Lenovo PCs ship with preinstalled adware and root certificate
We all know that computer manufacturers make much of their revenue from device sales with software and service deals.
They integrate trial programs on user systems and may also cooperate with search engines to make a particular search engine the default on a system and with other companies to place shortcuts to their sites on the desktop.
The tech community calls this crapware and it is a fitting name as most users don't need or want these types of offers on their systems.
That's one of the reasons why programs like Decrapifier and services to remove these offers are popular. Sometimes, manufacturers are offering services to remove these products from systems for a price.
Lenovo confirmed recently that it shipped some (it is currently unclear which models are affected) its consumer devices with Superfish, a known adware. This particular version of Superfish analyzes images that are displayed on the web, looks up matching offers in a database to display these offers to the user.
According to a Lenovo rep on the official company forum, the system is not profiling customers or recording user information.
Superfish technology is purely based on contextual/image and not behavioral. It does not profile nor monitor user behavior. It does not record user information. It does not know who the user is. Users are not tracked nor re-targeted. Every session is independent. When using Superfish for the first time, the user is presented the Terms of User and Privacy Policy, and has option not to accept these terms, i.e., Superfish is then disabled.
If that was not bad enough, the installation of Superfish on Lenovo devices also installs a root certificate to the Windows certificate store which makes all https connections vulnerable to man in the middle attacks as it can be used to intercept https traffic to any website.
A user connecting to secure websites may notice that the certificate is signed by Superfish regardless of site visited.
The certificate, on top of all that, shares a private key amongst all installations and uninstallation of Superfish won't remove the certificate with it.
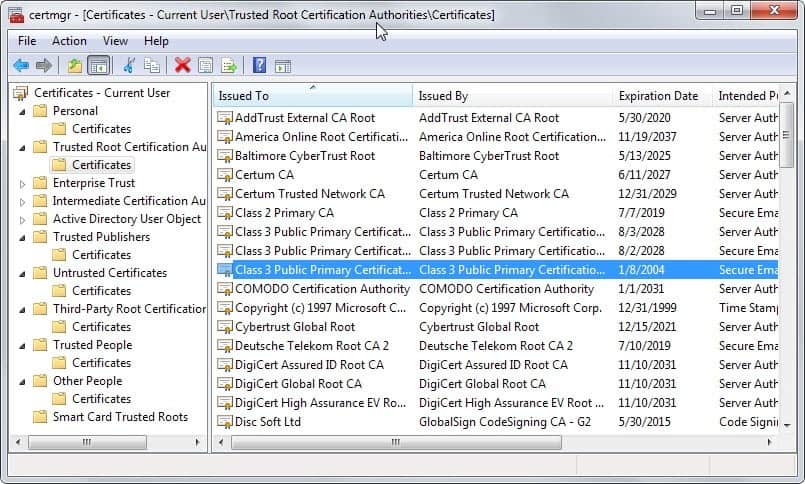
Side Tip: Checking the Certificate Manager

If you are running a Lenovo device you may want to check if the certificate is installed on the device and remove it if it is.
- Tap on the Windows-key to bring up the start menu or start screen.
- Type certmgr.msc and hit enter. This opens the Certificate Manager.
- Use the folder structure on the left to navigate to Trusted Root Certification Authorities -> Certificates.
- Check if Superfish Inc. is listed among the certificates.
- If it is, right-click the certificate and select Delete from the context menu to remove it.
Update: As Rodsmine mentioned in the comments, you need to use the Microsoft Management Console to check for Superfish.
- Tap on the Windows-key, type mmc.exe and hit enter.
- Go to File -> Add/Remove Snap-in
- Pick Certificates, click Add
- Pick Computer Account, click Next
- Pick Local Computer, click Finish
- Click OK
- Look under Trusted Root Certification Authorities -> Certificates
- Find the one issued to Superfish and delete it.
Here are the instructions that Lenovo posted on its support website to remove Superfish.
Closing Words
It is bad enough when PC manufacturers add all kinds of crapware on a PC to make money as these programs tend to slow down the PC quite a bit as many of them come installed on it and may run on system start as well.
It takes time and effort to remove those. What Lenovo did however is a whole new level. Not only did it install Superfish on systems with injects advertisement when users browse the Internet, that freaking thing did install a root certificate on the system as well sharing its private key which makes your system vulnerable to man in the middle attacks.
