
Azure vulnerability allowed hackers to manipulate Bing results and take over accounts
BingBang, that is the name that security researchers at Wiz gave the Azure platform vulnerability that allowed them to change Bing search results and access Microsoft user data, including emails and work […]

How to stay safe while using public Wi-Fi
Whether you are traveling frequently or a remote worker, relying on public Wi-Fi may not be ideal, but it may be the only option to get work done sometimes. Many may not […]

Dark and Darker Developer Uses ChatGPT AI tool in Bid to Prove it Hasn't Infringed Copyright
Nexon files lawsuit. See detail of the lawsuit. Check out Ironmace using ChatGPT to show baseless claims.

How to use Bitwarden's Password Manager in Chrome, Edge and Firefox
Users of the Bitwarden Password Manager may install it on their desktop computers and also mobile devices. Computer users may also install the Bitwarden extension in browsers such as Chrome, Edge or […]

The FBI Has Been Buying Bulk Internet Data from This Florida Company
Discover what type of bulk Internet data the FBI has been purchasing. Discover the name of the Florida company and its affiliates.
How to protect your Windows PC from the attack that led to the Linus Tech Tips hack
One of the world's most popular tech YouTube channels was hacked recently. Linus Tech Tips has over 15 million subscribers on YouTube, but all of the company's technical expertise has not prevented […]

Should you use your browser's password manager or a dedicated app?
Password managers are one of the most important security tools for computer users. They store passwords securely and help with the generation of strong and unique passwords. Computer users have two main […]
GitHub Publishes RSA SSH Host Keys by Mistake, Issues Update
Recently GitHub seems to be getting its fair share of problems. It all started with the user who published Twitter’s source codes on GitHub. Who remains unidentified as Twitter takes Github to […]

Passwords vs Passwordless: A Debate on Online Security
Passwords can be a source of frustration for many individuals in the digital age, often viewed as an inconvenient necessity. While they are an essential element of online security, research indicates that […]

Twitter Says Source Code Was Leaked on GitHub, Now It’s Trying to Find the Culprit
Twitter source code revealed on GitHub. Now they’re trying to find the culprit. Twitter has taken the issue to court making demands to GitHub.

