Give your Windows Certificate Store a thorough scan for suspicious certs
RCC is a free program for Windows that scans the Windows Certificate Store when it is run highlighting potentially dangerous certificates.
Two major computer manufacturers -- Lenovo and Dell -- put millions of customer computers at risk by installing certificates that included their private key.
Certificates use public and private keys, with the public key available openly, and the private key available only to the company that owns the certificate.
Anyone with access to the private key may use it to compromise HTTPS connections on the system among other things.
Windows users have access to the system's Certificate Manager, and while it is theoretically possible to go through the lists of certificates regularly to make sure that only legitimate certs are installed, it is not really practicable unless one has a deeper understanding of which certificates are required and which are not.
To load it tap on the Windows-key, type certmgr.msc and hit enter.
One of the better options is to export the certificate list on first start, and then again at a later point in time to compare the data. This won't help obviously if the PC manufacturer adds certificates to the system directly.
This is done with a click on Action > Export list in the main menu bar.
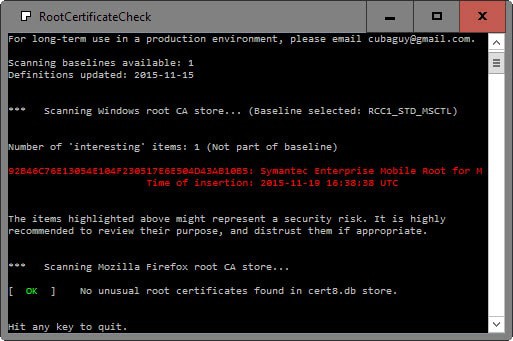
RCC, which stands for Root Certificate Check, is a free for home and educational use program for the Windows operating system that scans the Windows root CA store and the Mozilla Firefox root CA store on the system for suspicious entries.
It uses a baseline for that to which it compares the certificates to, and highlights interesting items after the scan.
These "interesting items" are not necessarily malicious or a security risk, but they can very well be one. It is necessary then to research the certificate on the Internet.
First thing you may want to do is open the Certificate Manager to list it there, as you find its full name and other information listed there which RCC does not list.
I suggest you search for the certificate name first, e.g. "Symantec Enterprise Mobile Root for Microsoft" and see what comes up. That may be enough to determine whether the cert is legitimate or not.
The "interesting" certificate in question that you see on the screenshot above seems to be used to sign Windows Phone apps, at least that's what a quick research on the Internet suggests.
Closing Words
Root Certificate Check enables you to scan the Windows Certificate Store and the Mozilla Firefox Certificate Store for certificates that need investigation.
Depending on the required level of security and thoroughness, it should not necessarily be your only checking option though.

























Hi, This is an awesome app–thank you! Question: Does it scan and compare ALL stores (“personal” and “computer”), and does it scan the “Third-party root cert authorities” and “Intermediate Certification Authorities”, as well as the “Trusted Root Certificates”…..or does it not matter? Thanks!
I found 2 “interesting” certificates… was from a program I uninstalled ages ago (Daemon tools). Ofcourse removed
An update to my earlier post
The change of the date of insertion of two certificates of my security software (a wellknown brand, one of the best on the market) was a result of a property update of third-party root certificate performed by Windows.
To recreate the situation I performed a backup restore and carefully monitored all the traffic. Auto update of third-party root list was performed (IPs verified no suspicious connections) and effective dates were changed on some cerificates, including the two of my security software.
So, even if that little tool considers those two certificates as interesting, I assume they are necessary for a security software to perform its functions properly. So it just coincided that after I checked the certificate store with that little tool, Windows performed an third party root certificate list update next morning. I just failed to monitor CAPI2 events in order to understand the cause for the change of the date.
Regards,
Art.
:)
Nice of you to update, guest earthling. Is demonstrated here why “interesting” rather than “suspicious” is the application’s terminology. Consequently, as mentioned in the article, it is most advised to investigate on those “interesting” certificates before choosing to disable/delete them. Your experience, first then updated, is relevant.
Thanks very much for this post, Martin. RCC detected a suspicious Dell certificate on a family member’s laptop. I researched it and ended up uninstalling Dell System Detect and manually deleting the DSDTestProvider certificate. (Belarc Advisor returns the computer’s “service tag” necessary for keeping drivers and utilities up to date, so Dell System Detect isn’t necessary anyway.) I was aware of the Superfish-like vulnerability on the most recent batch of Dell laptops, but I wouldn’t have thought to check this old one if I hadn’t seen your article.
Thank you for recommending the app.
I’ve downloaded and checked the installed certificates.
First, I visited the site and tried to download the RCC.exe. I was prevented from downloading it by a security software that is installed on the computer. That particular security solution has an antimalware filter and it scans network traffic. The filter was on and it told me that the download page is blocked by the antimalware filter. That really surprized me, but I wasn’t going to blindly trust the warning. So I visited the site from differently configured system (different OS & security solution). No warning, no malware alert. The executable was clean as I had no doubt about that.
I ran the RCC.exe on the sytem with the security software installed which had tried to prevent me from downloading the app. The security software didn’t stop it from running, I didn’t receive any virus alert from it upon accessing the RCC.exe. Moreover, I manually checiked it. Again, no warnings.
So when RCC.exe yesterday scanned the certificates it found 2 (two) certificates that it considered suspicious. Both certificates were installed by the very security solution that was preventing me to download the app. The time of insertion of those certificates reported by the app was the day the software installed.
