Ransomware payments are marginal when compared to the overall costs
Ransomware payments by organizations made up about a seventh of the overall costs of ransomware attacks in 2020 according to a new study by Check Point Research and Kovrr. While ransom payments make up about a seventh of the total costs for the attacked organizations, expenses such as response and restoration expenses, legal fees, or monitoring costs, make up the bulk of the total expenses for organizations.

Most ransomware attacks are designed to encrypt data on organization devices after successful breaches; the attackers use the encrypted data as a bargaining chip, but may also threaten to leak data that was dumped during the attack to pressure organizations into giving in to ransom demands.
Check Point Research saw an increase in ransomware attacks by 24% year-over-year globally, with 1-in-53 organizations suffering a ransomware attack on average. Ransomware gangs and operations have evolved, and gangs are establishing structures and policies that resemble those of legitimate organizations.
The duration of ransomware attacks went down as a result of the professionalization of ransomware gangs and improved response processes on the victim's side. At its peak, ransomware attacks lasted for an average of 15 days according to Check Point Research. The number of days dropped to an average of 9.9 days in 2021, and the researchers believe that structural changes in ransomware organizations and improved processes in legitimate organizations play a role in this.
Tip: Windows users may enable ransomware protection on Windows 10 and 11.
Ransom demands and how they are calculated
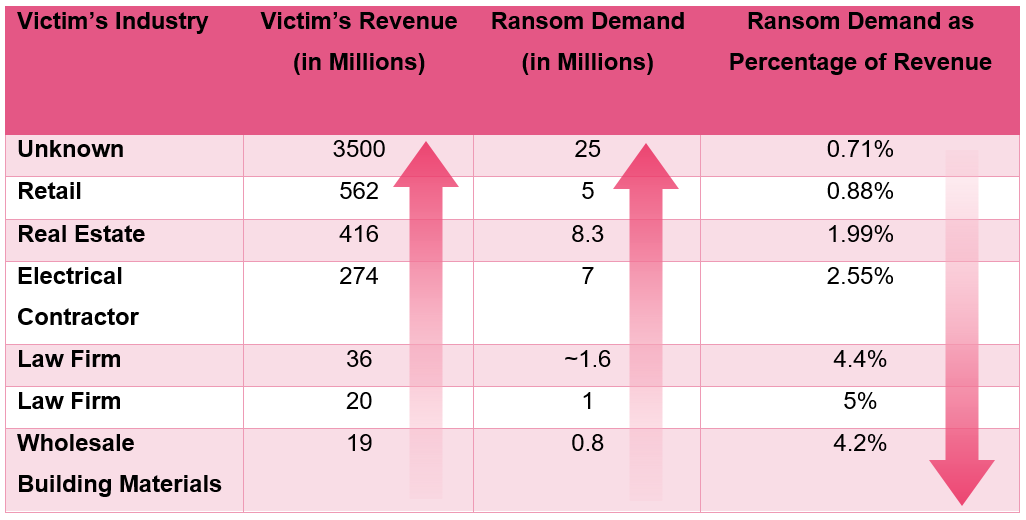
Ransomware gangs use research, that is very similar to the research of financial analysts, to determine the ransom. Research looks at the annual revenue of organizations, the industry, and other parameters to come up with a number.
Analysis of Conti Group activity, a ransomware group that has been in operation since 2020 at the least, revealed an average demand of 2.82% of an organization's annual revenue. Individual percentages of revenue ranged from 0.71% to 5% in the analyzed data set.
The requested percentage decreased, the higher the annual revenue of the organization was. Check Point Research explains that lower percentages still led to higher payments, because of the organization's higher annual revenue.
Ransomware negotiations
Check Point Research identified five major steps in the ransomware negotiation process:
- Finding leverage. Ransomware gangs are interested in completing transactions quickly. They will analyze the stolen data to find leverage that they may use in negotiations with company representatives. They attempt to find the "most sensitive files" for use as leverage. Groups may publish files on private sites and threaten to make the data public if the ransom is not payed by the organization.
- Discounts for quick payments. Ransomware gangs may give organizations a discount if they pay in the first couple of days after the attack hit the organization's infrastructure. The Conti group offered discounts between 20% to 25% of the ransom in those cases.
