Firefox 63: Tracking Protection with Miner and Fingerprinting protection
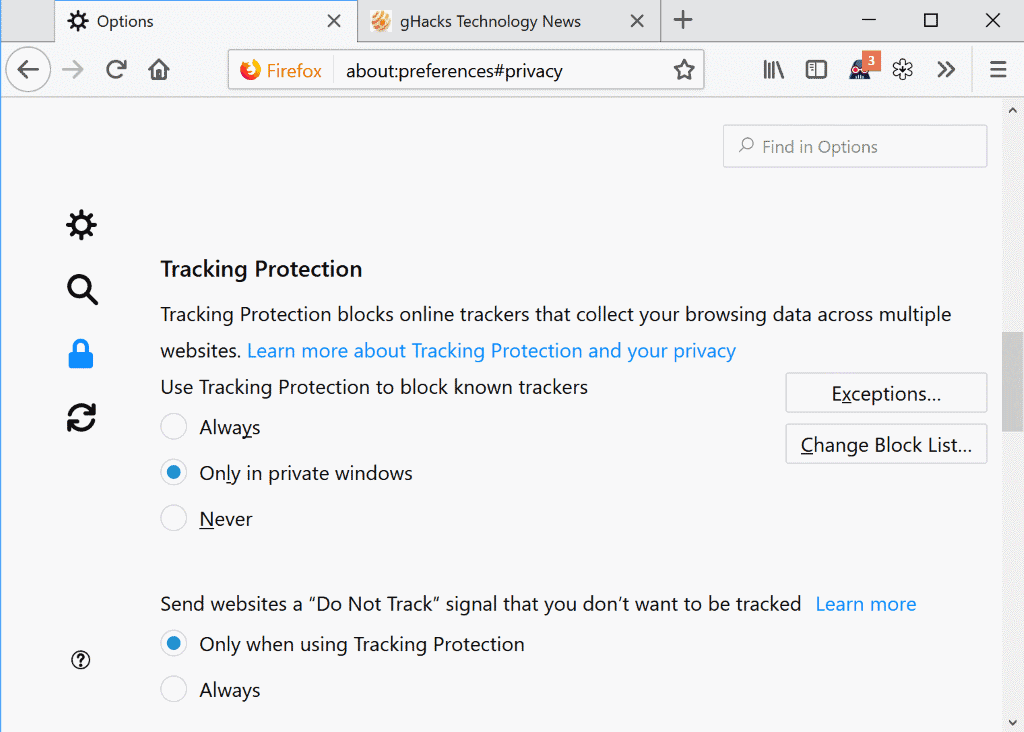
Mozilla plans to include a new protective feature in Firefox 63; the browser's Tracking Protection feature, enabled by default only in private browsing windows, will protect users of the web browser from so-called in-browser miners and fingerprinting scripts.
JavaScript mining is a relatively new threat that Internet users face. Websites and browser extensions may embed JavaScript code to mine cryptocurrency using the system the browser is run on.
While some sites ask users about it or limit the percentage of CPU power that is assigned to mining tasks, others use all of the processing powers of the device without asking users about it first.
Mozilla launched Tracking Protection in 2014 in Firefox Nightly for the desktop and for Android. Firefox 39, released in 2015, was the first stable version of the web browser with Tracking Protection but only in private browsing mode.
Mozilla did not push the feature, however, even though tests showed that Tracking Protection could reduce page loading time by almost 50%.
Firefox 57, released in 2018, was the first version of Firefox that included GUI options to enable Tracking Protection for all sites and not just in private browsing mode.
To do so, just load about:preferences#privacy in the Firefox address bar and scroll down to the Tracking Protection section on the page. Switch it from "only in private windows" to "always. You can add exceptions to disable the feature on select sites; useful if a site does not work properly after you enable the feature or if you want to support the site by not disabling advertisement on it.
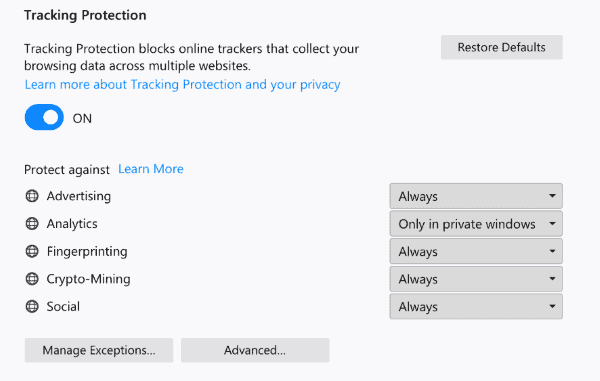
Tracking Protection uses a blocklist provided by Disconnect; it blocked certain forms of advertising, analytics and social scripts by default. The release of Firefox 63 in October adds support for blocking crypto-mining and fingerprinting scripts to the list of protective features.
