Encrypt all data on your Android phone
One of the first things that I decided to do of after getting my new Samsung Galaxy Note 2 smartphone was to protect the data stored on the phone's memory space from unauthorized access. Phones by default are only protected by the PIN, which may protect the phone just fine if it is not turned on. If the phone is turned on though, an attacker can access all of the data stored on the phone without having to enter a single password or PIN first.
Setting a lock screen password is however just one of the steps that you should undertake to protect your phone from unauthorized access. While it may keep out people who got hold of your phone in first place, it may not protect the actual data on the phone's storage device. You need to encrypt the data on the phone to make sure that the data can't be dumped by a third party.
Encrypt your Android Phone
A few requirements have to be met before you can go ahead and encrypt the data on your phone:
- Your Android phone needs to support encryption. I'm not 100% about that but I think encryption was added in Android 3.0. You may alternatively want to check out third party encryption apps. Update: It was added earlier in Android 2.3.4.
- You need to set a lock screen password or pin.
- Your phone must be connected to a power source.
Setting a lock screen may be enough if you do not have overly sensitive data on the phone. Regular attackers won't get past the lock screen which leaves them with the option to reset the phone and all the custom data that was saved on it.
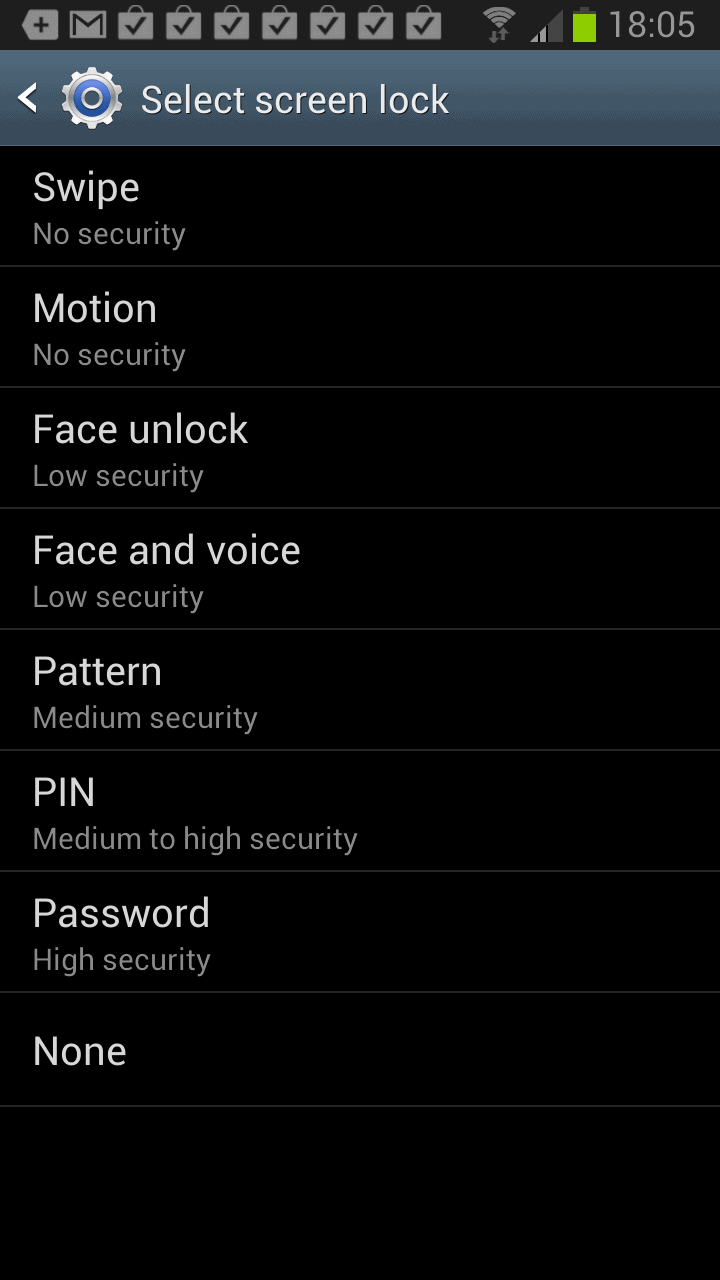
1. Setting the lock screen password
On the Samsung phone, you tap on the Settings button and select Lock screen >Â Screen Lock from the options page. Here you need to select how you want to protect the phone when it is locked. Available for selection are protection by pin, password, pattern or other methods. Select password protection here and make sure the password has at least six characters of which one is a number. I highly suggest to increase the number of characters to the maximum number of 16 characters to improve security.
Once you have set the password, you will be asked to enter it whenever you turn on the phone, or want to continue your work after a time of inactivity. This may be inconvenient but that is a small trade-off for better security.
