Storing Data In The Cloud With Dropbox And TrueCrypt
In Why You Need To Protect Your Data In The Cloud I have explained why it is important to protect data that you upload to the cloud. In this guide, I will show you how to implement one of the suggestions: Encryption. I'm using the cloud hosting and synchronization service Dropbox and the Open Source encryption software TrueCrypt for the example. In the end, you should be able to use the same method to protect data with your encryption software and cloud hosting provider of choice.
Lets take a look at the basics first. If you are a free Dropbox users, you get 2 Gigabytes of space. That's usually more than enough to store documents and files in the cloud. Dropbox uses encryption to protect data on their servers from unauthorized access. As I pointed out before, that may not sufficient considering that the company may decrypt all files in a legal process, which also means there is a chance that an attacker might do the same. (Dropbox has responded to the issue)
TrueCrypt is an Open Source encryption software for Windows, Linux and Macintosh that can encrypt data containers or full hard drives or hard drive partitions. Since we only have a maximum of 2 Gigabytes of storage on Dropbox, we need to create an encrypted container to store our files in.
The basic idea is therefor the following: We create a TrueCrypt container on the local system. The size depends on your preferences, I would suggest to keep it as small as possible. If you run out of space you can either increase the size of the TrueCrypt container or create a second container to store additional data in. My suggestion is a maximum size of 500 Megabytes, if you can live with less select that number. My personal container has a size of 100 Megabytes.
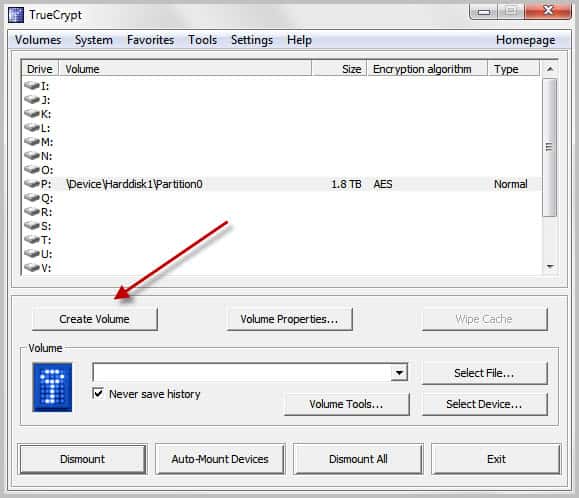
Download the latest version of True Crypt from the developer website. Install it and run it after installation. Locate the Create Volume button in the interface and click on it.
Click Next two times on the following screens to create an encrypted file container with a standard TrueCrypt volume (those are the default options). Click Select File and browse to a location where you want to create the new container. Make sure it is not in the Dropbox folder if Dropbox is running. You can name the container anyway you want, e.g. holiday2010.avi.
Click Next on the encryption options page unless you want to change the encryption algorithm or hash algorithm. Select the volume size on the next screen. I suggest you keep it at a few hundred Megabytes tops.
You need to enter a secure password on the next screen. It is suggested to use as many characters as possible (24+) with upper and lower letters, numbers and special characters. The maximum length of a True Crypt password is 64 characters.
Now it is time to select the volume format on the next screen. If you only use Windows computers you may want to select NTFS as the file system. If you use others you may be better of with FAT. Juggle the mouse around a bit and click on format once you are done with that.
Congratulations, the new True Crypt volume has been created.
Move your unmounted new data container to the Dropbox folder. That folder, but not its contents since Dropbox cannot access those, will now be synced with your space in the cloud. It can take minutes to hours depending on the upload speed of your Internet connection and the size of the container that you have created.
But this is a one-time transfer. Dropbox will only transfer the changed bits after the first upload. This is theoretically a security risk as well but it would require lots of energy and dedication which means it usually can be neglected for personal data.
You can now mount the container on your local system and use it normally just like any other True Crypt volume. You can add, delete or edit files in it. Whenever you unmount it, it gets synced with your Dropbox account. This means that you need to unmount it regularly before you shut down the computer in order to sync the data with Dropbox.
Install True Crypt on all your other devices to access the encrypted volume there as well. You can also copy a portable version of True Crypt to the Dropbox for direct access without installation.
Problems
The biggest problem is that you cannot access the encrypted data on Dropbox's web interface anymore. All you see is that one big encrypted container that you cannot access because you cannot run True Crypt on the cloud. There is no way around it: You either use the encrypted container for additional security, or trust the standard Dropbox encryption to access the data on the web interface as well.
You also need to make sure to mount the encrypted data container on one computer at a time. Dropbox would otherwise create a copy of the file in the Dropbox folder which would cause files becoming out of sync.
Verdict
If you want that extra bit of security, and eliminate the minor chance that someone manages to decrypt your data on Dropbox, or that Dropbox decrypts the data for law enforcement, then your best bet is third party encryption of the data. It may sound complex and complicated to setup, when it is a straightforward process that's done in less than five minutes.
Advertisement

















So if I lose all my computers and devices but have a backed up TrueC file on a cloud but can’t decrypt if in the cloud … how do I get access to it once I gain access to another computer?
Well you need to install TrueCrypt and get the container back on your system, for instance by syncing it. Then you can mount it as usually.
Because, as the author mentioned, “Only the changed bits are transferred, not the whole container”, you are exposing your Truecrypt volume to a security vulnerability. Different versions of your TC volume throughout time are available, and if piecemeal changes are visible and comparable, that spells trouble. If you decide to change your password, you should copy the contents to your offline hard drive, and create a new container from scratch. Otherwise you compromise your volume’s security (TC mentions this on their website).
