Google Authenticator adds support for syncing 2FA codes to the cloud

The Google Authenticator app has been updated with a much requested feature, cloud backup. The new feature is available on Android and iOS versions of the app.
Two-factor authentication (2FA) is a must-enable option that allows you to protect your online accounts from being hacked. Authy has offered 2FA account syncing for many years. But Google Authenticator, which is equally, if not more popular, lacked the option. The app was launched in 2010, but has barely evolved over the years, and users had been requesting the Mountain View company to add support for a cloud backup option.
Google Authenticator can now sync your accounts between multiple devices
Think about it, if you lose access to your device, you could use a backup code (recovery code) to access your Google account, but what about all the other accounts that you had added to the authenticator app? Without access to the phone, you would be essentially be locked out of your own accounts. Syncing 2FA codes can be particularly useful if your phone gets stolen, or stops working all of a sudden, or if you had to factory reset your mobile to fix some issue.
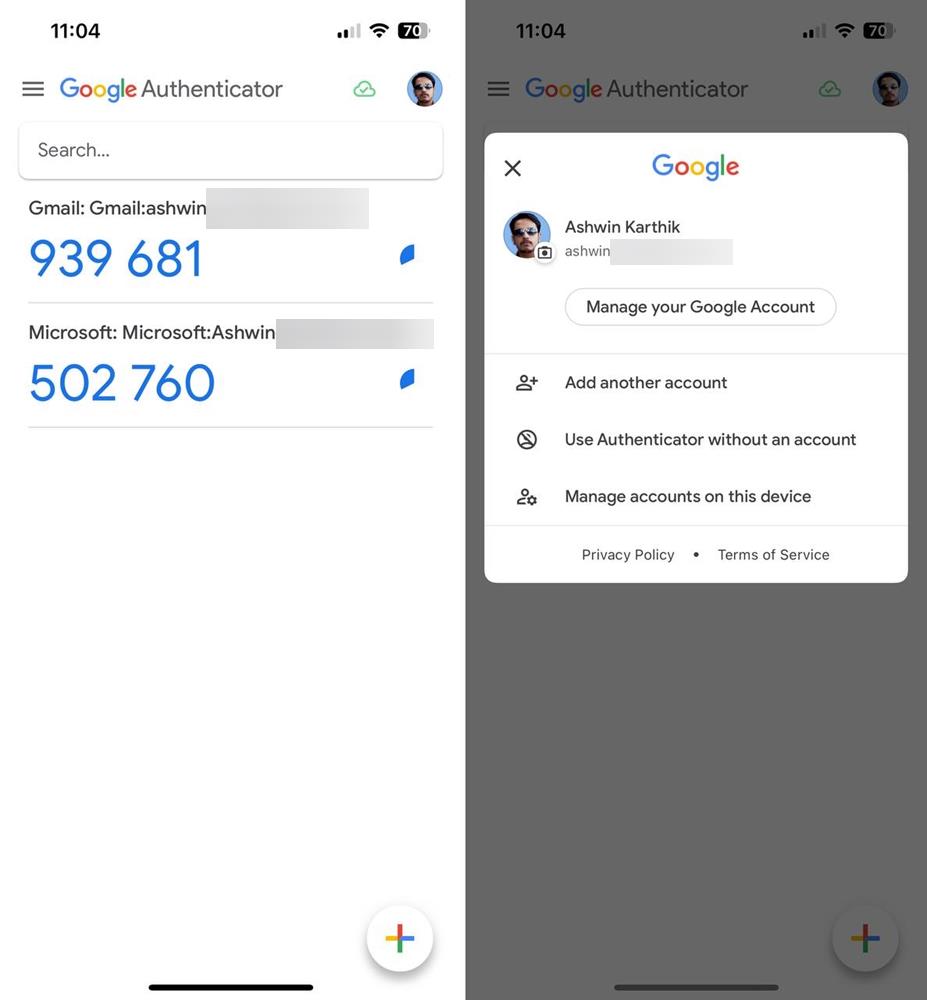
Today's Google Authenticator update solves this problem by adding support for syncing 2FA codes. To use it, you will need to sign in to your Google account. The app will prompt you to choose the account that you want to use for syncing. Select the ID, and tap on Continue. That's it, the app will automatically backup the 2FA details of all your accounts to the cloud. It displays a small cloud icon at the top of the screen to indicate the synchronization status. If you have a second device, open the Google Authenticator app on it, and select the account to sign in to, this will sync the associated accounts and their 2FA tokens.
