Workaround for security issue in 7-Zip until it is fixed
Recent versions of the open source archiver 7-Zip have a vulnerability that has not been fixed yet. Successful exploitation of the vulnerability allows privilege escalation and the execution of commands; it appears that the issue can be exploited locally only.

Filed under CVE-2022-29072, the vulnerability is using the included 7-Zip Help file, 7-zip.chm, for the exploit. Attackers need to drag and drop files with the 7z extension on to the Help > Contents area in the 7-Zip interface.
Update: The CVE is disputed. Multiple researchers, who analyzed the vulnerability, have reported that no privilege escalation can occur.
Vulnerability details have been published on GitHub. The page provides technical information and a short demonstration video of the exploit.
It is unclear if and when 7-Zip will address the issue. The last update of the application dates back to the release of 7-Zip in December 2021
Users of the application may use the following workaround to mitigate the vulnerability on their devices. Since it is using the included Help file, one way of dealing with the issue is to delete the Help file.
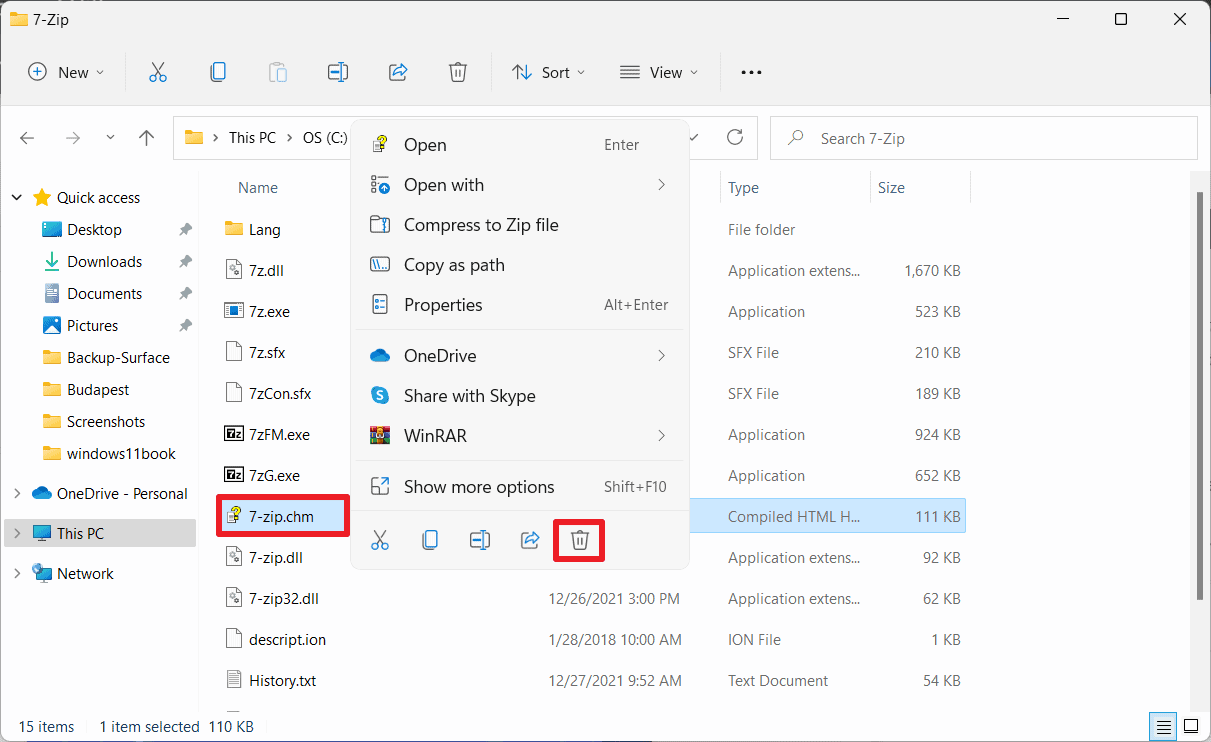
- Open the 7-Zip installation directory or folder on the system. On Windows, these are usually C:\Program Files\7-Zip or C:\Program Files (x86)\7-Zip, depending on whether the 64-bit or the 32-bit version of the application has been installed.