- Negotiations. Some organizations hire third-party negotiations to act on their behalf. At this stage, organizations may attempt to reduce the ransom demand further, or provide explanations why payments take longer than expected.
- More threats and last chance to come to an agreement. Groups may upload more data on that they have stolen to private sites at this point to put additional pressure on the organization.
- Agreement or the dumping of data. The final stage of the negotiations has one of two outcomes: both parties agree on a ransom, which is then paid, or the data may be leaked to the public if both parties do not come to an agreement.
Established ransomware gangs depend on their reputation. Not handing out the decryption keys after ransom has been paid could impact future negotiations severely.
The financial impact of ransomware attacks
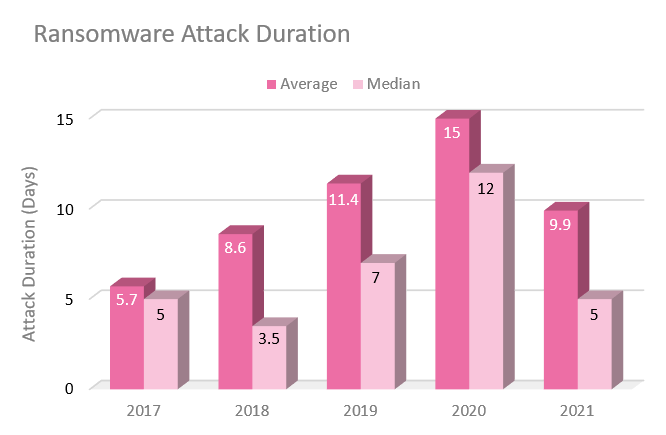
Victims of ransomware attacks are often unaware of the costs associated with ransomware attacks. The duration of ransomware attacks may have serious impact on an organization's capabilities to operate its business.
The encryption of key servers, databases or employee endpoints may result in a slow down or standstill of operations. Toyota had to halt production in some of its facilities after a successful ransomware attack in 2022.
The average and media ransomware attack duration decreased in 2021 for the first time since 2017. In 2020, average and median attack lasted for 15 and 12 days; the numbers dropped to 9.9 and 5 days in 2021.
Check Point Research suggests that the peak in 2020 was caused by a rise in double-extortion attacks in 2020, which "caught organizations off guard and resulted int long negotiations between attackers and victims". Organizations "established better response plans to mitigate ransomware events" to better react to double-extortion attacks, and this resulted in decreased attack durations.
Negotiations may reduce the actual ransom payment significantly. In 2021, the ratio of average extortion payments to extortion demands was 0.486. Victims paid less than half of the requested ransom on average in 2021.
The number was higher in 2019, when it was 0.889, and lower in 2020, when it was at 0.273. Explanations for the dropping since 2019 include the implementation of effective ransomware response plans in many organizations, which often include professional payment negotiations.
The researchers suggest that the ratio increase between 2020 and 2021 is a direct result of professionalization of ransomware groups. Groups "have become more efficient at calculating their extortion demands".
