Microsoft Security Updates July 2017 release
Microsoft released security updates for all supported versions of Microsoft Windows and other company products on July 11, 2017.
The following guide provides you with in-depth information on the July 2017 Microsoft Patch Day. It starts with an executive summary that covers important to-know bits about the updates.
What follows is the distribution of updates for individual operating systems, server and client, and other Microsoft products.
It lists security updates, security advisories, and non-security updates afterwards, each with a short description and link to the Microsoft Knowledgebase article.
Last but not least, you get direct links to download the cumulative security and non-security, and only-security updates for all supported operating systems, and download information.
You can check out the June 2017 Patch day overview for information in case you missed it.
Microsoft Security Updates July 2017
You can download this Excel spreadsheet for a list of all security updates that Microsoft released on the July 2017 Patch Day. Just click on the following link to download the document to your computer: (Download Removed)
Tip: Make sure you create a backup of your system before you install the patches.
Executive Summary
- Microsoft released security updates for all client and server versions of Windows that the company supports.
- All operating systems are affected by critical vulnerabilities.
- Security updates have been released for other Microsoft products as well including Microsoft Office, Microsoft Edge, and Internet Explorer.
- Windows 10 version 1507 won't receive security updates anymore.
Operating System Distribution
- Windows 7:Â 22 vulnerabilities of which 2 are rated critical, 19 important, and 1 moderate
- Windows 8.1: 24 vulnerabilities of which 2 are rated critical, 21 important, and 1 moderate
- Windows RT 8.1: 21 vulnerabilities of which 2 are rated critical, and 21 important
- Windows 10 version 1703: 27vulnerabilities of which 2 are rated critical, 23 important and 1 moderate
Windows Server products:
- Windows Server 2008:Â 22 vulnerabilities, of which 2 are rated critical, 19 important, and 1 moderate
- Windows Server 2008 R2: 23 vulnerabilities, of which 2 are rated critical, 20 important, and 1 moderate
- Windows Server 2012 and 2012 R2: 24 vulnerabilities, of which 2 are rated critical 21 important, and 1 moderate
- Windows Server 2016: 29 vulnerabilities of which 3 are rated critical, 25 important, and 1 moderate
Other Microsoft Products
- Internet Explorer 11: 7 vulnerabilities, 5 critical, 2Â important
- Microsoft Edge: 19 vulnerabilities, 15 critical, 3 important, 1 moderate
- Microsoft Office 2010 Service Pack 2: 2 vulnerabilities, 2 important
- Microsoft Office 2013 Service Pack 1: 1 vulnerabilities, 1 important
- Microsoft Office 2016: 1 vulnerability, 1 important
Security Updates
Windows 10 version 1703 -- July 11, 2017 -- KB4025342 (OS Build 15063.483)
- Addressed issue introduced by KB4022716 where Internet Explorer 11 may close unexpectedly when you visit some websites.
- Addressed issue to improve MediaCreationTool.exe support for Setup Tourniquet scenarios.
- Addressed issue with CoreMessaging.dll that may cause 32-bit apps to crash on the 64-bit version of the Windows OS.
- Addressed an issue where Visual Studio or a WPF application may terminate unexpectedly (stops responding, followed by a crash) when running on a pen and/or touch enabled machine with Windows 10 Creators Update.
- Addressed issue that causes the system to crash when certain USB devices are unplugged while the system is asleep.
- Addressed issues with screen orientation that stops working after lid close and lid open transitions.
- Addressed issue that causes .jpx and .jbig2 images to stop rendering in PDF files.
- Addressed issue where users could not elevate to Administrator through the User Account Control (UAC) dialog when using a smart card.
- Addressed issue where input using the Korean handwriting feature dropped the last character of a word or moved it to the next line incorrectly.
- Addressed issue with a race condition between the App-V Catalog Manager and the Profile Roaming Service. A new registry key is available to control the waiting period for App-V Catalog Manager, which allows any third-party Profile Roaming Service to complete.
Security updates to Internet Explorer 11, Microsoft Edge, Windows Search, Windows kernel, Windows shell, Microsoft Scripting Engine, Windows Virtualization, Datacenter Networking, Windows Server, Windows Storage and File Systems, Microsoft Graphics Component, Windows kernel-mode drivers, ASP.NET, Microsoft PowerShell, and the .NET Framework.
Windows 8.1 and Windows Server 2012 R2 -- July 11, 2017—KB4025333 (Security-only update)
- Security updates to Windows kernel, ASP.NET, Internet Explorer 11, Windows Search, Windows Storage and File Systems, Datacenter Networking, Windows Virtualization, Windows Server, Windows shell, Microsoft NTFS, Microsoft PowerShell, Windows Kernel-Mode Drivers, and Microsoft Graphics Component.
