SecretSync, Security Layer To Protect Sensitive Files On Dropbox

The popular file synchronization and hosting service Dropbox encrypts all uploaded files and folders automatically to protect network snooping and other forms of attack and unauthorized access to those files. Dropbox recently changed their terms of service which confirmed that the company was able to decrypt files that you upload to Dropbox, for instance to comply with law enforcement.
The chance that someone may look through your files may not be that enticing to you, especially if you have uploaded sensitive information to Dropbox.
Encryption is the best option if you want to sync sensitive or confidential files with Dropbox. Encrypted files can only be accessed by authorized users who have the right key to decrypt the files.
I have demonstrated in the past how to encrypt files that you sync with Dropbox with the help of the Open Source software True Crypt (sync confidential files with Dropbox). The process was lengthy, technical and not very comfortable, especially for users who have never worked with True Crypt before.
SecretSync is a standalone software programmed in Java that offers a more comfortable file storing solution. It is basically an add-on service for Dropbox that will automatically encrypt files for you before they are synced with Dropbox.
First time users need to create an account on first run. A username and password is mandatory for the account creation. Security can be improved further by adding a passphrase to the account.
All those information need to be entered on every computer that Secret Sync is installed on, to gain access to the encrypted files on those system.
Secret Sync creates a new folder on the user system and links that folder to the Dropbox folder. All files placed inside the Secret Sync folder will be encrypted before they are moved and synced with Dropbox.
Files moved or copied into the Secret Sync folder are encrypted with 256-bit AES encryption. Files are only decrypted on the user's computer systems, and not on Dropbox.
Anyone accessing the files directly on Dropbox only gets garbage from that point on because of the encryption that is in place online. These files can also not be opened on systems where Dropbox is installed, but Secret Sync is not.
Dropbox would sync those files normally, but since they remain encrypted it is not possible to access them on those systems.
The core advantage of using Secret Sync over a manual solution is that it is way more comfortable to use. All you need to do is install the software, create an account and you are set to go. This does not take longer than a minute at most.
It is even easier on additional systems as you only need to supply your username, password and optionally the passphrase that you have configured during the first installation of the service.
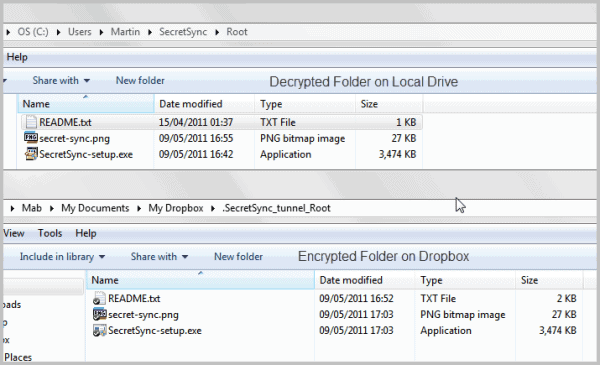
All files that you move into the Secret Sync folder on your hard drive (the one outside of the Dropbox folder) will be automatically encrypted by the application before they are synced with Dropbox.
You get nothing if you try to open the files on Dropbox directly, while they open fine on the local computer.
This method has a disadvantage though that needs to be addressed. Secret Sync can only do its magic if the program is running in the background. The Windows beta version is using roughly 30 Megabytes of RAM. You may also need to add Java to the equation as it needs to be running as well.
The program runs silently in the background with no user interface to stop or start it. If you want to close the program, you need to kill it in the Windows Task Manager. This may change considering that this release is a beta version and not the final product.
Secret Sync is only available for Windows currently, but the developers have promised that Mac and Linux versions will be offered soon on the program homepage as well.
You can download the Windows release from this page (via Lifehacker)
Advertisement




















We now know that Dropbox can decrypt your files, but was anyone else familiar with it’s “deduplication” process?
After reading this article – http://paranoia.dubfire.net/2011/04/how-dropbox-sacrifices-user-privacy-for.html – it appears that the deduplication process is a potentially significant privacy issue.
