May 2019 updates for Windows 7 and Server 2008 R2 don't play nice with McAfee or Sophos software, again
It seems that the saying "history repeats itself" is true, at least when it comes to Microsoft patches. Microsoft released updates for all supported versions of Windows -- client and server -- on the May 2019 Patch Day.
We covered the updates in our monthly security updates overview for Windows. Microsoft confirmed two issue: an update might be installed twice on affected systems, and some UK government sites were not accessible in Internet Explorer 11 or Microsoft Edge.
Microsoft added gov.uk to the list of HTTP Strict Transport Security Top Level Domains, and that caused issues for government sites that did not support it.
Things looked better compared to last month. Several Enterprise-focused security products did not play nicely with last month's updates for Windows 7, Windows 8.1, Windows 10, and the Server variants.
Security companies Sophos, Avast, Avira, ArcaBit and McAfee acknowledged issues with last month's updates. Machines would not boot into Windows anymore and appeared frozen or locked on startup.
Patch notes suggest that the issues are fixed. The monthly rollup patch KB4493472 for Windows 7 SP1 and Windows Server 2008 R2 SP1 states that the issues with security software has been resolved and that Microsoft removed the temporary update block as a consequence.
Fast forward to May 2019. If you check the known issues of the monthly rollup patch KB4499164 for Windows 7 and Windows Server 2008 R2, you may have a deja vu when you go through the known issues.
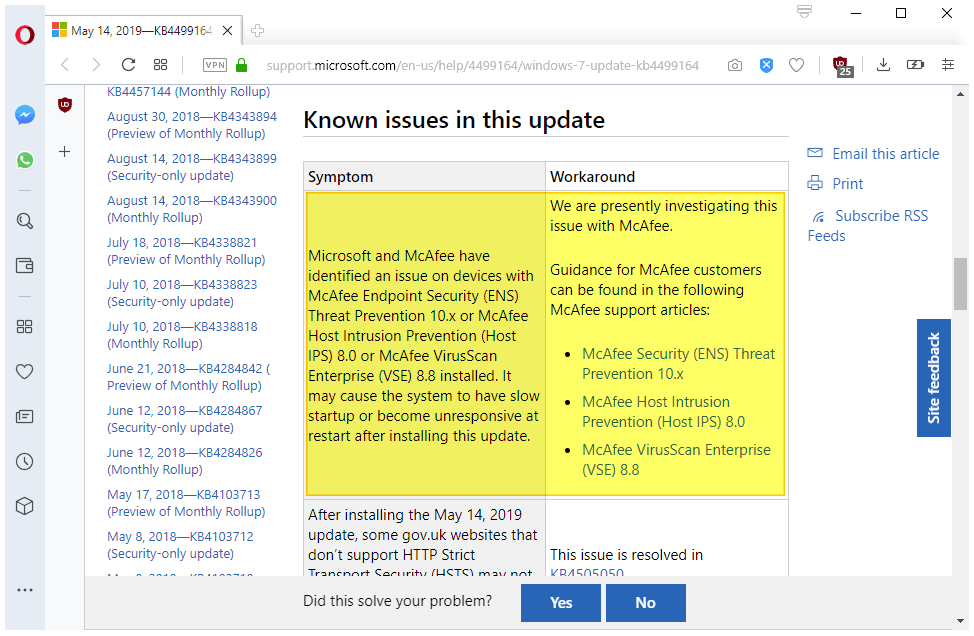
A new issue, added on May 18, 2019 suggests that systems with McAfee security products installed may freeze, hang or start very slowly after update installation.
Microsoft and McAfee have identified an issue on devices with McAfee Endpoint Security (ENS) Threat Prevention 10.x or McAfee Host Intrusion Prevention (Host IPS) 8.0 or McAfee VirusScan Enterprise (VSE) 8.8 installed. It may cause the system to have slow startup or become unresponsive at restart after installing this update.
The known issue and the listed products are identical. McAfee updated its knowledge center on May 14 (the Patch Day) and May 16 (Endpoint Security), and on May 17 (VirusScan Enterprise).
McAfee reveals that all Microsoft updates released in April 2019 or later are known to cause the issues. Workarounds should work for the May 2019 updates as well.