Windows 8.1 and Windows Server 2012 R2 -- July 11, 2017—KB4025336 (Monthly Rollup)
- Addressed issue called out in KB4022720 where Internet Explorer 11 may close unexpectedly when you visit some websites.
- Addressed issue that causes .jpx and .jbig2 images to stop rendering in PDF files.
- And all security updates of KB4025333
Windows 7 SP1 and Windows Server 2008 R2 SP1 -- July 11, 2017—KB4025337 (Security-only update)
- Security updates to Microsoft Graphics Component, Windows Search, Windows kernel-mode drivers, Windows Virtualization, Windows Server, Windows Storage and File Systems, Datacenter Networking, Windows shell, ASP.NET, Microsoft PowerShell, Windows kernel, and Microsoft NTFS.
Windows 7 SP1 and Windows Server 2008 R2 SP1 -- July 11, 2017 -- KB4025341 (Monthly Rollup)
- Addressed issue called out in KB4022168 where Internet Explorer 11 may close unexpectedly when you visit some websites.
- And all security updates of KB4025337.
KB4022746 -- Security Update for Windows Server 2008 and Windows XP Embedded -- Security update for the Kerberos SNAME security feature bypass vulnerability in Windows Server 2008: July 11, 2017
KB4022748 -- Security Update for Windows Server 2008 -- Security update for the Windows kernel information disclosure vulnerability in Windows Server 2008: July 11, 2017
KB4022883 -- Security Update for WES09 and POSReady 2009 -- Windows kernel information disclosure vulnerability: June 13, 2017
KB4022914 -- Security Update for Windows Server 2008 -- Security update for the Windows kernel information disclosure vulnerability in Windows Server 2008: July 11, 2017
KB4025240 -- Security Update for Windows Server 2008 and Windows XP Embedded -- Security update for the Microsoft browser security feature bypass vulnerability in Windows Server 2008: July 11, 2017
KB4025252 -- Cumulative Security Update for Internet Explorer
- Addressed issue introduced by KB 4032782Â where Internet Explorer may close unexpectedly when you visit some websites.
- Addressed issue in Internet Explorer 11 where a text node returned from the DOMParser may be incorrect when MutationObserver for childList and subtree is active.
- Addressed issue in Internet Explorer 11 where a crash can occur in limited scenarios when using the Find feature (Ctrl-F).
- Addressed issue where the onhashchange event fails to trigger when navigating some hashed URLs in Internet Explorer 11.
- Addressed issue where the NewWindow3 event handler is never called in a managed WebBrowser class of .NET 4.6.
- Addressed issue that can cause cursor flicker when hovering over a pop-up menu option in Internet Explorer 11 and Microsoft Edge.
- Addressed issue where Internet Explorer 11 crashes when a user clicks an empty column header and then quickly does a Shift + double click.
- Addressed issue where Internet Explorer 11 crashes with certain Browser Helper Objects after the July Internet Explorer updates.
- Addressed issue where certain elements (input or select) cannot be active targets of any action in Internet Explorer 11. This occurs after removing an iframe that contained a cursor inside certain elements (input or select) and adding a new iframe.
KB4025397 -- Security Update for Windows Server 2008 -- Security update for the Windows Performance Monitor information disclosure vulnerability in Windows Server 2008: July 11, 2017
KB4025398 -- Security Update for Windows Server 2008 and Windows XP Embedded -- Security update for the MSINFO.exe information disclosure vulnerability in Windows Server 2008: July 11, 2017
KB4025409 -- Security Update for Windows Server 2008 and Windows XP Embedded -- Security update for the Windows elevation of privilege vulnerability in Windows Server 2008: July 11, 2017
KB4025497 -- Security Update for Windows Server 2008 and Windows XP Embedded -- Security update for the Windows Explorer remote code execution vulnerability in Windows Server 2008: July 11, 2017
KB4025674 -- Security Update for Windows Server 2008 -- Security update for the Windows Explorer denial of service vulnerability in Windows Server 2008: July 11, 2017
KB4025872 -- Security Update for Windows Server 2008 -- Security update for the Windows PowerShell remote code execution vulnerability in Windows Server 2008: July 11, 2017
KB4025877 -- Security Update for WES09 and POSReady 2009 -- This security update resolves vulnerabilities in Windows Server 2008 that could allow elevation of privilege or information disclosure.
