
The initial release of Apples Ipod Video Player seems to have encouraged hundreds of software developers to create a software that would convert video files into the format that the ipod video player is compatible with. I was using Super for that purpose for a long time which is a great converter, probably the best that is currently available for free. Super has the disadvantage that new users might be overwhelmed with all the options and I was looking for a easier solution to convert videos into a format that the ipod video player would be able to play

Karaoke and Karaoke software is becoming more and more popular since Sony decided to release the first Singstar Playstation 2 Karaoke game. Even friends who never heard of the Playstation 2 before were fascinated by those Karaoke games and some even bought a Playstation 2 only for those games. In case you did not know, Karaoke means that someone sings the song while only the instruments play in the background. This is tremendous fun especially in conjunction with cold beer.

Rootkits received a publicity boost with Sony's rootkit infested CDs that was supposed to be some kind of copy protection. Since then rootkits have become an ever growing threat on the Internet in line with Viruses, Trojans, Phishing and Spam. The major problem with rootkits is that most users think that their virus scanner protects them from rootkits as well which is most of the time not the case. Rootkits are much harder to detect by normal means and software that can scan systems for rootkits should be used by inexperienced users to be able to detect at least the most common ones.
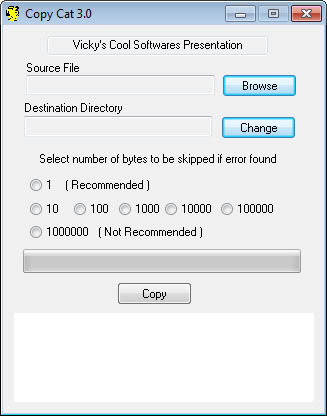
About eight years ago I was backing up some pretty valuable files on CD. I should add valuable to me. One Cd contained demos of me and my clan playing Unreal Tournament capture the flag and I've always seen this as a part of my history. Well, I tried to copy the CD to my hard drive a few days ago and guess what; Some files could not be read and I lost some of them during the process. At least that's what I thought until I found the freeware Copy Cat. Copy Cat uses a superior method to copy files by using a byte per byte method.

One of the many disadvantages of every new Windows edition is the fact that the operating system becomes more and more bloated. Microsoft adds new features to Windows which could then be used to exploit the system.Instead of concentrating on fast efficient systems they produce heavy systems that look shiny but have problems under the surface. Recently a vulnerability in Windows Animated Cursor Handling was discovered. In order for this attack to be carried out, a user must either visit a Web site that contains a Web page that is used to exploit the vulnerability or view a specially crafted e-mail message or email attachment sent to them by an attacker.
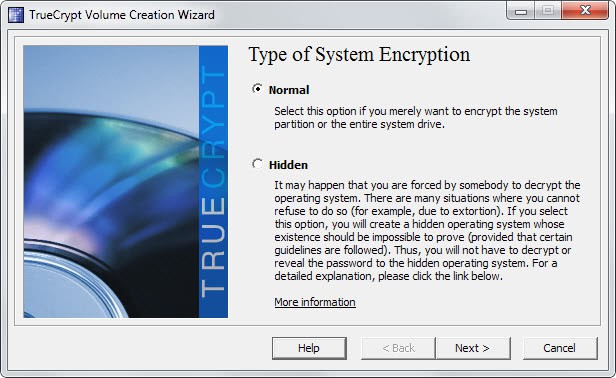
This article is going to show everyone, even the inexperienced, how to create a data safe that can store as much personal information and files as you want using the open source program True Crypt. True Crypt makes it very easy to encrypt almost every piece of hardware including partitions, hard drives, usb keys and other storage devices. Once everything is setup you would mount the True Crypt container using the password that you have selected while creating the encrypted container. This is actually the only password that you have to remember, everything else can be kept in the encrypted container for safety reasons.

