Ransomware Study 2022: attacks are up, ransom payments are increasing
Ransomware attacks are increasing and getting more complex, according to the State of Ransomware 2022 report, which cybersecurity firm Sophos published. Companies are getting better at restoring data after attacks, but ransom payments have increased by 4.8 times when compared to the 2020 average.

Sophos commissioned the research agency Vanson Bourne to conduct an independent "vendor agnostic survey of 5600 IT professionals in mid-sized organizations" across 31 countries. The survey was conducted during January and February 2022, and the results of the survey have now been published in the State of Ransomware 2022 report.
Ransomware attacks on organizations rose to 66%, an increase of 29% compared to the 2020 attack rate. Organizations from Austria, Australia, Malaysia, India and Czech Republic experienced the highest average percentage of attacks, while organizations from South Afria, Brazil, Saudi Arabia, the UK, and US the lowest average percentage of attacks.
Sophos suggests that cybercriminal operations have been professionalized, a finding that Check Point Research's study on Ransomware suggests as well. Ransomware as a service, the use of ready-made ransomware packages, plays a role according to the report, as it reduces the skill level and financing required to run ransomware attacks.
Cybercriminals managed to encrypt data in 65% of all attacks, an increase by 11% over the 2020 success rate. Extortion-only attacks, attacks that do not encrypt data but use it for blackmail, have seen a reduction from 7% to 4% in 2020. Cybercriminals threaten to leak data that they have stolen in attacks to improve their position in ransom negotiations.
More than two-thirds of all companies saw an increase of attacks or in the complexity of attacks. The number increased by 13% to 72% in the last year.
Sophos notes that organizations are better prepared when it comes to ransomware attacks. 99% of organizations managed to get "some encryption data back", usually through the use of backups but also through other means, e.g., using decryption tools if available.
More than 73% of all organizations used backups to restore data on average and 30% used other means to restore data.
Organizations who paid the ransom, 46% according to Sophos, got 61% of their data back on average. Only 4% of organizations got all of their data restored after paying the ransom.
The Media, leisure and entertainment industry had the highest use of backups in 2021, followed by other, business and professional services, and energy, oil/gas and utilities.
Organizations started to use multiple approaches to restore data. Backups were used if available but other means of restoration, including paying the ransom, were also used to speed up the recovery process.
32% of local and state government paid ransoms, the lowest number across all industries. Healthcare organizations paid 61% of the time, the highest reported number.
Ransom payments are increasing
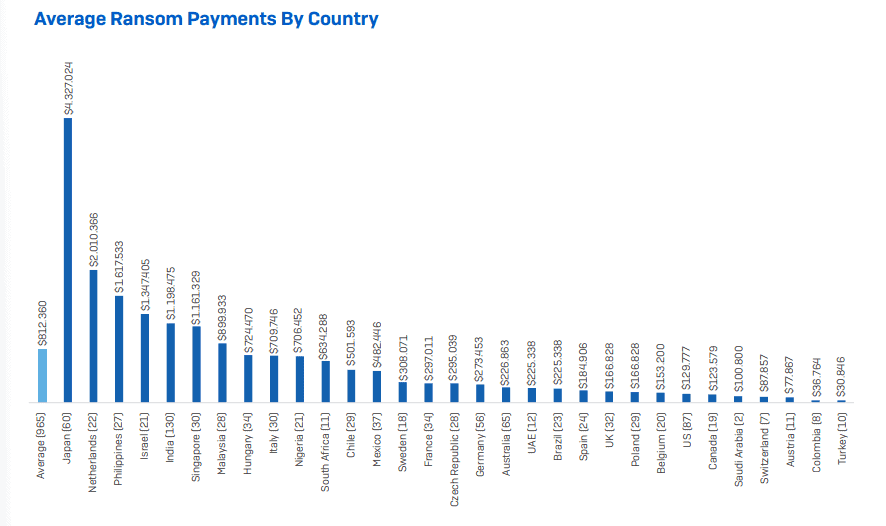
In 2021, the average ransom payment increased by the factor 4.8 according to the study. The average ransom payment was $812,360 in 2021, compared to $170,000 in 2020. Ransom payments of $1 million and more increased by the factor 3 in 2021, while payments of $10,000 and less dropped to 21% from 34% in 2020.
The average ransom exceeded $1 million in six of the surveyed countries:
- Japan -- $4.3 million
- Netherlands -- $2 million
- Philippines -- $1.6 million
- Israel -- $1.1 million
- India -- $1.1 million
- Singapore -- $1.1 million
The surveyed countries with the lowest average payment were Turkey ($30,000), Colombia ($36,000), Austria ($77,000) and Switzerland ($87,000). Organizations in the United States paid an average ransom of $129,000 in 2021.
The operational impact increases
The operational impact of ransomware attacks is significant, as 90% of organizations stated that ransomware attacks impacted their ability to operate. A total of 86% reported that the attacks resulted in the loss of business or revenue.