I don't understand how a company, or its executives, can think for a moment that this is good business practice. Even if Lenovo did not know about the certificate, it should considering that it added the software to its systems and hopefully tested this before it went to production, it is bad enough but with the certificate, it could severely damage the companies reputation for years to come.
Coincidentally, I purchased a Lenovo laptop back in 2014 but replaced its hard drive with a faster one and installed a system from scratch on it so that I never had to experience any adware (or worse) issues while using it.
Update: Lenovo released a statement on Superfish today. The main takeaway from the statement is that the company stopped the preloading of Superfish in January, that it won't preload the software in the future, and that the system has been disabled server-side since January.

















A small point, but the screen shot of certificates would be more helpful it it showed the Superfish certificate. I fear some people will delete the one highlighted in the screen shot!
For whom it may concern Lenovo has released a SuperFish Removal Tool 1.0.2.0 available at this time at :
http://www.majorgeeks.com/files/details/superfish_removal_tool.html
On Lenovo’s page the Removal Tool is mentioned as about to be relesed …
Lenovo PCs ship with man-in-the-middle adware that breaks HTTPS connections [Updated]
http://arstechnica.com/security/2015/02/lenovo-pcs-ship-with-man-in-the-middle-adware-that-breaks-https-connections/
Absolutely astonishing. The adware that Lenovo installed was bad enough but — of all the other bad things that could have been installed on top of that — they installed one of the worst possible: a root certificate!? Amazing. I don’t care what Lenovo has said or promised since this god-awful practice was discovered. I will never trust Lenovo ever again nor will I ever buy another computer — or anything else — from them.
Lenovo announced they will uninstall Superfish from PCs.
Actually, http://www.zdnet.com/article/how-to-remove-superfish-adware-from-your-laptop/ (How to Remove Superfish) says you procedure is wrong, Martin:
You can’t just run CertMgr.msc directly because that shows only the User Account, not the Computer Account certificate store. The bad Superfish certificate lives at the Computer Account level.
Run the Microsoft Management Console, mmc.exe (you need an administrator’s credentials to do this), and do the following:
1. Go to File -> Add/Remove Snap-in
2. Pick Certificates, click Add
3. Pick Computer Account, click Next
4. Pick Local Computer, click Finish
5. Click OK
6. Look under Trusted Root Certification Authorities -> Certificates
7. Find the one issued to Superfish and delete it.
My Computer Account/Local Computer store had several certificates not in the User Account store (Avast’s info is also in the Computer Account/Local Computer store).
Thanks I have added the information to the article. It may/will still show up under the certificate manager though as confirmed by this screenshot: https://twitter.com/fugueish/status/568252885839912960/photo/1
So, they “stopped in January” …what? did they get wind of people finding out about what they’d been doing and decided that trying to hide their heads in the sand was the best response?
“All your base are belong to us.” …well, that *used to be* a joke line–don’t know about now.
LENOVO STATEMENT ON SUPERFISH -> http://tinyurl.com/ox49xls
In fact their aim was to help their customers the best they could but since no one feels helped the company will reverse gear.
See how people are, you try to help them by delivering a Superfish crafted to help them find what they need and all they do is complain … life is tough.
Lenovo also make Medion computers. Are they infected?
http://www.borncity.com/blog/2015/02/19/superfish-adware-auf-lenovo-computer-vorinstalliert/
I should also add that at least one of the comments on the forum at HTG recommends Martin’s article for his detailed instructions on how to locate and remove the certificate.
I really appreciate the hard work you put in to writing these articles and keeping your site updated and relevant on a daily basis.
+1
I posted a link to this article over at How-To-Geek and Lowell Heddings replied with a link to an article at ars technica which also covers this issue in deep and scary detail:
“Lenovo PCs ship with man-in-the-middle adware that breaks HTTPS connections – Superfish may make it trivial for attackers to spoof any HTTPS website.”
http://arstechnica.com/security/2015/02/lenovo-pcs-ship-with-man-in-the-middle-adware-that-breaks-https-connections/
*sigh*. Unfortunately we may get to know about these things after being fooled. Seriously, is there any decent option for us customers wanting windows laptops besides buying microsoft signature?
Lets not forget uncle sam wanting to know all your details too.
Everyone has their finger in the pie these days its almost impossible to escape any aspect of this sort of behaviour.