I came upon the article "How I would hack your weak passwords" yesterday and pondered if I should write an article about it. I decided that it would be worth it. The author of the article details how he would try and find out your passwords and get access to all of your accounts in the end. His first approach would be to use the most common used passwords by users on the net. He needs information about your personal life for some passwords but those information can be obtained pretty fast through social engineering. Trying those "top 10" passwords would already cover a large percentage of online users, statistically speaking that is.
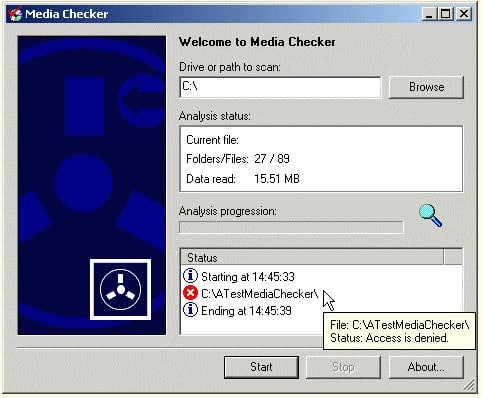
Nothing is more frustrating than to realize that some files of a backup are corrupted. This happens of course right at the time when you need the backup. One way to prevent this scenario from happening would be to use different locations for your backups, for example CDs, external hard drives and USB drives. Even though you store the backup in different places it is not guaranteed that the files on those devices are not corrupted. The probability that it will happen is simply reduced.
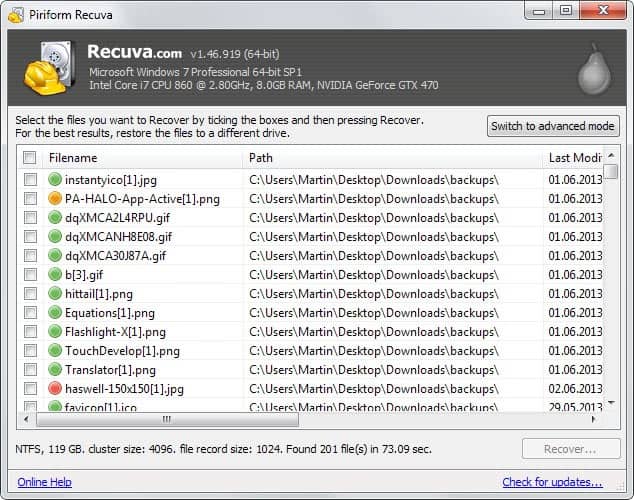
I disabled my trashbin by default which means that deleted items bypass the trashbin and are deleted immediately. This works fine most of the time but it happens that I occasionally delete a file that I need later on again. There is no obvious way to get those files back and you will face serious troubles if want to get them back but used something like defragmentation on that hard drive after the deletion.
The question that some might ask is why one could recover deleted files at all. This is actually a very good question. Windows does not delete the file at all when you press the delete button. It simply deleted the reference to that file and makes the space the file occupied writable again. This means that you can recover most files if you are just fast enough. One freeware that can do the job is Recuva which is supposed to be pronounced recover.
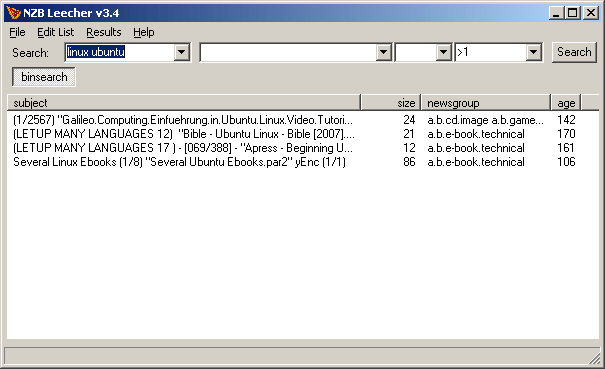
Newsgroup indexing sites such as binsearch.info and binaries.nl make it easier to search for files that have been posted to the Usenet by allowing searches in all groups. If you are familiar with the Usenet you might know that you can only search one group at a time which does not help much if you do not know if the file(s) that you are looking for have been posted in that group.