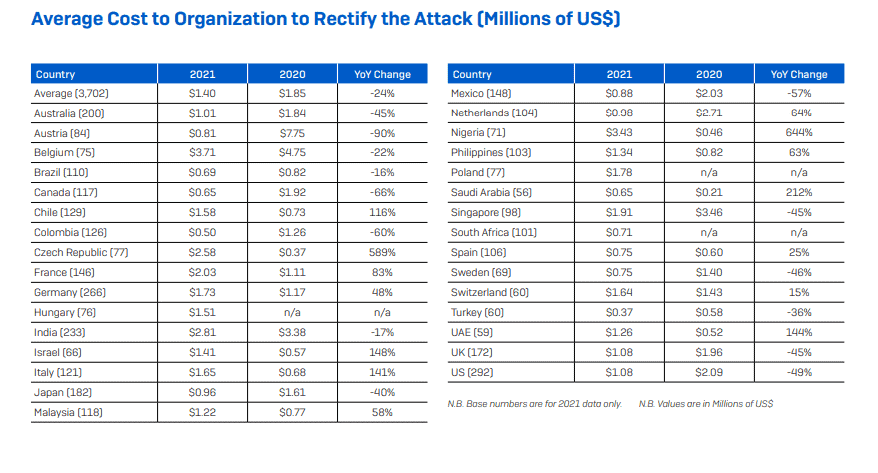
Costs to remediate attacks fell to $1.4 million in 2021 on average. In 2020, costs to remediate attacks were $1.85 million on average. Sophos believes that several factors have played a role for the decrease of costs in 2021. For one, insurance providers have become better at guiding their customers to react to the threat quickly and effectively. Optimized processes helped reduce the impact and costs of ransomware attacks, and other factors, including that the reputational damage of ransomware attacks has lessened, played a role as well.
The average cost to remediate ransomware attacks did not drop in all surveyed countries. Organizations saw increases in several countries. The highest increases were in Nigeria (644%), Czech Republic (589%), Saudi Arabia (212%), Israel (148%) and in UAE (144%). Payments rose in Germany, France, Italy and Spain as well.
It took an average of one month to recover from ransomware attacks. Higher Education and central/federal government took the longest to recover, as two in five needed more than one month to recover from attacks. The fastest recovering sectors were manufacturing and production, and financial services.
88% of all surveyed organizations believe that they have a cybersecurity budget and headcount that is either more than needed or sufficient to deal with ransomware attacks. With 66% of organizations hit by ransomware attacks in 2021, Sophos believes that organizations "are struggling to deploy their resources effectively in face of the accelerating volume and complexity of attacks".
Cyber Insurance
83% of the surveyed organizations have cyber insurance against ransomware, but 34% of them have exclusions and exceptions in the policy. Cyber insurance adoption increases by size according to the study, as 88% of organizations with 3,001 to 5,000 employees have cyber insurance compared to 73% of organizations with 100 to 250 employees.
Organizations hit by ransomware are more likely to have cyber insurance than organizations who were not hit by ransomware in 2021. 89% of organizations hit by ransomware have cyber insurance compared to 70% of organizations who were not hit by ransomware.
The process of securing cyber insurance has changed in 2021 in the following ways:
- 54% of organizations state that the level of cybersecurity that is needed to qualify for insurance is higher.
- 47% state that cyber insurance policies are more complex.
- 40% say that fewer companies offer cyber insurance.
- 37% say the process is taking longer.
- 34% state that cyber insurance is more expensive than in 2020.
97% of organizations with cyber insurance have made changes to their organization's cyber defenses: 64% if implemented new technologies and services, 56% have increased staff training and education activities, and 52% have changed processes and policies.
Insurers paid cleanup costs in 77% and 40% of ransoms in all reported cases. Clean-up cost payouts increased by 10% to 77% in 2021 while ransom payouts dropped by 4% to 40% in the same year.
You can check out the full report here.
Now You: have you experienced ransomware attacks at home or work?


















The other thing increasing are my backups on offline media :)
Those SATA write blockers are really handy to access read only data.
Four words: Back…. up…. your…. data!!!!!
Yes, absolutely. However, only if you’re employed at or do contract work with mid-high value businesses. Since so many people do at least some of their mission-critical work remotely, from home, their home network is just an extension of the corporate intranet. That’s why any Enpoint XDR Solution has a very strong focus on their anti-ransom components these days. Personally, I’ve had MS Defender Endpoint intercept next-gen Ransonware attacks on my home network maybe 5 times over the past 6-8 months, roughly.
In this interesting post, all the talk is about “organizations” targeted by ransomware attackers. Sure, I suppose they are the main target now, because on a per-attack basis they yield a far higher profit than individuals. On the other hand, if you work dragnet-style, individuals may be an easier (and more frequent) catch.
So, I am curious: is there still much ransomware around nowadays that is targeting not organizations, but individual home users? If so, any statistics available on that?
I myself have had only once to help a home user whose PC actually was hijacked by ransomware, and that was at least some 6 or 7 years ago. And yes, as one might expect, this was a clueless user who admitted himself that he probably got ransomware while trying to download some p*rn (unfortunately, he was also just the type of user who had never bothered to keep adequate backups) .
I’d like to know: has anyone still encountered actual ransomware on a home PC in the last couple of years?
@Henk
> ..has anyone still encountered actual ransomware on a home PC in the last couple of years?
Yes.
I’d like to know: has anyone got ransomware or malware from just downloading porn media (e.g. mp4 and jpg files)?
I know folks say that’s a thing, but I’ve never seen such evidence.
How about the important info: What operating systems were on top in being infected? Windows 7? 10? 11? God forbid, XP? Linux?
My wild guess would be Windows 7 tops the list, closely followed by 8, 8.1, 10 and 11. Then maybe even a few mac computers. Linux is not even measurable, the impact is that low. Right?