Pretty much every time I read news articles these days its about some sort of cloak and dagger crap, just recently I read about some sort of shadow group which has been funneling data since 1996 and whats worse is security companies have been paid or coerced into keeping it a secret and overlooking it all. (One recent example: http://mashable.com/2015/02/17/equation-group-cyber-spying-program/)
The scary part is I doubt anything will result from this… a tiny backlash at best and all will go on as usual, people have absolutely no backbone these days and are too willing to comply regardless of what is at stake. I am not exempt from this either. at some point we all just magically became accepting of such behaviour and have done little to stop it.
It seems like we have more and more black hats than white hats these days. No longer are the black hats rogue groups romantisised by the public as a mischievous young person in their little garage working away their aggression… no! they are faceless villains which are part of a sophisticated group more than likely tightly affiliated with those in power out to collect your data and control every aspect of it.
Its a sick sad world.
Civil disobedience is needed on a large scale in times like this as its clear our rights are being violated on a mass scale.
Thanks for bringing this to my attention Martin.
I have a Lenovo laptop and I am very concerned about these revelations. I’m going to look into this and if I have to do a clean install then that’s what I’ll do. I’ve already checked for the Superfish root certificate but didn’t find it. Then again, I recently did a Full Reset of my Windows 8.1 via Charms->Settings (i.e. not via Lenovo OneKey) and that may be the reason I don’t see the rogue certificate.
I absolutely detest what Lenovo has done. I don’t care about all their fancy explanations. You are right – Lenovo doesn’t understand what they have gotten into. I will never buy another Lenovo product and I’ll make sure I tell all my family and friends about this issue.
I confirmed by Microsoft Store Chat today that Lenovo Signature products purchased through the Microsoft Store do not contain Superfish. FWIW…. I don’t work for Microsoft and did purchase a laptop through the Microsoft Store a few years ago, and am pleased.
http://www.microsoftstore.com/store?SiteID=msusa&Locale=en_US&Action=ContentTheme&pbPage=MicrosoftSignature&ThemeID=33363200
yes, at a christmas party, i was talking to a smart gal about computers… she said she just bought a lenovo. i answered “oh, a chinese computer” …she got the strangest look on her face.
“I don’t understand how a company, or its executives, can think for a moment that this is good business practice.” What country are these computers manufactured in? “People’s” Republic of China? A country ruled by the communist party? This is the same country accused by numerous countries of government sponsored computer hacking? This is the same country that have had their IT equipment banned or restricted from being used by numerous governments. Theft of trade secrets, copyright infringement and cloning (Range Rover Evoque, iPhone just two examples) has been a huge part of China’s business model for years. Whats a little adware? I for one decided a couple years ago to avoid as much as I possibly can any purchases of computers or smartphones from the People’s Republic. It surprises me that not more people are concerned where their computers (including smartphones) come from!
The point I was trying to make and failed to do so can be summarized in one word. TRUST. Everything that they (Chinese government and their high-tech manufacturers) can do to make me hesitant in giving them that trust they have done so. Repeatedly. I keep thinking of a scenario where a high-tech manufacturer is visited by a representative of their government and is grabbed by the throat and told “This is what I want you to do” and I can’t help but wonder what the outcome of that conversation will be. LMAO
This whole situation is unacceptable, that’s for sure. I lost my faith in Lenovo as well… as well as in almost every other company over the years, Sony being the sour cherry on the top of this rotten cake. Spy agencies deserve their own category though.
If you are from USA you should start wondering what in the long term could harm statistical John Smith more: Chinese government and companies who might spy on you, but know that due to it’s obviousness they will be caught every time so they have to play dumb and incompetent? (It has to be obvious like in this case of Lenovo because the cost would be too high for them if it was found way deeper in the system, and it WOULD be found at one point) Or maybe security agencies who implement backdoors on genetic level due to “patriotic and national security concerns”, not caring about the price, so that whatever they find or fabricate can be used against you in the future in case you are a threat to the “security”*? (*Whatever they decide is worth “securing” at that moment). The fact that the leaks of them spying/implementing vulnerabilities goes unpunished legitimizes everyone else doing the same, because why the hell not?
Basically, it’s YOUR government or governent agencies – not some Russian, Chinese or North Korean – that has the power to crush you, lock you up, censor you, decide your laws for you. I don’t trust American IT or communication services any more than I do Chinese or any else.