Even better, Mozilla plans to give users full control over the protective features in the options. Firefox users can manage each protection individually and set them to protect always or only in private browsing mode in the settings.
The organization wants to improve the discoverability of the Tracking Protection feature as well. While it will still be listed under Privacy in the Firefox preferences, plans are underway to add Tracking Protection switches to other parts of the Firefox user interface like the security information panel that users get when they click on the "secure" text in the address bar.
Closing Words
Mozilla did not push Tracking Protection to the center stage back in 2015 when it launched the feature; a missed chance in my opinion as it probably would have had a positive effect on the user growth of the browser.
Now, Google launched its own ad-blocking in Chrome, and while it is fairly limited when compared to Tracking Protection or content-blocking scripts, it reduces the impact that an improved Tracking Protection feature has when announced by Mozilla.
Now You: Do you use Tracking Protection in Firefox? (via Bleeping Computer)





















I tried the blocking feature and ended up with some sites not working, or many not completely functional. Not really a solution for many who would get frustrated and simply turn off the blocking completely or disable for those sites. Which what benefit is doing this with the biggest offenders? Haven’t they won when they simply prevent you from using a blocking tool?
Hey Martin,
There is even a Smart Blocking feature planned to be enabled by default in the future as a phase 3 of the Tracking Protection redesign.
https://mozilla.invisionapp.com/share/KPIYY4DVHXS#/screens/301705296
good news but how exactly is crypto mining blocked? classic blocklists have no effect on mining scripts behind a proxy. it takes more than that.
I’ve been using FF Tracking Protection for some time now and it works well. There are a couple things I wish it wouldn’t block like embedded video from Instaporn and Tweeter and there are domains that could probably be blocked like tinypass. But then, the more thorough the protection, the more likely some sites will end up with some kind of broken functionality.
Anyway, I am constantly amazed at the current state of the ad/tracking ecosystem. You would think that with the constantly increasing percentage of people using ad blockers that the ad networks would wise up, and granted, some of the most annoying examples of ads have been reduced, but it seems to me like they have instead doubled down on their data collection.
Why do so many sites have to connect to 50+ domains? Gizmodo is one example. That’s horrible, isn’t it? Actually no, that’s not even close to being one of the worst examples. There are sites like Forbes, theChive, Wired and ZDNet that connect to 80+ domains on one page. But wait, even those sites haven’t reached the “how low can you go stage”. In my contest, participation trophies go to androidcentral and pcworld with 120-160+ connected domains. And the winner is? Definitely not the public. ;)
Screenshots taken today:
https://s7.postimg.cc/hqveai98r/Domains_Connected_PCWorld.png
https://s7.postimg.cc/tfzdyh7x7/Domains_Connected_PCWorld_2.png.png
https://s7.postimg.cc/n2aav8aqz/Domains_Connected_android_central.png
For me everything seems to be perfectly fine. Disconnect (strict rules) and uBlock Origin (3rd iframes blocked and so on). That’s what I see: https://imgur.com/a/SiWxwRi (screens of sites you’ve visited).
I should have been more clear about what I was doing in my examples. Sorry. The number of domains that the websites connected to was with uBO and FF Tracking Protection disabled on that site. During the tests, the only content blocking being used was my small hosts file (4400 entries) which is setup for malware and cryptomining and is the hosts file I use when doing any browser/extension testing. My bigger hosts file (15,490 entries) covers most everything but I’ve ended up leaving the smaller one enabled this last month or two. I have always used a hosts file as a backup to in browser content blocking. Most of the time, ideally, the hosts file is just sitting there doing nothing because no unwanted network requests leave the browser.
Because I’ve been testing privacy extensions in Chromium browsers, I noticed recently that some websites had a higher number of domains that they were connecting to when no content blocking was enabled. I have for years thought that a website connecting to 30-50 domains was excessive and to see the much higher numbers recently is just mind-boggling. I’ve always tried to stay aware of what those people that do not use any content blocking have to deal with and it’s a mess. Without some serious processing power and lots of very fast bandwidth I don’t see how anyone could stand to Not use a content blocker nowadays. I’m literally used to most pages taking a second or two to load but with content blocking turned off a page can take 30-90 seconds, or even longer to load, and on one well-known website I’ve actually seen over 1600 network requests made in the first 45 seconds. WTH? And I looked, that’s with very very few repeated or failed requests.