Breakdown of costs
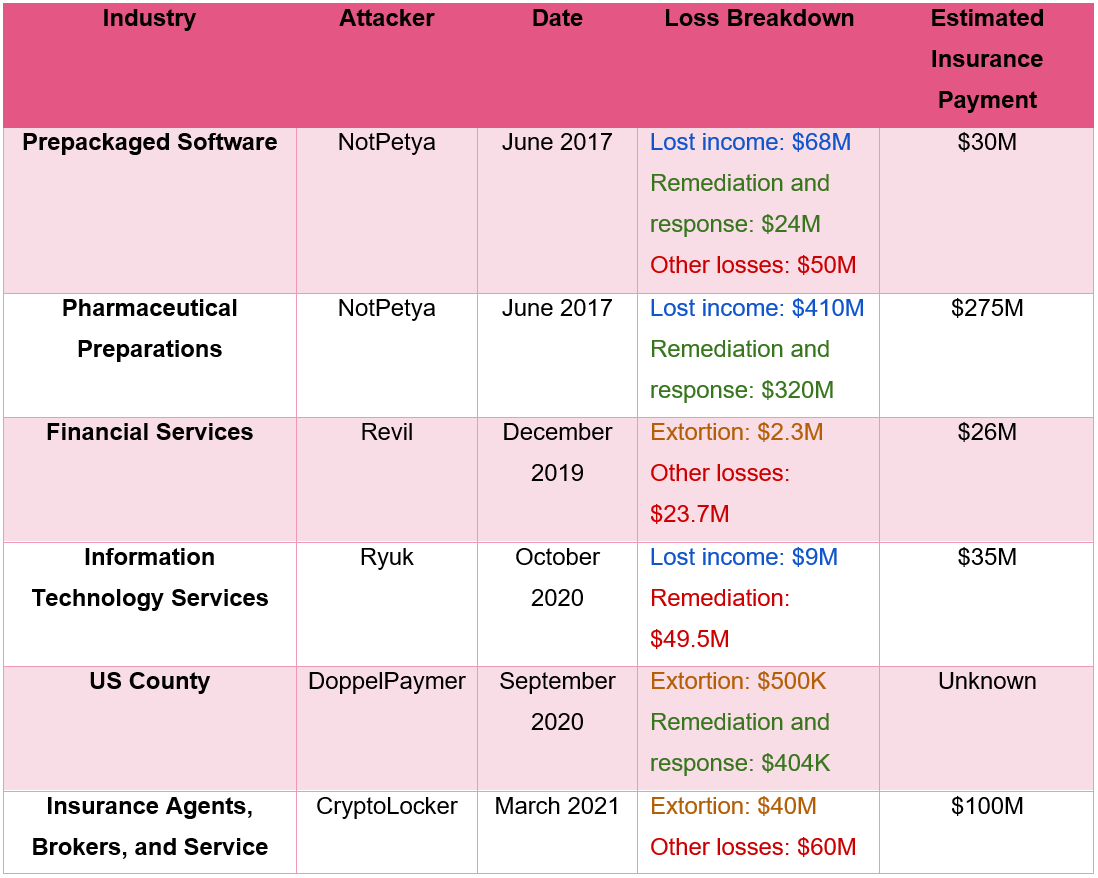
The financial impact of ransomware attacks consists of several components. The ransom that is paid, "response and restoration costs, legal fees, monitoring and additional costs". The majority of costs apply regardless of whether the ransom is paid by the organization.
Organizations may lose income during the attack and after it has ended, as core systems and processes may not be accessible. The ratio of total attack costs to extortion payments rose from 3.463 in 2019 to 7.083 in 2020. Ransom demands made up a little bit more than 15% of all expenses associated with ransomware attacks in 2020 on average; this is a huge increase in costs.
The researchers did not include data from 2021, as it was not complete at this point. They explain that there are delays between when ransomware attacks occur and the reporting of the attacks. Additionally, it may take time to calculate costs caused by the attack, as factors such as long-term reputational damage or legal costs may take time to be factored in.
Now you: have you experienced ransomware attacks on your devices or in your organization?



















We suffered terrible damage.
Although we cannot reveal the timing and circumstances of the incident, the cause of the breach was that some employees violated the bylaws on the system terminals (prohibiting the use of wireless runs and, prohibition of reuse of passwords) due to the “remote working” of the business.
Since this incident, we have strictly enforced internal regulations and have been able to prevent cyberattacks such as ransomware.
By the way,
After two years of thorough implementation of remote work for all employees at all offices and affiliated companies, the company concluded that the cost performance was too low for management due to deteriorating decision-making efficiency and the high costs associated with the enormous amount of terminals, and stopped remote work and returned to an attendance at work system (office work).
Because of remote work (unlike office work, which is well eyes, employees’ work at home cannot be thoroughly eyes), we were reminded of the threat of cyberattacks.
The attackers (Chinese military cyber-attack units) targeting huge enterprise are very sophisticated programs, enter through vulnerabilities like (that take advantage of the carelessness of Just a few employees) “A little leak will sink a great ship”, and spread to core servers and all terminals as in a zero-day attack, embedding special backdoors. Even initializing the system did not remove the malware.
But the lessons learned were “very basic”.
As stipulated in the “bylaws”, “do not use wireless LAN”, “do not reuse passwords”, and “ignore and delete unknown e-mails and attachments”.