KB4026059- Security Update for Windows Server 2008 --Security update for the Windows CLFS elevation of privilege vulnerability in Windows Server 2008: July 11, 2017
KB4026061 -- Security Update for Windows Server 2008 and Windows XP Embedded -- Security update for the WordPad remote code execution vulnerability in Windows Server 2008: July 11, 2017
KB4032955 -- Security Update for Windows Server 2008 and Windows XP Embedded -- Security update for the Windows Search remote code execution vulnerability in Windows Server 2008: July 11, 2017
KB4033107 -- July 11, 2017, update for Microsoft Office
Known Issues
Important note for CVE-2017-8563: After installing the updates for CVE-2017-8563, to make LDAP authentication over SSL/TLS more secure, administrators need to create a LdapEnforceChannelBinding registry setting on a Domain Controller.
Security advisories and updates
Microsoft Security Advisory 4033453 -- Vulnerability in Azure AD Connect Could Allow Elevation of Privilege
The update addresses a vulnerability that could allow elevation of privilege if Azure AD Connect Password writeback is misconfigured during enablement. An attacker who successfully exploited this vulnerability could reset passwords and gain unauthorized access to arbitrary on-premises AD privileged user accounts.
The issue is addressed in the latest version (1.1.553.0) of Azure AD Connect by not allowing arbitrary password reset to on-premises AD privileged user accounts.
Non-security related updates
KB4034374 -- 2017-07 Dynamic Update for Windows 10 Version 1703 -- Compatibility update for upgrading to Windows 10 Version 1703: July 11, 2017
KB890830 -- Windows Malicious Software Removal Tool - July 2017 -- Remove specific prevalent malware with Windows Malicious Software Removal Tool
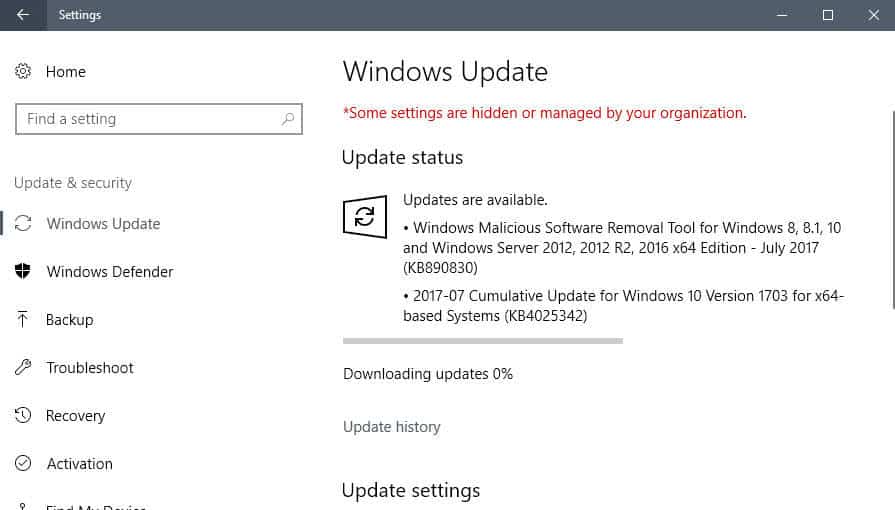
How to download and install the July 2017 security updates

Windows PCs are configured by default to search for, download and install updates automatically. This is not a real-time action, and if time is of the essence, you may run a manual check for updates at any time.
- Tap on the Windows-key, type Windows Update, and hit the Enter-key.
- Depending on how Windows Update is configured, you either need to click on the "check for updates" button, or that happens automatically.
- Again, depending on the configuration, Windows may download and install these updates automatically when found, or on user request.
Direct update downloads
Windows 7 SP1 and Windows Server 2008 R2 SP
Windows 8.1 and Windows Server 2012 R2
Windows 10 and Windows Server 2016 (version 1703)
- kb4025342 -- Cumulative Update for Windows 10 Version 1703
Additional resources






















How do I set the registry key for LdapEnforceChannelBinding on a domain server?
Microsoft has it listed as a key- https://support.microsoft.com/en-us/help/4034879/how-to-add-the-ldapenforcechannelbinding-registry-entry and not as the name of the DWORD.
Path: HKEY_LOCAL_MACHINE/System/CurrentControlSet/Services/NTDS/Parameters
Key: LdapEnforceChannelBinding
DWORD value: 0
DWORD value: 1
DWORD value: 2
If keys and sub-keys are the “folders”, then the new registry hive path would be HKEY_LOCAL_MACHINE/System/CurrentControlSet/Services/NTDS/Parameters/LdapEnforceChannelBinding
If I then add a new DWORD value type, what do I name it?
Or
Are they calling the DWORD the key and I should name it LdapEnforceChannelBinding?
I have spent weeks trying to figure it out. The computer mostly works, but some things have been killed because of the failed downloads. My start button no longer works, my search bar doesn’t work. My printer doesn’t work and all downloads of printer software all fail in one way or another.
