Dell does a Lenovo: ships laptops with rogue root CA
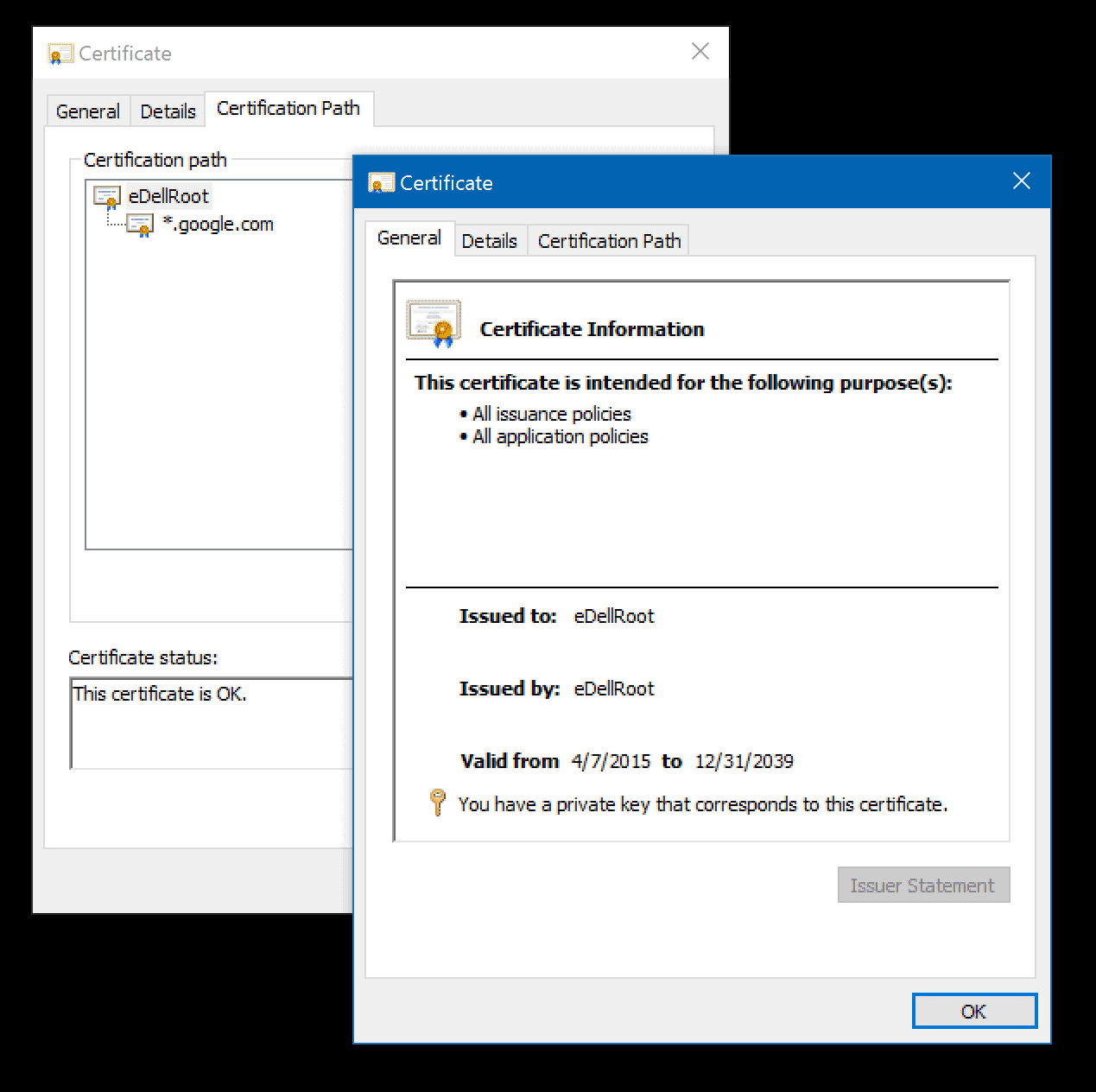
Some Dell laptops ship with a self-signed root certificate eDellRoot and private key that attackers can exploit. The issue, first reported on Reddit, has resemblances to the Lenovo incident earlier this year when the company shipped some of its laptops with a pre-installed third-party root certificate that could be exploited in a similar fashion.
The self-signed root certificate and private key appear to be identical on all affected Dell machines.
Update: Dell published an official response on the official Dell website. stating that the purpose of the certificate was "not malware or adware", but to "provide system service tag to Dell online support" and here specifically to allow Dell to "quickly identify the computer model".
The company has posted instructions on how to remove the certificate from Dell systems. End
Update 2: A second certificate vulnerability similar to the first has been discovered. The certificate DSDTestProvider is installed by Dell System Detect and includes the private key as well making systems running with it vulnerable as well to attacks. End
The preinstalled root certificate is accepted by browsers who use the system's certificate store, and that is Chrome and Internet Explorer on Windows for instance. Mozilla Firefox on the other hand is not affected by this as it uses its own certificate store.
The issue is severe, as it enables attackers to sign fake certificates for use on websites, and users would not notice this unless they pay attention to the certificate chain.

The certificate, which is installed on laptops by default, is installed by the software Dell Foundation Services which, according to the description on Dell's website, "provides foundational services facilitating customer serviceability, messaging and support functions".
The private key is not exportable by default but there are tools that can export it. The key has been posted in the meantime on Reddit.
