Microsoft Security Bulletins For August 2012 Released
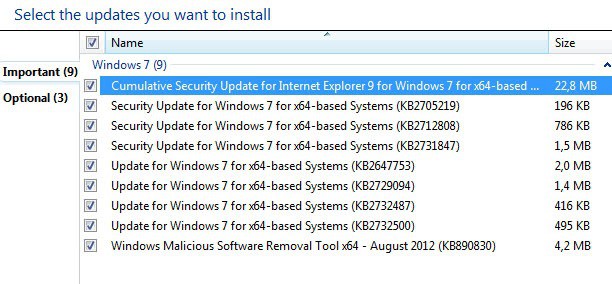
Microsoft a few minutes ago has pushed out nine security updates as part of this month's update for the Windows operating system. The security bulletins for August 2012 address vulnerabilities in programs such as Microsoft Windows, Internet Explorer, Microsoft Office, Microsoft Exchange and Microsoft SQL Server. Five of the bulletins have received a maximum severity rating of critical, the highest available rating for vulnerabilities, while the remaining four bulletins a rating of important.
Maximum severity rating means that there is at least one version of a product that has received the rating. Critical vulnerabilities allow code execution on a user system without user interaction. Lets take a look at the different operating systems and their severity ratings:
- Windows XP: 3 critical, 2 important
- Windows Vista: 1 critical, 3 important
- Windows 7: 1 critical, 2 important, 1 moderate
- Windows Server 2003: 1 critical, 1 important, 1 moderate, 1 low
- Windows Server 2008: 1 important, 2 moderate, 1 low
- Windows Server 2008 R2: 1 important, 2 moderate, 1 low
As you can see, newer versions of Windows in this particular case face less severe vulnerabilities than older versions. While this does not have to be always the case, it is usually the case. Sometimes though, newer operating systems may be vulnerable while oder are not due to added features in those newer systems.
The updates are already available on Windows Update. You may need to check for updates manually for the operating system to catch the updates.
You can alternatively download the updates from Microsoft's Download Center where they are available for all affected products both as standalone patches and a monthly ISO image.
Bulletins
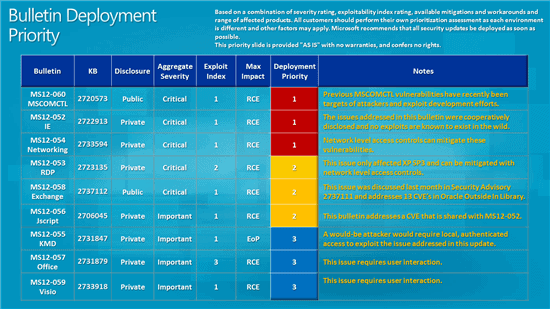
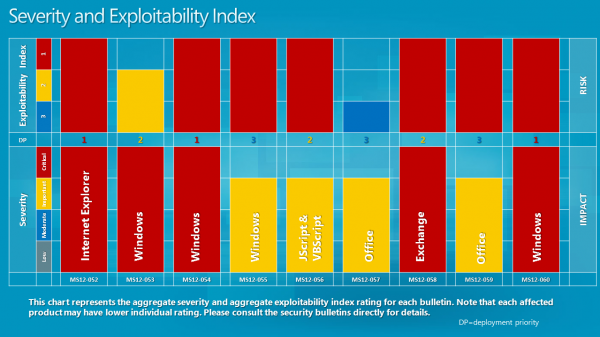
- MS12-052 - Cumulative Security Update for Internet Explorer (2722913) This security update resolves four privately reported vulnerabilities in Internet Explorer. The most severe vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer. An attacker who successfully exploited any of these vulnerabilities could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
- MS12-053 - Vulnerability in Remote Desktop Could Allow Remote Code Execution (2723135) This security update resolves a privately reported vulnerability in the Remote Desktop Protocol. The vulnerability could allow remote code execution if an attacker sends a sequence of specially crafted RDP packets to an affected system. By default, the Remote Desktop Protocol (RDP) is not enabled on any Windows operating system. Systems that do not have RDP enabled are not at risk.
- MS12-054 - Vulnerabilities in Windows Networking Components Could Allow Remote Code Execution (2733594) This security update resolves four privately reported vulnerabilities in Microsoft Windows. The most severe of these vulnerabilities could allow remote code execution if an attacker sends a specially crafted response to a Windows print spooler request. Firewall best practices and standard default firewall configurations can help protect networks from attacks that originate outside the enterprise perimeter. Best practices recommend that systems connected directly to the Internet have a minimal number of ports exposed.
- MS12-060 - Vulnerability in Windows Common Controls Could Allow Remote Code Execution (2720573)
This security update resolves a privately reported vulnerability in Windows common controls. The vulnerability could allow remote code execution if a user visits a website containing specially crafted content designed to exploit the vulnerability. In all cases, however, an attacker would have no way to force users to visit such a website. Instead, an attacker would have to convince users to visit the website, typically by getting them to click a link in an email message or Instant Messenger message that takes them to the attacker's website. The malicious file could be sent as an email attachment as well, but the attacker would have to convince the user to open the attachment in order to exploit the vulnerability. - MS12-058 - Vulnerabilities in Microsoft Exchange Server WebReady Document Viewing Could Allow Remote Code Execution (2740358) This security update resolves publicly disclosed vulnerabilities in Microsoft Exchange Server WebReady Document Viewing. The vulnerabilities could allow remote code execution in the security context of the transcoding service on the Exchange server if a user previews a specially crafted file using Outlook Web App (OWA). The transcoding service in Exchange that is used for WebReady Document Viewing is running in the LocalService account. The LocalService account has minimum privileges on the local computer and presents anonymous credentials on the network.
- MS12-055 - Vulnerability in Windows Kernel-Mode Drivers Could Allow Elevation of Privilege (2731847) This security update resolves one privately reported vulnerability in Microsoft Windows. The vulnerability could allow elevation of privilege if an attacker logs on to the system and runs a specially crafted application. An attacker must have valid logon credentials and be able to log on locally to exploit this vulnerability.
- MS12-056 - Vulnerability in JScript and VBScript Engines Could Allow Remote Code Execution (2706045) This security update resolves a privately reported vulnerability in the JScript and VBScript scripting engines on 64-bit versions of Microsoft Windows. The vulnerability could allow remote code execution if a user visited a specially crafted website. An attacker would have no way to force users to visit the website. Instead, an attacker would have to convince users to visit the website, typically by getting them to click a link in an email message or Instant Messenger message that takes users to the attacker's website.
- MS12-057 - Vulnerability in Microsoft Office Could Allow Remote Code Execution (2731879)
This security update resolves one privately reported vulnerability in Microsoft Office. The vulnerability could allow remote code execution if a user opens a specially crafted file or embeds a specially crafted Computer Graphics Metafile (CGM) graphics file into an Office file. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights. - MS12-059 - Vulnerability in Microsoft Visio Could Allow Remote Code Execution (2733918)
This security update resolves a privately reported vulnerability in Microsoft Office. The vulnerability could allow remote code execution if a user opens a specially crafted Visio file. An attacker who successfully exploited this vulnerability could gain the same user rights as the current user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.




















Had repeated prompts for KB2647753 after installing automatically.Fixed by uninstalling & installing manually from MS Support..
Microsoft’s updates are just out and I got already 4 revision.
Thanks Martin, Again your article was a big help with main 15 updates I received this mount. Six for office 2010 and 9 for Windows 7.