QuickHash GUI is an open source hashing tool for Windows, Linux and macOS
QuickHash GUI is an open source hashing tool which is available for Windows, Linux and macOS. If you're a security conscious person or want to verify file integrity, e.g. for backups, you must be aware of hashing.
Tip: we reviewed several programs to compute hashes in the past: you can use PowerShell to generate hashes, or use the programs Hashing, HashTab Shell extension, or Nirsoft's Hash My Files.
For those who aren't here is a brief description.
What is a hash value? Why is it important?
A hash value is an alpha-numerical string calculated by an algorithm which determines the integrity of a file. Every file has a hash value and the value is unique for each file.
The most common usage of hashes are to cross-verify them with the values given on the download page of digitally distributed content (software, Android ROMs, apps, etc). If the values given by the developer and the downloaded file are a perfect match, it means the file has not been tampered with during transport.
If the values are different, one of two things are probable. Either the downloaded file is corrupted, or worse, the file has been modified by someone.
Tip: You can see how this works yourself. Create a text in notepad, or doodle something in Paint and save it. Those files will have hash values of their own. Note them down, edit the files and save them. Look at the hash values again, they should be different.
QuickHash GUI
The interface (or GUI, if you will) of QuickHash GUI is quite simple. It has a tab bar with several tabs, each of which displays a set of options. There is a side-bar which is persistent across all screens. It houses the algorithm panel and the System RAM panel, which shows your computer's total RAM, and available RAM).
You can select one of the 5 algorithms: MD5, SHA-1, SHA-256, SHA-512 and xxHash32, and QuickHash will compute the corresponding value.
Tip: MD5 isn't exactly secure. So I recommend using one of the other options, all of which are cryptographic hash functions.
File
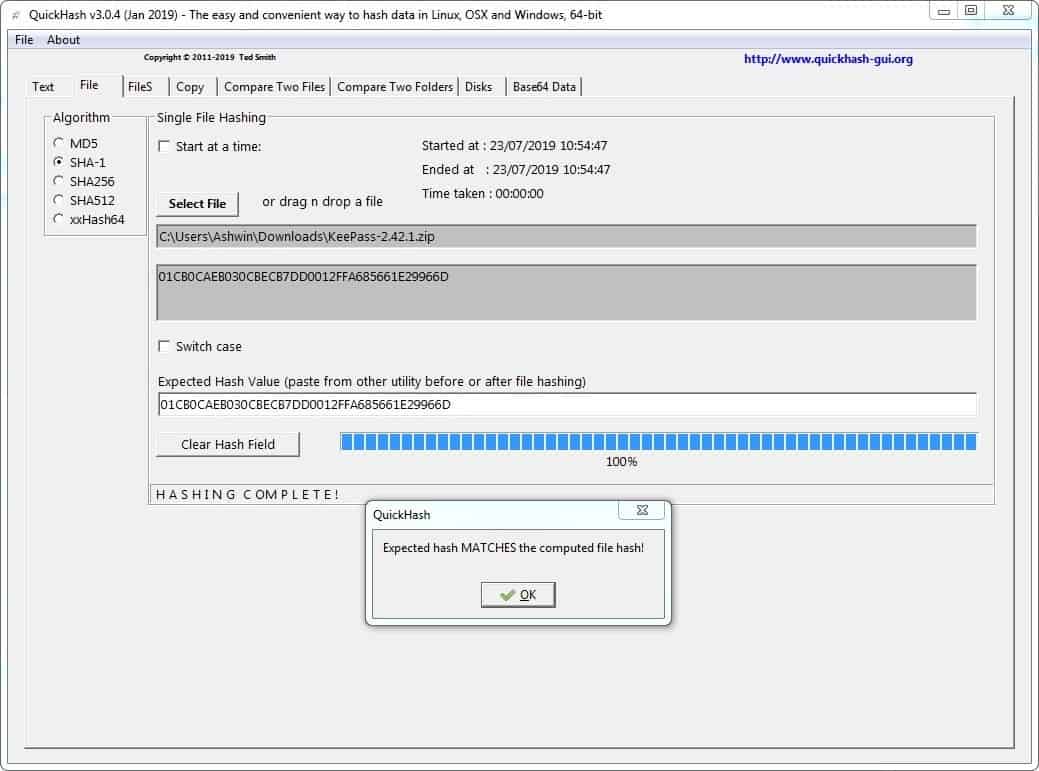
This is the second tab of the program. The reason I'm beginning here is because it may help in making it easier to understand how hash comparison works. You can use the "select file" button in the tab to navigate and choose the file which you want to check, or drag and drop one to the interface, and the computed hash value of the file will be displayed just below the button.
