How to protect your Windows PC from the attack that led to the Linus Tech Tips hack
One of the world's most popular tech YouTube channels was hacked recently. Linus Tech Tips has over 15 million subscribers on YouTube, but all of the company's technical expertise has not prevented it from being hacked.
It appears that Linus Tech Tips was not the first company that fell for the attack. It started with an email inquiry regarding sponsorship. It is unclear if there was more than one email, as a common strategy of threat actors is to send a harmless email in the beginning, wait for the potential victim to respond, and then include the malware in the next email.
Linus Tech Tips received an email with a zip file, which supposedly contained a sponsorship offer. One of the company's employees extracted the zip archive, and discovered that it contained the promised PDF document.
Only problem was, it was not a PDF document, but a Windows screensaver file. One of Windows' biggest issues regarding security is that it hides certain common file extensions in File Explorer. An attacker can rename the file SuperOffer.scr to SuperOffer.pdf.scr, and Windows, in all its glory, displays only the SuperOffer.pdf part by default in File Explorer. It looks like a PDF document, and since it is possible to give it a PDF icon, it makes it even more believable.
Execution of the file does not load the system's PDF viewer, but runs the executable. At this stage, if no security software kicks in, the PC should be considered infected.
Protecting your Windows PC from this attack
Protecting Windows PCs from this double file extension security issue is quite easy, as it takes just a few clicks. The main issue here is that Microsoft decided to favor a cleaner look of files on the system over security.
The change forces Windows to always display the file extensions of files. The malicious file example from above would be displayed as SuperOffer.pdf.scr by Windows, which would increase the chance of the user to identify the file as potentially malicious.
The following step-by-step instructions explain how the change is made on Windows 10 and 11 devices:
Windows 10
- Open a File Explorer instance, for example, by clicking on the File Explorer icon in the Windows 10 taskbar.
- Select File > Change folder and search options.
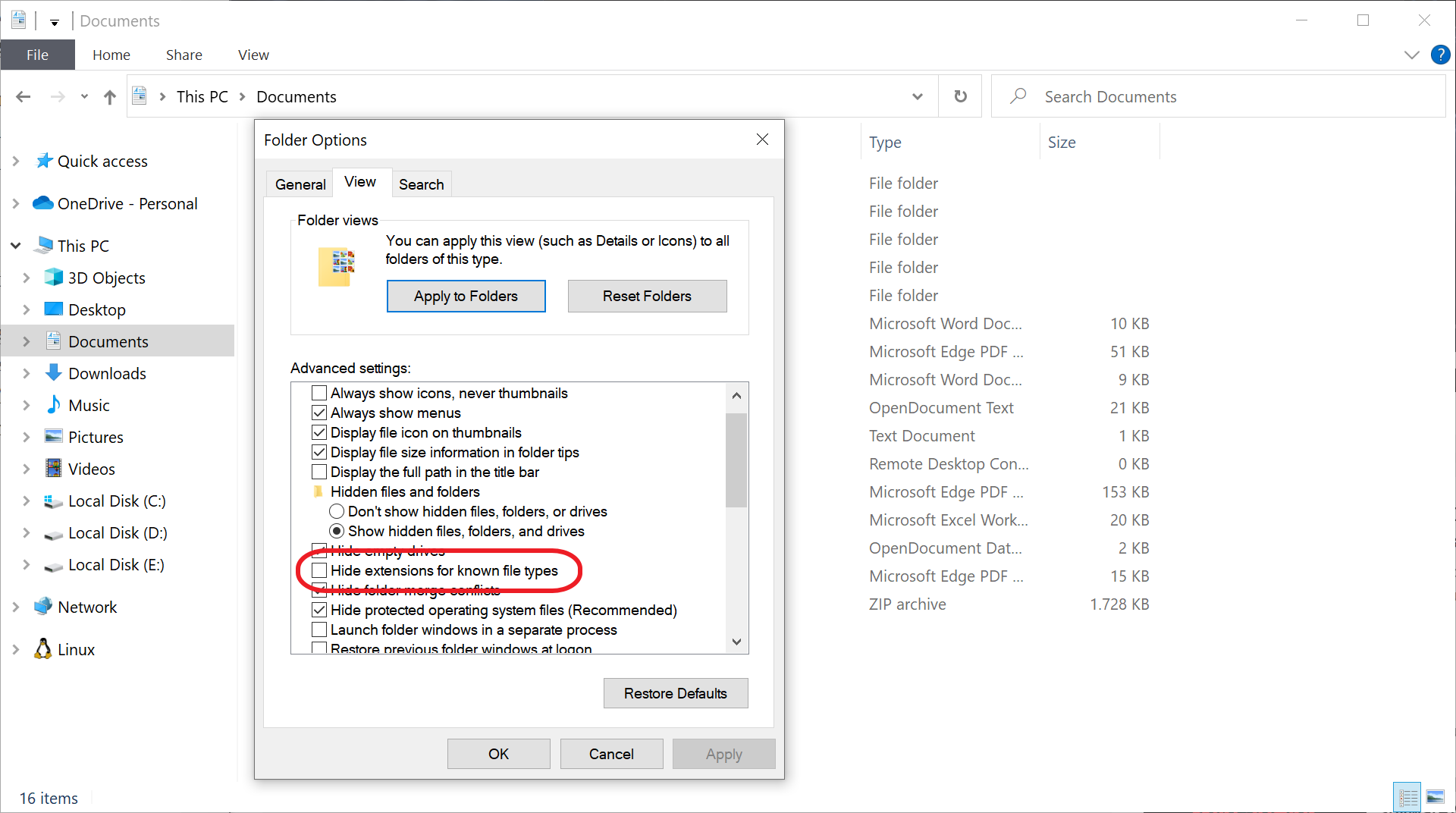
- Switch to the View tab.
