Microsoft, LastPass and others post solutions to handle Superfish
An adware called Superfish is making big waves currently on the Internet after news spread that PC manufacturer Lenovo shipped some -- it is still not clear which devices are affected -- consumer PC models with the software preinstalled.
The core purpose of Superfish is to display advertisement to users based on what they are looking at in web browsers. It injects advertisement on web pages that users visit in browsers.
While that is bad enough, it is only part of the reason why Superfish is universally condemned currently. What is even more problematic than that is that the program installs a root certificate on the system. This is done by the software to gain access to https traffic as well, something which it would not otherwise be capable of.
The certificate was cracked recently which means that attackers can exploit it for man in the middle attacks.
Lenovo posted Superfish removal instructions yesterday but it is not the only company that sprang into action after the news broke.
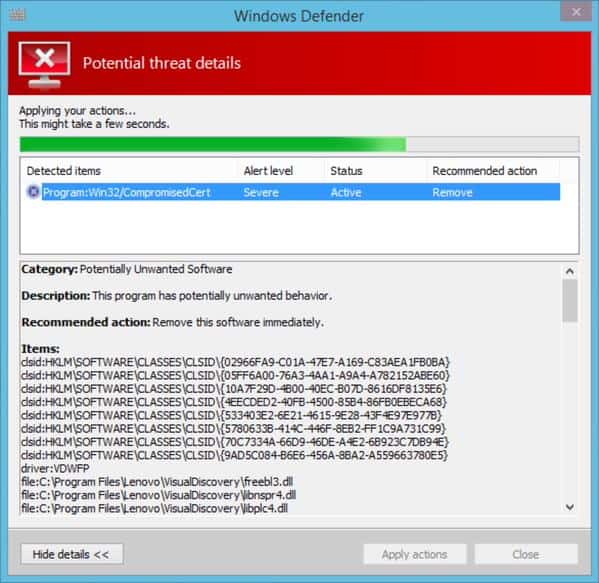
Microsoft for instance updated Windows Defender, the built-in Windows security program to detect the Superfish certificate and VisualDiscovery program so that affected users can remove it from their systems using it.
Filippo Valsorda posted a screenshot of Windows Defender detecting Superfish on Twitter today.
Microsoft has not confirmed the integration yet but an update to the program's definition file was released today by the company.
You can check for the update manually in Windows Defender or download the most recent definition files from this page on the Microsoft website.
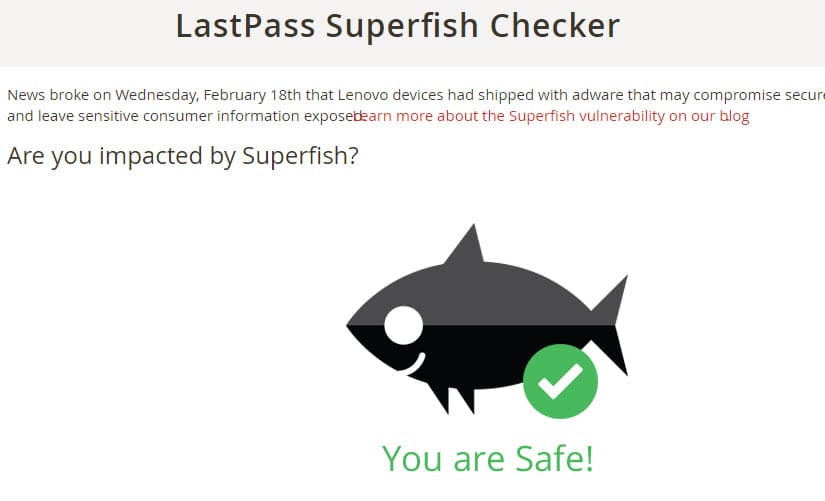
LastPass, makers of the popular password manager of the same name, have published Superfish Checker, a page on their website which detects whether Superfish is installed on the computer you are accessing the page with.
Besides checking whether you are affected or not by it, it lists removal instructions for the program and certificate.
The company is not the only one that published an online check tool. You can also use the Superfish CA test instead which tells you if the certificate is installed on your system. It recommends to perform the check with all browsers installed on the system.
If you are affected, you may also want to check out the removal instructions on the EFF website which offers a detailed guide to remove the Superfish software and certificate.
The whole Superfish incident turned quickly into a PR disaster for Lenovo. While the issue was first reported on tech sites (well actually first on the Lenovo forum some time ago) it was quickly picked up by newspapers worldwide.
If you search for Superfish right now you find articles about it on Forbes, The Independent, The Wallstreet Journal, Der Spiegel, the BBC and dozens if not hundreds more.