TikTok Bans: Governments Worldwide Take Action Over Security and Privacy Concerns
From the U.S. and Canada to India and Afghanistan, various countries have banned or restricted TikTok due to concerns over privacy and security risks. Click here to learn more.
How Do I Get My Phone To Stop Tracking My Activity?
Our phones are multifunctional devices that help us in many ways. However, every phone activity leaves some kind of digital print, similar to our fingerprints. Almost like creating our digital identity, who […]
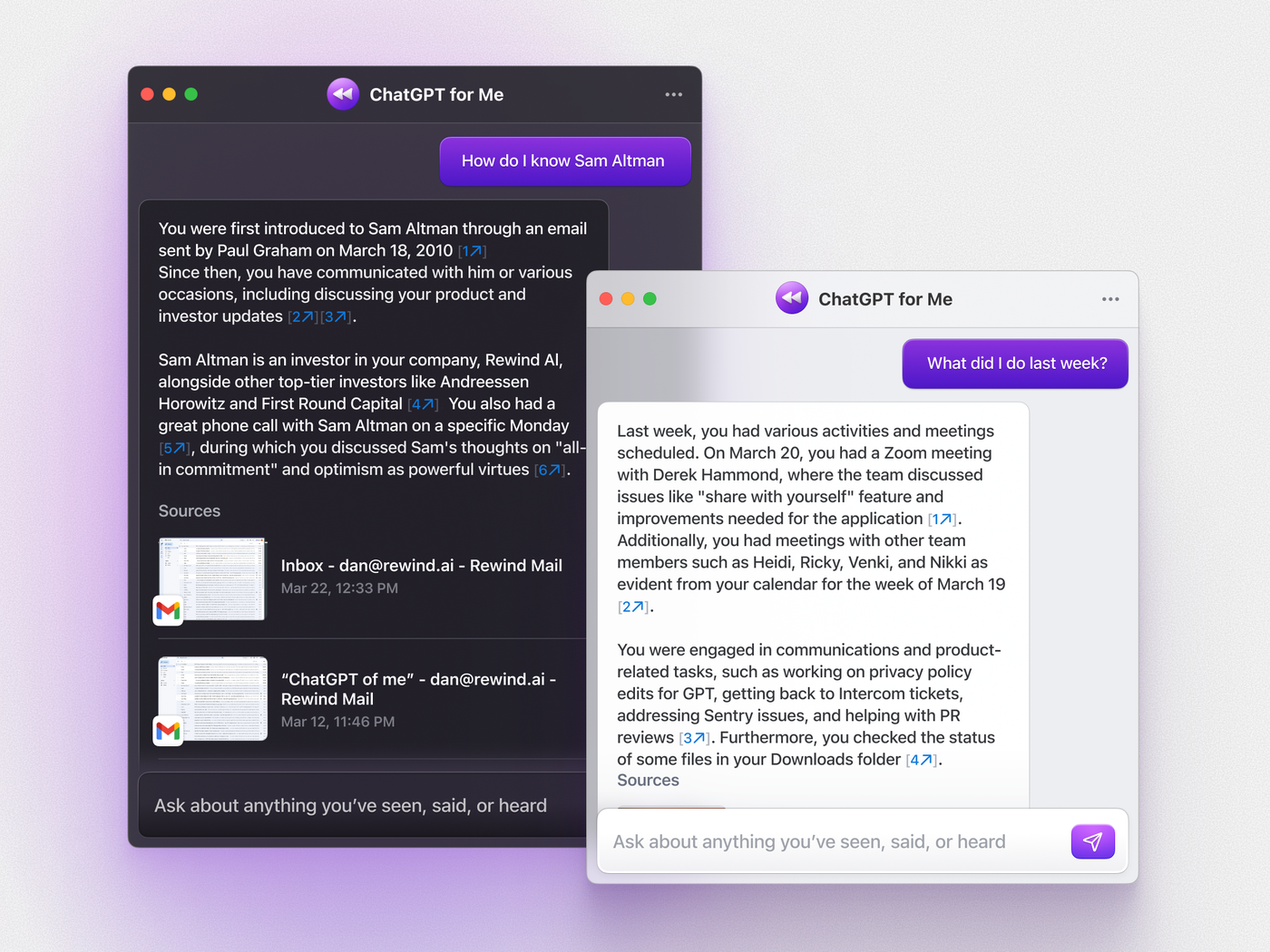
Rewind brings ChatGPT into your personal life, but at what cost?
ChatGPT for Me by Rewind is a new AI system that promises to help you find things on your PC, but there are some security issues. Read more!

Hacking contest Pwn2Own: Ubuntu, Tesla, macOs and Windows 11 cracked
It is the third day of the PWN2OWN VANCOUVER 2023 hacking contest. So far, security researchers managed to crack the operating systems Ubuntu, macOS and Windows 11, and other products, including Tesla […]

How To Secure Your Twitter Account Without Sms-Based Two-Factor Authentication
Since Twitter disabled SMS-based two-factor authentication (2FA) for non-paying users, there are still ways you can protect your twitter account for free. Stay here to read more about the reasons for this […]

How to add a backup two-step login provider to Bitwarden
Earlier this month, I wrote a tutorial on enabling the upcoming security standard WebAuthn in Bitwarden as a two-step login protection. WebAuthn, which stands for Web Authentication, is integrated into operating systems, […]

Emotet is back: Microsoft OneNote is not a safe place anymore
Emotet is back and ready to strike via Microsoft OneNote email attachments. The Emotet threat, associated with the Gold Crestwood, Mummy Spider, or TA542 threat actor, remains active and resilient despite law […]

Meta's security manager targeted by Greek espionage
A former Meta employee was reportedly hacked and wiretapped by the Greek intelligence agency. According to a report from The New York Times, the Greek intelligence agency hacked and wiretapped Artemis Seaford, […]

Oops! ChatGPT Shares AI Chat Histories with the Wrong Crowd
We can’t help but be fascinated by this new revolutionary AI model that is causing so much controversy and changing everything that we’ve known for our entire lives. Since the AI model […]

Bitwarden's unlock with PIN feature is convenient, but also a security risk
Users of the password manager Bitwarden may use the application on all major platforms and on the web. Depending on how they have set up the password manager, they may have to […]

Two Charged in Alleged Hacking of Drug Enforcement Agency's Web Portal
According to previous reports by Gizmodo, two individuals have recently been charged for their suspected involvement in the 2022 hacking incident of the Drug Enforcement Agency's web portal. The Department of Justice […]