Using p2p networks such as Emule or Bittorrent to download mp3 files is not as dangerous as the Music Industry tries to make it appear but there is still the chance that you might face consequences if you share copyrighted music. A much easier and safer way would be to simply use Google to find and download the music that you like. The Music Industry somehow does not seem to care that Google indexes more copyrighted mp3 files than the total number that is available on all p2p networks combined.
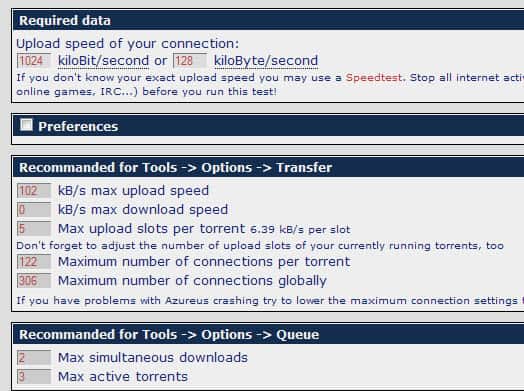
If you search the internet for tips to improve your download speeds with bittorrent clients such as Azureus and uTorrent you do find many tips that have one thing in common, all suggest different settings for maximum performance. There are several things that can influence download speeds in bittorrent including bad Seeds to Peer ratio and firewall settings. I would only change settings in my bittorrent client if I thought that my download speeds would be really bad, say 2K with a torrent that has 10+ seeders.

Version tracking is extremely useful if you work with files that change very often. This is mostly interesting for coders and website owners but also for users who write large text files and artists that work with graphics or music for instance. In short; File Hamster keeps backups of all old versions of files that you specify making it incredibly easy to revert back to a previous version or take a look at the changes between different versions.

You can use iTunes to copy to your iPod but not to copy them back to your hard drive. I don't know if this has been intentional to please the Music Industry but I doubt it was just an error that could not be corrected in later revisions of iTunes. You have to look elsewhere if you want to copy songs from the iPod to a hard drive again, lucky for us tools that can do this exist and are free to download and use.

Pando is a free online service that utilizes p2p technology to share large encrypted files by email and instant messenger. The sender selects files and folders that he wants to share. Those files are immediately uploaded to the Pando server where they are stored in encrypted form. The recipient receives an email that contains a small attachment which starts the download process when executed. Data will be send from the Pando server and other users who are currently online.

You might have come upon this problem during scans for viruses and Trojans on your system. A malicious file was identified by your favorite virus scanner and it prompts for action. You can delete, move, rename or move the file into quarantine. It is however not possible to delete malicious files when you choose to delete them because they are currently in use and can't be therefor deleted.
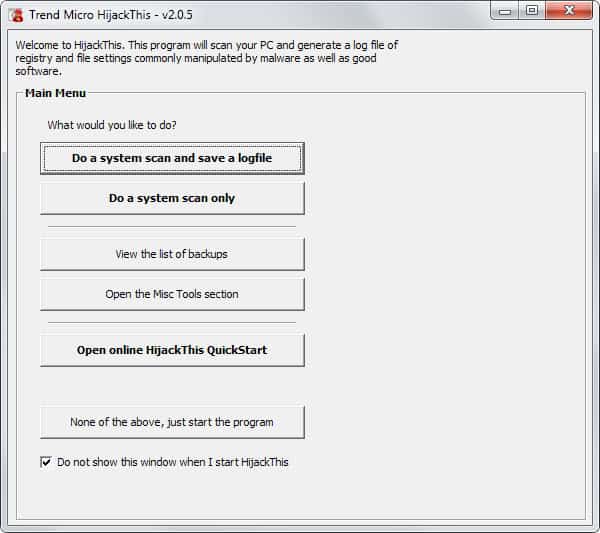
HiJack This is a very sophisticated security analyzer that generates an advanced report of various registry settings and files in your computer. The difference to many other security analyzers such as trojan scanners is that Hijack This makes not difference between "good" and "bad" settings but displays everything that it founds in its security log. It is then up to the user to find potentially harmful files and settings and remove them from his computer.