Sophos is not listed by Microsoft but Sophos published a support article that suggests that the May 2014 updates are causing issues on Windows 7 and Windows Server 2008 R2 devices after installation. (via Ask Woody)
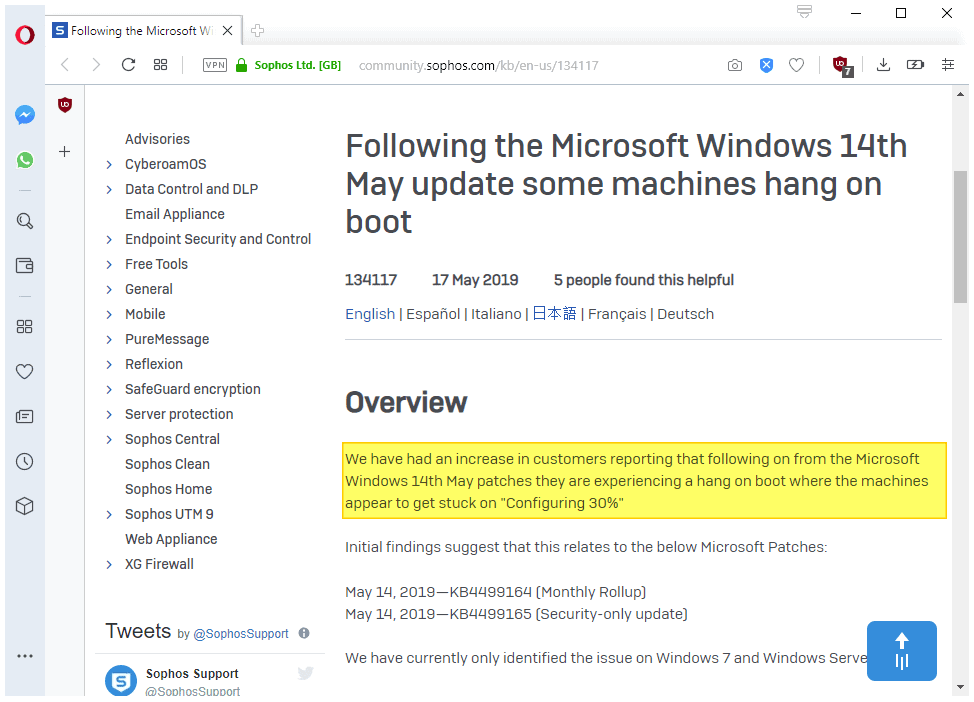
We have had an increase in customers reporting that following on from the Microsoft Windows 14th May patches they are experiencing a hang on boot where the machines appear to get stuck on "Configuring 30%"
Both issues appear to be limited to Windows 7 and Windows Server 2008 R2 updates. It is possible that the products of other security companies are affected by the issue again as well but that has not been confirmed.
Open questions:
- Is the issue limited to Windows 7 and Windows Server 2008 R2?
- Is the security-only update affected? Microsoft says no (McAfee), Sophos says yes for its products.
- Are all other security products unaffected by the issue?
Closing Words
The issue is limited to Enterprise security software; Home users and small businesses should not run into these issues. It is still a good idea to create backups before updates are installed, and to wait with the installation of updates until absolutely necessary (e.g. active exploit of security issues or major bug fixes).
Now You: Any bets for next month's updates?


















Despite M$ propaganda, the problem is NOT limited to McAfee and Sophos, or any third party applications. The same problem occurs without any of the aforementioned installed. M$ can’t solve a problem while they falsely blame it on others.
The update seems to have impacted Symantec EPP. As a fix, I found if you remove the page pool then reinstall it, the problem seems to go away. It also seems that it impacted only my VM’s physical machines seemed fine.
The May patch KB4499164 causes very slow startup (like 20minutes) on our machines with Sophos. We have to manually remove it and then hide it.
How does the sequence go when MS releases a patch with important security fixes in it, but soon discovers that it corrupts or hangs many users’ systems? For example, the April 2019 rollup did this on Windows 7. Many users can’t or won’t install the buggy patch. But they need the security fix it was originally intended for. Does MS revise the buggy patch? If so, does it retain the same KB number or get a new one? Or for monthy rollups, does the next monthly rollup contain the security fix from the last one without the bug?