Your files are being hashed and compared to what is already on their servers before the files are sent. They wouldn’t be able to compare (or generate) these hashes if the entire process were encrypted (and not decrypted on their side or through unencrypted hashes being sent). Which means that someone might know what files are without even decrypting them – purely by comparing the hashes. This doesn’t even take into account that at some point decryption is taking place, not just in the occurence of legal requirement.
Examples given in the article:
A. If someone uploaded a file to Dropbox and compared the file size versus data sent. You could potentially know if that file already existed on their network. The existance of a file on the network might be justification for the legal process to decrypt that file (i.e. for copyright issue or domestic security).
B. The possibility of Dropbox maintaining a database of file hashes required to (or agreed upon) by the US government. This could lead to account flagging and forwarding based on uploaded or potential uploaded content.
Encrypting your files before introducing them to Dropbox seems like an important step if you require more security and privacy.
This article is why I see not reason to trust any server that provides the encryption key to secure data whilst retaining a copy itself:
Facebook “handed out spare keys” to users’ data
Read more: Facebook “handed out spare keys” to users’ data | Security | News | PC Pro http://www.pcpro.co.uk/news/security/367267/facebook-handed-out-spare-keys-to-users-data#ixzz1M2VAxXxB
I ti would be must better if any “secret” software included the function to generate the key on the local machine with no interaction with any server and that any such software should not require online sign up provision of personal data.
It is a promising bit of software, but calling it “secret” needs critical qualification.
Online registration and server interaction seem more of a business model issue that keeping dropbox users data secure.
Now if they want to create an option to create a key online, then this should be disassociated from the software and no registration should be required.
Is it open source?
Seems quite similar to http://www.boxcryptor.com/ ;-)
Thanks for the heads up, Martin. I’ve been using SynchToy to copy files to/from the Dropbox folder. It looks like SecretSync might give me the same or enhanced functionality plus encryption.
lol, from “Quo Vadis Lifehacker?” to “(via Lifehacker)” in six short days. :D
Seriously though, this sounds great. Better than trying to work with .bat files and Truecrypt.
be glad ghacks filters out the lifehacker nonsense – you wanna go there every day and do it yourself?
Zeus well I cannot change that if a company decides to give them an exclusive story.
“On the first installation of SecretSync, you’ll need to sign-up for an encryption key. ”
No thanks the user needs full control over any “encryption key”, the need to involve an online process is a security flaw in and of itself. I will pass on this ‘solution’…
It just looks like a clone of dropbox
I take a dim view of this piece of software, to be called standalone is a misnomer, use requires setting up an online account to activate, this is a weakness.
I do like it’s website statement:
“Your files are always encrypted when online. This means that before your files leave the computer you physically control and own, they’re encrypted. They stay encrypted while being synchronized, until they’re back in your physical control. ”
http://getsecretsync.appspot.com/download/lifehacker/
But I also prefer a fuller FAQ about what encryption it uses, what are the terms and conditions of use etc
I also do not like the name, to many the word “secret” can infer a negative. Even so I will give it a whirl
Interesting solution!
>> “First time users need to create an account on first run…”
Is this acct. in your local PC only,
or in the SecretSync web site?
– I’m concerned about the additional security concerns
of any Java applet with access to my SecretSync pwd!…
— how’s my SecretSync pwd stored?
just asking, Martin…
Hi, this is James with SecretSync. When you sign-up via the installer, we generate a truly random 256-bit key. You may use this on its own, or you can provide your own passphrase, which can be anything, including another truly random key. We’ve added the following to the FAQ to help clear up how this works —
http://getsecretsync.com/ss/faq/#q3
When SecretSync starts up it retrieves the key we generate, but after that there is no more contact with our site. (And this can be verified by watching network traffic on your NIC.)
Good question that I have not thought about at all. The FAQ seems to suggest that the account is only needed for key creation and sharing with additional computer systems, but not after it has been created. http://getsecretsync.com/ss/faq/