I was not really sure how to name the title of this article. Jocr is a freeware that makes it possible to capture to capture a set region, a window or a full screen image in Windows and use character recognition to write the text of the image into a notepad file. The only prerequisite as far as I can tell is - unfortunately - a copy of Microsoft Office 2003 or newer with Microsoft Office Document Imaging installed which you can find under the Office Tools tab of the installation CD. The language that you are using has to be supported by Microsoft Office Document Imaging, about 20 are supported next to English of course.

It is very convenient to save login passwords for internet sites such as forums, blogs or paysites to login quicker to those websites. That is, it is great until you can't remember the password anymore but would like to know it again. This could be the case if you want to switch from Internet Explorer to Firefox or Opera for instance. Protected Storage Pass View does not only reveal passwords that have been saved in Internet Explorer while accessing protected sites or using the auto complete form but also passwords that have been saved in Outlook Express and MSN Explorer.

Most versions of Windows Vista ship with Windows Aero which offers a function called Windows Flip 3D which makes it possible to organize and use Windows in a 3D environment. The main advantage of this method is that it is possible to display more content on the same amount of desktop space which makes it much easier to keep an overview over all windows that are currently open and not minimized.
Most people don't ever think that it is possible that free and legal torrent websites exist, they automatically assume that torrents equal illegality. The list of then free and legal torrent sites proves this assumption wrong. NewTeeVee did a great job of compiling the list which is just a tiny fraction of the whole torrent scene. I still think that it is a good beginning to show others who do not know that much about bittorrent that there are indeed legal applications.

A new kind of Trojan was discovered recently which targets only Japanese file-sharers. When executed the Trojan displays manga-like images with a reminder which differs depending on which image is displayed. The text however looks similar and always asks the user to stop using P2P networks. One of the messages for instance reads ""Ah, I see you are using P2P again...if you don't stop in 0.5 seconds, I'm going to kill you." Talk about a threat boy, jeeze."
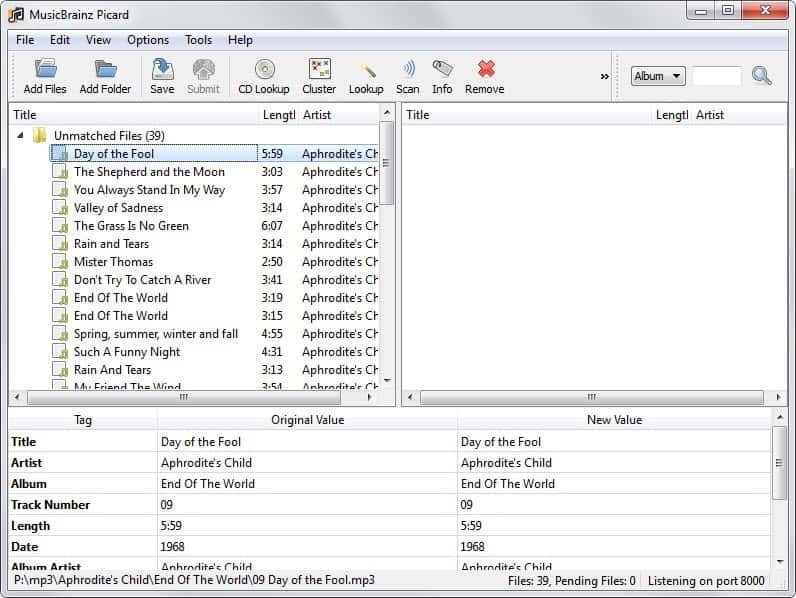
Music collections are usually a big pile of messy filenames and folders that have artist, album and song names mixed up. Some files do have mp3 tags, some don't and it would take a long time to go through your music collection manually and edit the mp3 tags. I literally tried and tested a dozen mp3 tagger before I came up with the best solution that would be the most precise and at the same time most automatic way of tagging my mp3 files.

