Study on the effectiveness of fingerprinting countermeasures
Fingerprinting is a common technique used by sites and organizations either on its own or complementary to track and identify Internet users.
Fingerprinting uses two core approaches to assign unique identifiers to Internet users. The first uses data that is transmitted automatically when users connect to sites. The web browser and version, operating system, or language falls into that group.
The second uses APIs that browsers support to generate and retrieve additional data points.
Techniques have reached a point where it has become possible to identify users across sessions and even across browsers. A study in 2013 suggested that at least 1% of the top 10000 sites used fingerprinting techniques.
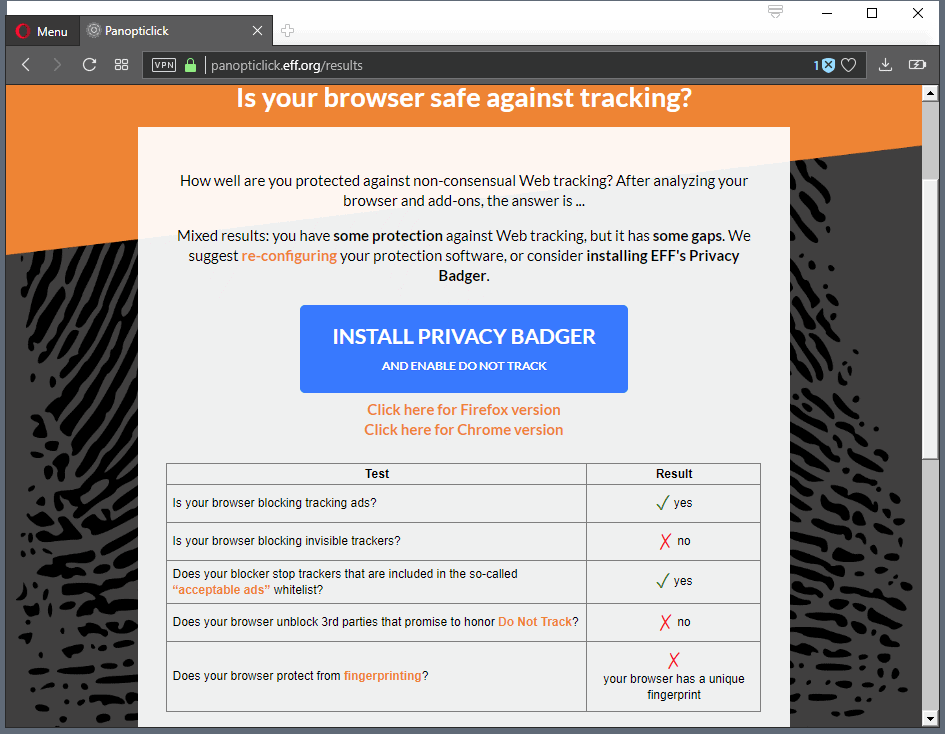
Internet users can run tests such as Browserprint or Panopticlick 2 to test fingerprinting, and users can install extensions to detect or block certain attempts at collecting data points that may be used to distinguish users from others.
The research paper FP-Scanner: The Privacy Implications of Browser Fingerprint Inconsistencies by Antoine Vastel, Pierre Laperdrix, Walter Rudametkin, and Romain Rouvoy, reveals that anti-fingerprinting techniques may not be as effective as developers claim they are.
The researchers investigated browser fingerprinting countermeasures to find out if these techniques would introduce inconsistencies and how these might impact user privacy.
The result is astonishing: not only is it possible to identify altered browser fingerprints, it is also sometimes possible to uncover the original values of fingerprint attributes that were altered by users.
The researchers developed FP-Scanner, a fingerprint scanner designed to explore "fingerprint attribute inconsistencies introduced by state-of-the-art countermeasures in order to detect if a given fingerprint is genuine or not".
The scanner detects a large number of attributes including HTTP headers, platform, fonts, screen resolution and more and checks them using various methods to find out whether they are genuine or fake.
One example: Firefox's fingerprint protection feature, which needs to be turned on by the user, changes the user agent of the browser to a generic one. Sites may use queries, e.g. -moz-os-version or the list of installed fonts, to determine whether that is indeed the right user agent, or not.