My primary browser is FF and I use the built-in Tracking Protection with the basic list. I use uBlock Origin with 3rd party iframes globally blocked but I have over a dozen noop rules that makes life easier when trying to watch embedded video and what not. If content blocking is being used and a website is still connecting to 8 or more domains, I will likely disable 3rd-party javascript for that site, not always but often. That’s just me, with most news sites I have 3rd-party js disabled. I use Canvas Defender part of the time and last but not least I use No-Script Suite Lite as a js whitelist. I use dozens of modified security and privacy settings in about:config. And of course, one of my two hosts files is always used. Most of the heavy lifting is done with uBO. I don’t know what everyone else uses in uBO but I have 155 rules in “My rules” and 86 filters in “My filters”. I’ve also modified the ‘default’ filter lists and use:
All of the “uBlock” filters.
Adblock Warning Removal List
EasyList​
EasyPrivacy
Malvertising filter list by Disconnect
Fanboy’s Annoyance List
Custom:
BarbBlock​​
facebook annoyances blocker
NoCoin Filter List
​​​Youtube: Other Annoyances​​
Richard – can you please share the 2 hosts files along with the configuration for the extensions? It would be a good starting point for me to secure the home laptop. Thank you.
@Richard Allen, your filter lists seem ok, even if the choice is essential.
You say that you set uBO with 3rd-party frames blocked and 3-rd party scripts blocked occasionally.
Why not block systematically 3-rd party scripts and add blocking of 3rd-party sites as a default policy? That’s what I do, building exceptions when required and most of the time the exception is easy to find. By exception I mean letting a 3rd-party be called in order to have the page correctly displayed and if necessary for my expectations, correctly operational.
I’ve abandonned the HOSTS file defense when I installed DNScrypt-proxy which, besides encrypting DNS requests, choosing the compatible DNS resolver, also includes programmable IP and domain blacklists, far more rational then the HOSTS file. Have a look i.e. on the occurrences of 30|2-9|br.net : dozens in most Hosts files. With DNSCrypt-proxy domain blacklist we’ll have 6 lines:
*.302br.net
*.303br.net
*.304br.net
*.305br.net
*.306br.net
*.307br.net
*.308br.net
*.309br.net
I never encounter sites, when checked as you with uBO, that conect to more than 20-25 3rd-parties.
“I never encounter sites, when checked as you with uBO, that connect to more than 20-25 3rd-parties.”
Have you disabled ALL content blocking? Including IP and domain blacklists? If so maybe it’s the difference in our locations. I’m literally in the “Wild West”, I can see Pikes Peak from my living room window, and you’re in the “EU”… eww. Just messing. LoL
“Why not block systematically 3rd-party scripts and add blocking of 3rd-party sites as a default policy?”
I’ve never wanted to ‘globally’ block 3rd-party js and then spend the time to figure out what’s needed to restore the functionality I want on each website. That said, I have disabled 3rd-party js on websites as needed. If a website connects to 8 or more domains, that is usually what prompts me to think about changes for that site. Right now, I would have a hard time finding bookmarked webpages that connect to 8 or more domains that do not already have 3rd-party js disabled, I currently have about 3 dozen websites with it disabled. Also, I’m going to make a wild guess and say that 15% of the sites that I visit have javascript disabled, they were not added to the No-Script Suite Lite whitelist because they work fine for my purposes. Let’s no forget that I’m globally blocking 3rd-party frames, and sites with auto playing video I’ve blocked the domain responsible.
I’ve intentionally kept the filters that I use in uBO to what I consider to be the most effective with the fewest used. Anything that can be added to what I currently use I look at as a waste of resources and it creates more “overlap” than I want to see. For instance, I replaced the default malware lists a while back because one of them will often fail to update the first attempt and the “Malvertising filter list by Disconnect” is smaller than the other two which is why I use it. If you are blocking ads and trackers the odds of you falling victim to a compromised 3rd-party ad is virtually non-existent. And my browsers are setup so that if I get an unwanted redirect, which will most likely be to a new site that I’ve never visited, that site will have js disabled by No-Script. Seems to me when landing on a malicious “website” having 3rd-party js disabled isn’t what is needed, what is needed is for all js to be disabled because inline js and 1st-party js will be what’s used to deliver the prize. Even when I choose to visit a new site, if it needs js enabled to view any content I will often just leave. Or, maybe I will disable 1st and 3rd party js in uBO before enabling js in No-Script. Paranoid maybe?
