A relatively new ransomware group has put all Sony data up for sale

A relatively new ransomware group known as Ransomed.vc has claimed to have executed a potentially devastating ransomware attack against the global entertainment giant, Sony. Despite being in operation for a short time since September, this group has managed to amass a significant number of victims, with Sony being one of their high-profile targets.
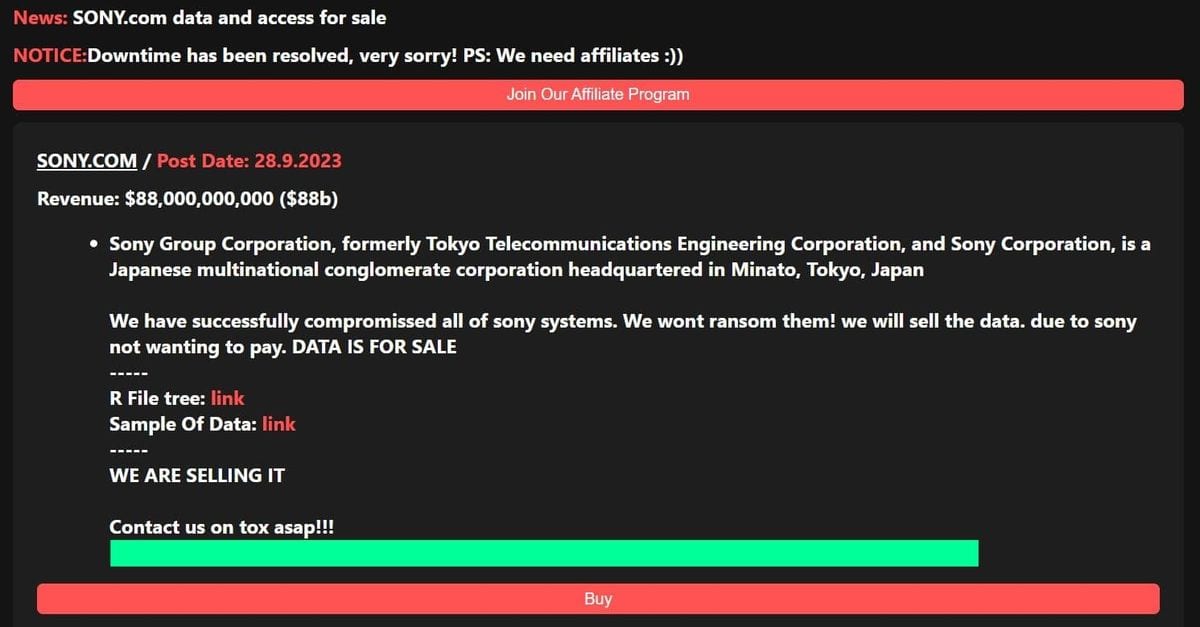
Ransomed.vc, in its statement on both clear and dark net platforms, described Sony Group Corporation as a Japanese multinational conglomerate headquartered in Minato, Tokyo, Japan. They boldly asserted that they had successfully compromised all of Sony's systems and revealed their intention not to ransom the data but to sell it due to Sony's reluctance to pay.
So is PlayStation hacked? According to Ransomed.vc, yes it is and the group emphasized that they were actively selling the stolen data before their X account was taken down.
How was PlayStation hacked?
While Ransomed.vc provided some proof of PlayStation hacked data, it appeared less substantial, consisting mainly of screenshots of internal login pages, an internal PowerPoint presentation outlining testbench details, and various Java files.
They also posted a file tree of the leaked data, which seemed relatively small given the claim of compromising "all of Sony systems," containing build log files, Java resources, and HTML files.
Interestingly, Ransomed.vc did not specify a price for the data but provided contact details for the Tox messaging service, Telegram, and email. They also indicated a "post date" of September 28, 2023, suggesting that they might publish the data wholesale if no one purchases it.

How Sony hack 2023 was met?
As of now, Sony has not officially acknowledged the alleged hack on its websites, and inquiries have been made for confirmation of any cyber incident.
Read also: Duolingo data breach exposes data of 2.6 million users.
Ransomed.vc appears to operate both as a ransomware operator and a ransomware-as-a-service organization, actively seeking "affiliates" to join their ranks. Furthermore, they claim to adhere to strict compliance with GDPR and Data Privacy Laws and vow to report violations to the GDPR agency when payment is not received, setting them apart from other ransomware groups.
The vx-underground X account, which has been analyzing malware source codes for years, shared the following about the case:
Because nerds keep asking us about alleged Sony ransomware incident
tl;dr Threat Actors did not deploy ransomware, no corporate data was stolen, services not impacted. Data was exfiltrated from Jenkins, SVN, SonarQube, and Creator Cloud Development. They're extorting Sony
— vx-underground (@vxunderground) September 25, 2023
Featured image credit: Sony.
Advertisement


















