Linus Torvalds calls Intel’s Spectre/Meltdown patches utter garbage
Linus Torvalds is the mastermind behind Linux, and well known for his very colourful opinions on things, like the time he flipped NVIDIA the finger. Yeah, he did that.
This time, Torvalds is getting rather vocal about his views on the patches released by Intel to deal with Spectre and Meltdown. I’m going to have to sensor some of the quotes in this article, but you can read the full flavoured ones for yourself.
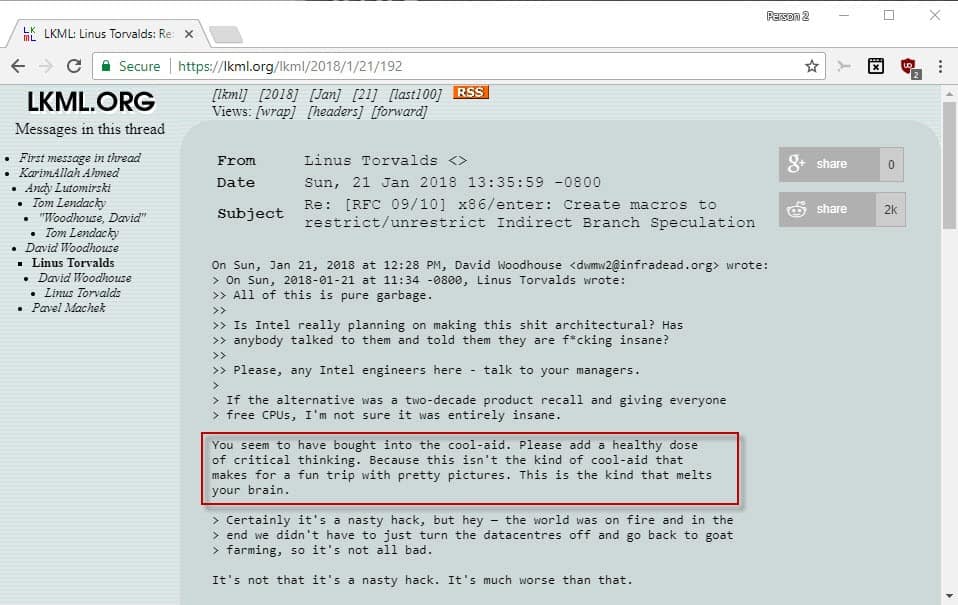
“You seem to have bought into the cool-aid. Please add a healthy dose of critical thinking. Because this isn't the kind of cool-aid that makes for a fun trip with pretty pictures. This is the kind that melts your brain.â€

Another such example being, “WHAT THE $@!$ IS GOING ON? And that's ignoring the much _worse_ issue, namely that the whole hardware interface is mis-designed by morons.â€
Torvalds made these statements and many others in a rather long message sent out in the unofficial Linux Kernel Mailing List archive on Sunday, Jan. 21. I would also like to add that the main homepage for the website itself, is not without its sass, reading,
“LKML.ORG?
In case you haven't read the title bar of your web browser's window: this site is the (unofficial) Linux Kernel Mailing List archive. This mailing list is a rather high-volume list, where (technical) discussions on the design of, and bugs in the Linux kernel take place. If that scares you, please read the FAQ.â€
That said, none of this really should be many surprises.
Torvalds ends off his post by saying, “I think we need something better than this garbage.â€
So, Torvalds once again has made headlines in the tech world for coming out and being very colourful in his opinions, but, often people support his reasoning and his logic for his rants.
Related articles
- Gibson releases InSpectre vulnerability and performance checker
- How to update Intel hardware drivers
- Microsoft releases out-of-band security updates to address Intel bug
- RedHat reverts patches to mitigate Spectre Variant 2
















Nice Move Microsoft and Intel that is one way to get people to spent money on an ale-ling computer market.
{Beware the phones are coming}
“The first Intel chips with built-in protections against the Meltdown and Spectre threats will start arriving later this year. The protections involve “silicon-based changes” to the company’s future processors, Intel CEO Brian Krzanich said in a Thursday, 25, 2018. PCMagazine.
There were no details given.
If you break down his statement, it is vague and open to interpretation …
“Silicon based changes” to future processors, is not the same as ‘ silicon redesign’
“Built-in protections” what is that, firmware patches ?
What future processors arriving later this year ?
He has a ‘Lake’ he wants to sell us, maybe it’s Chaubunagungamaug Lake.