On Windows bbs, (windowsbbs.com) there were many having similar problems. I don’t know if the got it fixed or gave up. On that site there is a section called repair windows 10. That goes to a tutorial on how to fix it. In step 2, there is an all in one program that does most of the stuff you’ve tried, but also does a lot more, and it’s all in one free program. It does take a while to run but many claim to have had good luck with it. It didn’t work for me, but it did clean up other problems.
Lynn1102, I’m having the same issue with the KB4025339 and I still haven’t been able to resolve it. I’ve researched online for days and it seems like no one else has experienced the issue. If you find a resolution, please post it and I’ll do the same.
Kelvin
I did download the new update for 1607. It’s a big file, a bit over 1 gig. It downloaded fine and a message popped up asking if I wanted to install the update. I clicked yes and waited close to ten minutes. A message popped that said install complete, restart your computer. I hit restart and got the message about updating and don’t turn off you computer.
After about 10 minutes, it rebooted and got the “installing updates, don’t turn off you computer”. Eventually it got to a zero percent level and stayed for a minute or two, then gave message “cannot install update, undoing changes” Another ten minutes of that message, then another reboot and back to desktop. Checked the install list and nothing new there.
Back to square one.
Lynn
I noticed that there is an update for version 1607. I have been trying to update this for many weeks and all I get is failed installs of update. All of the fails are from kb4025339 and 4022715. They have downloaded dozens of times in the past few weeks but always fail. Sometime they will download 3 or 4 times a day. Next day they are gone.
Do you know if those links would help me at all. I’m about ready to wipe my drive, but I would lose lots of stuff I cant replace.
I have tried all the usual fixes but no help. Using Win10x64, 16 gig ram and lot of hd space, I have the manual installs but fail part way thru.
Lynn
Anybody experience issue with after installed updates on server 2012 and server gets error “online-cannot get role and feature data”. It happens to three of my machines already.
Nm, stupid McAfee access protection
Martin,
Forgive me for asking but am I to assume that the Cumulative security update for IE11 is now included in the Security Only Update for a given OS? In this particular case that would mean that KB4025333 for 8.1 includes the fixes detailed in the following link: https://support.microsoft.com/en-us/help/4025252/cumulative-security-update-for-internet-explorer-july-11-2017 (although that makes no mention of the Security only update package).
Also, are 8.1 users supposed to make the registry change recommended in https://support.microsoft.com/en-us/help/4025333/windows-8-update-kb4025333 ?
Thanks in advance.
Security updates for Internet Explorer are not included in the Security-only update package that Microsoft releases: https://blogs.technet.microsoft.com/windowsitpro/2017/01/13/simplified-servicing-for-windows-7-and-windows-8-1-the-latest-improvements/
It’s all very confusing. Thanks anyway.
hi, typo under first appearance of KB4025341
– And all security updates of KB402337 **should be KB4025337 **
Thanks, corrected :)
Hello All,
Today I had downloaded the offline wsusscn2.cab file from go.microsoft.com/fwlink/?LinkID=74689. See support.microsoft.com/en-us/kb/926464 for more details.
But when I check the properties of the cab file under the Digital Signature Tab its showing the date as 13 June, 2017. Just wanted to check if anyone else out there is seeing the same when they are downloading the cab file for month of July 2017.
And is this cab file valid or any new cab file will be released by the Microsoft in few hours from now.
Any reply and help on this is appreciated.
Same problem here with the wsusscn2.cab file from June instead of July.
Are their an update for Edge to disable JavaScript (no seriously) or install extension or whatever name for Edge?
Dynamic Update for 1703 (KB4034374):
http://download.windowsupdate.com/c/msdownload/update/software/crup/2017/07/windows10.0-kb4034374-x64_d3a152e9b04967413f9ece84aa87aea25de3a677.cab
http://download.windowsupdate.com/c/msdownload/update/software/crup/2017/07/windows10.0-kb4034374-x86_5176b3fd767266b0e9019417cc7d28dee6ac259b.cab
Dynamic Update for 1703 (KB4025342):
http://download.windowsupdate.com/c/msdownload/update/software/secu/2017/07/windows10.0-kb4025342-x64_d5d2a01364bb3ad0e12aa914922b233a8d499843.msu
http://download.windowsupdate.com/c/msdownload/update/software/secu/2017/07/windows10.0-kb4025342-x86_167badec6b6a9cd5af65d15e61f8fa6e2d23e704.msu
Cumulative Update for Windows 10 Version 1607 for x64-based Systems (KB4025339):
(changelog: http://sihmar.com/kb4025339-build-14393-1480-windows-10-changelog/
http://news.softpedia.com/news/microsoft-releases-windows-10-cumulative-updates-kb4025342-kb4025339-kb4025344-516924.shtml