Of course, that applies only to John Smiths. Recently it hit the news that some VIPs, politicians etc. were blackmailed to become spies of different countries. The truth is, they will get blackmailed to cooperate by whoever finds something on them, no matter if it’s their own country or not, agency or thieves. It depends what was found during the hack and how useful can that person be.
I can easily imagine that US manufacturers have been “grabbed by the throat” by US government agents. And — given the revelations about sophisticated NSA rootkits shoehorned into hard drive firmware for the last decade — I believe that “compromises” were reached which compromised user security. And I believe those practices continue. and user security will continue to be a pawn in clandestine US, British, Israeli, Chinese, and Russian cyber-warfare. But computers are hardware, so in the real world you have to work with some kind of hardware, from somewhere. It can be pre-loaded with backdoors, whether made in Bejing or Palo Alto.
Quite nasty. I have a Lenovo desktop, now several years old, but I wiped the hard drive and did a clean install right after buying it. It’s a dual-boot machine and runs Linux 99% of the time, but I’ll have a look through the root certificate list next time I boot to Windows.
Of course applications in Linux use root certificates as well. There are few tools to manage certs, and I have no experience with them — XCA and OpenCA are the two I know of.
Apart from not buying Lenovo hardware, is there any utility that scans these certificates and alerts you of ‘bad’ ones? Not everyone understands these certificates and machines are messed up quite often than we may think. How one can address that? Any suggestions?
I was thinking the same thing, Noel. When I looked at my Trusted Root Certification Authorities list, there were dozens in there that don’t seem to be of any use to me, from seemingly all over the world (Autoridad Certificadora Raiz de la Secretaria de Economia), and for products I don’t use (Comodo, TrendMicro).
Maybe that’s an article idea for you, Martin. How certificates get installed, what they are for, what to do if you don’t recognize the issuer, what will happen if you disable or delete a certificate that you may need, and what the “expiration dates” are (and why do they only display a day name & number, not a month and year)…
It isn’t the first time Lenovo does such things… Do you remember about the enabled Computrace “backdoor” that was present in Lenovo laptops (and other brands) and was discovered a year ago? (You can read more about this here: http://securelist.com/analysis/publications/58278/absolute-computrace-revisited/ ). If you have a Lenovo laptop, you may want to check for this, because changing the HD won’t be enought!
I’ll be surprised if anyone gets a Lenovo computer (or anything) in the future.
i agree with previous comments about not buying, but seriously, the majority of people wont know about this, and if they did they wouldnt know what adware is, and if they did, they wont care anyway.
See a backlash coming for Lenovo on this…
Agreed. This was foolish for Lenovo to do. I still believe their ThinkPad’s and ThinkCentre’s are superb computers. This crap is not preinstalled on the Think products based on my setting them up for many customers over the years. HP and Dell business machines are fine also.
I certainly will never purchase any hardware from Lenovo nor recommend them to anyone else. How do you ever trust a company proven to be untrustworthy?
I agree as well, of course! Pitiful business practice indeed. A company cannot be unaware of the fact that such a decision as that of Lenovo will be brought to light, especially nowadays, without a very strong financial advantage which it believes will compensate commercial issues should they arise. No morality in business is one thing but to the extent of stupidity is another. Meanwhile how many users are and will be using a system infected at the root (almost) by the device’s manufacturer itself? Such practices should be sentenced, and I truly hope LENOVO’s will face charges.
Agree. I don’t think Lenovo realizes yet how bad this is.
Lenovo was originally
an IBM product.
It is (was?) maybe the best portable PC
for many years.
Then,
(if I remember correctly),
it was sold by IBM
to a company in mainland China (PRC).
This incident is really deplorable
and a wake-up call to business users…
Too bad,
my next portable will NOT be a “lenovo”, obviously…
Since the software they used supplied by Komodia specifically brags about its ability to do a man in the middle on SSL, the absolutely knew what they were doing.
Since Lenovo did not install this garbage on their business PCs, I take that as they knew all along with they were doing. No doubt some customers have now lost faith in Lenovo’s corporate professionalism. Lenovo may be the #1 PC company in the world, but that may not last. Look at what happened to HP and Dell when they made strategic errors a few years back. Both lost over 20% of their market share while Lenovo kept growing. .