I have to say that I had already known that the software that I have installed in order to monitor network traffic actually preforms a kind of MITM attack and, if an SSL scan is ON it presents to sites I visit a ‘fake’ certificate. I ran the RCC.exe today and to my surprise I found out that the date of insertion of those two certificates has changed! It now reports yesterday as the day of insertion for those two certificates! That is really confusing.
Translated from French, “God, protect me from my friends, as for my enemies I’ll handle them myself”
Your experience, guest earthling, demonstrates this, and your “security software” whatever it is, seems to be an odd friend. It wouldn’t be the first time.
Of course remains the fact that your security software, the one anyway having blocked access to RCC’s home/download page, may be otherwise viable but over zealous and/or bugged on that particular address. No idea. We all know that facts are not always in a bad/good binary scheme, can be far more complex, and that’s where it becomes complicated.
@ A different Martin,
Je le savais (I knew it) !
This is both off-topic (sorry & thanks, Martin) and most interesting. “Gods” became “God” hence “Lord” but the idea of calling upon the heavens for protection against our friends (when we can manage our enemies) remained throughout the ages, Voltaire refreshed it and Mesrine (the criminal) would refer to it as well. A strong and persistent idea that of treason.
You learn every day, even on topics far from a computing blog :)
Lord, help me be a faithful friend!
@ Tom Hawack:
Good catch, Tom. I saw the attribution ages ago and didn’t vet my source. It turns out it probably dates back to well before Voltaire:
« Mon Dieu, gardez-moi de mes amis ! Quant à mes ennemis, je m’en charge ! »
Dans l’Encyclopédie des citations de Dupré (1959), est indiquée comme faisant partie de l’Anthologie Palatine d’Eustathe (12e siècle), avec cette note en bas de page : « On attribue souvent ce mot à Voltaire. Il est bien plus ancien. Selon Stobée, il aurait été prononcé par un roi de Macédoine, Antigone II, mort en 221 av. J.-C. »
Mais certains auteurs indiquent que la traduction utilisée dans le Dupré est mauvaise. C’est en fait : « Que les dieux s’occupent des amis (philoi), je me charge des ennemis. »
— « Mon Dieu, gardez-moi de mes amis. Quant à mes ennemis, je m’en charge ! » – Le blog de JACQUES BERTHOMEAU
Oh, well. I was only off by one author, one country, one language, and two millennia. I really should have written Antigone II of Macedonia knew from software…
@A different Martin, so was it Voltaire who declared “Lord, protect me from my friends; I can take care of my enemies.”? (I’ve googled a bit!) — My reference, far less academic, was from a book by or concerning Jacques Mesrine, a famous french criminal…
Thanks :)
@ guest earthling:
Voltaire knew from software. ;-)
@ Tom Hawack
Thanks for the phrase. :) I like it.
I think I’ll give the security solution i’ve installed on that comp a little bit more close look and after a while I’ll report my findings to their support team. Options are wide: from a glitch, misconfiguration, to a compromise of the product.
I have these 3 , any thoughts
Number of ‘interesting’ items: 3 (Not part of baseline RCC1_STD_MS
495847A93187CFB8C71F840CB7B41497AD95C64F: VeriSign Class 3 Code Si Time of insertion: 07/10/2015 05:14:12 UTC
C9AB582BF062FF9D702C7666CA2B9AC49552628B: Symantec Root 2005 CA Time of insertion: 07/10/2015 05:22:00 UTC
74CDD21C2F1D104F8940DFFE7E6F035756E2F5D0: Symantec Root CA Time of insertion: 07/10/2015 05:22:00 UTC
The Symantec one is interesting because it also turned up for me in a near-clean W10 TH2 image. I do have a few things installed, so it could have been one of those, I suppose. More likely though is that it comes with Windows, which is strange, since what does Symantec have to do with Windows Mobile? I would think MS would be able to handle any certs of that nature itself. Nothing that informative comes up on searches about it. I don’t think it’s a problem, just odd.
https://wikileaks.org/hackingteam/emails/emailid/507281
https://wikileaks.org/hackingteam/emails/emailid/104655
The Symantec certificate is used for signing malware files, to bypass antivirus checks: http://git.io/vBB0E
thanks for this
around this same time of this Dell Certificate news
my Zemana Antimalware Beta i’m testing gets a update and now it is finding a Certificate from HP (my pc is HP)
the Certificate is called HPSelfSignedCA
and after reading this story i found this Certificate using (certmgr.msc)
so after all this news i’m thinking this could be more than just Dell
so now a ? if someone would be kind and tell me
should i delete this Certificate ?
thanks so much
Now that even system root certificates can no longer be trusted blindly (Lenovo, Dell, next?) this neat little application comes in at the right time and at the right place! Now, once the “interesting” certificate(s) are pointed out, the next (big) step is of course to investigate in which way “interesting” must be understood. Some beautiful (and smart of course) ladies are “interesting” as well as a psychopath may be for a novelist or a psychiatrist! Let’s not banish a beautiful (and smart maybe) certificate : ask the Web first if the lady is a psychopath or not. Lol :)
Thanks again Martin for reviewing one of those apps which are “interesting” (and healthy!) and deserve to be brought to a wider audience.
The whole CA-system is broken anyway.
Just look at the situation between Google and Symantec.
Or DigiNotar.
Are you absolutely sure of that? I have no reason not to take your word for it, especially that I’m totally illiterate in computing, even more when it comes to the depths of the networks, those I perceive as the infinity of our universe!
Frankly, what is the actual situation of Certificate Authorities? Is it really as bad as Joker mentions it?
I’d like to know, like all of us, the boundaries of trust!! (they move every day!)