Alleged Owner of BreachForums Arrested: Why It Matters
Earlier reports by Krebs on Security and Bleeping Computer have indicated that Conor Brian Fitzpatrick, known online as "Pompompurin," was arrested at his residence in New York on Wednesday by the FBI […]

Cloudflare announces AI-powered Fraud Detection tool
Cloudflare announced a new AI-powered fraud detection tool this week that is designed to protect businesses and consumers against various types of fraud. Cloudflare Fraud Detection protects against fake account logins, account […]

How to Hide Instagram Account and Prevent Other Users from Finding You
Did you know that people can find you easily on Instagram? This can, however, be changed. You can now hide your Instagram account and hide from your contacts and other people finding […]

What Is a Deepfake? Is It Legal? Everything You Need To Know
Computers are getting smarter by the day. From movie graphics to AI-powered tools, almost everything can be simulated. Deepfake technology has now been making the headlines. So, what is Deepfake and is […]

NordPass Password Manager adds passkeys support
Disclosure: Ghacks may receive a referral fee if you click or buy any of the products featured here. NordPass is an emerging password manager from Nord Security, the company behind the popular […]

Bitwarden addresses autofill issue that could be exploited to steal logins
Bitwarden plans to roll out an update to its applications soon that addresses an autofill issue that threat actors could exploit to steal login information. Bitwarden is a popular password management solution […]

How to View Your Google Chrome Saved Passwords
Have we not all been there - you set up a new online account only to frustrate yourself by realizing you can’t remember your password? Thank goodness Chrome allows you to save […]

How to switch from LastPass to RoboForm password manager
This guide walks users through the steps of switching password managers. In particular, it helps users export LastPass passwords and import them into the RoboForm password manager. LastPass is a popular password […]

Telehealth startup shares your data with tech giants
The telehealth startup, Cerebral, has unveiled it shared personal data with Meta, TikTok, and Google. The personal data includes the date of birth, name, email addresses, phone numbers, IP addresses, other demographics, […]

LastPass not the last password manager? Tips for switching password managers
All password manager provide a basic set of features to users, which includes managing, saving and generating passwords. Most users may be surprised that feature sets may different significantly between password managers. […]
Microsoft hardens OneNote against Phishing attacks
Microsoft plans to roll out an update for OneNote in April 2023 to improve the product's protection against "known high risk" phishing attacks. A new entry on the official Microsoft 365 Roadmap, […]

Numerous Lexmark Printers affected by critical security issues
Lexmark confirmed this week that many of its printer models have security vulnerabilities, some of which are rated critical. The company has released seven security advisories for Lexmark devices. Successful exploitation of […]

How to Safely Export Your LastPass Passwords to Keeper
Due to LastPass experiencing several security breaches over the past year, numerous security-conscious users have opted to transition to a more secure password manager. It is likely that you have also encountered […]

9 Tips to Protect Your Mobile Data Security from Hackers
When considering the term "hackers," the common perception is often of individuals seeking unauthorized access to computers to obtain passwords, steal identities, or cause general disruption. However, it is important to note […]

WhatsApp Takes on the EU regarding Encryption and Child Abuse Content
WhatsApp Head Will Cathcart is heading to the United Kingdom to discuss the latest bill that has to do with end-to-end encryption on messaging apps. With the government trying to get a […]

7 Essential Password Manager features and 6 Bonus features
Not every password manager is created equal. In fact, there are huge differences between password managers. Some are local apps, others cloud-based. Some have mobile apps and browser extensions, some support security […]

Neglected security: Government official ignores privacy settings
A security researcher has tracked the location of a former top Biden administration official through the AllTrails app. According to Vice's Motherboard, a security researcher discovered a huge issue that could lead […]

How to configure Two-Step Login via FIDO2 WebAuthn in Bitwarden
Bitwarden password manager users who want to step up the security may configure two-step login via FIDO2 WebAuthn. The feature is not available for all users or in all Bitwarden apps. This […]

LastPass Details Security Breach, Hackers Accessed Encrypted Data
LastPass has released an update that discloses a security breach in which a threat actor gained access to corporate and customer data by infiltrating an employee's personal computer and deploying keylogger malware, […]