- Locate the file 7-Zip.chm; this is the help file. You can open it directly to display its content.
- Hit the delete button on the keyboard or right-click on the file and select the Delete context menu option, to remove it from the system.
- You may get a prompt, File Access Denied. If that is the case, select Continue.
The file is moved to the recycle bin of the operating system by default. 7-Zip functionality is not reduced when you delete the help file. The Help file won't open anymore after the deletion, when you select Help > Contents in the 7-Zip File Manager or press the F1-key on the keyboard.
Closing Words
Deleting the Help file does not take longer than a minute. While it appears unlikely that the issue is exploited on large scale, most users may want to remove the Help file to protect their systems against exploits targeting the issue.
Now You: which archiver do you use? (via Deskmodder)



















Would you mind updating this article?
The CVE is now officially disputed : https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-29072
It is a hoax. That shameless person was just looking for attention. CERT own researcher already called him out: https://twitter.com/wdormann/status/1516979696126369792
Other well known researchers also called him out and asked for evidence, and his response was really amateurish and troll: https://twitter.com/taviso/status/1516103911253286914
Sumatra pdf viewer can open chm files. Anybody know if this is another good workaround?
@NA,
> Sumatra pdf viewer can open chm files. Anybody know if this is another good workaround?
I have been am regular user, and favorite a SumatraPDF v3.3.3 64-bit.
It is possible to view CHM files using SumatraPDF.
Free PDF Reader – Sumatra PDF
https://www.sumatrapdfreader.org/free-pdf-reader
In this case, since it is a viewer function, the use of SumatraPDF should not result in an exploit vulnerability.
But the issue now is that if the app’s help files are “CHM” files, the app could “trigger an exploit” and those “CHM” files, it would be wise to remove them. This is the topic.
In any case, the problem and workaround were raised by the program creator. It is up to the end user to decide what to do about it.
The CHM (.chm) files in my Windows 10 (x64) Version 21H2 (build 19044.1645) as listed by “WizFile” are as follows:
In third-party apps:
All items in the Nirsoft program
AIMP
IrfanView
M Calc
TVClock
I believe that the use of CHM (.chm) files is a rare case (either the program developer is unaware of the vulnerability or has forgotten to move from the CHM (.chm) files to an alternative solution). In any case, removal of the file will not interfere with the original function of the program.
Total 59 files related to Microsoft (Windows OS):
C:\Windows\IME\ :10 files
C:\Windows\Microsoft.NET\Framework\ :4 files
C:\Windows\Microsoft.NET\Framework64\ :4 files
C:\Windows\System32\DriverStore\FileRepository\cnlbcja64.inf_amd64_3120ae9234c33f56\ :4 files
C:\Windows\WinSxS\ :37 files
Now, I removed all third party CHM (.chm) files.
However, Microsoft’s portion is managed by UAC, so the exploit vulnerability is supposed to be avoided.
Those who have CHM (.chm) files that they wish to delete, but contain information that they would like to retain can safely convert them to a PDF before deletion.
One means by which to accomplish this is with the online converter Zamzar:
https://www.zamzar.com/uploadComplete.php .
@AJNorth
Your link for the .CHM converter (https://www.zamzar.com/uploadComplete.php) should be:
https://www.zamzar.com/converters/ebook/chm/
Wow. That was supposed to be a simple ascii text thumbs up.
…../ )
…..’ /
—‘ (_____
……… ((__)
….. _ ((___)
……. -‘((__)
–.___((_)
I think the solution would be to invoke the .chm file in a standalone way. Windows handles these by itself. Now 7zip opens it within its main process I think. I don’t know the standard procedure of handling .chm files, I rarely use these help files, but I keep them around nonetheless if at any time I need them.