The Free Ipod Video converter is a very easy and reliable program to batch convert videos into a format that all video iPods can play. The process of adding files is always the same. You add files by selecting them from your hard drive, the free iPod video converter will display information about the file first and let you choose some settings in the next window. You may change the output filename and the video and audio quality.
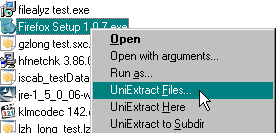
If you ever wanted to have a free software that would be able to handle all the different zip formats then you might want to take a look at the open source program called Universal Extractor. Universal Extractor can only be used to extract archives handling this task excellently. It supports a multitude of zip formats including the following popular ones: 7-zip archive, ace archive, arj, gzip, rar, tar and zip archives.

There has been a lot of controversy about the recent acquisition of uTorrent by Bram Cohen, the creator of the Bittorent protocol. Most users seem to be disturbed about the partnership between Bittorrent and the MPAA which started in fall 2005 with the agreement that illegal searches would be removed from its own Bittorrent search engine. The fear that the cooperation will affect the development of the popular uTorrent client seems to grow with every passing day.

Didier Stevens did it again with a pretty useful tool that could be used for backups that should be placed on another server on the internet. This is great if you want to separate site or operating system backups from the running server to avoid that both are not recoverable after a crash.
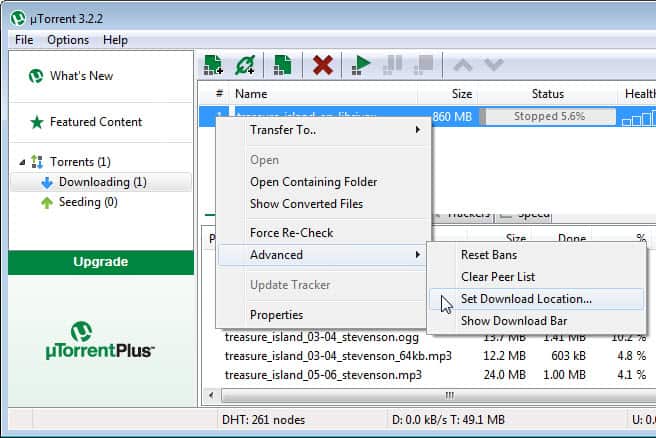
I'm so glad that I made the change from bitcomet to uTorrent some time ago because uTorrent is by far the most efficient bittorrent client that I could get my fingers on until now. I receive great speeds, it does not use many resources on my computer, heck the client is only 173 KB in size.

20 minutes to increase the security of a computer, wow that must be a good guide. The guys at itsecurity have written a security guide that indeed covers the basics of PC security. I do know from first hand experience that many users do not follow simple PC security guidelines, e.g. they probably have a anti-virus solution but never update it.
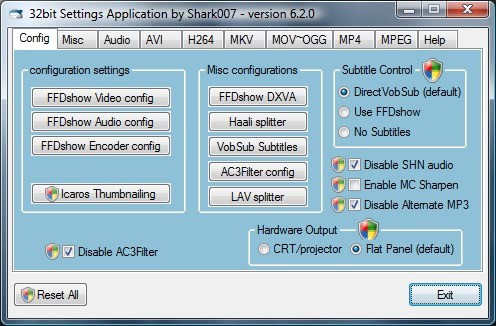
I'm normally not a friend of codec packs because they tend to install many codecs that are not needed on most systems and could pose compatibility problems with codecs already installed on the system. Windows Vista on the other hand misses some essential codecs that can be quite easily added with the Vista Codec Package which can be customized during installation. That is right, unlike other codec packages you can select to install all or only some of the codecs offered.

You all know that you can run virtual operating systems using vmware. VirtualBox is a free open source alternative to vmware which currently runs on 32-bit versions of Windows and Linux and supports the following guest systems: FreeBSD, OpenBSD, Linux 2.4 / 2.6, Windows NT 4.0, Windows 2000, Windows XP, Windows Server 2003 and Windows Vista.