@LD
Your interpretation is extreme, the fixes for the spectre/meltdown variant flaws will be built into the silicone, this is whats is the message. That alone is a redesign of this particular portion of the architecture affected.
What your comment implies is that somehow the whole architecture should be redesigned even the unaffected portions. That will never happen for this particular issue.
The current series 8 are still flawed. Youre looking at 3rd quarter silicon for the in silicon fixes.
@Author
“Linus Torvalds is the mastermind behind Linux, and well known for his very colourful opinions on things, like the time he flipped NVIDIA the finger. Yeah, he did that.â€
He did this for good reason and is worthy of applause IMHO. Nvidia refuses to make its drivers code opensource, unlike AMD which did
@LD
Your interpretation is extreme, the fixes for the spectre/meltdown variant flaws will be built into the silicone, this is whats is the message. That alone is a redesign of this particular portion of the architecture affected.
What your comment implies is that somehow the whole architecture should be redesigned even the unaffected portions. That will never happen for this particular issue.
The current series 8 are still flawed. Youre looking at 3rd quarter silicon for the in silicon fixes.
@Author
“Linus Torvalds is the mastermind behind Linux, and well known for his very colourful opinions on things, like the time he flipped NVIDIA the finger. Yeah, he did that.â€
He did this for good reason and is worthy of applause IMHO. Nvidia refuses to make its drivers code opensource, unlike AMD which did
@LD
Your interpretation is extreme, the fixes for the spectre/meltdown variant flaws will be built into the silicone, this is whats is the message. That alone is a redesign of this particular portion of the architecture affected.
What your comment implies is that somehow the whole architecture should be redesigned even the unaffected portions. That will never happen for this particular issue.
The current series 8 are still flawed. Youre looking at 3rd quarter silicon for the in silicon fixes.
@Author
“Linus Torvalds is the mastermind behind Linux, and well known for his very colourful opinions on things, like the time he flipped NVIDIA the finger. Yeah, he did that.”
He did this for good reason and is worthy of applause IMHO. Nvidia refuses to make its drivers code opensource, unlike AMD which did
Hi Cigologic, I know that what you are saying…
Put the point is that the patches works on the good spec pc’s. Even a 7 year old one. Oke, it’s a little bit over-tuned than the basics that you find in the stores but I do not think that Intel looks to hard for low-end-spec pc’s and if it works as good as the high-end-pc’s, so bashing Intel for it that it is utter garbage is also a little bit over the top. And no slowdowns with a HD 7200 ten years old laptop… this is not high end in my mind. Laptop, surely 7 years ago where slower than a desktop and even in these days and we know that with a regular HD that there is a big bottleneck and so the CPU works overtime. Therefore with a SSD the CPU can just run smoothly…
But like I see it it’s not tested with such a high ends CPU’s Cigo. Even I have here an i5 from 2011 but I’m on Xp and cannot download these patches but I’m fine with the speed like it runs now.
– 2010 laptop – 1ste GEN i5 CPU
– 2011 desktop – i5 from that time also
– 2012 – similar to the gaming rig but with a slightly less CPU
– 2013 – Vivobook
– 2014 – i7 laptop CPU (are not so fast as the i7 Desktops)
– 2015 – i3 CPU
The most are laptops and sure there are high ends hardware in it but like I see it, the CPU’s are not so high end this days and laptop CPU’s are slower than desktop CPU’s. And that he has no AV and no slowdown whereby there are people like him with an AV and they have slowdowns, then, like I see it, is there a problem with the AV and they need also to update. And I think that none knows the long-term impacts for now…
>> KeZa_BE: “the point is that the patches works on the good spec pc’s”
Apparently, neither Intel nor Microsoft has any confidence in their Meltdown-Spectre patches, regardless of whether the machine is high-end or not.
Intel has withdrawn ALL of its microcode updates related to Meltdown-Spectre. And as of 27 Jan 2018, Microsoft has also released an out-of-band patch for ALL supported Win OS versions to DISABLE the early Jan 2018 Meltdown kernel patch, which is based on Intel’s self-confessed flawed microcode updates.
As Intel & the entire IT industry have known about Meltdown-Spectre since around Jun 2017 (but kept silent due to non-disclosure agreements), they have more than ample time to come up with a proper fix during the past 6-7 months.
The fact that ALL patches have been withdrawn recently suggest that a microcode/software fix might not be possible without incurring significant performance impacts. Which is probably why Linus Torvalds said that Intel should offer a replacement to users of vulnerable CPUs.