Copy and paste the hash value from the developer's website in the "Expected hash value" field, and if both values are the same, QuickHash will display a message saying they match. You can switch the case of the checksum from lower to UPPER using the option above the expected hash value field.
Let's check the hash of a KeePass archiv (refer to the above image). You can get the hash value posted by the developer, and use it to compare the hash of the file which you downloaded from the website.
Tip: Spaces matter. QuickHash does not include spaces in the computed hash field, so if you paste an expected value that has spaces, they won't match. Delete the spaces manually to get the "matches" pop-up.
Text
Text has its own hash values. You can use the text tab to type or paste some text and see its value displayed in the field on the bottom. This tab has 2 buttons which can be used to convert the case of the text (Make UPPER and Make lower), and a clear text button. You can also configure the application to hash text, or an entire file, line-by-line.
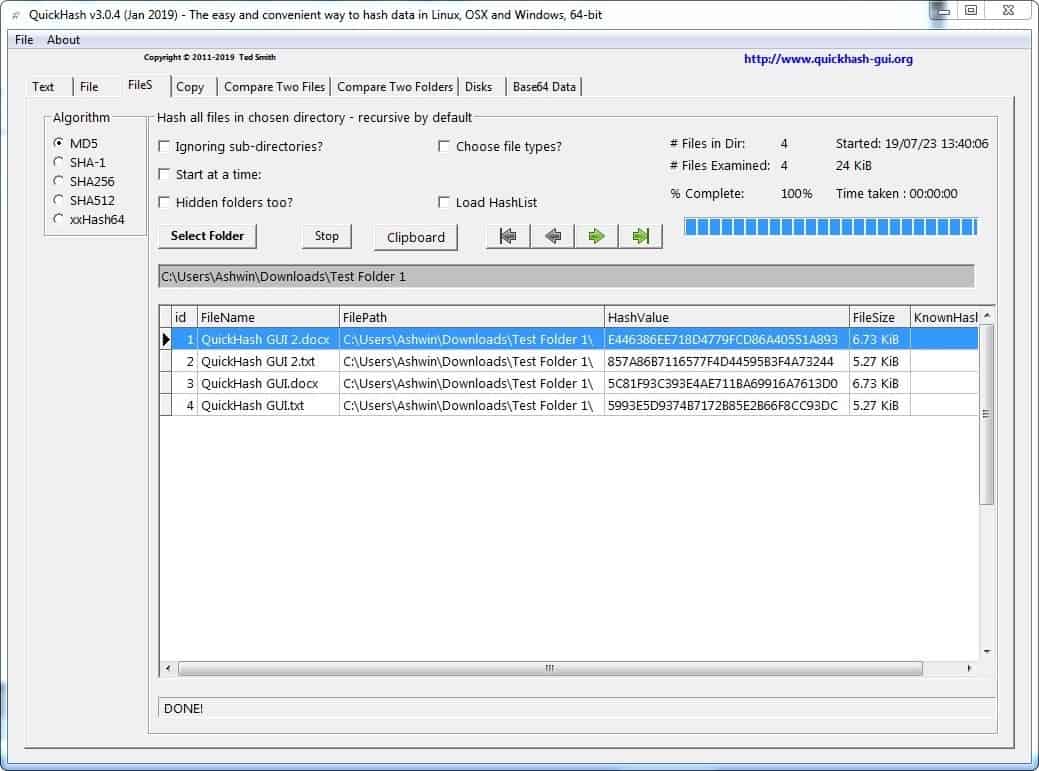
FileS
This tab lets you compute hashes for all files in a folder. It includes sub-folders, but you can optionally disable that. You can set wildcards using the file types option, to only compute the values of the files in the defined format. It even has an option to work with hidden folders, which can be useful if you are checking the System directory.