- Scroll down until you see "Hide extensions for known file types".
- Remove the checkmark from the setting.
- Click on OK.
Windows 10 will display all file extensions all the time now.
Windows 11
- Open File Explorer on the operating system, it is pinned on the taskbar.
- Select Menu (three-dots) and then Options.
- Switch to the View tab in the Folder Options window.
- Uncheck the "Hide extensions for known file types" options.
- Select OK.
Windows 11 displays all file extensions now for all file types.
Closing Words
The change improves the chance of spotting files that try to disguise their real type by adding a fake file extensions to the filename. While that does not guarantee that users do not execute the file accidentally, it does give inexperienced users a better chance at spotting that something is wrong.
Another option that may work wonders is to always execute certain files, for instance all email attachments, in sandboxes or virtual machines.
Now You: have another tip on how these attacks can be prevented?


















“have another tip on how these attacks can be prevented?”
Sure: use a real file manager, e.g TC or FAR.
Before opening the file which attached you could use virus tool to analyze first the file then that’s the time you could unzip the file
Get antivirus installed as soon as you get your PC and run initial Windows Updates. It will protect you from the majority of viruses.
For as long as I have had Windows PCs, one of the first things I do after first install is to change that extension setting. For the life of me I will never understand how Microsoft thought that was a good idea, and never changed their minds. Infuriating.
Jesus, you’d think everyone on a Youtube tech show would have the smarts not to have hidden file extension.
The first thing I do after installing Windows – that is, after installing an AV – is to open Explorer, and get rid of the bad Microsoft decisions vis-a-vis file displays, etc.
While I agree that file extensions should be on by default, there is still another method hackers can use to fool you, even with file extensions turned on. This video (https://www.youtube.com/watch?v=nIcRK4V_Zvc) explains more, I actually only recently learned about it. TL;DW is that there is a special unicode character that can reverse text and can be used to hide an exe or other dangerous file type.
Sure, do this on your parents/relatives/friends computer and then answer endless rage messages when their files stop working. How so? They rename them and don’t realize the .jpg and .mp3 etc etc extensions need to be there for the file to be of any use. Why? Because they have never seen any file extensions and don’t want to see them either, this is how Microsoft have taught them for ages. Oh and if someone downloads a pdf file they want to have a look at for any reason has a name xxxxxx.pdf.exe they damn sure WILL press that file BECAUSE IT SAID PDF. People are idiots. The best way to solve all this is to install a simple linux (Mint, Zorin) on your moderately gifted friends/relatives computers. They won’t even know they aren’t using windows, just slap on Google Chrome there and they’re happy.
Thats basically Microsoft reaping what they sowed with their in windows integrated softwashing (not to say dumbifcation).(though softwashing is phenomen in the whole US) They perfectly created the vulnerable users with this method. Softwash stuff, remove aspiration and you get Stupid. Brain is incredible powerful, but only if its motivated to work and improve. You wont achive that with more comfort and supported mental lazyness.
What an overexaggeration! File extensions for “known file types” has been default set to off since at least W7 and Vista – Microsoft probably thought “users want to rename files, if they accidentally rename an extension they may make their file unusable, if they want to know what kind of file it is, they can use the icon to see what program it’s associated with”. – Which is totally sound logic, I lived like this for years at one point, without issue – most users just need to know that a picture is a picture, not whether it’s a png, jpeg, or tiff.
Programs with exe extensions which don’t have built in icons, show up with a generic “program” icon, and all dodgy exe’s i’ve seen by small developers, and viruses, usually show up with that “program” icon, so seeing extensions isn’t even necessary really. You also get the “type” in file explorer when using “details”, which is a dead giveaway. Also if someone opens up a word document and get a UAC prompt, that should be a dead giveaway that they didn’t open a word document.
On my windows machine, file.exe.pdf, displays the icon for exe files, regardless of the folder settings related to showing extensions.
Did you set that up yourself, if so, why? “.exe.pdf” will never execute as an exe – it will be handled by pdf viewer.
Don’t you mean “.pdf.exe”? This will show up as an executable, because that is the file extension.
First thing I do with a new machine is to open Folder Options and checkmark the necessary options, or remove the checkmark from where it shouldn’t be IMHO. Also, I always use the “Details” option to display files rather than the standard picture format.
Amazing that the YT channel got caught on on this occasion though.
As for James’s comment above about opening emails from unknown senders I always hit Ctrl+U to see where it originated from before opening it (if ever). The headers will always reveal who the sender is and where they’re located.
If you see a file with an extension when you have explorer set to hide known extensions, that’s a big red flag right there.
Ignorance is the problem, the only cure is knowledge.
“Now You: have another tip on how these attacks can be prevented?”
How about don’t open attachment in emails from an unknown sender?
Or better yet, just don’t use Windows. Even if you know the sender, that doesn’t mean that their machine isn’t infected and sending you some malware.
“don’t use Windows”, unless you mean return to pen and paper, what are you implying here?
There’s no decent alternative to Windows that can accomplish the same things, whether you’re a Mac or Linux guy you need to know there are good reasons for why your OS isn’t the most popular. No offence intended.