>> “bashing Intel for it that it is utter garbage is also a little bit over the top”
I suppose you are referring to Linus Torvalds’ colourful outrage ? :) In my earlier comment, I didn’t talk about Intel itself — whether in negative or positive light.
Instead of system performance benchmarks, I think Linus’ rage comes after examining the details of Intel’s microcode itself, which he concludes to consist of nonsense “garbage hacks”.
My earlier comment was about taking those “zero/negligible impact” tests with a grain of salt, because so far they are all performed on high-end machines with professional or enterprise-level hardware. Hardware doesn’t just refer to the CPU. A fast disk & abundant RAM can to some extent possibly buffer slowdowns in CPU processing speed.
>> “no AV and no slowdown, whereby there are people like him with an AV and they have slowdowns, then, like I see it, is there a problem with the AV and they need also to update.”
I don’t think the latest updates by third-party antivirus have made them less liable to slowing down the system, because they still hook onto the OS kernel, which is the reason why it is relatively tedious to uninstall third-party antivirus cleanly.
Which brings to mind … I notice an increasing movement amongst IT enthusiasts to ditch third-party antivirus — & either go without any real-time protection (but maintain a locked-down system & observe strict IT hygiene practices), or else install Microsoft’s in-house antivirus.
He’s not bashing Windows, he’s bashing Intel (as he and everybody else should).
@Ron
Businesses and people should vote with their wallets and no buy up to any Intel 8 series. Will it ever happen? No, I dont think so.
Bashing intel has zero value and no fucks are given. Hurt their bottom line and see how quickly their song and dance changes.
But he does not… https://www.dedoimedo.com/computers/meltdown-performance.html
Much testing on different devices and OS and everything fine. So Linux is bashing Windows… nothing new here.
>> KeZa_BE: “Much testing on different devices and OS and everything fine.”
Users’ mileages would probably vary according to how expensive their machines are. If you scrutinize the specs of the PCs that were tested, ALL of them are **higher** end rigs. (… As I observed so far, likewise for the ALL other testers who announced that their machines have not experienced any slowdowns since installing the Meltdown-Spectre patches.)
In Dedoimedo’s tests, even the PC with the lowest specs — an “old HP machine” (2010 laptop) “conceived with high-end gaming in mind” — has a 7,200 rpm disk & got installed with an extra 4 GB (making it a total of 8 GB). Such specs were not standard to laptops released in 2010. For comparison, my 2010 gaming laptop has only 4 GB RAM & a 5,000 rpm platter disk.
Also, none of the tested machines has any antivirus installed. In fact, Dedoimedo made it clear why these machines were selected for testing: “No real-time anti-malware thingie using CPU cycles.”
Moreover, Dedoimedo appears to have multi-numerous PCs to use at his convenience, with his main rig likely to be the latest & the greatest amongst them all. As such, even discounting the fact that all his machines boast higher-end specs, he probably doesn’t use any of his secondary/ spare/ storage PCs long enough to know that the Meltdown-Spectre patches will not have any long-term impacts.
‘Every cloud has a silver lining’ – Penned in the year 1634 when if you were accused and convicted of sorcery, you got burned alive.
Meltdown and Spectre is the stormy blackish grey puff ball looming menacingly over our computers. Intel gave this building storm 90% of its energy in the first place and now their efforts to batten down is sorely wanting. The prevailing storm may pass, but then again, it could intensify.
So what about the silver lining, where is it? According to those who are still ‘in charge’ of the issue, say they have brand new product in the wings that repels the existing threat. Silver has always been what they had in mind. The more the better.
I am all for a huge bonfire. I think the sorcerer(s) are still at it.
Oh the panic!!!!
What if this is actually a secret a plan by chip maker to make people rush out and buy their newest chips which don’t have the problem?
Nah. They’d never do that …. or would they?
I’m just glad my main PC is not impacted by this BS. But, what’s coming next?
@pHROZEN gHOST
You see conspiracy, when in fact its more like Intel doesnt care really.
Their new chips (8 Series) still has the issue and thats the newest.
Now if people or businesses stpped buying Intel chips old and new up to 8 series, that would be the right thing to do, It will never happen of course.
Also people claiming no exploits being used, is, at the very least FUD. Anyone that reads security news knowns that things being actively exploited for years and years like 5 or more years ago only now coming to light. Nothing surprises me anymore not even the publics never ending ignorance.