If you use the Windows Vista Media Center you might have noticed that playback for various formats is not supported by default. You can't playback divx, xvid or h.264 movies or play mp3 or aac files by default which is really annoying if you want or have to use the media center.

Floola is a multi-platform freeware replacement for iTunes which adds some much needed features that iTunes does not offer. Before you can use Floola you need to prepare your iPod and enable it to work as a portable hard drive. A good walkthrough of the different steps can be found at the official Apple website. When that is done you need to configure iTunes to manages songs and playlists manually.
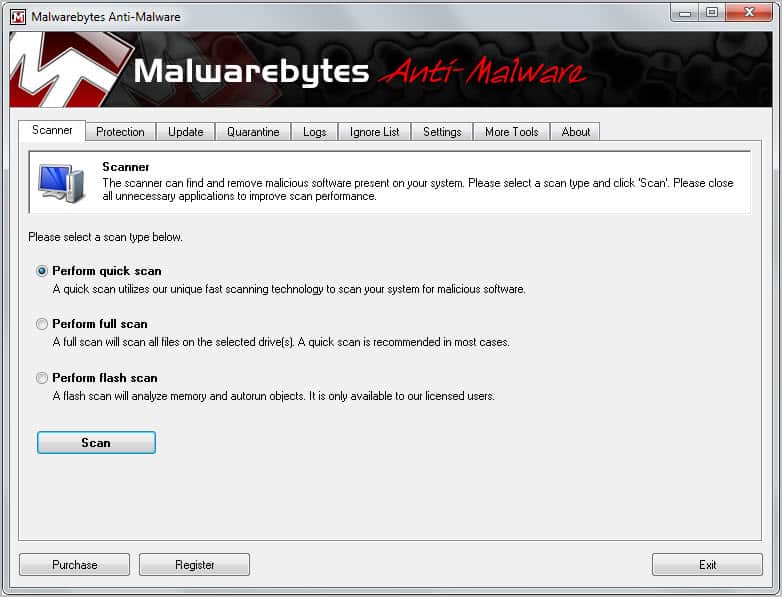
We all known that quite a few spammers make big bucks by offering software like antivirus, antispyware or hard drive utilities whose main function is to either spy on the user or spam him. Those products are quite common nowadays and it is difficulty for an inexperienced user to remove the software completely again.
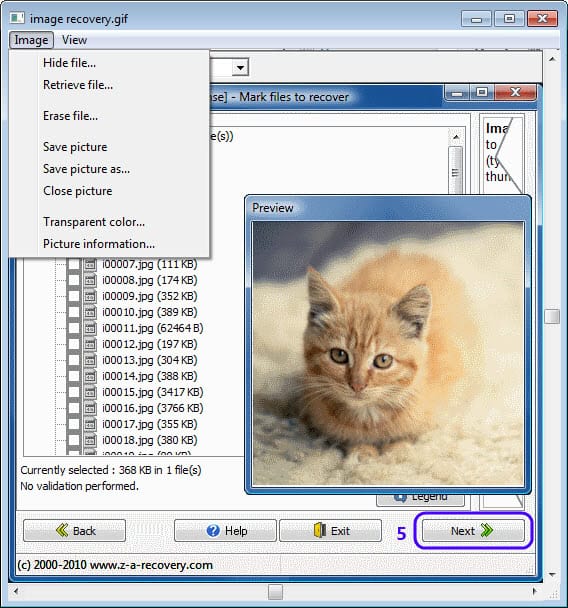
I never was a great fan of programs that would hide files or information but I can see that some people might find this kind of tools useful. I can think of several reasons why someone would want to hide files in pictures; maybe it is because a file needs to be sent by email and no one that would intercept the email would find the file or a way to bypass a filter easily.
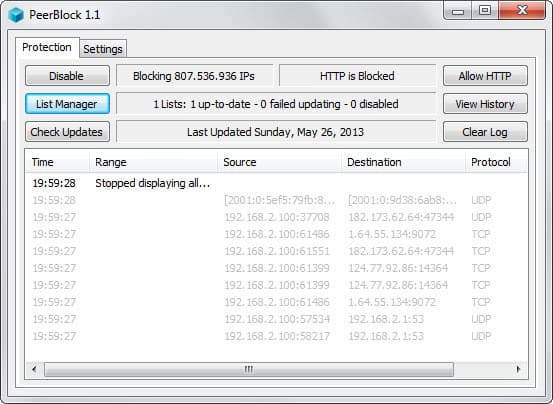
Why would you need another program to block IP addresses if you already have a firewall ? A good question that can be answered easily. Peer Guardian uses a database of bad IP addresses and blocks them automatically as soon as the IP is added to the database of blocklist.org. A single user would have to know that a new IP (range) poses a thread and add it manually to his firewall.