My primary goal is first and foremost, performance. I will do everything I can to improve security and privacy, and I will take every opportunity to give ad networks and trackers a one-finger salute but if some kind of change has an impact on performance or breaks too many sites, then it’s use is doubtful.
There are none of the “br.net” entries in any of my hosts files. I’ve never expected nor do I want my hosts file to block 100% of ads and trackers. Because I use my bigger hosts file on both PC and mobile devices I don’t want it breaking any websites. The hosts file is mostly just used as a backup to content blockers in browsers. With mobile I mostly use 3rd-party Chromium browsers with built-in content blocking but… Chrome is a beast when paired with my hosts file and I Never see any ads. Anyway, I like the simplicity of using my hosts files, they can easily and quickly be swapped when needed. And, it’s been years since I’ve used the DNS service provided by my ISP.
https://fiprinca.0x90.eu/poc/ … 321 (it should be 326, 325 CAs and the 1st party, but I guess some are now obsolete?) .. soz, it’s not a real world example, just a PoC :)
https://i.imgur.com/w5wktOB.png?1 (not mine) – 1million (not domains, but requests blocked, it just keeps attempting requests as long as the page is open)
I knew the company in the time (Around 1970) when they were still a Dutch company and where called IVA Software. I am not quit sure what I am thinking about a company who was giving out in 1999 the largest bonus in history at that time from a public company a $675 million after-tax charge for $1.1 billion in payouts to Wang and other top CA executives.
Especially when the story continues when In 2000 a shareholder-based class-action lawsuit accused CA of misstating more than $500 million in revenue in its 1998 and 1999 fiscal years.
And what to think about that same company were after 2000 eight CA executives since then pleaded guilty to fraud charges – most notably, former CEO and chairman Sanjay Kumar, who received a 12-year prison sentence for orchestrating the scandal.
And do not forget that CA has been party to a large number of lawsuits over its forty-year history.
Can I trust any result from such a company?
Due to all Respect, People,…you cannot hide yourselves from Internet’s Electric Eyes, accept it.
“More than three-quarters of people globally believe their internet privacy is at risk, according to data compiled by U.S. News as part of its 2018 Best Countries rankings, breaking down how respondents from particular nations and regions view the world. The rates of concern are almost all between 75 percent and 80 percent regardless of gender, age or living in an urban or rural environment, and are comparable among respondents in Europe, Asia, the Middle East and Africa, and the Americas.”
Source…
https://www.usnews.com/news/best-countries/articles/2018-05-24/data-heavy-reliance-on-social-media-aligns-with-trust-in-private-companies
I use this in my huge HOSTS file:
https://github.com/hoshsadiq/adblock-nocoin-list/blob/master/hosts.txt
Checked a few in your list and they were in here, too:
https://github.com/StevenBlack/hosts
An alternative with variations on what you want blocked.
@ Martin,
Respectfully, all you’ll achieve with the continual cookie warnings is to alienate users. After all, how many times do I have to click “GOT IT! in order for it not to reappear on the next article I open?
Needless to say, it puts me off doing that when I know I’m going to have to click the damn notice again.
i just created a Filter with uBlock Origin’s Element Picker. i’ve done this a long time ago. Haven’t seen it since it was first implemented.
That’s the EU Cookie Law! Absurd. Strange though the cookie warning reappears because as long as you haven’t quit a website after having clicked the cookie agreement the warning shouldn’t reappear. Maybe have you blocked cookies or blocked them for Ghacks?
I allow session cookies only everywhere.
But I’m also using a VPN which means my IP adress changes from day to day.
@TelV, here the ‘EU Cookie Law’ annoyance is handled by a script and a css,
https://cdn.ghacks.net/wp-content/plugins/cookie-notice/js/front.min.js
https://cdn.ghacks.net/wp-content/plugins/cookie-notice/css/front.min.css
But a simple blocking rule in either a Styles manager (Stylus, Stylish) or in Firefox’s userChrome.css should block the annoyance. I have several ‘EU Cookies’ dedicated filters and I think this one should handle the annoyance here as well as on all sites using the same scheme:
#cookie-notice
Of course it’s not Martin’s, Ghacks’, WordPress’ fault but the aberration of an extremely badly thought technocratic EU law, bothering everyone. Used to get me out of my mind before I decided to put a definitive end to this absurdity.
Thanks for the tip Tom, I’ll keep it in mind.
However, after updating the “I don’t like cookies….” addon earlier, I haven’t seen the cookie notice again :)
@TelV, I hadn’t understood you were running the ‘I don’t care about cookies’ extension is it? With that you should be OK on most sites.