If that was Intel’s plan, they’d have fixed it first with their latest silicon. No, i think this is just a massive screw-up.
Lets let people believe it was just a major f**kup. It’s better for the manufacturers.
However, there will always be a new “latest silicon” which can fix this.
“there will always be a new “latest silicon†which can fix this.”
In this case, the “latest silicon” that fixes this is at least two years away, minimum. In the meantime, we’re going to have to endure a series of patches over time as new Spectre-class exploits are developed and deployed.
A side-advantage of being knowledgeable is that fury is then legitimate.Basic users as myself can then have a basis to follow on via others’ talents. For instance I have no technical argument to motivate what may be excessive caution when it comes to the anthology of patches and more specifically concerning the Meltdown/Spectre tsunami. I even dislike the very word “patch” (“Computer Science : A piece of code added to software in order to fix a bug, especially as a temporary correction between two releases.” according to The American Heritage® Dictionary of the English Language, 4th Edition). Sounds to me as a “better than nothing”. I’ve always had the feeling the entire code universe was a dimension of perpetual try-do-fix, with fixing more the latest cause than the first one.
So, Linus Torvalds expresses feelings with colors about black/white code. Enforces my wait and see approach.
> And they knew what was coming, which is why Haswell and newer have INVPCID support.
What is INVPCID support? I tried searching but didn’t find anything.
@ JC
It’s PCID or Process Context Identifiers.
Considering that Intel and pretty much everyone else except those fine and responsible folks at Microsoft have advised their customers not to apply the patches they have issued, I don’t think we can accuse Linus of overreacting under the circumstances.
I gave away my last Pentium MMX last year so it’s nail biting time for me. I practically have a museum here and every single damn computer has a vulnerable processor.
I’m using a laptop from 2012, so as for the Spectre vulnerability, it’s a matter of whether ASUS decide to release a BIOS update.
@ Gavin — Further to my earlier comment, ASUS has an additional advisory page regarding the BIOS patch status wrt Meltdown-Spectre.
ASUS states that it would be releasing revised BIOS updates for motherboards with 6th, 7th or 8th Intel Core CPUs, or X99 & X299 platforms with Intel Core X-series CPUs. The page has a detailed list of affected motherboards/ chipsets.
https://www.asus.com/News/V5urzYAT6myCC1o2
@ Gavin — You can check ASUS’s advisory list for which models have or would be receiving BIOS updates related to Meltdown-Spectre at:
https://www.asus.com/News/YQ3Cr4OYKdZTwnQK
But note that as of 23 Jan 2018, Intel has withdrawn ALL of its microcode updates (which OEMs incorporate into BIOS updates) that were issued to patch Meltdown-Spectre. This is because the microcodes contain flaws that are known to cause spontaneous reboots/BSODs or other unexpected system instabilities.
As such, some OEMs have similarly withdrawn the already-released BIOS updates. Even if ASUS has not done so, you should not install any BIOS update released between the first week of Jan 2018 (when the vulnerability was disclosed) & 23 Jan 2018.
However, since most OEMs do not typically issue BIOS or driver updates for machines older than 5 years — even in the event of critical security vulnerabilities — ASUS may or may have any BIOS update for your 2012 laptop.
>And that’s actually ignoring the much _worse_ issue, namely that the
>whole hardware interface is literally mis-designed by morons.
Omg, way to start my morning off :) (It’s actually close to noon here, but don’t mind it, I drink my coffee now, so it must be morning)
He is right though. These potential (then) issues have been presented somewhere in the 199-something. It’s a two decade flaw. And they knew what was coming, which is why Haswell and newer have INVPCID support. But the fact that it has been there, well known, and they just left the defect for two decades is unacceptable imo. And expecting people to accept patches that literally make their PCs unbootable at worst, or, at best, have a significant overhead, is absolutely disgusting.
@Yuliya – yes, disgusting. But look how the media had us (those that pay any attention, anyway) running around like fools trying to sort out their mess. Something that’s been there for decades, suddenly hits the panic button. Everyone just has to slow down and quantify the issue, not act like little sheep that follow “cause someone says so”.
Yesterday morning, my dedicated media PC was blue screening. Its been good as gold for 3 years. Suddenly…the crap was hitting the fan.
What was it? I had left it sleeping al night…..(unusual for me to leave that PC to sleep), and in its infinite wisdom, the AV on that PC had decided to update, and likely for reasons to mitigate these threats, had bricked the PC in the process.