It is unclear why Dell added the certificate in this way to some of its machines. It seems unlikely that spying is the reason for this, considering that the company would not include the private key if this would be the case.
It is surprising however that another manufacturer of Windows PCs and devices would make the same mistake that Lenovo did earlier that year considering that the company should have paid close attention to the fallout afterwards.
Test your laptop
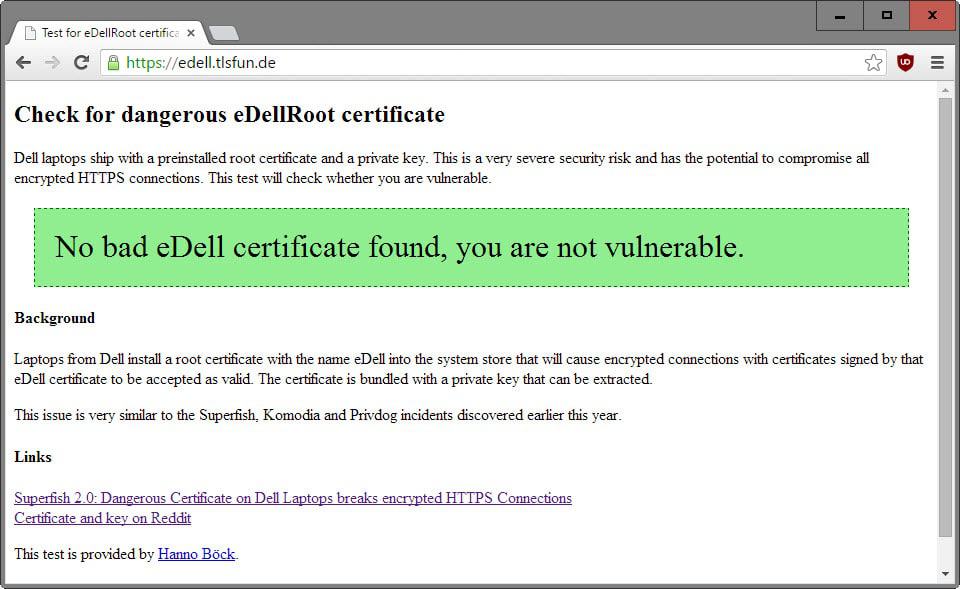
Hanno Böck created a web test to find out if the bad eDell certificate is installed on the system. Simply connect to the test website and you will receive information whether your system is vulnerable or not.
Remove the certificate
If the root certificate is installed on your laptop, you may want to remove it immediately to block any attacks from being carried out successfully against your system.
Windows users need to do the following to remove the certificate:
- Tap on the Windows-key.
- Type certmgr.msc and hit enter.
- Accept the UAC prompt if it is shown.
- Switch to Trusted Root Certification Authorities > Certificates.
- Locate the eDellRoot certificate in the list.
- Right-click the certificate and select Delete.

















Concerns this article as it concerns all system certificates : an interesting application I’ve discovered called RCC which aims at checking your system’s trusted root certificate store :
Source : http://www.wilderssecurity.com/threads/rcc-check-your-systems-trusted-root-certificate-store.373819/
Application’s home & download page : http://trax.x10.mx/apps.html
Application’s latest beta download page : http://trax.x10.mx/beta/
I’ve ran it and discovered one “interesting” certificate. “Interesting” is the application’s terminology to indicate possibly suspicions certificates as the idea is to search for information before removing it if applicable. RCC does not provide any certificate removal procedure, it only scans, analyses and informs.
SSL Cert Store Viewer v2.5
http://securityxploded.com/getsoftware_direct.php?id=7755
@Martin, just an info to simplify the steps. Just right click in certmgr.msc – right click on ‘Certicificates current users’ – ‘Search certificates’ – SHA1 and type in the certificate hash.
Inspiron 15 7000 Series Laptop infected too with the government backdoor.
Not only that. It even comes installed on the new Alienware Laptops. :shock:
I uninstalled every dell product and then certificate. It has not come back.
This issue also affects Dell desktops. I found the certificate on my XPS 8900. I uninstalled Dell Foundation Services, deleted the certificate, then rebooted to make sure it didn’t come back.
Revoking rather than deleting the certificate should prevent it from being made available again at reboot.
Open a CMD prompt as Admin.
certutil -v -revoke “6b c5 7b 95 18 93 aa 97 4b 62 4a c0 88 fc 3b b6” 1
The “6b c5 7b 95 18 93 aa 97 4b 62 4a c0 88 fc 3b b6” is the eDellRoot certificate serial number, the 1 indicates a compromised key as the reason for revocation.
In the Ars Technica article’s comments .. someone said the cert comes back on the next reboot
If so perhaps disabling/uninstalling the Dell Foundation Services, though I ignore what they are, if they run as a service, if any uninstall procedure is available, what would be the impact on the computer. I just hope the culprit is not in the system disk’s boot sector.
I am stunned with this repetition of Lenovo’s root certificate odyssey; I would be even more should the true story be that of an attack of the company at the manufacturing stage, involving Dell as the certificate issuer to prove its implication. We’ve already seen in the past similar attacks via viruses distributed on a famous hard disk manufacturer…
Who can you trust? “Paranoia, the true story” soon in your bookstores …
ok, another company goes on my shit list….once bitten…done. too many others out there not doing this to even give them a second chance.