Personally this does not affect me, my PCs run with LUA disabled, so everything has administrator priviledges. User knowledge is the only thing keeping my computers safe.
The CVE is disputed:
https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-29072
https://twitter.com/wdormann/status/1516217431437500419
Mind you, CHM files are basically rendered in IE/Trident (even if your system does not “have” IE or if you have “removed” it by yourself). You can change these settings so that nothing gets automatically executed via inetcpl.cpl upon drag and drop operations. On my system where I am “machine\administrator” I am being asked what to do with the dragged file bofore anything happens.
#Workaround for 7-zip Vulnerability
$filepathx64 = “C:\Program Files\7-Zip\7-zip.chm”
$filepathx86 = “C:\Program Files (x86)\7-Zip\7-zip.chm”
if (Get-ChildItem -Path $filepathx64) {
remove-item -path $filepathx64 -Force
}
else {Get-ChildItem -Path $filepathx86 | remove-item -Force}
@RedMan,
@MarlKax,
@Pet,
@Schmurtz,
@Phil G,
This article (gHacks Tech News) is only quoted verbatim from an “emergency alert” by a 7zip developer.
gHacks Tech News has an explicit link to the citation:
https://github.com/kagancapar/CVE-2022-29072#mitigations
Did you guys check the citation neatly?
You are the ones spreading falsehoods, misinformation and other BS!
Who the hell are you people?
Speaking of which, there has been a lot of talk lately about demagoguery by Russian sympathizers.
https://www.ghacks.net/2022/04/16/google-chrome-emergency-update-patches-0-day-vulnerability/#comment-4519664
“Attackers need to drag and drop files with the 7z extension on to the Help > Contents area in the 7-Zip interface.”
But I don’t let attackers touch my mouse or even get into the house while I’m at my computer.
They can hypnotize you, just be careful
Suggesting to delete the help file is going way overboard. Just change the file extension or move the file elsewhare. Then you can rename or move it back if and when you need to use help, but it won’t get activated during normal operation.
@saywhat,
And you too!
Why are they all such (shallow and unwise, impulsive) goofballs?
https://www.ghacks.net/2022/04/18/workaround-for-security-issue-in-7-zip-until-it-is-fixed/#comment-4519712
https://www.ghacks.net/2022/04/18/workaround-for-security-issue-in-7-zip-until-it-is-fixed/#comment-4519714
https://www.ghacks.net/2022/04/18/workaround-for-security-issue-in-7-zip-until-it-is-fixed/#comment-4519723
Ridiculous…
There are a lot more dangerous things on Windows vulnerabilities on Windows !
This even not useful for a hacker.
It may still be an issue in some cases, for instance in organisations. For Home users, it does not appear to be a big issue.
You mean, for single home users with no untrustworthy guests. Literally hermits who live in a vault.
Of the people I know, MANY are not ones I would trust with unsupervised access to any of my devices, whether computer or computer-with-a-phone, computer-with-a-tv-tuner, etc.
Want some everyday homeuser examples?
Kids getting admin rights – and doing shit knowingly or not – e.g. because some game they want to run. Or other restriction they want to get around.
Kids, “friends”, neighbours, partyguests, spouse, kids-“friends”, and so on and so on, all potentially not respecting your stuff or even just for the most petty or whimsical reasons want to spy or sabotage.
And that is just for your stuff at home. Now imagine a business/school/library/government wanting to minimize user mischief and/or crime but have to let people use the machines or go back to pen, paper, typewriter and photocopier.
So this is still a issue though (unrestricted) physical access is a bigger issue in itself. Even so, most people are not TAO level threats, but they can pull a “drag here to exploit” on a common piece of (“safe” and whitelisted) software if it is vulnerable.
It is lowering the bar.
So, even to the dumb, it should be clear that privilege escalation and console/shell access is not to be taken lightly just because it does not come with the dreaded ‘remote’ prefix.
