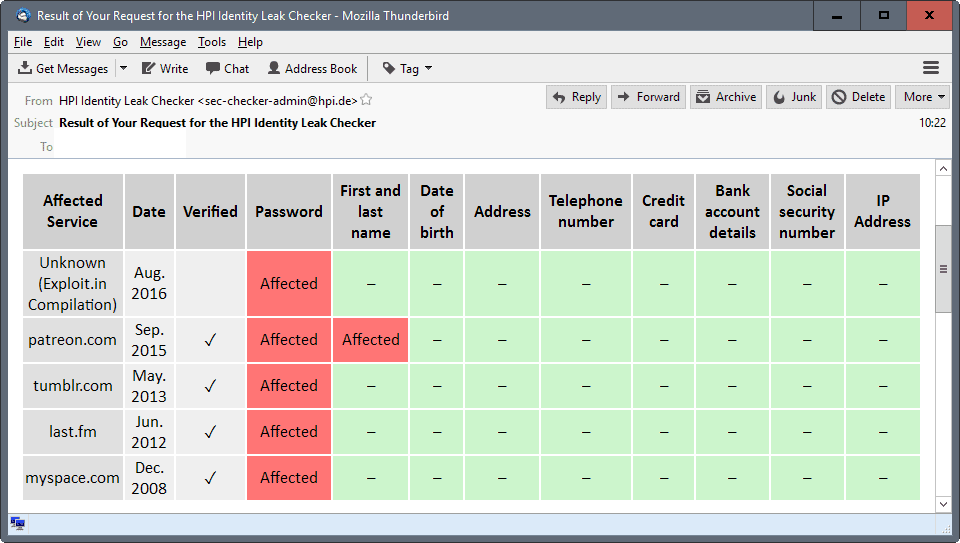
Wonderful. Here’s the result of my HPI Identity Leak Checker for my most used email address.
Verified Leak
Affected Service: majorgeeks.com
Date: Oct. 2015
Password: Affected
IP Address: Affected.
No problems reported with other email addresses.
According to the test one of my email addresses was leaked from “nexusmods” in December 2015, thanks nexus I even donated to you in the past…
Funny enough, I did not received more spam since then.
Hate to say it. but they didnt hide it.
http://www.nexusmods.com/games/news/12675/?
they email and took appropriate steps to contact users that were effected. Maybe you missed the email assuming it was spam/it got caught in spam etc…
Ditto on nexusmods, but also five other services. The funny thing is, that of those six websites only one informed me of the leak and asked me to change my password. While using unique passwords is simply a must nowadays, what’s even more important and disappointing is the lack of honest action by those services that have been compromised. It is not like every user can and will go trawling through internet news and leaked databases all the time in order to find out if they were affected.
The ones that keep quiet are the worst, Fosshub https://www.ghacks.net/2016/08/03/attention-fosshub-downloads-compromised/ is one that comes to mind, after the hacking took place (infected downloads) the owner of said site never spoke anything about the incident, at least I did not find anything.
I use the Firefox extension password hasher, so all my password are unique.
Nexus might have told me to change my pass at the time, but I’m not sure,anyway changed it now.