The Windows December 2023 security updates fix a 0-day vulnerability

Microsoft released security updates for all supported Windows operating systems and other company products on the December 2023 Patch Day. The company fixed 36 unique Microsoft product vulnerabilities and six non Microsoft product vulnerabilities on the last Patch Day of the year 2023.
It is a smaller Patch Day that fixes three critical security issues in all supported Windows client and server products. The update fixes one publicly disclosed 0-day vulnerability. Listed as CVE-2023-20588, it affects devices with AMD processors only.
Our overview is designed to be a resource for system administrators and home users alike. It includes information about all major security updates that Microsoft released. You find links to support pages and resources, the list of known issues, direct download links and more listed below.
Check out the November 2023 Security update overview here.
Microsoft Windows Security Updates: December 2023
Here is a link to an Excel spreadsheet that lists information about the released security updates on the December 2023 Microsoft Patch Day. Follow this link to download an archive file that contains the spreadsheet: Microsoft Windows security updates December 2023
Executive Summary
- Windows 11 version 21H2 is no longer supported. Upgrades to Windows 11 version 22H2 are available.
- Windows Copilot is now available on Windows 10 devices. Microsoft's March 2023 announced change to app pinning and app defaults is now in effect. It applies to Microsoft apps and third-party apps, according to the company.
- Windows clients with issues are: Windows 10 version 1809, Windows 10 version 21H2 and 22H2, Windows 11 version 21H2, 22H2 and 23H2
- Windows Server clients: Windows Server 2008 and 2008 R2, Windows Server 2019
Each supported version of Windows and their critical vulnerabilities are listed below.
- Windows 10 version 22H2: 15 vulnerabilities, 3 critical and 12 important.
- Internet Connection Sharing (ICS) Remote Code Execution Vulnerability -- CVE-2023-35630
- Windows MSHTML Platform Remote Code Execution Vulnerability -- CVE-2023-35628
- Internet Connection Sharing (ICS) Remote Code Execution Vulnerability -- CVE-2023-35641
- Windows 11 version 22H2: 17 vulnerabilities, 3 critical and 14 important
- same as Windows 10 version 22H2
- Windows 11 version 23H2: 18 vulnerabilities, 3 critical and 15 important
- same as Windows 10 version 22H2
Windows Server products
- Windows Server 2008 R2 (extended support only): 15 vulnerabilities: 3 critical and 12 important
- Internet Connection Sharing (ICS) Remote Code Execution Vulnerability -- CVE-2023-35630
- Windows MSHTML Platform Remote Code Execution Vulnerability -- CVE-2023-35628
- Internet Connection Sharing (ICS) Remote Code Execution Vulnerability -- CVE-2023-35641
- Windows Server 2012 R2 (extended support only): 61 vulnerabilities: 11 critical and 50 important
- Not published (yet)
- Windows Server 2016: 17 vulnerabilities: 3 critical and 14 important
- same as Windows Server 2008 R2
- Windows Server 2019: 19 vulnerabilities: 3 critical and 16 important
- same as Windows Server 2008 R2
- Windows Server 2022: 18 vulnerabilities: 3 critical and 15 important.
- same as Windows Server 2008 R2
Windows Security Updates
Windows 10 version 22H2
- Support Page: KB5033372
Updates and improvements:
- Security updates.
- Includes all non-security changes of the November 30, 2023 preview update for the operating system.
Windows 11 version 22H2 and 23H2
- Support Page: KB5033375
Updates and improvements:
- This update makes miscellaneous [unspecified] security improvements to internal OS functionality.
- Includes all non-security updates of the December 2023 Preview Update, including:
- Support for multiple displays when using Copilot in Windows (even though issues on multi-monitor systems is still listed as a known issue).
- Alt-Tab supports Copilot in Windows now.
- Windows Spotlight will become the default background on Windows to replace the inbox Windows image.
- Account-related notifications will display in Settings > Home after the update.
