Add McAfee products to the list of security products that don't play well with latest Windows patches
When Microsoft released the monthly cumulative updates for Windows 7, Windows 8.1, and Server products, no one could imagine what a nightmare these patches would become for many system administrators.
Microsoft acknowledged two days later that something was not alright, and that the updates caused compatibility issues with certain Sophos and Avast security products. Microsoft added products by Avast and ArcaBit to the list of known issues later that week.
Users and the security companies reported that devices might fail to boot or appear frozen or locked for a long period of time. The only solution back then was to uninstall the updates to resolve the issue.

Today, Microsoft added products from another security company -- McAfee -- to the list of products that did not like the newly released update.
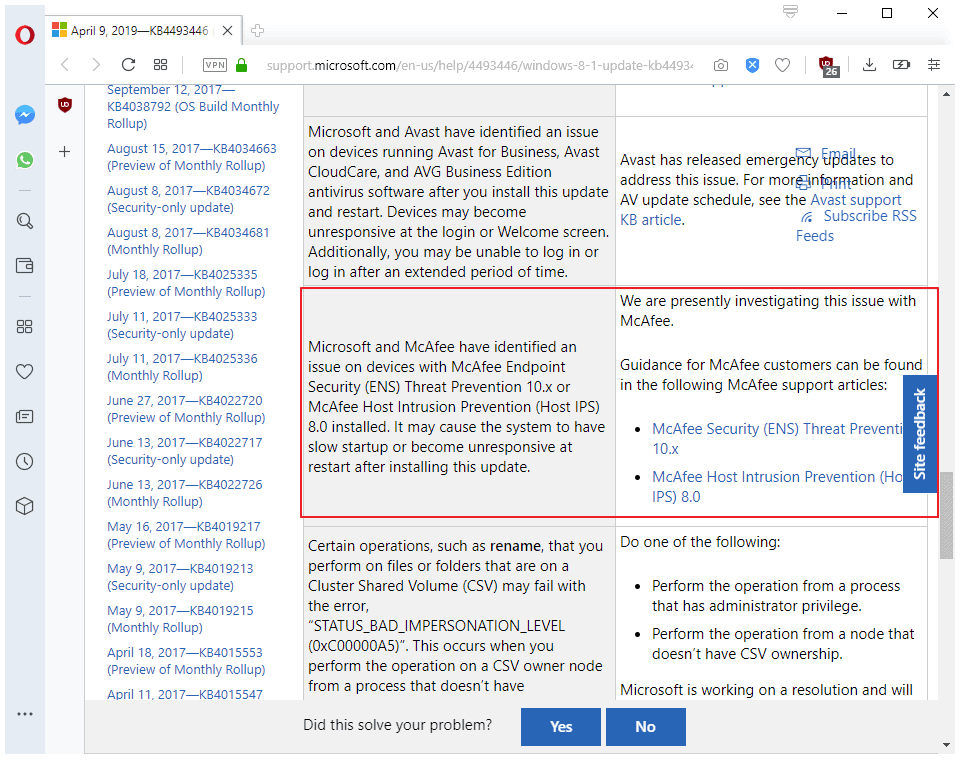
Patch notes for KB4493472 and KB4493446, the cumulative monthly rollup updates for Windows 7, Windows Server 2008 R2, Windows 8.1, and Windows Server 2012 R2, highlight the issue:
Microsoft and McAfee have identified an issue on devices with McAfee Endpoint Security (ENS) Threat Prevention 10.x or McAfee Host Intrusion Prevention (Host IPS) 8.0 installed. It may cause the system to have slow startup or become unresponsive at restart after installing this update.
Microsoft lists McAfee Security (ENS) Threat Prevention 10.x and McAfee Host Intrusion Prevention (Host IPS) 8.0 specifically, and links to McAfee support articles (here, and here).
McAfee provides some insight on the cause of the issue, and it seems likely that it is the same cause for all systems with affected security products.
Changes in the Windows April 2019 update for Client Server Runtime Subsystem (CSRSS) introduced a potential deadlock with ENS.
The company's workaround suggests that system administrators should "disable any Access Protection rule that protects a service".
Woody Leonard notes -- correctly -- that the "announcement's strange" as Microsoft lists the issue only for the monthly rollup patches but not the security-only patches. The security-only patches list issues with Sophos, Avira, and Avast products only; ArcaBit and McAfee are missing.
Are not devices with security-only patches and McAfee or ArcaBit software installed affected as well? Woody suggests that it could be "sloppy documentation"; it would not be the first time that Microsoft's provided documentation lacks vital information.
Anyway, if you run an Enterprise security solution on devices running any of the affected operating systems, you better avoid the released patches until things are sorted out. At the very least, create a backup on a single machine, apply the update and monitor the behavior carefully.


















Um, does it -rly- come as a surprise to ANYBODY (anyone, whoever) that “McAfee products [..] don’t play well with latest Windows [whatever]”, hehe. xF #noSPAM
McAfee?! Ha.. I may be dumb for using Windows, but I’m not dumb enough to use anything from McAfee.