Copy
This is a very useful option when you are transferring data. Use the left pane to select the source folder which has the files that you wish to copy. Now select the destination folder where you want the content to be copied to using the right pane.
Hit the Go! button and QuickHash will initiate the process. The program will hash the values of the source files, copy the content over, and re-hash (checks the values of the copied content). It helps in avoiding corrupted files or errors during the copying process.
You can set custom options to only list sub-folders or sub-folders + files, wildcards, ignore sub-folders. QuickHash also displays the number of files in the folder, a progress bar, the start time, end time and the total time it took for the process to be completed. Optionally, you can save the results to a CSV.
The file and the files tabs, and the Compare two files tab have a "Start at a time" option. This is a timer, which automatically executes the hash computation, using the defined options.
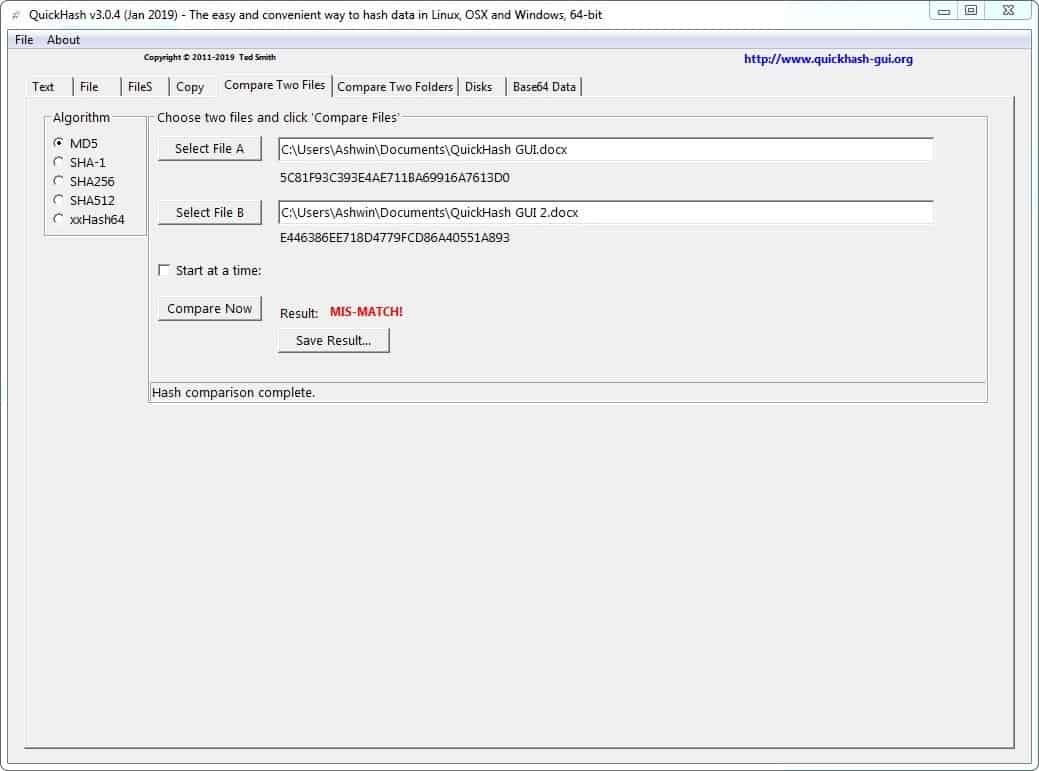
Compare Two Files
QuickHash GUI can be used to compare the hash values of two files. You just need to select the two files, and use the compare now button. The result will tell you if they are a match or a mis-match.