My dad’s backup laptop runs Windows 7 Enterprise and Sophos Endpoint Security and Control. Tech support at his work does the initial OS installation and setup, but subsequent maintenance (for laptops and home-office desktops, at least) falls to users. Where my dad is concerned, that means maintenance falls to *me*. This makes two months in a row that I’ve been unable to install “critical” security updates on his Windows 7 laptop, and this month, one of the patched vulnerabilities is expected to be targeted by potentially serious real-world exploits in the near future. Accordingly, I asked my dad to ask tech support at his work to recommend an acceptable alternative antivirus. My first choice would be Kaspersky, but I don’t know whether his work and institution are covered by the US government ban.
Okay, that was my calm, rational response. My emotional response is: *WTF*, Sophos?
Three months in, my dad’s employer — a major public university located in Microsoft’s home state — has finally arrived at a solution to the Sophos problem: they’re forcibly upgrading all of their Windows 7 users to Windows 10, six months before end of life. After trying to decipher Sophos’s updated response to the issue several times since the problem arose, and factoring in the cost of paid extended Windows 7 Enterprise support after January 2020, it’s what I was privately *expecting* them to do. I’m not sure what they’re going to do with specialty software that doesn’t work properly on Windows 10 — maybe run it on air-gapped, outdated Windows 7 computers or something. (Hey, if Paris airports can run their weather-alert software on Windows 3.1, why not, right? ;-)
Anyway, facepalms all around, on me!
Pretty obvious that Microsoft is not caring about problems on Windows 7 or Server 2008, since they’d prefer those enterprises still on those systems move to Windows 10 and Server 2016 or 2019.
This is par for the Microsoft “cause pain until you upgrade” policy.
If only there existed some OS that doesn’t need antivirus, and wouldn’t get completely soiled garbage updates every month. Oh well, maybe sometime in the future.
@Mork:
Yes, if only there *were* such an OS. And you know what would make it even better? If it were *free* and you could install it on whatever hardware-compatible machine you wanted to! Oh well, in the meantime I guess we can only dream… ;-)
McAfee or Sophos software don’t play nice with May 2019 updates for Windows 7 and Server 2008 R2, again
I think would be the appropriate title. Shouldn’t these companies test their sowftware against the preview patches which MS is releasing? And as others have already stated, just stick with MSE/Defender, if you need an a/v – if you don’t just kill that one also, saves your resources and potential headaches.
Nah, why test if it’s easier to blame “evil Microsoft” and their “crappy Windows” when something doesn’t work. The same happened with 1809 and some device drivers…wtf you had insider versions almost a year before the release and you couldn’t make your stuff compatible? That’s just laziness combined with blame-shifting, nothing else…sadly no customer will blame Intel for their broken GPU drivers or any of those incompetent 6 antivirus companies, just Win 10 and the updates.
So far I’ve been lucky and none of this has impacted Mom, who is still on Windows 7, (She uses Norton(. But 2020 can’t come fast enough, so that I can migrate her to Linux.
Her best friend already got a Chromebook and loves it.
I would love a Chromebook if I could easily figure out a way to get a different Linux build on it (like Q4OS or Puppy)
With some of them, it can be done. But this is potentially dangerous, as you are messing with the firmware on the device, basically converting it into a generic PC and kicking off Chrome OS completely and if something goes wrong with the firmware flash, it might get bricked.
https://www.youtube.com/watch?v=AxsckwmRhfw
(I did not make this video)
McAfee is crap, it’s creator, John McAfee says so.
agree
I got my current laptop when Windows 10 x64 Home was first released and have installed all Microsoft fixes shortly after they have been released. I do not recall a killer problem ever with this approach and have enjoyed the many improvements and fixes provided this way. It’s a mostly shame on Microsoft and application owners when shortcutting testing burns so many, but I and I suspect many others are happy campers.
It’s time to blame third-party software for not being resilient enough to Windows changes, which means that they’re relying on bad programming practices.
Just use Microsoft Security Essentials on Windows 7 or Windows Defender on Windows 8.1 and 10 on your PC and Microsoft’s equivalent enterprise solutions if it’s a work device.
It is time to take Microsoft to court for inflicting $Trillions in damages each month with unreliable, untested… updates.
Microsoft has changed some fundamental components in kernel without notifying major A/V software developers and without testing in house before spreading malware updates to Enterprise PCs.
Microsoft Defender… is just junk A/V software not suitable to use.
You know the best way around the Microsoft issue is to use Linux. I am slowly converting all of my customers so they don’t have these issues.
Agree 100%
Agree 100%.