Google Authenticator's mysterious security update does not enable end-to-end encryption

Google has released a new update for its Google Authenticator application. The changelog reveals that Google "added device encryption to storage of secret value". Users who have hoped that Google would integrate end-to-end encryption to the application will be disappointed, as this is still not the case.
Google Authenticator was updated about a month ago. The main new feature that Google integrated into the application was two-factor authentication syncing. The applications syncs the stored data with a user's other devices, when turned on.
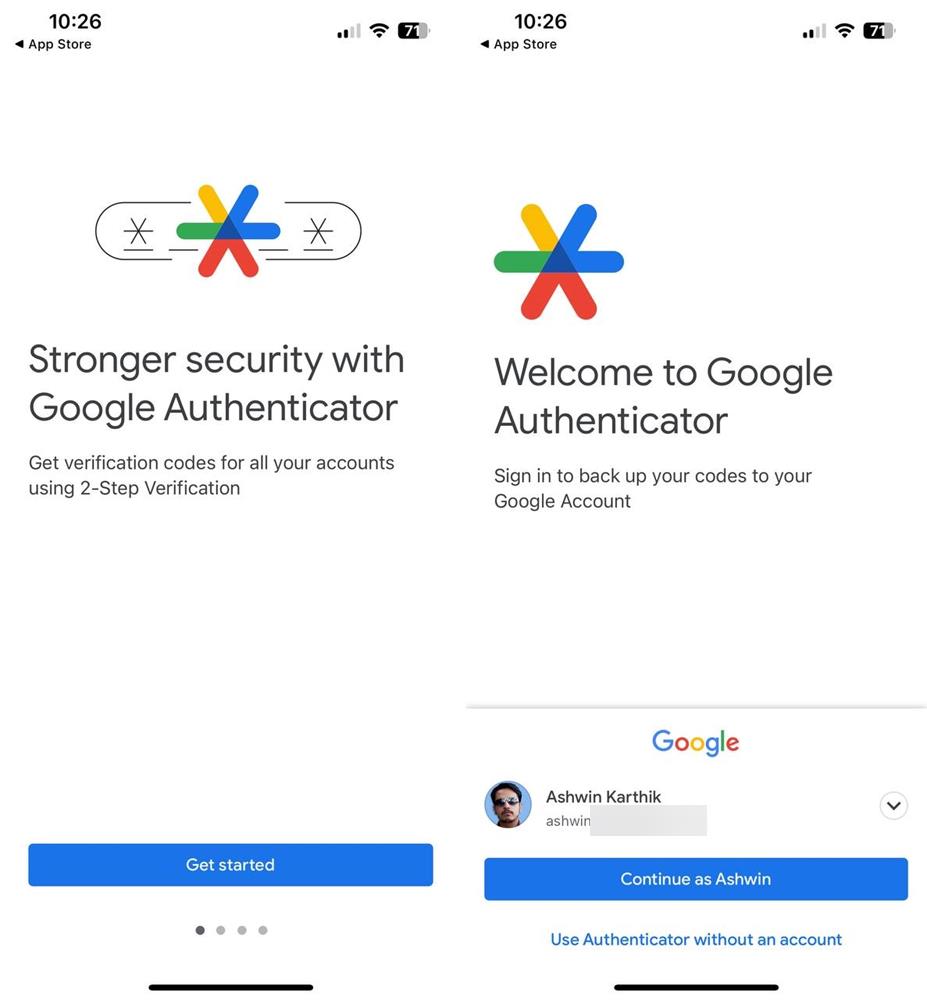
While that sounds like a good usability improvement, as it means that users do not have to set up the functionality on all their devices manually, it turned out that Google did not implement end-to-end encryption of the data. In other words: attackers, for instance by using man-in-the-middle attacks, may read the secrets; this would give them access to the codes generated. A secret, or seed, is used to generate one-time codes for specific services or apps.
We advised Google Authenticator users to keep the feature turned off, or use a different authenticator application instead. End-to-end encryption encrypts the data on the user's device, so that sensitive information are protected.
The latest changelog of Google's Authenticator app suggests that Google has integrated the feature into the app. Tests, by the German Heise publisher, and confirmed by us, do not confirm the change. The changelog message, Added device encryption to storage of secret values, must mean something else then, but it is unclear what it does exactly.
Accounts added to Google Authenticator are synced to the cloud using TLS encryption. An inspection of the data reveals that the seeds are still Base32 encoded. Base32 can be decoded easily. Proper end-to-end encryption would not reveal any seed data, or any other data for the matter, thanks to the use of encryption.
Google Authenticator users should keep the cloud syncing functionality of the application turned off as a consequence.





















Nothing happens mysteriously at Google’s headquarters.
Google’s CIA and NSA bosses are very hesitant to allow them to use end-to-end encryption in their consumer products. Unless it has built-in backdoors. Then it’s OK.
Lack of end-to-end encryption aside, the new icon sucks. Looks like something a per-kindergartner drew on a paper with crayons.
Looks like the Walmart App on Android.
So Google apparently gave into the state’s demand that the possibility of allowing the state to crack the “secret” code remain an open option ??