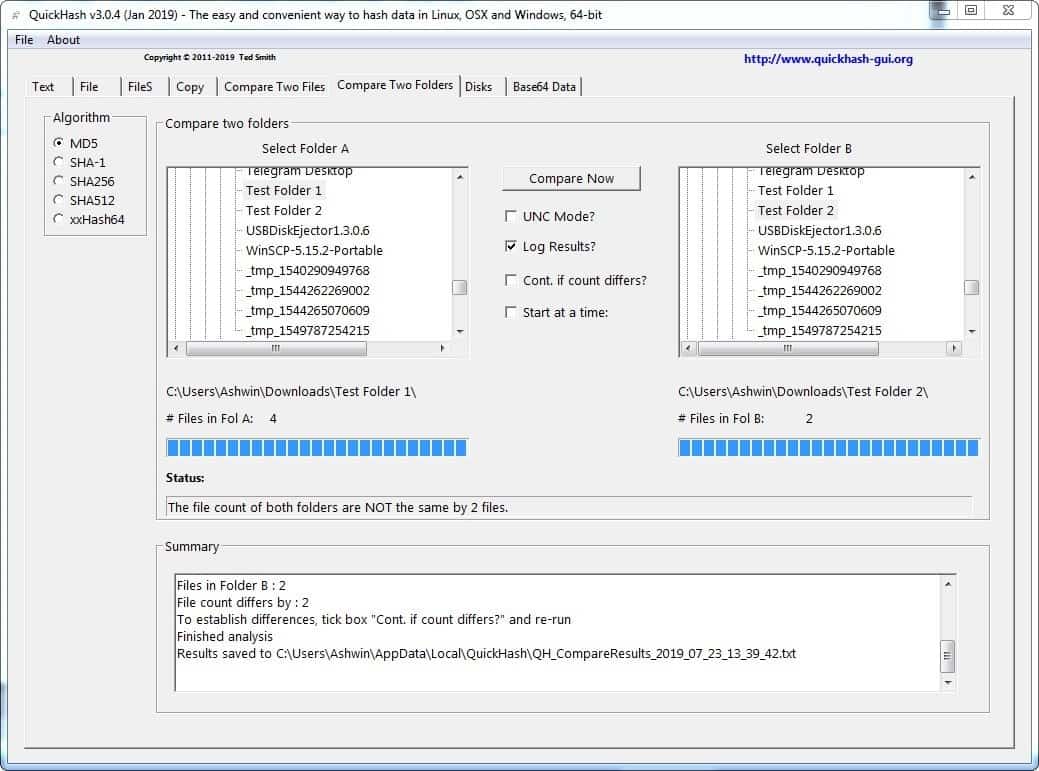
Compare Two Folders
This is similar to the above option, but used to compare two folders. A result of the comparison can be saved in a text, if you use the Log result option.
Disks and Base64
Want to check an entire disk's hash? You can do so with the program. But, in the Windows version, you can only run the SHA-1 algorithm to check physical disks, and you also need to run the program with administrator privileges. QuickHash GUI can also be used to decode Base64 data from files.
QuickHash GUI is a portable application, and supports 32-bit and 64-bit systems.
Hashtab is a good alternative for QuickHash, though the former hasn't been updated in 2 years.


























“the value is unique for each file.” — Absolutely not. That would imply that hashing is the equivalent of almost infinite compression. The value isn’t unique for each file; it’s just unlikely that two given files will have the same hash, to the extent that the hash has a large keyspace, and it’s prohibitively difficult to generate a specific hash.
In both Linux and Windows, I use the “Checksum” function in the “Download Status Bar / Download Statusbar / Downloads Statusbar” class of extensions available for legacy Firefox-family browsers. (Currently, that’s down to Pale Moon and, for a limited time yet, Waterfox.) You download the file, and when the download is completed, you right-click on its “tab” in the browser’s statusbar, choose Checksum, and select the type of hash you want to check (MD5, SHA1, MD2, SHA256, SHA384, or SHA512). The only time I’ve ever gotten bad hash calculations from it was when my integrated-graphics CPU was pegged out at 100% doing video re-encodes, so I don’t rely on it under those circumstances.