2. Encrypting the Android phone
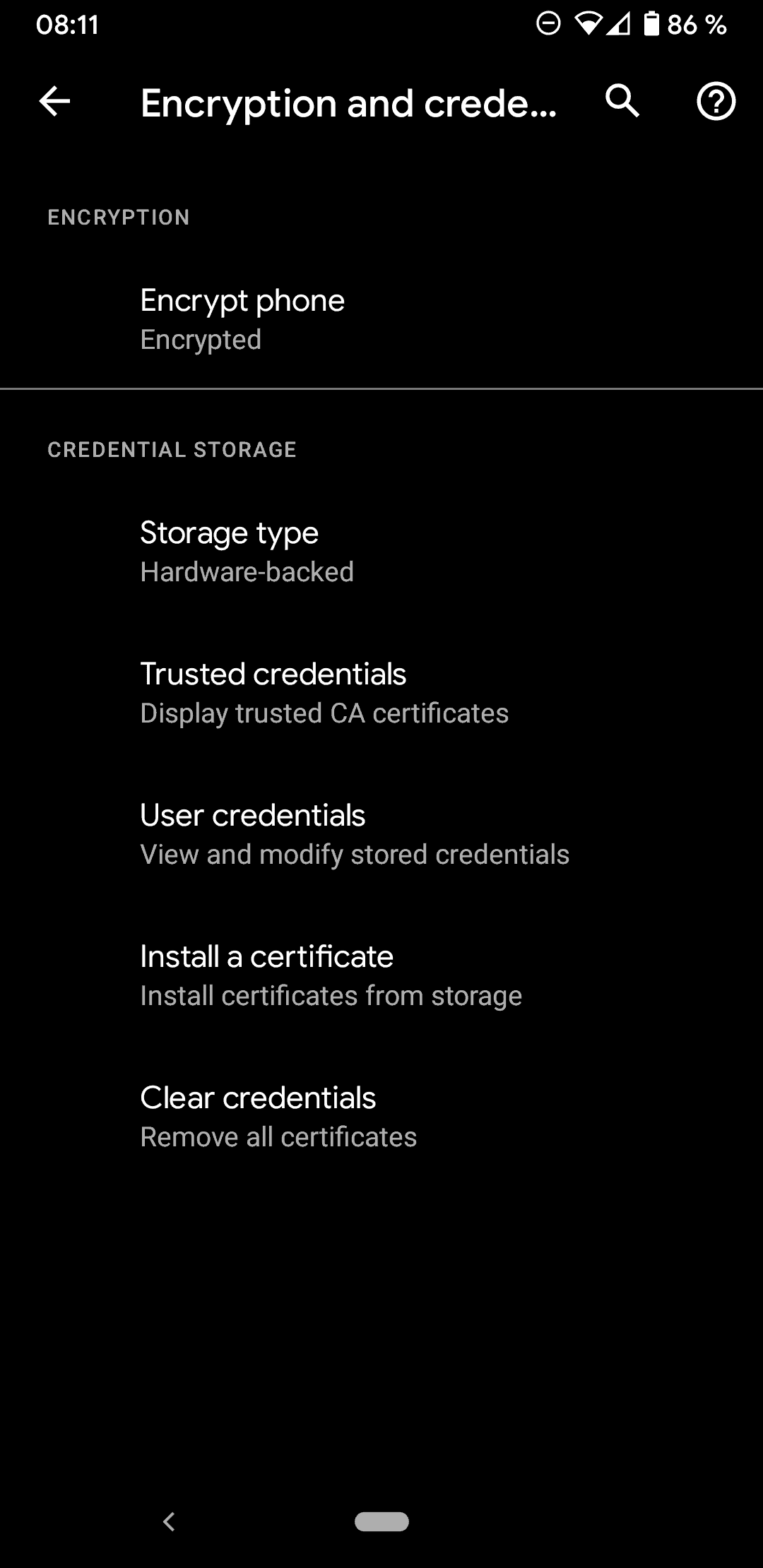
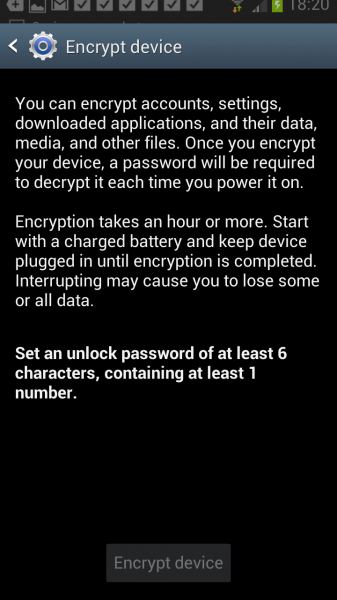
You need to plug in your phone and make sure that the battery is charged before you continue. The option to encrypt the phone is grayed out otherwise. A click on Security > Advanced > Encryption and credentials > Encrypt Phone under Settings opens the configuration menu where you can start the encryption process. Please note that it may take an hour or more to complete.