Fake torrents are spread into the system by organizations for two reasons. The first and in my opinion dominant one is to unsettle the torrent users by lowering the rate of successful downloads. Nothing is more discouraging than downloading the latest blockbuster for days only to see that you downloaded only garbarge in that time. In addition to this the trackers that spread the fake torrents are recording every bit of information they can get their hands on.
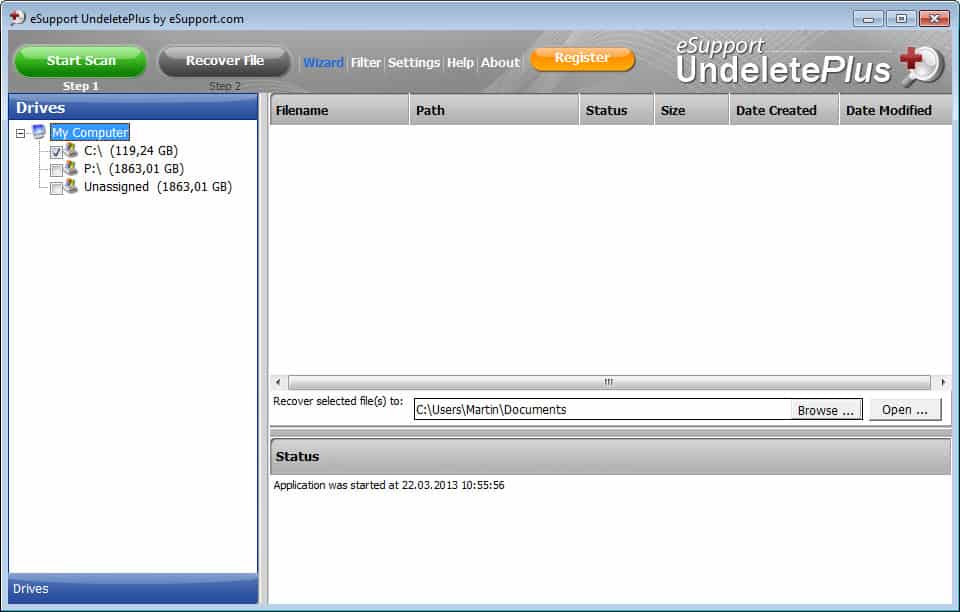
I delete files most of the time by pressing down the shift key which will delete them immediately without moving them to the trashbin first. It happens from time to time that I deleted a file that I want to recover, sometimes it is because another file depents on the deleted one or it could be that I need to access the information again that was contained in the file. There is unfortunately no direct way to recover the files in windows which means that we have to rely on third party tools to recover lost files.

Not many free or open source video editing software suits exist and many people rely on commercial programs like Adobe Premiere to transfer videos from a camcorder for instance and edit / convert the video. Jahshaka is a open source video editing program that offers its users a huge functionality that can almost be compared to those commercial programs.

USB Virus Scan is a nice little command line utility that performs predefined operations if a usb drive is connected to your computer. It is able to distinguish between various drives which means that you can add custom operations for the drives that you own and a general option for drives that are not recognized. The tool uses the volume serial number of the drives to identify them and perform the operation.