Security updates
2023-12 Cumulative Update for Windows 10 Version 1507 (KB5033379)
2023-12 Cumulative Update for Windows 10 Version 1607 (KB5033373)
2023-12 Cumulative Update for Windows 10 Version 1809 (KB5033371)
2023-12 Cumulative Update for Microsoft server operating system version 21H2 for x64-based Systems (KB5033118)
2023-12 Cumulative Update for Windows 10 Version 22H2 and Windows 10 Version 21H2 (KB5033372)
2023-12 Cumulative Update for Windows 11 (KB5033369)
2023-12 Servicing Stack Update for Windows Server 2008 (KB5033466)
Windows Server
2023-12 Cumulative Security Update for Internet Explorer Windows Server 2012 R2, Windows Server 2012, Windows Embedded Standard 7, Windows Server 2008 R2, and Windows Server 2008 (KB5033376)
2023-12 Security Only Quality Update for Windows Embedded Standard 7 and Windows Server 2008 R2 (KB5033424)
2023-12 Security Monthly Quality Rollup for Windows Embedded Standard 7 and Windows Server 2008 R2 (KB5033433)
2023-12 Security Monthly Quality Rollup for Windows Server 2008 (KB5033422)
2023-12 Security Only Quality Update for Windows Server 2008 (KB5033427)
2023-12 Security Monthly Quality Rollup for Windows Server 2012 R2 (KB5033420)
2023-12 Security Monthly Quality Rollup for Windows Server 2012 (KB5033429)
2023-12 Cumulative security Hotpatch for Azure Stack HCI, version 21H2 and Windows Server 2022 Datacenter: Azure Edition for x64-based Systems (KB5033464)
Non-Security updates
None listed
Known Issues
Windows 10 version 22H2
Description: Desktop icons may be moved around unexpectedly between monitors when using Copilot on more than one monitor. Users may also experience "other alignment issues" according to Microsoft.
Workaround: none. Microsoft may disable Copilot on multimonitor devices.
Description: Copilot in Windows is not supported if the taskbar is located vertically on the right or left side of the screen.
Workaround: align the taskbar horizontally, either at the top or bottom of the screen.
(OLD) Description: Using the FixedDrivesEncryptionType or SystemDrivesEncryptionType policy settings in the BitLocker configuration service provider (CSP) node in mobile device management (MDM) apps might incorrectly show a 65000 error in the "Require Device Encryption" setting for some devices in your environment.
Workaround: this is a reporting issue only according to Microsoft. Microsoft suggests to set the "Enforce drive encryption type on operating system drives" or the "Enforce drive encryption on fixed drives" policies to not configured as a workaround.
Windows 11 version 22H2 and 23H2
Description: Microsoft Narrator may not start when installing Windows 11 from physical media or disk images.
Workaround: Microsoft is working on a resolution.
(OLD) Description: Users who use multiple monitors on their Windows devices may notice that desktop icons move around unexpectedly. They may, for instance, move between monitors.
Workaround: Microsoft "may" have disabled Windows Copilot on multi-monitor devices until a solution is found.
(OLD) Description: The color font format COLRv1 does not render properly. It is used to display emoji with a 3D-like appearance.
Workaround: none at the time. Microsoft is working on a solution.
(OLD) Description: Using the FixedDrivesEncryptionType or SystemDrivesEncryptionType policy settings in the BitLocker configuration service provider (CSP) node in mobile device management (MDM) apps might incorrectly show a 65000 error in the "Require Device Encryption" setting for some devices in your environment.