You can encrypt accounts, settings, downloaded applications, and their data, media, and other files. Once you encrypt your device, a password will be required to decrypt it each time you power it on.
Encryption takes an hour or more. Start with a charged battery and keep device plugged in until encryption is completed. Interrupting may cause you to lose some or all data.
Set an unlock password of at least 6 characters, containing at least 1 number.
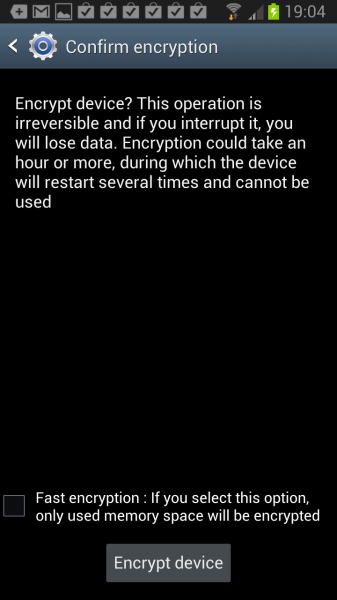
You are asked to enter the unlock password after tapping on the encrypt device button. The next screen offers information about the consequences, and an option to run a fast encryption instead of a full device encryption. A fast encryption will only encrypt the used memory space and not all the device space.
Encrypt device? This operation is irreversible and if you interrupt it, you will lose data. Encryption could take an hour or more, during which the device will restart several times and cannot be used.
Fast encryption: If you select this option, only used memory space will be encrypted.
You need to wait until the encryption completes before you can start using your phone again. Make sure it is connected to a power source throughout the whole process to avoid power failures and resulting data loss. If you want to be on the safe side, consider backing up your Android phone before you start the encryption of storage space. Samsung smartphone owners can use Samsung Kies for that. Make sure the backup is stored safely as well.
If you are using external SD cards, you may want to consider encrypting those cards. The option is available under Security as well.
Advertisement



















Encrypt account settings problems
Thanks
good lord this article did not say anything other than what the Samsung menus said.
I cannot encrypt my samsung galaxy s3….is there any other method for permanently deleting all the data from my phone??
help me!!!
How to remove encrypt password in my samsung core 2 galaxy SM-G355H mobile, Pls help me
curious george,
I don’t know exacts with Android, but the idea of encrypted storage means data is encrypted at rest, ie when written to disk. Data is NOT encrypted when in memory. So data generated by a chat will reside in memory for time and then it will be written to disk where it will be “safe”.
Does it encript all chats, as I think my chats are being tapped into I have video chat and external messaging apps. I think it’s being tapped through our wifi. When encrypted can they see data being made, they just can’t see content right?
I was accidentally encrypted my Samsung Galaxy Note 3.
But I am now cannot switch on my phone at all.
Every time I switch it on, it required to enter password and it immediately switch it off.
What is the problem here?
how can i remove the decrypt device or decrypt password of samsung S duos 2.?
Heu…Pensez à ceux qui comme moi ne savent pas parler anglais!
Une version en français serait la bienvenue…
Is that the only way to “turn off encryption” or is there another way?
Can someone tell here how to turn off the encryption without destroying data and I know my pin and its working too…… I saw some ppl asked same but surprisingly no answer but other answer is there !!!!!
As far as I know, the method to do so is the following:
1. Create a full backup of your phone.
2. Restore the phone to factory defaults.
3. Restore the backup you made previously.
I’ve encrypted my Samsung note 2 phone, both internal, and the SD card. Unfortunately, my password is not working when I try logging into the encryption box. Is there any way to reset encrypted password? I only have 3 more opportunities to get it right, after that all data will be lost, and the phone reset. The password I’m inputting is the same one I’ve always used, I’m totally bewildered. Any suggestions! Thank you
walker,
256bit encryption is more than enough. It is what you use to transmit days to and from your banks site.
I think you are thinking of key pair size which is 2048 standard now for TLS communication.
“So to brute-force a 128 bit cipher key you have to try most of the 2128 ~ 1038 different keys until you found the one that worked. So if you can check a trillion (10^12) keys per second it would take ~10^19 years before you’ve checked most of the keys. Note a 256-bit key would be 2^128 times harder to brute-force (take 10^57 years).”
http://security.stackexchange.com/questions/13624/how-safe-is-the-256-bit-encryption-used-in-bank-transactions
The Samsung encryption is seriously weak. 256bit. The gov. Can crack twice that, easily. Give me 2000+bit encryption. Then I’ll feel secure.
