A look at Spybot Identity Monitor for Windows
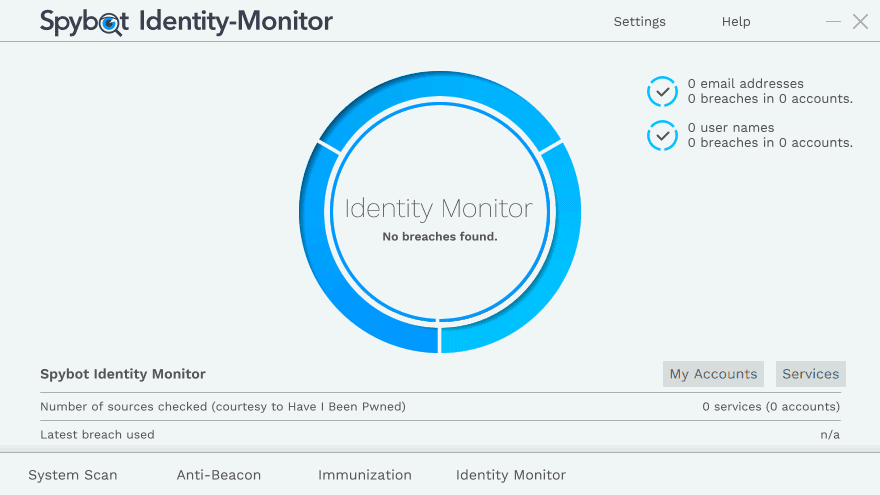
Spybot Identity Monitor is a free software program for Microsoft Windows devices designed to monitor account email addresses using the leak database provided by Have I Been Pwned.
Account databases may leak on the Internet sometimes when a service gets compromised; this happens when the hacker sells the database or puts it or a part of it online.
Leak checking services like Have I Been Pwned add these leaked databases to their own which means that it grows over time. Mozilla integrated Have I Been Pwned recently in a service called Firefox Monitor.
While it is possible to check any email address directly on the service's website and even get notifications when the email is found in a database, some users may prefer to use a program like Spybot Identity Monitor instead as it offers some advantages.
Spybot Identity Monitor

Spybot Identity Monitor is created by Safer Networking, the team behind the popular anti-spyware solution Spybot – Search & Destroy. The program is compatible with Windows 7 to Windows 10, and needs to be installed before it can be used.
The application offers two main advantages over using the Have I Been Pwned website directly:
- You get breach information for as many accounts as you enter.
- The program can recheck the data on every start.
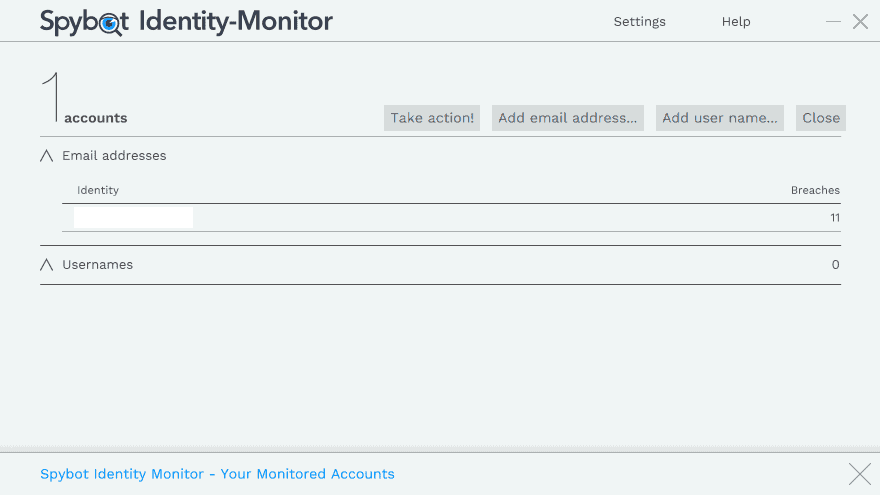
Click on "My Accounts" to add email addresses or usernames that you want to check for breaches. A check is performed as soon as you add a new account to the program's local database.