Workaround: this is a reporting issue only according to Microsoft. Microsoft suggests to set the "Enforce drive encryption type on operating system drives" or the "Enforce drive encryption on fixed drives" policies to not configured as a workaround.
Security advisories and updates
- ADV 990001 -- Latest Servicing Stack Updates
Microsoft Office Updates
You find Office update information here.
How to download and install the December 2023 security updates
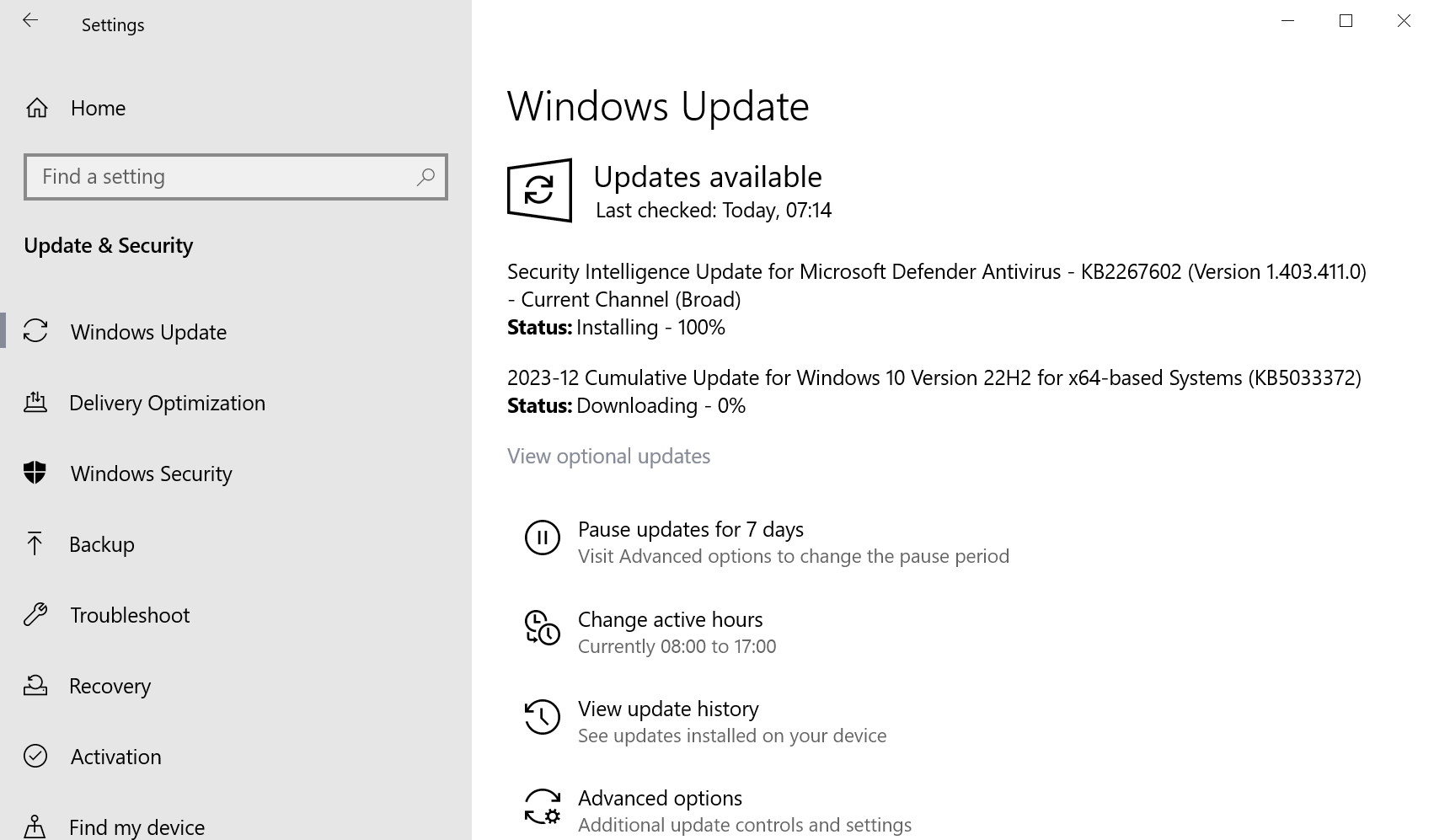
Security updates roll out to all non-managed Windows devices automatically by default. This process may take a while to reach all devices. Administrators may download the updates as soon as they are released, either via Windows Update or by downloading the updates manually.
Tip: create a backup before you install updates
To update using Windows Update, use the following guide:
- Select Start, type Windows Update and load the Windows Update item that is displayed.
- Select check for updates to run a manual check for updates.
Managed systems receive updates when system administrators allow them to be distributed to managed devices.
Direct update downloads
Below are resource pages with direct download links, if you prefer to download the updates to install them manually.
Windows 10 version 22H2
- KB5033372 -- 2023-12 Cumulative Update for Windows 10 Version 21H2
Windows 11 version 22H2
- KB5033375 -- 2023-12 Cumulative Update for Windows 11 version 22H2
- KB5033375 -- 2023-12 Cumulative Update for Windows 11 version 23H2
Additional resources
- December 2023 Security Updates release notes
- List of software updates for Microsoft products
- List of the latest Windows Updates and Services Packs
- Security Updates Guide
- Microsoft Update Catalog site
- Our in-depth Windows update guide
- How to install optional updates on Windows 10
- Windows 11 Update History
- Windows 10 Update History



















@Martin
Edge stable just updated and I found this “take screenshots for history” (super invasive spying feature) has been added to edge.
I can not turn it off. There’s a button to do so but it’s stuck on and doesn’t work.
The most confusing part of Windows Updates, is that in Hindi 100% apparently means 50%.
I wish “SECURITY” updates were only just that.
This dishonest bullshit needs to stop.
I had to do a system restore after the last ‘security’ update because the crap that it tried to add broke my start menu. So I doubt I can install this one without making my pc useless either :(
Exactly…
Security updates are important but they are also the mechanism tech companies use to convince users to allow unverified code into their environments.
If these companies were serious about security, there would be a separate security only update channel that did not push any new features and would have the specific CVEs listed before automated download so the user could verify what is involved before being forced to install.
It’s not a zero-day.
Mr. B, underneath your link to the November updates your header for the December updates reads:
Microsoft Windows Security Updates: November 2023
You may wish to correct this to avoid confusion.
Be well-
oh, and have a Merry Xmas and Happy New Year!
Ed
Thank you, copy and paste error ;)
Merry Christmas and Happy New Year to you as well.