Great how to, but would it not be easier to just use a service that does not have the ability to view your files? SpiderOak states that they cannot view or see a users files.
https://spideroak.com/engineering_matters#true_privacy
Granted you can see your files through their web interface, but they also claim that they do not store a users password except during a persons session.
https://spideroak.com/engineering_matters#instant_access
Not to mention SpiderOak does more than just sync files, it also performs backups and shares data if you want it shared.
I use the free cobian backup software to automatically create an encrypted 7-zip backup of important unencrypted files and folders outside the drop box folder The encrypted backup is automatically then placed in the dropbox folder for online cloud syncing. 7-zip can also be used to encrypt the file name, which for some can be important.
http://www.educ.umu.se/~cobian/cobianbackup.htm
For linux, as least Ubuntu I have used Duplicity to offer an equivalent to the above suggestions.
http://packages.ubuntu.com/search?searchon=names&keywords=duplicity
I would be interested to know of any free backup software that has options for encryption. I always suggest that when using any kind of cloud service to store files I recommend using separate software to do the encryption, to ensure full local user control over the process, too often online cloud services oversell encryption options that are weak and ultimately involve placing trust in a provider who often has direct access to files in ways that ensure it can unencrypt them.
Of course these ideas compromise dropbox ease of use, but for those in need of encryption it might be a useful trade-off.
What I never knew about drop box is that the local photos folder it creates is Public by default, meaning anyone can view the contents, for the average user that might be more worrying than other dropbox problems, who reads terms and conditions and then chooses not to use the photos folder….
I tried doing this several years ago and found DropBox did not reliably update the TrueCrypt file container. I think it had something to do with the timestamp of the TrueCrypt file not changing when the internal contents where updated, or maybe it had something to do with synchronizing between two PCs. Anyway, I lost some data and stopped using this trick. I gather DropBox has improved it’s synchronization mechanism?
My solution in Linux is to use eCryptfs and put a symbolic link to the .private folder inside the DropBox folder so the encrypted files are automatically uploaded to DopBox. Obviously this doesn’t work for Windows, but I wish it did.
Thank you for the great article. May I ask for clarification on why you suggest that the container by kept to “a few hundred Megabytes tops”?
Why use cloud storage at all ? Isn’t the whole point of cloud storage like Dropbox to have access from anywhere with any PC/device and to share/collaborate files ? Encrypting those files just misses this point.
well backup and availability are two reasons.
I currently use Axcrypt to secure files with sensitive data that I store on Dropbox. You can encrypt or decrypt single files or groups of files fairly quickly. The main reason I decided to go with Axcrypt is the ability to quickly update the file on Dropbox due to the smaller file size. Axcrypt has a portable software package called “Axcrypt2go.exe” that allows you to work with your files most anywhere. Thanks for all your articles as they are very helpful. I’m impressed with your skill as a technical writer. Such volume with such quality!
So I haven’t used TrueCrypt in a while so I apologize if this is a silly question…Let’s say you setup a 500MB TrueCrypt container and host it on DropBox…when you mount that container and change a file, does it have to upload the whole container again? I know DropBox has some bite-level sync magic but since the whole container is encrypted I’m wondering how well that work? Cause if you had to re-upload the full 500MB even if you just edited a simple text file within it…well, that’s pretty inefficient I would think.
Looks like I have to read more before commenting. I’ll do a more detailed analysis and see what I get.
Thanks a lot for the info, Martin!
Finally, I made some tests and now I’m using it to sync a big database over three places.
Thanks for your comments and info!!! :D
Sure no problem, definitely worth investigating.
actually I think you need to activate the setting “preserve modification timestamp of file containers” under Settings -> Preferences in the main TrueCrypt window.
The default is (or at least was, when I last did this) that every time TC-Container is modified, the timestamp would also change.
Only the changed bits are transferred, not the whole container. And since you transfer the encrypted container and not the files therein, it is not different from any other file transfer to Dropbox.
Surely Dropbox changes ALL of the bits of the file for any given small change of any file within the container. To do otherwise would be a security hole. Therefore both are true. Dropbox only uploads the changed bits, AND the entire file must be resynced (because all the bits have changed) every time.
From what I’ve tested for work, Dropbox syncs the whole file. Even if the only thing changed was the date stamp. At least that’s what I experience with large files. I tried syncing a ~100Mb access database and it syncs the whole file…
I’d be happy to sync big files this easy.
According to Dropbox’s Wiki: “Dropbox tries to achieve the best possible performance by trying to be as smart as possible about what data it transfers. It only uploads changes made to the file instead of the entire file. For example, if you upload a 30-page document and only edit one page of it, Dropbox can detect and update only the page that changed. What that means to you is faster, safe and reliable syncing.” http://www.dropbox.com/help/8
Sweet…Looks like I have another geeky project to try this weekend then, thanx again!!!
Another very good article, Martin!
Question: [ instead of using TrueCrypt … ]
———–
If I simply use “7-Zip” to pack and encrypt my data file,
(using 7-Zip ‘s own ** AES-256 encryption **),
and I then upload the file to Dropbox,
will my data file be well protected against attacks, etc.?
thks!
Sure those files are encrypted as well and cannot be opened without the password. The system is different from True Crypt in some regards, as you need to replace existing files in the zip file with new versions manually. Not a problem though if you never update those files. And it is obviously easier to configure and setup.