In Windows, I find the HashTab shell extension even easier and faster to use (unless the downloaded file in question is really big), because it automatically picks up file hashes you have copied to the Clipboard. I configure my “Downloads Statusbar” extensions to automatically open the target directory in Windows Explorer when a download completes, and the downloaded file is automatically selected, so all I have to do is type Alt+Enter to bring up the file’s Properties menu and then click on the File Hashes tab. All of the hashes get calculated, and if whatever is in the Clipboard matches one of them, I get a checkmark. I think there may be different versions of HashTab available, offering different collections of hash types, but mine offers MD5, SHA1, and SHA256. And that’s where file size comes into play. If you’ve just downloaded a big file like LibreOffice or a Linux ISO, the amount of time it can take HashTab to calculate *all three* hashes is non-negligible. Downloads Statusbar’s Checksum function only calculates one hash at a time and so is faster. But most of the time, FileHash is more convenient, and I’m pretty sure it’s never given me bad calculations when the CPU was maxed out.
Oh — I almost forgot. The download-management extension DownThemAll still works in Pale Moon, and it has its own optional hash-checking feature (for MD5, SHA1, SHA256, SHA384, and SHA512). I sometimes use that, too, in both Linux and Windows.
I have a hash-related question. The hashes for some files are provided in the form of a *.*.sha256 file, where *.* is the same as the name and extension of the file they are for. For example:
TrueOS-Stable-x64-18.12.iso
TrueOS-Stable-x64-18.12.iso.sha256
Are these *.sha256 files supposed to be picked up automatically by some kinds of hash-checking or download-management utilities I’m unfamiliar with? So far, I’ve just been opening them in Notepad++ and copying the hash from there.
Use the Windows
certutil command to check hashes
e.g., certutil
-hashfile
hash method one of :
MD2, MD4, MD5, SHA1, SHA256, SHA384, SHA512
e.g., certutil
-hashfile test.exe SHA256
HashTab works really good too.
HashCheck Shell Extension, “Lean and mean”, only 85KB.
This is the correct answer.
I’ve always used gtkhash, which is integrated into many Linux file managers and also has a Windows version. Download it from: https://sourceforge.net/projects/gtkhash/
gtkhash = 40MB to only calculate hashes???
I prefer cyohash: https://sourceforge.net/projects/cyohash/
Guys, hashing is not encrypting.
Who cares if it’s “secure” or not.
Considering that even big companies make the mistake of not implementing them properly, I think it’s important to understand the difference and especially considering that nearly most of the time your information is not processed by you. That is why we have huge leaks even at big companies such as LinkedIn, Tumblr, Dropbox, Facebook…
https://stackoverflow.com/questions/4948322/fundamental-difference-between-hashing-and-encryption-algorithms
Here we go again, although it seems this time there was no leak and they were able to fix it before anything bad happened (then again they won’t provide any details about it due to security concenrs). It just proves that these things do happen in the real world either by honest mistakes (such as this one), intentionally (Facebook) or maliciously (Linkedin, Dropbox).
https://techcrunch.com/2019/07/24/robinhood-stored-passwords-in-plaintext-so-change-yours-now/
Yes, In this context it makes zero difference as far as I know.
I happen to check file hashes, mainly that of downloads, though seldom. For this purpose I’ve always used ‘HashTab’ at http://implbits.com/products/hashtab/ which displays as a tab in a file’s properties window (hence its name), hence quickly accessible.
I admit that I don’t check file hashes systematically even if I consider myself as a security conscious person and such lacks contribute to my arguments when facing friends who point out my excessive caution in the wild world of the Web arena :=)
Hi Ashwin, thanks for bringing in another excellent article, I will definitely be checking this one out. I also just want to point out something about what you said above:
>> “MD5 isn’t exactly secure. So I recommend using one of the other options, all of which are cryptographic hash functions.”
SHA-1 is also not secure, it may be used to validate signatures, version control and generate unique values but please don’t use this for anything requiring cryptographic security.
https://en.wikipedia.org/wiki/Secure_Hash_Algorithms
https://en.wikipedia.org/wiki/SHA-1#Applications