People who publicly dismiss this type of exploitable problem are effectively working to keep the lid on it (they are part of/using the problem) or hopeless ignorants who think their hermit lives protects them and by faulty logic also protects everyone else if we would just take their view.
I really recommend you impose a harder stance against their unhealthy posts.
Btw, the mitigation has and exposes some problems. Without giving too much detail:
Like another commenter pointed out, ‘.chm’ has been retired for a long time for being a *problem*, because the components that provide use of it are unsafe. It is dangerous unmaintained code, some of which dates back to the reckless parts of activeX and even win95 and the many horrific practices of the time.
Throw in a possibly unsafe UI in 7z and shit blows up.
That is, why would you even allow a drag action there? And not handle it safely. Doing it on purpose?
You should be delegating any app ancient enough to still use CHM to a disconnected VM, it is a screaming sign that there may be many other old vulnerable parts buried in it.
That shit should have died ages ago, but people cling to old tools and old ways that do not have safe failure modes.
It’s a lot like having a unsafe version of Flash installed. Needs to be treated the same way. Kill the support for it, help crowdfund a safe replacement for a safe *subset* of it, if you must have those old CHM files and can’t get replacement.
While I’m at it, same with PDF. Unsafe, featurecreeped. Needs a return to basics. It’s not a fit document when it can specify needs to load external or remote content, run embedded code or external programs and talk to the internet.
NOTE: in the start menu, All Programs -> 7-Zip, the link to the help file will fail. Windows will ask if you want to delete the link.
You could delete it or leave it as a reminder the help file is gone.
How many other CHM files can cause this issue?
@pHROZEN gHOST,
> How many other CHM files can cause this issue?
Do you mean other apps besides the 7-zip program?
Indeed, I too am concerned about parallel case (similar instance).
For example, “plug-ins” bundled with apps can introduce exploit vulnerabilities, so perhaps the same is true of “CHM files”. Incidentally, the auto-update feature is also a concern of danger.
Unnecessary items (e.g., other language files), even those bundled with the application, would be candidates for deletion.
I looked it up,
The CHM (.chm) file was a proprietary online help file format developed by Microsoft, but has been discontinued for security reasons (migrated to the new “Microsoft Assistance Markup Language”).
https://en.wikipedia.org/wiki/Microsoft_Compiled_HTML_Help
Google Reviews lists CHM (“.chm”) files on the “blocked” list.
In short, the CHM (.chm) file is “potentially risky”.
If other apps also ship with a CHM (.chm) file, it is wise to remove it.
My main system has 620 CHM files.
OhMyGorsh, pass the TP.
@pHROZEN gHOST,
> My main system has 620 CHM files.
I see that there are quite a few CHM (.chm) files in your system.
The CHM (.chm) files in my system (as listed by WizFile) are as follows:
In third-party apps:
All items in the Nirsoft program
AIMP
IrfanView
M Calc
TVClock
I believe that the use of CHM (.chm) files is a rare case (either the program developer is unaware of the vulnerability or has forgotten to move from the CHM (.chm) files to an alternative solution). In any case, removal of the file will not interfere with the original function of the program.
Total 59 files related to Microsoft (Windows OS):
C:\Windows\IME\ :10 files
C:\Windows\Microsoft.NET\Framework\ :4 files
C:\Windows\Microsoft.NET\Framework64\ :4 files
C:\Windows\System32\DriverStore\FileRepository\cnlbcja64.inf_amd64_3120ae9234c33f56\ :4 files
C:\Windows\WinSxS\ :37 files
Now, I removed all third party CHM (.chm) files.
However, Microsoft’s portion is managed by UAC, so the exploit vulnerability is supposed to be avoided.
By the way, my system (Windows OS),
Windows 10 (x64) Version 21H2 (build 19044.1645)
I also forgot to mention… besides all my point, I forgot something important.
Most computers already run as admin in this world, it’s rare the cases (besides enterprise) where you don’t, maybe someone sharing their device and setting the account with limited access.