The developers provide analysis for user agent spoofers, random agent spoofer, canvas poiseners like Canvas Defender and Canvas FP Block, the Brave Browser, and other anti-fingerprinting techniques or implementations.
The researchers conclude that anti-fingerprinting techniques in browsers may make users more trackable rather than less because of the inconsistencies they introduce and use of these in the fingerprinting process.
In this article, we focused on evaluating the effectiveness of browser fingerprinting countermeasures. We showed that these countermeasures can be detected because of their side-effects, which may then be used to target some of their users more easily. We think that the same techniques could be applied, in general, to any browser extension.
Starov et al. [18] showed that browser extensions could be detected because of the way they interact with the DOM. Similar techniques that we used to detect and characterize fingerprinting countermeasures could also be used for browser extension detection. Moreover, if an extension has different settings resulting in different fingerprintable side effects, we argue that these side effects could be used to characterize the combination of settings used by a user, which may make the user more trackable.
Closing Words
If you break the research down you will come to the conclusion that most anti-fingerprinting techniques are ineffective as it is possible to detect inconsistencies. While that would not be such a bad thing, the fact that these inconsistencies may be used to fingerprint users who value privacy is.
It is too early to say what will come out of this but it looks as if browser developers need to integrate effective options into the browser to protect user privacy better. (thanks Pants)
Related articles
- A history of Fingerprinting protection in Firefox
- Firefox 63: Tracking Protection with Miner and Fingerprinting protection
- How to detect Zero-Width Characters fingerprinting
- Malwarebytes Anti-Exploit 1.08 ships with fingerprinting detection and more





















OK, I am a bad guy who doesn’t want to be tracked. In my idea, almost anyone spoofs almost anything so big brotha cannot fingerprint anyone at all. But the real internet has one big browser developed by a big ad enterprise, so alphabet chrome users are definitely tracked. IF the little number of those into Tor/VPN used something that totally changes both software and hardware fingerprints, THEN these other bad guys won’t be tracked. BUT, again, even the privacy aware ones don’t do this. If you use default TAILS you’re tracked.
I apply as much garbage data inot my headers that make me unique in the universe. Everyone should do like me and the tracking problem will end.
Facebook & Privacy is an Oxymoron. By using Facebook you agree to the Facebook EULA and offer all your info to be shared, sold and studied to and by 3rd parties who may vary according to Facebook’s market choices…
Facebook choices, not yours.
When I toggled resist fingerprinting in FF about:config
It broke what few of my, flash-heavy streaming websites.
I USE PRIVACY POSSUM, A CHROME ADD ON AND RECEIVE ” Yes! You have strong protection against Web tracking, though your software isn’t checking for Do Not Track policies.” FROM https://panopticlick.eff.org/results?aat=1&dnt=11
I just installed PP in chrome and clicked your link only to find that the fingerprinting test failed. Any idea what I’m doing wrong?
@Millenicide
Well, for starters, you’re using Chrome.
Haha well I was at work and they force us too (which is hilarious since it’s a defense contractor) what specifically about chrome are you referring to? I assumed you’re alluding to Google tracking everything you do through it?
Yes, I was just making a snide joke based on Chrome’s privacy invasive nature.
You know, I hear conflicting information on exactly how invasive Chrome is. Many people say if you simply turn off all the privacy options it’s fine, but I’d be curious to hear what you know.
I just tried adding privacy possum to Chrome, then clicked your link and it said I’m still vulnerable to fingerprinting… what am I doing wrong?
@Millenicide
Privacy Possum is going to manipulate tracking headers e.g. cookie headers, referrer headers and etag headers. I guess in a way they can be used to fingerprint you but “fingerprinting” generally refers to a method of using a combination of different types of info shared by your browser. Canvas and WebGL fingerprints, super cookies, screen resolution and size, useragent, fonts and other info. PANAMA PATRICK mentioned strong protection against “Web tracking” which is not the same thing.