But alas, I reckon there are some poor souls who are forced to use McAfee at work, so, thanks for the tip Martin.
From Wikipedia. I agree 100% with this as a former McAfee user.
“On January 6, 2014, Intel CEO Brian Krzanich announced during the Consumer Electronics Show the name change from McAfee Security to Intel Security. The company’s red shield logo would remain, with the firm continuing to operate as a wholly owned Intel subsidiary.
John McAfee, who no longer has any involvement in the company, expressed his pleasure at his name no longer being associated with the software. “I am now everlastingly grateful to Intel for freeing me from this terrible association with the worst software on the planet. These are not my words, but the words of millions of irate users.”
However, as of 2016 the products still bore the McAfee name.
@Dave:
McAfee is no longer part of Intel. Intel spun it off in 2017.
There’s a whole lot of insider baseball drama around why Intel acquired McAfee in the first place, and why they got rid of it shortly afterwards. The short summary is that it’s one of the symptoms of Intel’s problems in terms of adjusting their business model to the new form the market has taken.
If you’re geeky enough to be reading this site, and you use any McAfee products, you deserve what you get.
How come M$’s Windows Defender AV has not been affected much.?
@AnorKnee Merce: How come M$’s Windows Defender AV has not been affected much.?
Well, first, HIPS and the like are not virus scanners, so comparing the two is a bit like comparing a word processor and a spreadsheet.
But your larger point is a valid question, and the answer is simple. In order to do their job, system defense software has to access the operating system at a very low level. Although products try to avoid it, it is often necessary to engage in unsupported activities such as examining undocumented operating system data structures, installing patches using undocumented methods, etc.
“Undocumented” really means that Microsoft (for example) does not tell you about how these things work and don’t guarantee that they won’t change in the future. Even small OS updates can cause substantial changes to OS internals, even though users may not notice any difference from the outside.
Microsoft’s own defensive software has a serious advantage in that these things are not undocumented inside the company. Microsoft’s own teams can access the information they need, have advance warning of breaking changes, and have an input on OS changes, so can sometimes avoid breaking changes in the first place.
Right, remember the “United States v. Microsoft Corp.”, the American antitrust law case – from 1998 to 2001, final ruling – where they had been ordered to split in three (ugh, in two?) and then got PAID compensation to do so… What insanity. Of course, the Wikipedia article conveniently “forgets” to include this info… https://en.wikipedia.org/wiki/United_States_v._Microsoft_Corp.
(Thus, it’s doubtful that anybody would be bothered to bring up this monopoly issue again – this time regarding security and antivirus components, blah.)
because windows defender works well with the recent Windows Updates while some 3rd party AVs choke. I don’t see or hear any problems with Symantec or even Kasperksy who also made their AV compatible with 1903.
only Avast, Sophos and Arcabit have already released new software updates that work with the newest Windows updates. waiting for avira and Mcafee to do the same.
although Avira have recently released new program updates, some avira users claim these new AV updates still do not fix the slowdowns with the recent Windows Updates.
read these posts from these avira answers pages:
https://answers.avira.com/en/question/two-updates-later-and-avira-still-causing-major-win10-issues-82706
https://answers.avira.com/en/question/why-does-my-system-run-very-slow-82653
@ EP
So, the new tech-dictatorship of “Windows as a Service” is for all 3rd-party AV programs to be updated before M$ issues her monthly Patch Tuesday updates. Otherwise, they will have their users suffering broken Windows computers every Patch Tuesday, eg AV developers with less resources. This is like suffering menstrual cramps every month.
……. Is this fair to the less resourceful AV developers.? Shouldn’t M$ test and ensure that her monthly Patch Tuesday updates do not conflict with popular and free 3rd-party AV programs.?
@AnorKnee Merce Uh-huh, Windows as a service is DESIGNED with that in mind: how to extort the most amount of money, from everybody; AKA, “a sadistic game with consumers and businesses alike”, as mentioned in an earlier comment here. xF
(& PLEASE, I am *not* trying to “spam, or “troll”, or anything; because, really, you’re living under a rock – if you don’t know this to be true.)
@AnorKnee Merce: “Shouldn’t M$ test and ensure that her monthly Patch Tuesday updates do not conflict with popular and free 3rd-party AV programs.?”
I actually don’t think so. Microsoft should provide other companies with the information they need to do this themselves, in my opinion — but it’s not really Microsoft’s job to make sure that all of the various third party AV software works. There’s a line here. The OS is responsible for making sure that documented APIs work as promised across releases. Software that strays away from using documented APIs have been given no performance promises (actually, they have been given the promise that what they’re doing can stop working in future release without notice) and are on their own.
I think that’s fair.
That said, at least around the time of the Win 8 rolllout (I don’t know their practices after that), they actually did go out of their way to give as much information and warning as possible to third party vendors. Prior to its release, we were getting weekly builds of Win 8 in order to give us the largest windows of opportunity possible to test and resolve any issues. Microsoft was not antagonistic to third-party security software at all. They helped us quite a lot.
But the reality is that this stuff is hard, and the release schedule is such that it can happen that a particularly tricky issue can’t be fixed in time for the public release of the OS update.
Its about McAfee endpoint security (bussi and schools) other products not affected !