The company’s terminals are all established in a system “built by the company’s systems department and handed directly to all employees without any third party”, which is different from the home-use system situation, but the lessons learned are “universal”.
Software vendors such as Microsoft and technology news sites such as gHacks Tech News tend to emphasize only the convenience of their applications, but Please do not fail to “remind” to use their applications.
End-users seem to be concerned only with those that cripple their systems or cause financial loss, such as ransomware, but many actual zero-day attacks and other attacks secretly penetrate systems and embed backdoors (of which the end-user is never aware).
At any rate, it is a matter of not neglecting to apply software updates (security patches) and actively ensuring the use and management of “Unique passwords”.
@Valrobex
you think most servers run om windows ?
think again
I’ve never experienced a ransomware attacks on any of my devices nor have I ever been aware of an organization I worked for having been such a victim.
What I’m sure of, as an individual, is how I’d deal with a ransomware attack : not one penny, computer to garbage, new device and restoration of data previously backed up on unconnected devices.
A word for those who practice ransomware, should any of them presently read : at least avoid the poor and the weak. Don’t attack hospitals, don’t attack non-profit organizations. There’s always been thieves but one can hope that, as in the past, some rob the wealthy “only”. Please keep that minimum humanity in your achievements.
The beat goes on.
A smile to end with : “Pay now and get 25% off” leads me to this state of mind where you’re tempted to laugh until you realize why you shouldn’t.
> Don’t attack hospitals, don’t attack non-profit organizations. There’s always been thieves but one can hope that, as in the past, some rob the wealthy “only”. Please keep that minimum humanity in your achievements.
I also, share the full text of @Tom Hawack’s statement.
But the goal of the bad guys is “money”. As the actions of Putin and the Russian military show, reason is lost for a purpose.
Hospitals and NGOs are extremely specialized and are not familiar with computers (cyber issues), which are merely tools, and are left to vendors, but even these are limited to their budgets (government-related terminals, which are also thoroughly budget constrained, are also inferior systems). In other words, these organizations are the perfect targets.
Ancient and modern saying: “There is no end to evil in the world”.
Even when “noble and well-intentioned” are put forth to the world, there are always those who harbor malicious intent to plot “unexpected outrages.”
There is no end to lies, and crime is no different.
There is no end to the struggle between good intentions and bad intentions.
We can’t expect to preach to the wicked, and it is more important to educate computer users and inspect them through third-party audits as a “minimum of common sense and responsibility”.
@owl, there is no end to virtue as well. Far more than plain rhetoric life shows, I’ll speak for myself : life has showed me, that no one is entirely bad (nor good) and that we all have (provided we are not insane) border lines within different levels of consciousness so to say. I continue to believe that ransomware attackers may have limits, at least for some of them. Who knows the debates going on within their communities? You must have as always some which have a more radical approach than others.
I could carry on with a questioning going around with some friends here : beyond virtue and vice could insanity be our civilization’s horizon? Is madness (in the clinical sens of the word) related to evil? Wide debate. If so, a mad, mad, mad world would be our world’s destiny. Mad, insane, not crazy. Not to mention that madness, with animals as well as with human beings, is the lot of the process of life which considers there is no exit.
@Tom Hawack,
I share your reply. I totally agree with you, and I am also a “Theory of Innate Goodness” value. However, “server attacks” that take advantage of vulnerabilities are a real and very serious problem.
Unless end-users change their perception, the damage will not stop, and they will continue to be taken advantage of.
https://www.ghacks.net/2022/04/28/ransomware-payments-are-marginal-when-compared-to-the-overall-costs/#comment-4520482
Vocabulary correction:
“server attacks” > “cyberattacks”
@ Tom Hawack,
You may never have been attacked by ransomware so far…
But after you switch to Win 11, as you’ve been contemplating, you better watch out!!!
@Valboorex, where did you get the idea I’d be or have been contemplating Win11?!
More important is the fact Win11 would be more inclined to ransomware attacks than its predecessors. That’d be a scoop for me as I thought that if there was only one true enhancement with Win10/11 it was that of security…
Ooops, I think I wrote with my memory, “Valborex” instead of “Valrobex” is it? :=)
Read you later alligator(s)!