Thanks Verizon tech support could not tell me how to do this.
Hello
How can I deactive encryption???
I don’t want to enter pin code every time.
plz someone help me too
i have samsung galaxy s duos GX-S7562
i want to encrypt my phone
if i will do this, i can install some apps to SD card?
this is my big problem about installing applications
This whole article just kinda sucks and I must say you are a really lazy author. The second comment you got clearly stated that you got a detail wrong and it is possible on earlier android devices, but you never had the energy to go back and fix your fuckup. Also, your whole reason for wanting encryption is just wrong. “Phones by default are only protected by the PIN, which may protect the phone just fine if it is not turned on. If the phone is turned on though, an attacker can access all of the data stored on the phone without having to enter a single password or PIN first.”
1) Your phone isn’t protected by a PIN as a default, you have to set that up.
2) You can make the phone require the PIN in plenty of different ways… the most obvious being the builtin setting (at least in Android 4+) to require the pin after seconds of being locked.
I hate stumbling onto lazily written, poorly thought out articles like this in google searches… it wastes everyone’s time.
How do I turn that off?
I want to protect info on my phone, its a galaxy note 2. I have a question, it says “a password will be required to decrypt it each time you power it on”. I would like to remove lock screen after encryption, so it still requires password when started but not when it wakes up. Is it possible or “power it on” means you cant remove password lock screen ever again?
My question exactly. I figure if the phone is fully encrypted that the need for pin while running is less. I would configure the phone to “watch” for an sms to tell it to reboot if ever lost/stolen.
Its good they include encryption but it takes forever! They must be able to speed it up?
Hi
I encrypt my SD
after that
I restart my Galaxy note 2
Without the SD
Now When i open The SD
I Can’t open Any file Because all the file is Encrypt
pls help me!
Thanks
i have the “Encrypt device” button, but doesn’t do anything. Some one have the same problem?
Your phone needs to be charged and plugged in, did you do that?
I have an Galaxy S3 with Android 4.1.1 Jelly Bean, rooted.
What if I have some apps installed onto the SD card, and they’re set to start up at boot — if my card is encrypted, there’s going to be a delay between the time my phone powers on & when I enter my password to decrypt the card, so will that cause any problems?
Also, will encrypting my SD card mean I’ll have to decrypt it every time I turn the screen off & back on again (sleep/wake), or after a certain amount of time, or is it just when the phone is powered off/on?
Your Android device decrypts on the fly. There is no manual need to decrypt your program. The only bummer I found is that encryption apps gets totally confused by Android encryption.
If you find that your apps are behaving funny, just turn off the encryption feature and everything is back to normal. But as a precaution, you should ALWAYS copy your entire SD card to your harddrive as backup. You can just copy the contents back from your harddrive to any SD card, stick it in and it’s up and running. Android’s program stucture appears to be like DOS, you don’t need to worry about stupid registry keys pointing to fixed locations.
I do not use an SD card so can’t say for sure, but it is likely that you will have a small delay until the apps get started.
You need to enter the pass every time you unlock the phone or turn it on. You can configure the time between the screen powering down and the phone locking itself under Settings > Lock Screen. The default is set to 5 seconds.
HTC EVO running Android 4.0 doesn’t seem to have an encryption option.
Might have to use a separate app for that.
Should have mentioned that not all Android phone implementations are the same.
Have you checked whether it is listed in another menu? I find it strange if it has really been removed by HTC from the phone.
The only bummer is that other encryption apps gets totally confused by this. I had to unencrypt Android again so that I can use encryption apps like eWallet and DoD’s CAC and PIV
There are also apps such as Unlock with wifi that will disable the lock screen pin as long as you are connected to your home wifi, as well as delaying the lock screen for a defined time period – it can help to lessen the pain of using one.
I’m pretty sure that app says it doesn’t work with an encrypted phone. I think once encrypted you can’t run without a lock screen. I could be wrong. I hope I’m wrong.
“Your Android phone needs to support encryption. I’m not 100% about that but I think encryption was added in Android 3.0.”
It was added as of Gingerbread Android 2.3.4. My mom’s android runs that and supports full device encryption. Source backing my claim: http://www.ehow.com/info_12183909_encryption-android.html You should be able to change that line in your article to something like:
“Your Android phone needs to support encryption. Encryption was added to most Android phones sporting Android 2.3.4 or newer, also known as Gingerbread.”
How much cpu and battery does it take to decrypt/encrypt applications and data every time
you use your Android device ?
Good question. I do not have any data yet about that. It is however likely that it will impact battery life during use, but not when the phone is idle.