Browsers should not report any details about my installation without my expressly allowing them to. No list of installed fonts, no window size, no browser identification, nothing. I have always viewed it as extremely irresponsible that browsers authomaticallyreveal any information about my installation to web servers.
Things are perhaps not as grim as this article would lead us to believe.
“Another lesson is that privacy defenses don’t need to be perfect. Many researchers and engineers think about privacy in all-or-nothing terms: a single mistake can be devastating, and if a defense won’t be perfect, we shouldn’t deploy it at all. ”
“Finally, the fingerprinting-defense-is-futile argument is an example of privacy defeatism”
https://www.doc.ic.ac.uk/~maffeis/331/EffectivenessOfFingerprinting.pdf
https://freedom-to-tinker.com/2018/06/29/against-privacy-defeatism-why-browsers-can-still-stop-fingerprinting/
Bottom line is detailed fingerprinting is only possible with javascript enabled.
Leave javascript off by default and only whitelist when absolutely necessary using something like NoScript.
Check the privacy policy for these sites before whitelisting.
“Check the privacy policy for these sites before whitelisting.”
I have no faith at all in what a site’s privacy policy says. Particularly since the vast majority of them — once you decipher the legalese — say “we’ll use the data we collect in any way we want”.
“detailed fingerprinting is only possible with javascript enabled.”
Well, that depends on what you mean be “detailed”. Fingerprinting is much easier and more precise if you can use a browser’s runtime API — but even without Javascript, plain HTML5 provides more than enough mechanisms that can be used for fingerprinting. Even in pre-HTML5, there are plenty of signals to allow identification (or, at worst, being able to say something like “you’re one of these dozen people”).
So I imagine that if you’ve been hiding things this way, that right there likely got you on a valuable marketing list:
List of Potential Privacy Concerned Customers
Next thing you know, your Facebook ads are full of privacy solutions, ha.
@Shannana
I think at this point, it’s fair to say that people who are concerned about privacy and tracking aren’t using Facebook. If they are, then they really need to think deeply on whether or not privacy and safety are actually something that is important to them.
@John Fenderson
“..it’s fair to say that people who are concerned about privacy and tracking aren’t using Facebook.”
Fair to say..? If you say so, ha!
Among the 2.19 billion users on Facebook, I have zero doubt there are many users there who are concerned about privacy and tracking. Keep in mind that any lazy idiot can be “concerned” yet do nothing. In fact, I bet marketers can buy a data list like this:
List of Active Facebook Users Who Have Voiced Much Concern About Privacy & Tracking But Still Do Nothing About It
Ha!
Regardless, it’s clear data miners, hackers, and advertising networks work hard to track and collect data about us, via evolving methods most privacy concerned folks are likely clueless about.
@Shannana: “Keep in mind that any lazy idiot can be “concerned†yet do nothing.”
I disagree. If someone is truly concerned about something, and they have control over that thing, they’ll do something. If they don’t do something about it, they’re not really all that concerned (regardless of what they may say).
FF configuration tweaks making it less prone to tracking and fingerprinting:
https://www.privacytools.io/#about_config
Valcik, thanks for the site….clas
That’s a very limited list and some recommendations are silly.
Disabling Safe Browsing is re-DICK-ulous advice and puts general readers at risk. (see https://feeding.cloud.geek.nz/posts/how-safe-browsing-works-in-firefox/ to understand that nothing is leaked to google).
access to dom.battery.enabled was limited to chrome/privileged code in FF52 (web pages cannot get this info)
geo.enabled = false is not necessary as it is behind a prompt (by default). All this does is limit the usability of the browser. In FF58+ you can use permissions.default.geo = 2 to change the default to block if you don’t want prompts (prompt fatigue?) and you can still set a site exception to use geo.
The three referer prefs are too strict (I can see loads of issues with these from experience and issues posted on github and elsewhere): instead users should be using SmartReferer for more granular control or even uMatrix’s `referrer-spoof: * true` with exceptions. You can’t properly control referers to any degree with just prefs
So out of their 21 prefs, PrivacyToolsIO are irresponsible with at least 2 of them, and ignorant of another. That’s a pretty abysmal ratio.