It almost certainly was that, because I managed to start in safe mode and completely removed the AV (will now never re-instate it on that PC), and everything was good again.
It wasn’t just a signature file update that it made, it was a whole new version, and perhaps because of missing registry key….that was it, a boot loop BSOD.
World has gone mad!!! If Satya is not messing with my stuff, the AV folk are. That’s why I am now handling all security my way….and holding all these untested “solutions” very much at arms length.
>> Sophie: “the AV on that PC had decided to update […] It wasn’t just a signature file update that it made, it was a whole new version, and perhaps because of missing registry key….that was it, a boot loop BSOD.”
The new engine/ version update by your antivirus is supposed to set the compliant registry key (required to receive Microsoft’s Meltdown kernel patch **via Windows Update**) ON YOUR BEHALF — or otherwise advise you to set the key manually (ie. if you wish to receive MS’s kernel patch **via Windows Update**).
** Note: The Windows Update issue is the only purpose of the registry key. An antivirus engine update alone in the absence of the registry key will NOT make your machine go into a BSOD reboot loop, unless your AV update is flawed.
By now, many AV vendors have already set this registry key. You can check if your (now-uninstalled) AV did or did not set the registry key by referring to the below product matrix, courtesy of the Google team that discovered the Meltdown-Spectre vulnerabilities:
https://docs.google.com/spreadsheets/d/184wcDt9I9TUNFFbsAVLpzAtckQxYiuirADzf3cL42FQ/htmlview
If your AV had set the key & you are using an OEM PC/ motherboard, the spontaneous “boot loop BSOD” problem on your machine could have been caused by an automated BIOS update (using Intel’s buggy “garbage” microcode patch) pushed out by your OEM via its system updater:
https://www.techarp.com/articles/intel-cpu-reboot-root-cause
As of 23 Jan 2018, Intel has recalled ALL of its microcode patches, with OEMs issuing emergency press advisories accordingly for users to either downgrade the BIOS version (if possible), or wait to receive the next proper BIOS update (& in the meantime, bear with spontaneous BSODs/ reboots).
I’m a little late to the party, but I think it’s a shame to have to respond to someone who firstly, misuses the term “brick”. Brick is when you’re electronic item is not easily recovered by uninstalling something and rebooting. Applies to cell phones when they won’t start up- therefore are functionally like a brick. Plus it wasn’t immediately clear that AV meant anti-virus and not Audio-Visual. It would make some sense for her to complain her dedicated media center is getting unneeded security patches, not so much that her anti-malware software is doing what it’s supposed to do. Sophie had already given me a lot of reasons not to listen to her. And I find it probable she didn’t listen to your advice. Nice work nonetheless.
My thoughts exactly. The wait and see approach has never been more convenient than it is right now. Patch this, pathc that, system fails to boot, now Intel has given instructions to the MB manufacturers to urge their users to revert to pre-pathc BIOSes (how stupid is that, especially when it comes to this low-level stuff – you’d surely want avoid messing with it for as much as possible since accidents can happen and this is not Windows to just reinstall it in a couple of hours and be done with it).
As for Micro$oft’s CEO.. well, Balmer brought us the disaster known as Windows 8, and I think Balmer was a better CEO than the current one! Nadella’s “mobile first, cloud first” approach is absolutely pathetic. I knew he would trash Windows even before he’s gotten started.
Everybody just has to sit tight. There are no known abuses of these exploits in the wild. Humans love a good scare story….just like storms, hurricanes and weather stories get ramped up to the max.
Not to suggest that these issues are not essentially serious, but the modus operandii always has to be wait and see, let others be the guinea pigs. Doesn’t it?
I’m not touching my stuff, and firmware updates is not for the feint of heart.
AV-TEST GmbH
[UPDATE: 2018-01-23] #Spectre & #Meltdown: So far, the AV-TEST Institute discovered 119 samples which appear to be related to recently reported CPU vulnerabilities. #CVE-2017-5715 #CVE-2017-5753 #CVE-2017-5754
https://m.facebook.com/avtestorg/photos/a.539657639420362.1073741831.104433409609456/1777730362279744/?type=3&source=48
I hope I’m not the only one dragging their feet getting the patches installed. I think I’ll just continue to wait and see how all of my beta testers do before jumping on the bandwagon and I suspect that I’ll be just fine for quite some time without the patches. I haven’t heard of any active exploits yet. ;)