Scan your Windows computer for untrusted root certificates
Root certificates are one core building block of today's Internet. They are used to verify connections and a list of trusted certificates ships with operating systems such as Windows which makes them more trustworthy than certificates added to the operating system by third-parties.
For end users, it is nearly impossible to tell which certificates are legitimate and which are not. While it is possible to display them all in a list in the Microsoft Management Console, there is no telling which ship with Windows, which are added by third-parties and which of them are legit and which are not, at least not on first glance.
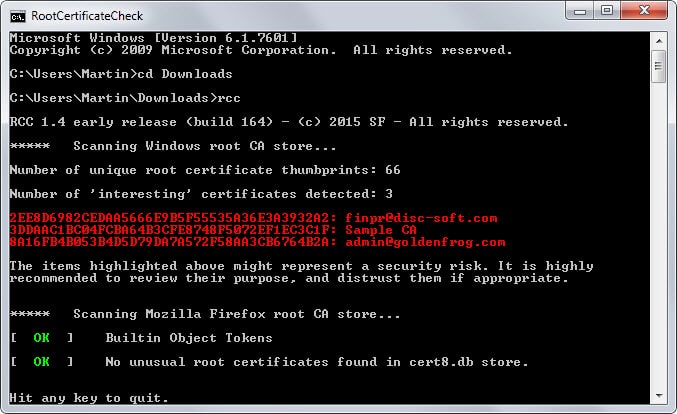
The free program RCC attempts to change that by scanning Windows and Firefox root certificate stores to display certificates that should be looked at more closely.
While the website of the author does not reveal how that is done, the most likely explanation is that it takes Microsoft's list of trusted root certificates into account at the very least and compare it to root certificates installed on the machine.
The program needs to be run from the command line:
- Download and extract it to a location on your system.
- Tap on the Windows-key, type cmd and hit enter.
- Navigate to the location of the extracted file on your system using the cd command, e.g. cd c:\users\martin\downloads
- Type rcc and hit enter.
The scan does not take long and the most interesting information are highlighted in red by the program. Interesting does not necessarily mean a rogue certificate though.
This means that you need to research them manually to find out more about them. While you could delete them right away, it might prevent services from running properly on your system if you do.
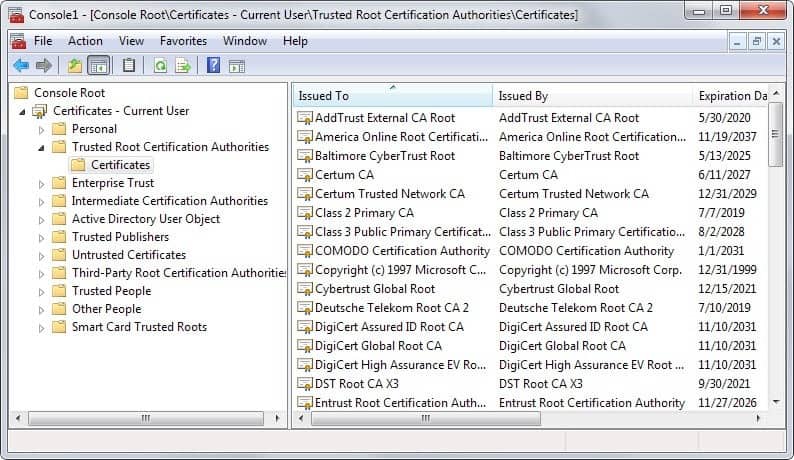
Find out more about a certificate
You need to use a different program to find out more about listed root certificates.
- Tap on the Windows-key, type mmc and hit enter.
- Select File > Add/Remove Snap-Ins from the menu bar at the top.
- Select Certificates, then user account and finish.
- Click ok.
- Expand the list of certificates and open trusted root certification authorities from the listing.
- Locate the certificates that the scanner listed in its interface.
The console may list additional information about it, for instance the company that issues it, its intended purpose or when it is expiring.
To remove a certificate from the list, select it and hit the delete key on the keyboard afterwards. Before you do that, you may want to search the Internet for information about a certificate.