Update: Lenovo has published a list of affected products (stating that they may be affected):
- E-Series: E10-30
- Flex-Series:Flex2 14, Flex2 15, Flex2 14D, Flex2 15D, Flex2 14 (BTM), Flex2 15 (BTM), Flex 10
- G-Series: G410, G510, G40-70, G40-30, G40-45, G50-70, G50-30, G50-45
- M-Series: Miix2 – 8, Miix2 – 10, Miix2 – 11,
- S-Series: S310, S410, S415; S415 Touch, S20-30, S20-30 Touch, S40-70
- U-Series: U330P, U430P, U330Touch, U430Touch, U540Touch
- Y-Series:Â Y430P, Y40-70, Y50-70
- Yoga-Series: Yoga2-11BTM, Yoga2-11HSW, Yoga2-13, Yoga2Pro-13
- Z-Series: Z40-70, Z40-75, Z50-70, Z50-75


















Superfish Mozilla Firefox Hotfix:
https://addons.cdn.mozilla.net/user-media/addons/354399/mozilla_firefox_hotfix-20150225.01-fx.xpi
Superfish is not the first, nor expected to be the last of its kind. Lenovo used to install other browser hijackers such as Conduit Search into laptops. This was found in my brand-new Lenovo laptop a few years back.
Subsequently, Conduit Search evolved to become Lenovo Browser Guard, which come shipped in some Lenovo desktop & laptop PCs. Lenovo Browser Guard is Lenovo’s own brand of Conduit Search created in partnership with Conduit/ Perion.
As recently as 2014 Q4 (& despite multiple Lenovo user complaints), Lenovo continues to claim (read: bullshit) that Lenovo Browser Guard (aka Lenovo-branded Conduit) “is designed to provide an extra layer of protection and prevent 3rd party applications from changing the user settings without the user’s explicit consent” !!!
* Lenovo Browser Guard – Facts and Q&A (Aug/Sep 2014):
https://forums.lenovo.com/t5/Security-Malware-Knowledge-Base/Lenovo-Browser-Guard-Facts-and-Q-amp-A/ta-p/1722691
* Lenovo sold me a laptop pre-installed with malware (17 Sep 2014):
http://www.reddit.com/r/Lenovo/comments/2eqeja/lenovo_sold_me_a_laptop_preinstalled_with_malware
Lenovo computers are not the only ones that are infected. This website is full of crap https://filippo.io/Badfish/ It says Superfish is probably not intercepting my communications. I opened Chrome Dev Tools and clicked the Resources tab. Guess what I found in there…Superfish cookies. I don’t get them on every site but most of them. I haven’t found an effective way to get rid of them either. Every blogger has theories but no solutions. I’m using an Asus M51A desktop computer not Lenovo. I bet every computer is infected with them. :( So far Adblock and uBlock have kept me from seeing the ads.
I’m getting cloudfront cookies on your site but not Superfish.
Nice review of the Lenovo Affair‘s current development as well as toolkits for everyone to check if his/her Lenovo device has been struck or not by the computer manufacturer’s outstanding strive for quick and easy cash flow.
Heh. I just bought the top model Lenovo g40 today – I was aware of the Superfish flap, but it’s dang hard to find a 14 inch laptop (I don’t want to carry around anything bigger) with windows 8.1 and an optical drive these days. Also I was aware of some fixes being mentioned online. It will be interesting to see if my new laptop is free of Superfish, but if not there are remedies.
Hello Everyone!
Now I’m afraid to purchase the MOTO X smartphone. I understand that Lenovo bought said device that was originally manufactured by Motorola (then Google). Now I worry that any product made by Lenovo could be compromised (security-wise) by a type of implanted malware like Superfish. I hope I am wrong in my summation ’cause I really want to purchase the MOTO X (or one of its siblings)!
Don’t be affraid to do that. All computer brands are infected with it not just Lenovo. Open Chrome Dev Tools to the Resources Tab to see their cookies on most sites.
Lenovo was originally
an IBM product.
It is (was?) maybe the best portable PC
for many years.
Then,
(if I remember correctly),
it was sold by IBM
to a company in mainland China (PRC).
This incident is really deplorable
and a wake-up call to business users…
Too bad,
my next portable will NOT be a “lenovo”, obviously…
FYI: Lenovo manufactured IBM branded laptops before they bought the product line from IBM.
I consider the Superfish inclusion on some consumer grade laptops, not ThinkPads, a stupid move by Lenovo where they were paid for doing so. That never benefits consumers.