Everything works until M$ decides to depracate/rename/remove switches, features or whatever. It’s always Micro$oft’s fault.
It makes me wonder that Microsoft is playing sadistic game with consumers and businesses alike. With rapid release of updates and upgrades tend screw things up for OEMs and softwares.
Making McAffee along with other anti-virus and anti-malware products unusable. Ergo opening up users to nasty surprises.
@Berry Oh, yeah!.. 100% and, also, FOR SURE they’re taking money to have 3rd-party software “certified” and “compatible” to run on their systems. That’s a *huge* part of why Windows is so broken, all of the time, blah. :/
(Sorry, I’m not going to look for links; but, it’s a topic which can be easily researched, meh)
Lets hope symantec SEP 14 keep their shit together
Yup!.. Just made that comment, above. Symantec, Norton, FTW. (What’s true, is true..;))
First it was Sophos. Then it was Sophos and Avast. Then it was Sophos and Avast and Avira. Then it was Sophos and Avast and Avira and MacAfee.* Ever heard the expression “waiting for the other the shoe to drop”? How many shoes does Microsoft *have*? Is Microsoft an *octopus*? ;-)
*Yeah, yeah, yeah, I know: Arcabit. I must have been in the shower when that particular shoe dropped.
Hey, btw., just a PERSONAL opinion: when it comes to antivirus software, I’m either with 1) Norton Antivirus, or 2) Bitdefender. Unfortunately, they are ALL (including the best ones, like Kaspersky) untrustworthy, a security (spyware) risk, an attack-vector… However, what to do. Meh.
P.S. Actually, what I’m doing is running COMODO (on fully-manual, with everything “cloud” set to OFF), with the Auto-Containment “Enabled” so that it’ll trap (hopefully, anyway, hehe) anything and everything that’s not “trusted” and give a choice to run it outside of the sandbox (when needed. :))
I worked on the HIPS team during the period of time that Win 8 was being rolled out (I haven’t worked there for years, though, so my knowledge is out of date). I can tell you first-hand that maintaining compatibility with Win 8 was an absolute nightmare. Every new release of it was a crisis for us as we scrambled to fix the breakage new versions caused.
Most of this is because a product like HIPS is necessarily more intrusive in the operating system than even virus scanners (and virus scanners are pretty intrusive), so the odds of an internal change in any OS release that will break things is reasonably high. This is not a point of criticism for either Windows or products like HIPS — it’s simply the nature of the beast.
However, the whole “rapid release” thing did ramp the problem up considerably, by making it more frequent.
Oh, please, like every new release of Windows isn’t “an absolute nightmare”, hehe. We’re only *lucky* that the corporate world is also using the operating system, so that there are the LTSB and, now, LTSC branches. These make it somewhat bearable, to use the OS, blah. ;P;D
Shouldn’t it be up to the other companies to keep their products up-to-date with the main software they depend on/are attached to? How can any main software product take every other product on the market into account when making changes? Like browsers and extensions. Seems to me it’s the developers of the extensions who need to remain in sync with the browsers, not the other way ’round.
@Anonymous: “Shouldn’t it be up to the other companies to keep their products up-to-date with the main software they depend on/are attached to?”
Yes, I think is should be (and it is). But it is also important for the OS manufacturers to provide the information and lead time before release to allow products a chance to do so.
@ Anonymous
Yes, for upgrades that come 6-monthly or yearly or bi-yearly, eg upgrade from Win 10 1803 to 1809. But not for updates that come monthly, eg every Patch Tuesday.
In this case, M$’s April 2019 Patch Tuesday updates have broken some enterprise-grade AV programs = not enough testing by M$ = M$ is to be blamed.
Browser upgrades very seldom break websites, eg the 6-weekly upgrades of Chrome and Firefox.
Add McAfee products to the list of products you should never use ;)
Yes, sure, BUT – who can remember their DOS (original!) software, the -command line- antivirus scan which used to (literally) save lives, back in the day?.. The wonderful scan.exe followed by a bunch of switches @
https://kc.mcafee.com/corporate/index?page=content&id=KB52229&locale=en_US
P.S. Check out the page rating, on that article, it’s 1/5 stars (LOL). I can understand all of the “hate”, but in this case: people are hating on the wrong thing. xD
(I guess that it could be everyone who’s unaware of how to update the .dat definitions, without having to pay for it. ;))
@Yuliya:
It’s unlikely that you’d be using those two products on your own machines anyway. They’re intended for enterprise deployments and are not commonly found outside of corporate environments.
he said products
I would not deploy McAfee-anything in an enterprise environment. Windows Defender all the way.
@Yuliya Alright, sorry, but: “Windows Defender all the way”?! You must be a special kind of masochist, LOL! xF
@Yuliya:
I completely understand your stance. The problem with enterprise environments is that they have rather special needs, and practically speaking there are only two companies that make products to address them — McAfee and Symantec (Windows defender doesn’t even try to address this market — we aren’t really talking about virus scanners here).
Both of those have their own issues. It wasn’t unheard of for customers to get tired of working around the issues of one and switch to the other, until they got tired of working around the issues of the other and would switch back. And so forth.