You may be able to identify some right away, for instance if a company name is used. That way you can tell right away if the certificate is still required or not on your system. If you don't use the company's services or products anymore on it, it is likely that it is not needed anymore.
Verdict
RCC is a useful program. It is portable and scans a system's and Firefox's root certificates to highlight certificates that you should investigate more closely to make sure rogue certificates are not installed on the computer system.



























I have built a windows SSL Checker that lets users view CA Root certificates in a tree view with child ‘Intermediate’ certificates below them and the program uses a white list of certificate thumbprints but i am not quite sure if my list is correct so please give me a link if you know of a list.
The program lets users click on certificates to delete them and has a ‘Mark All Safe’ Button so it makes it easy to see if new certificates have been added behind your back.
What i do know is that my ISP is hijacking DNS lookups for Youtube.com and can server up SSL pages for Youtube.com and I would like to get to the bottom of how they are doing this and this is why i needed to clean out all my CA certificates which lead me to write the program in the first place.
One last thing is that Firefox on Android devices is now using DLNA to hack serial numbers from your “Smart TV’s” to be used as a type of super cookie so watchout for that one if you are using anything like the Tor network.
I use Firefox portable. Is there a way to check for portable certificate stores?
Always wonder how you find these little gems Martin.
Thank you.
I’d love to see a post about your sources.
The author contacted me directly this time.
Martin, thanks for the nice review! Keep up the good work.
@Tom, @Rik: please try the latest build (168), which should fix the “OS not supported” issue. Only Vista and below are truly not supported.
@John: the scan process itself does not require Internet access; however what you are seeing is the result of RCC checking the CRL for a critical Mozilla Firefox DLL. Servers contacted are simply the ones listed in the Firefox code signature certificate chain. Also PowerShell (part of a vanilla OS install since Windows 7) is currently required for the enumeration of the Windows certificate store. I will document this in a small FAQ on the website.
I hope to further improve both the software and the website, as time permits.
My firewall records this program starting powershell.exe and going out to a number of websites:
C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe, Outgoing TCP access allowed to: (ocsp.digicert.com;cs9.wac.edgecastcdn.net;crl3.digicert.com;cs9.wac.phicdn.net) 72.21.91.29:80
Presumably this is where it checks the certificates.
Blocking internet access results in the program just hanging after identifying what it calls ‘interesting certificates’. The last 4 lines shown in the first screen grab in this article never show up when access is blocked.
Not impressed with the lack of disclosure about where the program goes on the internet. Deleted.
I would prefer to use built in tools when possible.
Here is an article that might help:
https://www.nsa.gov/ia/_files/factsheets/adf-2012-1202_defending_against_compromised_certificates.pdf
Note: Does not work with Windows 10 (“OS noty supported”)
Windows 8.1 “OS not supported”
It crashes. Problem details:
Problem signature:
Problem Event Name: APPCRASH
Application Name: rcc.exe
Application Version: 1.2.2.1
Application Timestamp: 552238cb
Fault Module Name: rcc.exe
Fault Module Version: 1.2.2.1
Fault Module Timestamp: 552238cb
Exception Code: c0000005
Exception Offset: 00002e94
OS Version: 6.1.7601.2.1.0.768.3
I ran VirusTotal on the download link
1 hit: malicious site
Sophos and German outfit Clean MX classify the download (direct) link you’re saying as a “malicious site”, but the actual file (rcc.zip) is marked as containing malware by Qihoo 360.
As for reports of RCC not working in Win 8.1/10, the software is in an early release state as warned by its developer and it is prone to bugs.
It’s a nice idea, although I can’t help wondering how useful this is in reality (that’s a genuine question BTW, I’m not mocking it)?
If a piece of software has already gained admin privileges in order to install it’s own root certificate in the first place, that piece of software can already do whatever it wants on your computer, including capturing all your keystrokes and sending them to a remote server. Therefore, why would malicious software even go to the trouble of installing it’s own root cert in order to MITM you, unless the software is like SuperFish where it claims to have a ‘legitimate’ use?