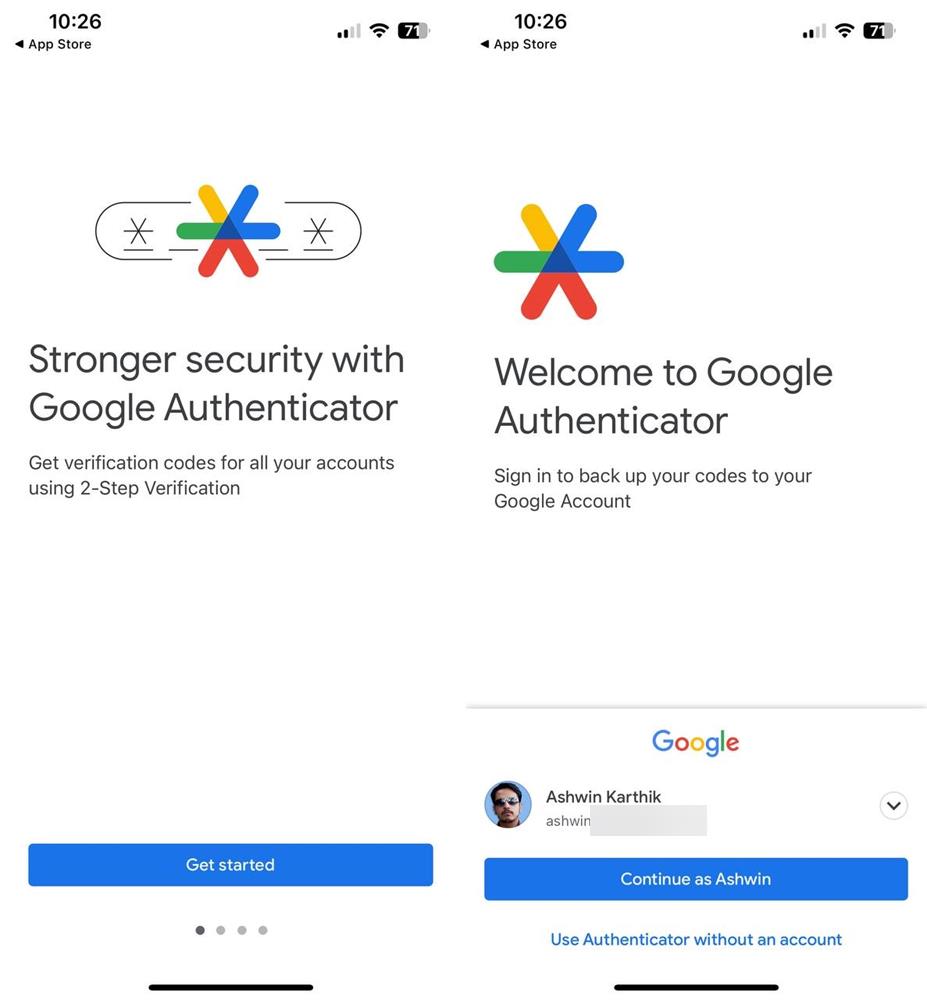
What if you want to stop using the cloud sync feature? Maybe you chose the wrong account to sync the data to, or you want to select a different one? Tap on your profile icon in the top right corner of the app to manage your account. If you wish to remove 2FA codes from Google Authenticator's cloud sync, tap the option that is labeled "Use without an account". Confirm the action, and the app will stop syncing the accounts across your devices, you will still be able to access the codes on the device. The Google Authenticator app has a new icon that looks like a colorful asterisk.
Refer to the official announcement for more details.
Download Google Authenticator from the Play Store (version 6.0) and the App Store (version 4.0). The Android version isn't live on the Play Store yet, I sideloaded it on my phone to test it.
Should you use Google Authenticator's cloud sync feature?
While the feature is convenient, it comes with a potential risk factor. Theoretically, a hacker who has managed to gain access to your Google account will also have access to your 2FA codes. I think it's worth mentioning that you don't need to sign in to your Google account to use Google Authenticator normally, it is optional and only required if you want to sync your accounts between your devices.
It may be a wiser choice to use a dedicated app for getting 2FA codes. If you prefer open source alternatives, I can recommend Aegis for Android and Raivo OTP for iOS. Both apps have an option to backup your 2FA accounts, you can save it to your computer or a cloud storage service and use it to import the data again. Bitwarden also supports 2FA codes, but the feature is only available with a premium subscription.
Which authenticator app do you use?





















2FA is bullshit. It adds a second vector of attack. It’s just another way to add to your “advertising profile”.
Remember when we all belived the “food triangle” the US government came up with only to eventually find out it was all bullshit designed to increase American farmers income?
People should be taught how to create strong passwords and store them safely, in school as children.
Longer is stronger. “TheBlueCatFliesSlowly” is twice as strong as “s9f%89<fde:" and easy to remember.
And never, ever, trust your passwords to strangers FFS!
>Longer is stronger. “TheBlueCatFliesSlowly” is twice as strong as “s9f%89<fde:" and easy to remember.
Lol no no no. Stay out of cryptography for the sake of all of us. Your password is terrible!
[https://arstechnica.com/information-technology/2013/05/how-crackers-make-minced-meat-out-of-your-passwords/]
Anatomy of a hack: How crackers ransack passwords like “qeadzcwrsfxv1331”. The characteristics that made "momof3g8kids" and "Oscar+emmy2" easy to remember are precisely the things that allowed them to be cracked. Their basic components—"mom," "kids," "oscar," "emmy," and numbers—are a core part of even basic password-cracking lists.
Passwords that use chaining of words are easiest to crack by dictionary attacks.
Now back to 2FA:
username
password
plus the FIDO2 ECC key
Think, think: You need all 3 to get in. Now what has the highest entropy? The FIDO2 2FA key of course! An ECC key with 256 bit is 2^256 combinations. You simply cannot brute force that on any hardware on Earth. The strongest secret out of all 3 you need is the 2FA key in a separate piece of hardware.
Now you with the conspiracy "it lowers security" or is "a second attack vector". Wrong, wrong, wrong. Each secret of the 3 increases the total entropy. Any PhD in maths will instantly agree.
You don’t understand what 2FA means, nor how it works. I am sure I am wasting my time here, but please do explain how do you think you can intercept FIDO2?
[https://hybrismart.com/wp-content/uploads/2019/05/Screen-Shot-2019-05-14-at-8.36.34-PM.png]
At what step do you see a problem? The ECC keys reside in a separate processor outside of the computer. The protocol is safe from MITM. You can only authenticate for the exact site the individual key is for.
If you write me in detail what technical problem there is, I’ll take you seriously. Otherwise I assume the level of cryptography of the FIDO2 protocol is not understood well by you to make baseless assumptions.