So, that simple fact proves this super critical security issue where you have to rush to delete a chm file and I will teach you to how step by step how to delete even though most people shouldn’t even have this program installed and less in program files… it is just weird drama, making something bigger than it should be.
enterprises aren’t “rare cases”, when they’re most likely the targets for many kinds of invasion
And how do you think websites like ghacks still survives? Repeat after repeat, hoaxes, false alarms etc.
Amen Brother
lol
and as usual this will not affect anyone relevant, especially ghacks viewers.
Even if it wasn’t just ‘local’, it wouldn’t be a problem, it’s like… if someone has already an intruder in their computers, I don’t think the first thought of the intruder will be “can I exploit 7zip?”
I mean, we have to even imagine that the intruder even knows you have 7zip and can exploit it…
and then what? again, do you think they will care about 7zip then?
Just another drama more like a hoax by people who want to make money out of bug bounty programs or put their names out there as someone who discovered some lame bug around.
I mean I would accept the fact that it can affect some enterprise but then, why would a business use 7zip and not something else anyway?
And wasn’t the power of Open Source that it could get fixed within 3 seconds of discovered but here there are the questions “when will it happen since last update was Dec 2021?”
I mean, just accept this is stupid to worry about and even give instructions to delete anything, it is a bug yes, but put it out there as this serious security issue that might be exploited so stay calm, don’t panic and do as I say…. it’s just ridiculous. Most of scare tactic drama exploitable bugs are usual local, so I guess the solution should be to make sure nobody gets in your computer like you should already be doing in the first place?
Just stop.
Sometimes the intruder only have User Rights on Windows, in many companies that means they could run admin commands through normal user accounts with this method…
Many people could exploit it, and many people like me, who work in Infra-IT for multinationals or other companies, would apply this type of corretion
Wankers!!!
What goes around my friends….
Fear mongering is a Dark Art, stop it, there’s enough sensationalism going on in the world.
And please stop censoring non-threatening posts.
It’s against the philosophy of the internet.
The article describes a security issue in 7-Zip. It is up to each reader to decide whether this is an issue that needs immediate attention or not.
Thank you for the information on the exploit vulnerability identified in the popular “7-Zip” program.
GitHub – kagancapar/CVE-2022-29072: 7-Zip through 21.07 on Windows allows privilege escalation and command execution when a file with the .7z extension is dragged to the Help>Contents area.
https://github.com/kagancapar/CVE-2022-29072#mitigations
Mitigations
first method: If 7-zip does not update, deleting the 7-zip.chm file will be sufficient to close the vulnerability.
second method: The 7-zip program should only have read and run permissions. (For all users)
Immediately, I alerted the Japanese portal.
https://freesoft-100.com/review/comment/21341/
Wow owl.
Someone has to get direct personal access to the PC to exploit this issue.
If a bad actor can do this you have far greater issues.
And, as pHROZEN gHOST said you can’t create archives with read only access.
It does make me wonder about the legitimacy of all the long posts you put on here (that I don’t bother reading as they always look like quick google searches compiled rather than legitimate knowledge).
Wow DrKnow,
I am laughing out loud at how your handle-name is an ironic way of saying “I don’t know anything, I don’t try to know anything”.
Just now, I have clearly known that you are foolish enough to simply “deny the unknown”.
Name calling and attacks on nicks? I’m surprised Martin hasn’t stepped in already.
This has no place here.
If the program does not have write privilege, you cannot create archives.
@pHROZEN gHOST,
> If the program does not have write privilege, you cannot create archives.
The workaround is a technique that the developers of the 7-zip program have demonstrated to end users.
https://github.com/kagancapar/CVE-2022-29072#mitigations
It is up to the end user to apply it.
The second method would be for environments with an unspecified number of users, such as corporate use, where the all users should be restricted.
In other words, I believe that restricting use by default and lifting it as needed was exemplified as a risk avoidance measure.
The lesson of history is that “safety management takes precedence over convenience”.