Spybot Identity Monitor reveals if the email address or username was found in known breaches. You can click on the account name to display the breached services and the date each breach happened or was revealed.
A click on a service's name displays additional breach information. You may get the number of affected accounts, the data that leaked, a short description of what happened, and the source of the information.
All leaks happened in the past but some may be surprising to you nevertheless. Spybot Identity Monitor informs you about leaks but it can't help you do something about it if you have not already.
The suggested course of action is to change the account password or close the account entirely. You may also need to change the password of other services if you used the same password, and may want to consider improving security by enabling two factor authentication or other security features that improve account security.
Identity Monitor supports re-checks of all accounts but will do so only when you enable the option in the settings. The program adds a task to the Task Scheduler which runs the check on logon.
Closing Words
Spybot Identity Monitor is a simple program to monitor email addresses and usernames against the Have I Been Pwned database of leaked account information.
The program offers a better overview in my opinion as you can add as many accounts as you like to it and get information about all of them in the interface. The option to rerun checks on logon is useful if you are particularly worried about accounts.
The application's interface design has a few inconsistency, especially when it comes to the placement of close buttons as they are all over the place.
Now Read: How to browse anonymously on the Internet





















ok but one of my accounts was victim of such a large scale breach.
I’ve changed my passwords a couple of times since then.
but still tools like this would say that my email address was compromised.
but my password was never cracked. as far as i can trace.
“Spybot” – wow… that’s a name I haven’t heard in a long time…
Thanks for the review!
I agree that local databases would be nice, but as Anonymous said, the databases would be extremely large. It’s billions of accounts. With updates again and again. We gave that some thoughts, but who would want to give up GBs of disk space for this?
Data is transmitted using a TLS 1.2 https connection, and only to the HIBP servers. HIBP doesn’t store the address. From our experience, more than 80% of long term email addresses and user names that we tried were listed, so chances are big that tested data is already on their servers and out in the wild ;)
It would be even better if HIBP would support salted hashes for lookup, feel free to recommend this to Troy Hunt :) Due to a fixed salt necessary, hash lookup tables would still be possible, but would have to be built specific to this service.
I totally agree that disposable email addresses / aliases are an important security layer. While I don’t like Google, the easy of use of “username+anyaliaswithoutsetup@googlemail.com” makes it a no brainer to use different addresses for each service out of the box.
If you’ve registered on a website using an email address, your email address and password(s) are already being stored.
Often, your email address is shared by those sites with other 3rd parties.
If one of those sites is hacked, and you are not notified, it’s more likely your credentials will be stolen there, rather than by using a security monitor to check your email address against a known database of hacked credentials.
I entirely agree. The major reason to use DEA (Disposable Email Addresses, not the Drug Enforcement Agency) systematically with the exception of commercial transactions (even if “eternal” DEAs are available via paying subscriptions) or at least true email aliases if your ISP and/or email provider makes them available.
Unfortunately many users lay their confidential emails and even use naive passwords as we know.
Also, the risk of having the email address you reserve for people of confidence be hacked should those people’s device be hacked.
Risk zero does not exist, but it’s certainly further from zero on the web than in “real” life.
What are awareness, caution, suspicion and paranoia, their specifics? Maybe I need a good doc (tor, not umentation) considering I happen to feel an increasing slide from level 1 to level 4 :=)
OK, to put it short : I don’t feel comfortable with the idea of sharing an email address with a security checking service over the clouds and seven seas, be it ”, ‘Firefox Monitor’ or this ‘Identity Monitor’. Of course I could tell myself that they (you know, those “they” we refer to when evoking the unknown bad guys who are going to eat you all up) may believe the user is sending an ennemy’s email address, how should they know it’s mine, right? Well, just in case they doubt it could be mine as well, I’ll remain silent for the time being :=)
“I don’t feel comfortable with the idea of sharing an email address with a security checking service over the clouds and seven seas, be it â€, ‘Firefox Monitor’ or this ‘Identity Monitor’”
I agree. For privacy, checks like that should be done locally, or not at all. However I think that the database is very large and that they don’t even want to make it fully available for download to avoid evil use. So, that will be not at all.