If you want a REAL list, with proper information, I have a *little* something here: https://github.com/ghacksuserjs/ghacks-user.js/blob/master/user.js
One of the researchers mentioned in the article also developed FPcentral which is used by the Tor Project to evaluate fingeprints as a “Panopticlick of their own” so to speak: fpcentral.tbb.torproject.org
Hi Y’all!
I use the Mozilla Firefox add-on, CanvasBlocker (along with a few other similar add-ons).
However, when I install CB last I go to that website that checks for browser fingerprint, Panopticlick and it makes the results say “your browser has a NEARLY-Unique fingerprint” which is alright in my book for now. It’s better than having a Unique result!
By the way, It does Matter in the order you install these anti-software. Trust. I found this out via trial and error. For example, if you try the M-FF addon, Disconnect – – This should be installed FIRST before any of the others to be more effective!
Thank You for Listening,
i
You can have CanvasBlocker work well and Panopticlick tell you that your fingerprint is unique, it’s normal. What you have to check is that this “unique” fingerprint is different every time you visit Panopticlick again : then you are protected (at least against that fingerprinting technique).
Most interesting article. The ‘fpscanner_normal’ pdf document is hard to understand for me but I do get some of the abstracts, such as in section [2.3 Browser Fingerprint Consistency] :
“[…]most of the browser fingerprinting countermeasures alter the value of several attributes, either by blocking access to their values, by adding noise or by faking them. However, by altering the fingerprint’s attributes, countermeasures may generate a combination of values that could not naturally appear in the wild. In such cases, we say that a browser fingerprint is inconsistent, or altered.[…]”
First thing which comes to mind is that anti-fingerprinting should all be conceived and coded by the same source, developer. I was already aware of redundancy as well of contradictions, incompatibilities between extensions themselves, now I realize that the inconsistencies these contradictions may lead to when in the area of anti-fingerprinting may create the opposite of their aim, exposing the user rather than protecting him.
What is too little, what is too much? Undoubtedly anti-fingerprinting must have all its components associated, under the control of one and one only coordinator in order to minimize the risk of theses inconsistencies. I’ll keep that in mind even if I already exercise caution with the very concept of adding protection to protection : too much doesn’t mean better, and the study demonstrates it.
This is true. There are no effective countermeasures on a desktop environment. The only solution is blending in with the masses. This is only possible if the browser itself uses technology to achieve this.
That’s why the new Safari will be the first browser with a working protection against fingerprinting. It will make everyone look similar.
[quote]We think that the same techniques could be applied, in general, to any browser extension.[/quote]
there goes their credibility.
translated in ordinary speak : “because there is one rotten tomato we suspect All tomato’s are rotten”
“We think,” they should be researchers and in such do the research, not generalize.
it would be right if they have tested this with 20 or so addons and then say “this MIGHT ally to other counter measure tools too.” and give a complete list of the tools they tested and the results per test.
This is an intriguing article, Martin but I have some questions:
The research identifies that it is possible to identify a user despite extensions that block tracking. While the technology exists to overcome the blocking are the web site developers sophisticated enough to implement that technology and are they numerous enough to affect all the websites people log on to?
No doubt, the researchers are top notch professionals who set out to determine if it is possible to fingerprint users despite blocking extensions but do the programmers who develop tracking applications have the same set of skills? Secondly, what is the percentage of the general population out there who use blocking applications? Are their numbers sufficient for the trackers to attempt to overcome the blocking apps? I simply don’t know.
It is good to have confirmation that despite our best efforts to block tracking that it still can happen. Just another reminder to surf the web in a responsible manner and to do everything we can to remain one step ahead of the trackers.
The researchers mention two technologies that can detect this already IIRC. At least some companies seem to do this already.
… Disable javascriot (unless temporarily needed)
Change your IP address often (depending on your ISP & device/router types)
Use multiple browsers of varied types & configurations … for different purposes.
Fingerprinting cannot be fully defeated… but one can readily make it much more difficult to do — especially for routine, commercial attempts at fingerprinting/tracking.
But if everybody randomized their system specs, all that they would know is that there is a lot of spoofed browsers out there and it would be easier to hide, no?
Very interesting article, thanks a lot !