@Martin (Ghacks) sorry for detailing above the script/css, even though it’s info accessible by all, remains it may be a bit inconsiderate to describe a site’s internals. I did because I know these are imposed by the EU Cookie Law and not pertinent to Ghacks.
Tom, no problem I hate this as much as anyone else :)
The cookie warnings are required by Eu law, and are cookie based. Do you clear all cookies on exit? If so, then the site has no way to know you already “got it”. Apologies if you already know this, but your complaint surprised me. Personally, I just ignore them completely.
I’m aware of that, but it’s ludicrous to have the notice appear when switching from one article to another.
https://addons.mozilla.org/en-US/firefox/addon/i-dont-care-about-cookies/
@ stefann,
It doesn’t appear to be working on ghacks.
I’m also subscribed to Prebake, but that doesn’t help either.
Those are great news, can’t wait to see it reach stable release !
Built-in privacy/security features are never to be neglected and ensure a basic protection for all, given the following equation be resolved for unaware users:
ON by default, blocked pages and users’ frustration,
verses,
OFF by default, no blocked pages and users’ vulnerability.
So, indeed, as Martin points it out,
“Mozilla did not push Tracking Protection to the center stage back in 2015 when it launched the feature; a missed chance in my opinion as it probably would have had a positive effect on the user growth of the browser.”
Firefox built-in tracking protection has to be loudly and wildly proclaimed, it must become IMO a systematic correlative argument for using the browser as well as speed, power, ram, cpu etc …
For myself? I don’t use Firefox’s Tracking Protection because the extension ‘uBlock Origin’ includes far more filter rules than Firefox’s on the basis of ‘Disconnect’. But for a starter or for anyone wishing to “surf and forget the extras” : at least DO enable Tracking Protection. I helped my neighbor install and configure his Firefox and of course I explained this Tracking Protection feature and we agreed to have it operational ‘Always’ and not only in Private Mode. It’s a required basic protection, IMO.
Oh! s*** … I should have wrote “ON by default, *possibly* blocked pages and users’ frustration”
“possibly” because it mustn’t occur often, that a site, a page be inaccessible because of Firefox’s Tracking Protaction.
That’s what I meant, my dear Tom :=)
“verses”? Was that spelling intentional, as I suspect, or did you mean versus? Or maybe it’s a subconscious manifestation of poetic expression? :)
@Richard Allen, you’ve won the First Price!
I had in mind vs., I therefor was in the concept of versus. Unfortunately it won’t have had the charm, mystery, exoticism of any subconscious manifestation nor whatever subliminal hidden power of an intentional mistake.
I could have had a darling to whom I would have promised to write “verses” inconsistently as a secret message meaning her eyes reveal to me the infinite beauty of the universe (as the verses do) but that wasn’t planned :=)
First PriZe, not PriCe …
I must be in love…
Right now I am using Canvas defender (From https://multiloginapp.com/).
Multiloginapp employs a number of counter-fingerprinting technologies, which helps to avoid different fingerprinting detection mechanisms that websites utilize to link together multiple accounts belonging to the same user. It works even with the toughest platforms like Google Adwords, Facebook Ads, LinkedIn and other.
Do I understand that when Firefox is coming with there one fingerprinting technology integrated into the browser I can disable/remove Canvas defender completely because it’s not only ads nothing to the then already integrated Firefox fingerprinting, but also then will class (Not work together) with Firefox 63 his one integrated fingerprinting technology?
Ignore my other comment, I wasn’t ready to post it lol.
The fingerprinting protection has been existing in FF for a long time, you can activate it in about:config (privacy.resistFingerprinting = true).
You can read more about it here: https://wiki.mozilla.org/Security/Fingerprinting
In order to make all TOR users and all users of this feature to appear the same, this will also spoof the Canvas fingerprint (as one fixed value). So yes, still using Canvas Defender which randomizes the Canvas hash would destroy the purpose of the feature. (But it doesn’t necessarily de-anonymize you.)
The fingerprinting protection is implemented in Firefox for a long time now.
I think it should be noted that Tracking Protection doesn’t block all trackers by default. For example, it still allows Google and Facebook to track users behaviour even in Private Browsing mode. In order to block all of them, users either have to change the Block List to “Strict” in which case some sites won’t work, or use an addon such as Privacy Badger.
It sounds like a good idea though to add crypto-mining protection along with fingerprinting and I hope Firefox forks like Waterfox will adopt the same settings.
Thanks but how would I check this?
If you have Privacy Badger installed, you can see which sites continue to be allowed when you’re using Private Browsing mode. You can download Privacy Badger from the AMO site at: https://addons.mozilla.org/en-US/firefox/addon/privacy-badger17/
Is this also from Disconnect ?